Author Archives: jac
Author Archives: jac
As a warning to everyone, I am not a developer. I am a network engineer who is trying to do some automation stuff. Some of what I’m doing sounds logical to me, but I would not trust my own opinions for production work. I’m sure you can find a Slack channel or Mastodon instance with people who can tell you how to do things properly.
The last time, I talked about using pynetbox to make queries to Netbox. This was a very simple example, and one of the things that bugged me the most about it was the API token. In that post, we used a statically-assigned API token where I went into the Netbox GUI and generated one for myself. I think I may have even noted that this was definitely not the best way to handle those things. A possibly-better way to do it is to use your username and password on Netbox to generate a token for yourself. This would a token that you then delete when you’re done.
How is this better? The static tokens are just that — they’re static. If you generate your token, then anyone who has it can use it to Continue reading
As a warning to everyone, I am not a developer. I am a network engineer who is trying to do some automation stuff. Some of what I’m doing sounds logical to me, but I would not trust my own opinions for production work. I’m sure you can find a Slack channel or Mastodon instance with people who can tell you how to do things properly.
The last time, I talked about using pynetbox to make queries to Netbox. This was a very simple example, and one of the things that bugged me the most about it was the API token. In that post, we used a statically-assigned API token where I went into the Netbox GUI and generated one for myself. I think I may have even noted that this was definitely not the best way to handle those things. A possibly-better way to do it is to use your username and password on Netbox to generate a token for yourself. This would a token that you then delete when you’re done.
How is this better? The static tokens are just that — they’re static. If you generate your token, then anyone who has it can use it to Continue reading
You should be using Netbox or something equivalent. I’m serious. Stop documenting your network with Word docs and Wiki pages and use something where the information can be queried. I’ve been using Netbox for a couple years, and it’s where I keep all that important information about my network. I use it to store hardware inventory, circuit inventory, contact information, site information…all sorts of stuff. Since all this information is already recorded there, I can just query it for the information I need. That includes any time I need to write some Python code to do something on the gear. I use the pynetbox module to do that.
To use pynetbox (or anything that uses API calls to Netbox), you’ll need to set up an API token. I am not qualified to tell you what the best way to manage these are, so we’re just going to assume you have an appropriate token configured already.
We’re going to write a short script to get all the devices from the Netbox instance…and here it is!1
import pynetbox
import urllib3
NETBOX_SERVER = "*.*.*.*"
NETBOX_API_KEY = "742*****"
nb_conn = pynetbox.api(url=f"https://{NETBOX_SERVER}", token=NETBOX_API_KEY)
nb_conn.http_session.verify = Continue readingYou should be using Netbox or something equivalent. I’m serious. Stop documenting your network with Word docs and Wiki pages and use something where the information can be queried. I’ve been using Netbox for a couple years, and it’s where I keep all that important information about my network. I use it to store hardware inventory, circuit inventory, contact information, site information…all sorts of stuff. Since all this information is already recorded there, I can just query it for the information I need. That includes any time I need to write some Python code to do something on the gear. I use the pynetbox module to do that.
To use pynetbox (or anything that uses API calls to Netbox), you’ll need to set up an API token. I am not qualified to tell you what the best way to manage these are, so we’re just going to assume you have an appropriate token configured already.
We’re going to write a short script to get all the devices from the Netbox instance…and here it is!1
import pynetbox
import urllib3
NETBOX_SERVER = "*.*.*.*"
NETBOX_API_KEY = "742*****"
nb_conn = pynetbox.api(url=f"https://{NETBOX_SERVER}", token=NETBOX_API_KEY)
nb_conn.http_session.verify = Continue readingI’ve been using Netbox for a while now, and, frankly, I can’t live without it. If you’ve never heard of it, it’s a Source of Truth for your network automation tasks started by Jeremy Stretch. I use it to document my networks (hardware inventory, subnets, physical connections, etc.), which provides my automation tasks a place to pull and push all sorts of information like management IPs, rack locations, power connections, network drops…the list goes on. In better words, your automation tools can ask Netbox what the state of your network is, and send it an update if that tool discovers something different. There are plenty of better places to discuss the benefits of a Souce of Truth, so just do the Googles for it.
My production instance is running Netbox 2.7.6, which is very old. The latest version of Netbox as of today is 3.3.7, so that should tell you how far behind we are. I’ve had mine running for over two years, and, in the meantime, the world has moved forward. If I update the server it’s running on (Ubuntu 20.04), then Netbox breaks. Yes, it’s so far behind Continue reading
I’ve never done a post on Forti-anything, but I’m really appreciating the products Fortinet is putting out lately. They’re transitioning from “run your SMB off of our stuff” to “actually, we’re pretty good for larger companies”, so their GUI lacks features to keep the SMB from blowing stuff up, The advanced features are there in the CLI, and I wanted to use it to show that difference between the GUI and the real config.
Let’s review some of the basic configuration elements of BGP first. You need an autonomous system (AS) number and a router ID for your side. You also need the AS number of the remote system. You need the IP address on their side (usually the interface facing you). That looks something like this. We’re going to be ‘Fortigate 1’ for this exercise.
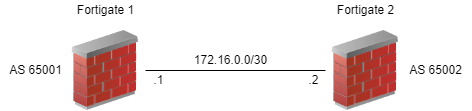
With just this information, we can turn up a BGP neighbor that does absolutely nothing. To actually send some routes, you need to tell BGP what to send. We’ll keep this simple and add just connected networks. Adding to the diagram, we get this.
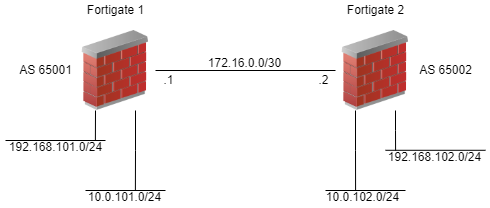
Now we have something of value (though choosing BGP over OSPF or RIP for this little scenario is pretty horrible). Continue reading
I was lucky enough to have been invited to attend Network Field Day 29 this past September in San Jose, CA. This event brings independent thought leaders together with a number of IT product vendors to share information and opinions. We saw presentations from a pretty full range of vendors — from the chips to observability. It was a great event and worth a few hours to check out the videos. Thanks to Gestalt IT for getting me involved.
Nokia was among the list of high-end companies we saw. No, they don’t make phones any more (though they do market their name to products), but they are still in the full-power, throw-packets-as-fast-as-you-can markets for hyperscalers and such. If you’re old like I am, you might remember Nokia as the hardware that Checkpoint ran on for a while. My brain has done its best to filter memories of those devices, but, luckily, the Nokia team is doing some much better things these days.
SR Linux was one of the focuses and the big hitter for me. This is a modernization of the SR OS that was introduced 20 years or so ago, and gets us into a “world of streaming telemetry. Continue reading