Author Archives: packetmischief.ca
Author Archives: packetmischief.ca

The architecture of the infrastructure-as-code (IaC) tooling you use will determine the level to which your IaC definitions are exposed to bit rot.
This is a maxim I have arrived at after working with multiple IaC tool sets, both professionally and personally, over the last few years. In this blog post, I will explain how I arrived at this maxim by describing three architectural patterns for IaC tools, each with differing levels of risk for bit rot.

The AWS CLI is a tool set that lets you manage your AWS resources. The CLI comes in two versions which, at the time of this writing, are developed concurrently: version 1 and version 2.
Internally, the AWS CLIv1 and v2 are quite different. Version 2 pulls in AWS libraries--libraries which are used across the AWS SDK ecosystem--rather than reinventing the wheel when it comes to common tasks, such as talking to Amazon S3. Running AWS CLIv2 on your operating system of choice requires building and installing these common AWS libraries.
I contributed changes to s2n-tls, aws-lc, the Python runtime, some build tooling, and various other libraries. As a result, the AWS CLIv2 now builds and runs on OpenBSD.
To make installation simple, I've created an OpenBSD port for CLIv2 and its dependencies. Instructions for installing the port are below.

"Software is eating the world." Have truer words ever been spoken other than these words by Marc Andreessen?
I've recently been immersed in a number of home automation projects (lights, heating/cooling, presence detection, and more). I was reflecting on what made all of these automations possible: the drastic increase in the amount of software present in the home. As I was reflecting on this, I realized how different my house is in this respect compared to the house I grew up in.
Now, I'm not saying I'm old. More like, the rate of digitization in the world around us has happened at such a pace that even in my short lifetime, the changes have been deep and wide.
This blog post is a tour of things in my house that are software operated that were not software operated in the house I grew up in. For my purposes here, I define "software operated" as any device that has software or firmware that is upgradable either by me or through an over-the-air process that the device or its cloud service initiates. I'm leaving out "obvious" items like laptops, tablets, and mobile phones.

When you assign an Identity and Access Management (IAM) role to an Amazon
Elastic Compute Cloud (EC2) instance, the short-term credentials for the role
are made available via a web service known as the
Instance Metadata Service (IMDS).
The IMDS provides an HTTP endpoint for retrieving instance metadata
such as the instance IP address, AWS Region the instance is running in, the
Amazon Machine Image used to launch the instance, and the access key, secret
access key, and session token associated with the instance's IAM role. The AWS
documentation describes how to
retrieve instance role credentials
from IMDS. If you've seen or used the http://169.254.169.254 or
http://fd00:ec2::254 endpoints, then you've seen/used IMDS.
Retrieval of instance role credentials from IMDS is the mechanism by which the AWS CLI and SDKs learn the credentials belonging to the instance's IAM role without you having to configure anything on the instance. Quoting the IAM documentation:
The AWS SDKs, AWS CLI, and Tools for Windows PowerShell automatically get the credentials from the EC2 Instance Metadata Service (IMDS) and use them.
This is great! It means you can start using the AWS CLI, SDKs, or Tools Continue reading

Passwords suffer from an inherent risk: whoever possess the password inherits the privileges granted by that password. If the possessor is the intended person, then all is good. Otherwise, all is not so good because it means an unintended person has access to the system the password is guarding.
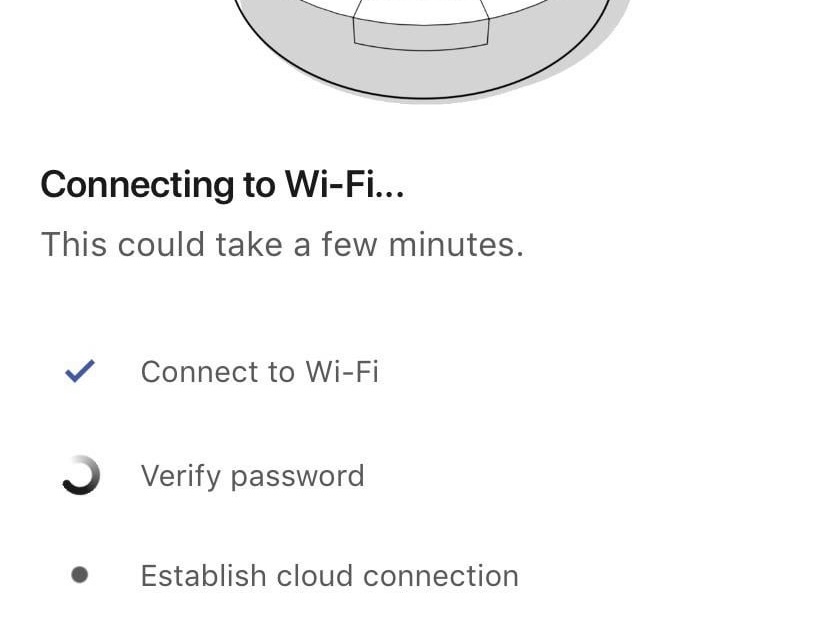
You have:
Verify password when setting up the Roomba.
A colleague of mine recently quiped, "'The perimeter' in AWS is actually defined by Identity and Access Management (IAM)." After some reflection, I think my colleague is spot on.

This is a retelling of a presentation I gave at work. In it, I describe a mechanism I've started using to raise the quality of artifacts I check into version control.

I've written before about how I use MediaWiki for taking notes and as one of my study tools. This has worked well for many years. But a problem started to develop: while I wrote my technical notes in MediaWiki, I wrote my day-to-day notes (books I want to read, notes from podcasts I listen to, and even my weekly planner) in Notion. This meant I had to use different apps for reading/writing in each tool, remember two different markup languages, and couldn't (cleanly) link pieces of content between the two. The final straw was realizing how much more effort I had to expend to maintain my MediaWiki instance; I just didn't have the time or will to keep up with new releases not to mention maintain the server itself.
For these reasons, I decided to move all of my MediaWiki content to Notion and unify all of my notes. But this revealed a new problem: there was no tooling to automate this. So I created my own. Here's how it works.

A friend of mine recently had a solar panel system installed on his acreage. Besides being interesting because of the renewable/green aspect of the project, the system itself—from SolarEdge—is actually highly digital.
The last point interested me the most because any time a device exposes its data or a control connection, it means there’s an opportunity to integrate it with other software. In this case, I wanted to create my own dashboard to display (near) real-time performance data for the system.
Whereas other blogs and articles on this topic describe how to monitor a single inverter system, this post will describe how I built a performance dashboard for a multi-inverter system.
In a throwback to the problems I dealt with using AirPlay across VLANs, I recently jumped through similar hoops for Sonos speakers. There are many forum and blog posts out there that describe (or attempt to describe) how to make this work, however all of the ones I read suffered from one or both of these problems:
This post will dive deep on what's happening on the wire when a Sonos controller (eg, your mobile phone running the Sonos app) tries to talk with the players (the speakers) on the network. The focus will be how to make this process work when those two devices are in different VLANs.
What you read below works successfully with Sonos Beam, Sonos Sub, and Sonos Move using the Sonos S1 app.
The AWS Cloud Development Kit (CDK) is an "open source software development framework to define your cloud application resources using familiar programming languages". When CDK launched in 2019, I remember reading the announcement and thinking, "Ok, AWS wants their own Terraform-esque tool. No surprise given how popular Terraform is." Months later, my friend and colleague Matt M. was telling me how he was using CDK in a project he was working on and how crazy cool it was.
I finally decided to give CDK a go for one of my projects. Here is what I discovered.
This article was originally posted on the Amazon Web Services Security Blog.
AWS CloudFormation is a service that lets you create a collection of related Amazon Web Services and third-party resources and provision them in an orderly and predictable fashion. A typical access control pattern is to delegate permissions for users to interact with CloudFormation and remove or limit their permissions to provision resources directly. You can grant the AWS CloudFormation service permission to create resources by creating a role that the user passes to CloudFormation when a stack or stack set is created. This can be used to ensure that only pre-authorized services and resources are provisioned in your AWS account. In this post, I show you how to conform to the principle of least privilege while still allowing users to use CloudFormation to create the resources they need.
I have a cron job that renews an SSL
certificate from Let's
Encrypt, and then restarts the smtpd daemon so that the new certificate is
picked up. This all works fine--as proven by both the presence of a new, valid
cert on disk, and smtpd successfully restarting--but cron never sends an email
with the output of the job. What gives?
This is a running list of unusual data found in the Domain Name System.
Typically, DNS stores name-to-IP (for example, foo.example.net -> 192.0.2.123) and IP-to-name mappings (i.e., the inverse). But, the
DNS is arguably the biggest, most distributed key/value store on the planet,
making it a great place to stash all kinds of simple data.
For years now I've had a light switch that can be programmed to turn itself on/off on a schedule. The switch is programmed with the date, time, time zone, and lat/long and then you can create a schedule such as, "turn the lights on at sun set". It works pretty well except when 1/ daylight savings time starts or stops (the schedule doesn't adjust itself) or 2/ the power goes out (bye, bye all programming).
This slight annoyance coupled with my desire for a project I could geek out on lead me to look into software-controllable light switches.
In this post I'll explain how I flashed the open source Tasmota firmware onto the Treatlife 3-way wall switch which in the end allowed me to control the lights via a home automation controller.
AWS Serverless Application Model (SAM) is a framework for building serverless applications on AWS. One of the components of SAM is a template specification. SAM templates would look and feel familiar to anyone who has used AWS CloudFormation to define their infrastructure as code, however they are not completely interchangeable. There are multiple reasons why you might want to convert from SAM to native CloudFormation:
AWS::Serverless
transform
in its templates and transforms are not supported by stack sets.This post will show you how to take an existing SAM application and convert it to a CloudFormation template (CFT). As a CFT, the challenges listed above can be avoided.
This article was originally posted on the Amazon Web Services Architecture blog.
In a recent customer engagement, Quantiphi, Inc., a member of the Amazon Web Services Partner Network, built a solution capable of pre-processing tens of millions of PDF documents before sending them for inference by a machine learning (ML) model. While the customer's use case--and hence the ML model--was very specific to their needs, the pipeline that does the pre-processing of documents is reusable for a wide array of document processing workloads. This post will walk you through the pre-processing pipeline architecture.
I recently used AWS DataSync as part of a lab I was building. These are my notes for using DataSync to replicate an Amazon Elastic File System (EFS) share from one region to another.
AWS DataSync is a managed service that enables replication of data between AWS services and from on-prem to AWS. It automates the scheduling of transfer activities, validates copied data, and uses a purpose-built network protocol and multi-threaded architecture to achieve very high efficiency on the wire.
The use case I needed to tackle was replicating an Amazon EFS share in one region to an EFS share in a different region (a one-way replication). (DataSync can also connect to Amazon S3 and Amazon FSx for Windows File Server)