Author Archives: Dani Grant
Author Archives: Dani Grant
We launched DNSSEC late last year and are already signing 56.9 billion DNS record sets per day. At this scale, we care a great deal about compute cost. One of the ways we save CPU cycles is our unique implementation of negative answers in DNSSEC.
 CC BY-SA 2.0 image by Chris Short
CC BY-SA 2.0 image by Chris Short
I will briefly explain a few concepts you need to know about DNSSEC and negative answers, and then we will dive into how CloudFlare saves on compute when asked for names that don’t exist.
Here’s a quick summary of DNSSEC:
This is an unsigned DNS answer (unsigned == no DNSSEC):
cloudflare.com. 299 IN A 198.41.214.162
cloudflare.com. 299 IN A 198.41.215.162
This is an answer with DNSSEC:
cloudflare.com. 299 IN A 198.41.214.162
cloudflare.com. 299 IN A 198.41.215.162
cloudflare.com. 299 IN RRSIG A 13 2 300 20160311145051 20160309125051 35273 cloudflare.com. RqRna0qkih8cuki++YbFOkJi0DGeNpCMYDzlBuG88LWqx+Aaq8x3kQZX TzMTpFRs6K0na9NCUg412bOD4LH3EQ==
Answers with DNSSEC contain a signature for every record type that is returned. (In this example, only A records are returned so there is only one signature.) The signatures allow Continue reading

CloudFlare and Gandi have been hosting a speaker series on DNS, previously bringing in the founder of DNS Paul Mockapetris and Dan Kaminsky, who uncovered one of the most critical vulnerabilities in DNS.
Our third and final talk is coming up on June 21st at 6PM PST at the Gandi office in San Francisco (live stream link will be posted on the Meetup page) and you won’t want to miss it, because our speaker is none other than Paul Vixie.
Paul wrote most of BIND Version 8 and hired the team who wrote BIND Version 9, the most widely used DNS software on the Internet. He founded ISC, home of BIND and F-root and later operated C-root.
We'll talk about alternative DNS root servers, email security and spam (Paul founded the first ever anti-spam company), and what needs to be done about DNS and security (Paul added most of BIND’s current security systems).
So come grab a beer and let's geek out about DNS one more time.
Today we’re announcing the sunsetting of CloudFlare’s first client API, API v1. Starting November 9th, 2016 at noon Pacific Time (20:00 UTC), CloudFlare will no longer be supporting API v1.
While it is bittersweet to let our first API from CloudFlare’s early days go, we are so excited to show you all of the great things about our latest API: API v4. We’re confident that once you get started using it, you’ll see how easy API v4 makes managing your CloudFlare settings.
(For those of you who are curious where CloudFlare’s API v2 and v3 went, they ran away with IPv5 and PHP 6.)
If you are using API v1 and need to migrate to API v4, we’ve written extensive migration docs here for you to follow. They contain every API call from v1 and their equivalent in v4 side by side.
After CloudFlare discontinues support for API v1 in November 2016, any calls to API v1 will return the HTTP status code 410 Gone with the message: “This API has been deprecated in favor of API v4, available at https://api.cloudflare.com.”
CloudFlare uses Continue reading

Our last DNS meetup was a packed house with Paul Mockapetris, the original inventor of DNS. We learned why DNS answers have a question count but always only one question, why underscores aren’t allowed in domain names, and the history of how DNS came to be.
Our next meetup is with the infamous Dan Kaminsky –– there’s even a DNS attack named after him, the Kaminsky attack. Dan is known for his work finding a core flaw in the Internet, and then leading the charge to repair it. He is an invited expert to the W3C, the guiding organization for the Web, and co-founded the cybersecurity firm White Ops. He is even one of the seven "key shareholders" able to restore the Internet's Domain Name System if necessary.
We’ll cover how Dan discovered the Kaminsky attack, the future of DNS and privacy, how to secure email with DNS, and what are the policy implications of governments allowing DNS blocking. It’s going to be a really great event - we can’t wait to see you there. The meetup is at Gandi’s headquarters: 121 2nd Street, San Francisco at 6PM PST on Tuesday, May 10th, 2016. To claim your spot, Continue reading
Today we're releasing a whole suite of upgrades to page rules: API support, additional settings, pausing a page rule and a mobile-friendly design. Page Rules is the technology that allows you to configure your CloudFlare settings on a per-URL basis. It's often our most powerful feature, enabling CloudFlare domain owners to customize CloudFlare's functionality to exactly match their application's needs.
Page Rules are now fully programmable via API.
$ curl -X POST "https://api.cloudflare.com/client/v4/zones/${ZONE_TAG}/pagerules"
-H "X-Auth-Email: [email protected]"
-H "X-Auth-Key: 000000000000"
-H "Content-Type: application/json"
--data '{
"targets":[{
"target":"url",
"constraint":{
"operator":"matches",
"value":"*example.com/images/*"
}
}],
"actions":[{
"id":"always_online",
"value":"on"
}],
"priority":1,
"status":"active"
}'
Starting today, you can script the creation and modification of page rules. You can integrate page rules into your deployment process to bypass caching on every new API endpoint you ship, or to automatically sync your page rules across your domains on CloudFlare. Check out the page rules API docs and get started today. We can't wait to see what automations you build.
Instead of the short list of settings you could previously toggle, we've added menus with almost every Continue reading
Today we're launching two new features and a brand new dashboard and API for Virtual DNS. Virtual DNS is CloudFlare’s DNS proxy that sits in front of some of the largest hosting providers in the world, shielding their DNS infrastructure from attacks and providing them with the DNS performance benefits of CloudFlare's network and caching.
It's been a year since we launched Virtual DNS, and the service has expanded a lot since then. Virtual DNS now answers 7 billion DNS queries a day, 4.6 billion of which are served from our cache, saving our Virtual DNS customers a collective 65% of their bandwidth. Beyond the bandwidth savings, Virtual DNS also protected its customers from a large vulnerability in BIND when it was discovered in August.
Virtual DNS is different from CloudFlare’s core authoritative DNS service, which comes included in CloudFlare’s standard plans. In authoritative DNS, CloudFlare hosts DNS records for a zone on its own infrastructure. In Virtual DNS, the customer hosts all of the DNS records for all of their zones, and CloudFlare serves as a front end proxy to them.
The new Virtual DNS dashboard makes it fast and easy Continue reading

We like DNS, we think you might too.
CloudFlare and Gandi are hosting a three-part series on DNS. Our first event will be at the CloudFlare office with Paul Mockapetris, the original inventor of the Domain Name System.
Beyond inventing DNS, Paul built the first ever SMTP server. He ran networking at ARPA, served as the chair of the IETF, and is a honored member of the Internet Hall of Fame. He is currently the Chief Scientist at Threatstop, and the visiting scholar at the Universite de Pierre et Marie Curie in Paris.
The event is on Tuesday, April 12th, 2016 at 6 PM PST at our office in San Francisco, 101 Townsend Street (RSVP here). We’ll be covering the early days of DNS, DNS and security, the commercialization of DNS (what Paul famously calls DN$), and the future of DNS.
So come, grab some beer, and hang out with people who like DNS as much as you do.

Yesterday we wrote about the 400 gigabit per second attacks we see on our network.
One way that attackers DDoS websites is by repeatedly doing DNS lookups that have small queries, but large answers. The attackers spoof their IP address so that the DNS answers are sent to the server they are attacking, this is called a reflection attack.
Domains with DNSSEC, because of the size of some responses, are usually ripe for this type of abuse, and many DNS providers struggle to combat DNSSEC-based DDoS attacks. Just last month, Akamai published a report on attacks using DNS lookups against their DNSSEC-signed .gov domains to DDoS other domains. They say they have seen 400 of these attacks since November.
To prevent any domain on CloudFlare being abused for a DNS amplification attack in this way, we took precautions to make sure most DNS answers we send fit in a 512 byte UDP packet, even when the zone is signed with DNSSEC. To do this, we had to be creative in our DNSSEC implementation. We chose a rarely-used-for-DNSSEC signature algorithm and even deprecated a DNS record type along the way.
Dutch mathematician Arjen Lenstra famously talks Continue reading

CloudFlare launched just five years ago with the goal of building a better Internet. That’s why we are excited to announce that beginning today, anyone on CloudFlare can secure their traffic with DNSSEC in just one simple step.
This follows one year after we made SSL available for free, and in one week, more than doubled the size of the encrypted web. Today we will do the same with DNSSEC, and this year, we’ll double the size of the DNSSEC-enabled web, bringing DNSSEC to millions of websites, for free.
If DNS is the phone book of the Internet, DNSSEC is the unspoofable caller ID. DNSSEC ensures that a website’s traffic is safely directed to the correct servers, so that a connection to a website is not intercepted by a man-in-the-middle.
Every website visit begins with a DNS query. When I visit cloudflare.com, my browser first needs to find the IP address:
cloudflare.com. 272 IN A 198.41.215.163
When DNS was invented in 1983, the Internet was used by only a handful of professors and researchers, and no one imagined that there could be foul play. Thus, DNS relies on Continue reading

Since January, CloudFlare has been running a small, private beta for DNSSEC. Starting today, the DNSSEC beta is open for everyone. To request access, email [email protected].
DNS is the system that lets your browser know which web server to connect to when you request to visit a website. It’s the underlying backbone of the usable internet, and yet, is vulnerable to man in the middle attacks.
In DNS, an attacker sitting in the middle of your connection to the internet can tell your browser to connect to any web server they’d like. Browsers trust any DNS records they receive as a response to a DNS query, because DNS, invented in 1983 before the public consumption of the Internet, does not perform any authentication.
There is a solution. It’s called DNSSEC and it adds cryptographic hashes and signatures for authenticating DNS records. You can read more about DNSSEC and how it works in a previous blog post.
The DNSSEC beta is open to all websites that use CloudFlare for DNS. If you want to be a part of our beta and be one of the first CloudFlare websites with DNSSEC, email us for beta Continue reading
Today CloudFlare is introducing a new way to purge the cache using Cache-Tags. Cache-Tags are assigned to cached content via a Cache-Tag response header, and are stored as metadata with cached objects so that global purges take only seconds, targeting a granular, finite set of cached objects.
For example, an e-commerce website can use Cache-Tags to purge all of their catalog images at once, without affecting any of their other assets. A blog can use Cache-Tags to update their JavaScript files in cache, without forcing a cache miss on their CSS. A business can use Cache-Tags to purge cache of all four hundred pages of their blog without purging any of the pages from their core platform.
With 42 data centers around the world, web pages served directly from CloudFlare’s cache are guaranteed to be just a few hops away from any visitor, anywhere. With a little bit of fine tuning, many websites succeed in delivering most of their content from cache, saving a majority of bandwidth on their origin servers. One website even managed to reduce their AWS bill by 96% when they started caching assets behind CloudFlare.
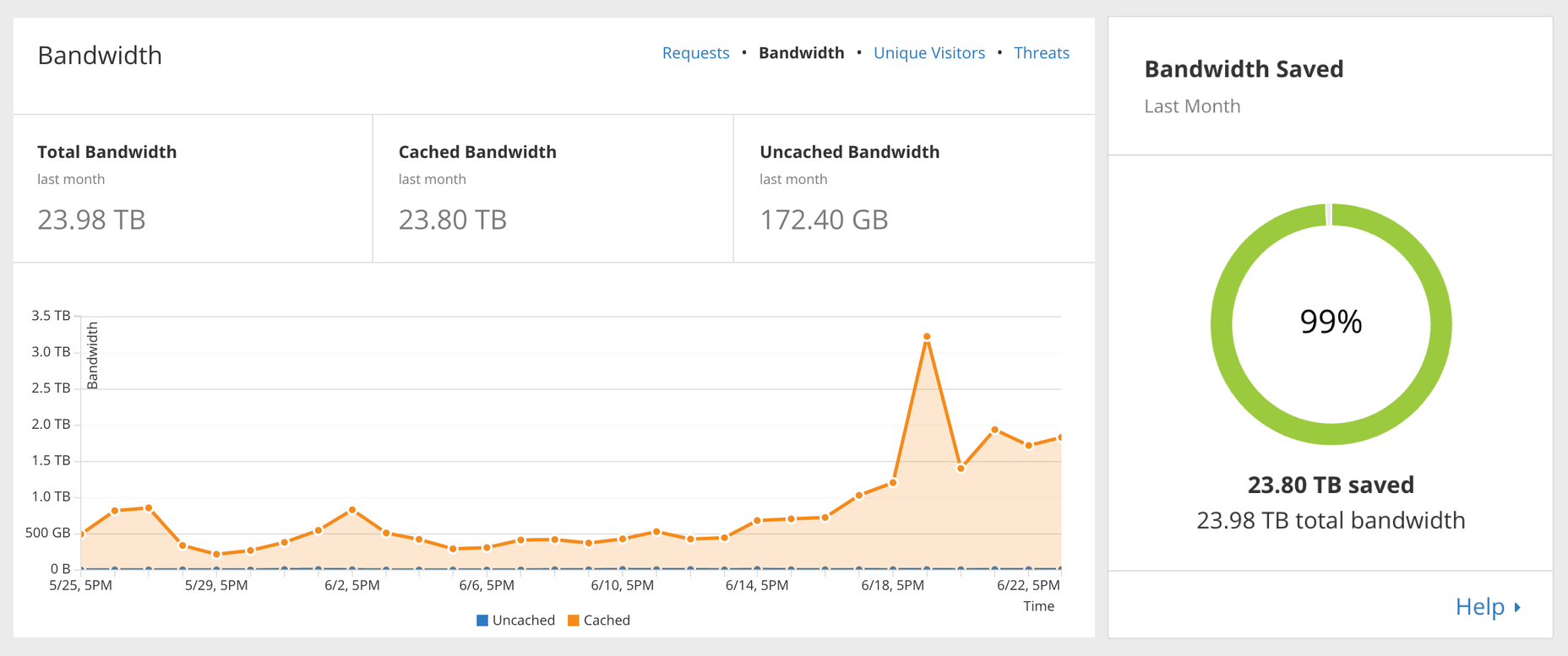
CloudFlare’s cache is powerful, but when a Continue reading
An enterprise needs security and controls around access.
Your web developer needs to update your website’s logo and make sure it’s live immediately, but doesn’t need access to your SSL keys. Your sysadmin manages your DNS, but doesn’t need to see your visitor traffic. Your marketing team needs to see traffic, but shouldn’t have access to your WAF.
Today CloudFlare is introducing new Multi-User functionality so that many members of a team can work together to manage one CloudFlare account, each with different levels of access.
CloudFlare Multi-User accounts are hierarchical, with the root privileges given to the account’s Super Administrator. The Super Administrator can add or delete users in the organization, change the permissions given to each user, and see and edit all CloudFlare settings. If there is more than one Super Administrator, the Super Administrators can remove each other, which is good practice when an employee leaves the company or switches jobs.
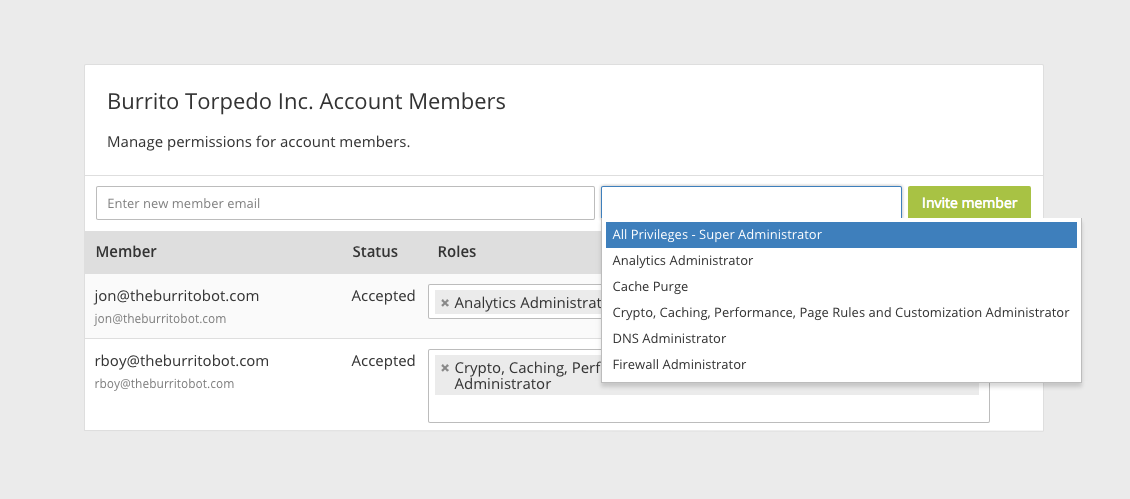
When a user joins a multi-user organization on CloudFlare, they can only see and access the settings that a Super Admin has delegated to them. For example, a user added to the organization as a DNS Administrator would only be Continue reading
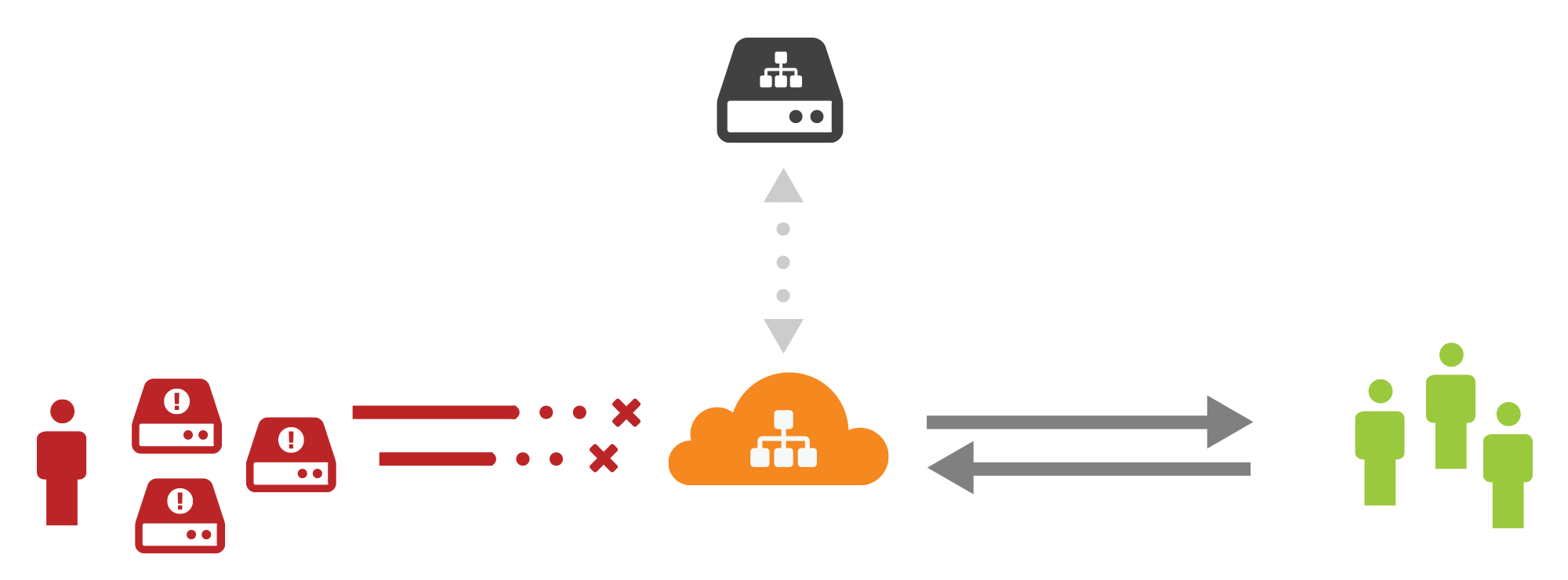
It’s 9am and CloudFlare has already mitigated three billion malicious requests for our customers today. Six out of every one hundred requests we see is malicious, and increasingly, more of that is targeting DNS nameservers.
DNS is the phone book of the Internet and fundamental to the usability of the web, but is also a serious weak link in Internet security. One of the ways CloudFlare is trying to make DNS more secure is by implementing DNSSEC, cryptographic authentication for DNS responses. Another way is Virtual DNS, the authoritative DNS proxy service we are introducing today.
Virtual DNS provides CloudFlare’s DDoS mitigation and global distribution to DNS nameservers. DNS operators need performant, resilient infrastructure, and we are offering ours, the fastest of any providers, to any organization’s DNS servers.
Many organizations have legacy DNS infrastructure that is difficult to change. The hosting industry is a key example of this. A host may have given thousands of clients a set of nameservers but now realize that they don't have the performance or defensibility that their clients need.
Virtual DNS means that the host can get the benefits of a global, modern DNS infrastructure without having to contact every customer Continue reading