Author Archives: packetmischief.ca
Author Archives: packetmischief.ca
How to Call REST APIs from a REST Client and Python
Presenter: Matt (didn't catch last name, sorry)

Presenter: Konrad Reszka, IoT Vertical Solutions Group Engineering Lead

“Given a chance, how many people in this room would volunteer to be a meteorologist in San Diego? You'd never be wrong!”
Presenter: Jeff Schutt - Cybersecurity Solutions Architect (Jeff works in Adv Services in the IoT team)
Full Title: An IoT Security Model & Architecture for Securing Cyber-Physical and IT-OT Converged Assets

Mix of IT/OT folks in the room.
I'm lucky enough to be heading to Cisco Live in San Diego this year to host customers from my area. When I'm not with a customer during the day I plan on attending these sessions:
I like MPLS. And I don't necessarily mean as a solution to solve a problem, but as something to configure in the lab. It's fun to build things that do something when you're done. Setting up OSPF or EIGRP and being able to traceroute across routers is meh. But configuring MPLS with all the associated technologies — an IGP, LDP, MP-BGP, — and then getting all of them working in unison… when you get the traceroute working, it's rewarding.
Here's something to keep an eye out for when you're troubleshooting MPLS: An LFIB entry (that is, the Label Forwarding Information Base) that states “No Label” versus one that states “Pop Label”. These mean very different things and can be the difference between a working Label Switched Path (LSP) and a non-working LSP.
Think about this for a minute: An MPLS network with a two Provider Edge (PE) routers and some Provider (P) routers. The P routers have no VRFs configured on them and therefore have no routes whatsoever for any of the customer networks. A customer then does a traceroute from one of their sites, across the MPLS cloud, and into one of their other sites. The traceroute output shows the P routers as hops along the path.
How is it possible for the P routers to reply to the traceroute if they don't have routes back to the customer network?
Normally for these FFF articles I've taken to writing about new protocols as a way of introducing others to it and also edumacating myself about it. For this post I get all nostalgic and look at good old Enhanced Interior Gateway Routing Protocol (EIGRP).
Let's take a look at EIGRP and the state a route can get into where EIGRP tells you “FD is Infinity”.
The worst feeling for a geek:

Courtesy of xkcd (http://xkcd.com/979/)
This has happened to me twice now: upgrading Mac OS X from one release to another and after the dust settles, the search function in Outlook 2011 totally breaks and always returns “no results”. As we all know, email sucks and being able to deftly search through that mound of crap in your mail client is the only thing that makes it somewhat bearable.
Click to enlarge
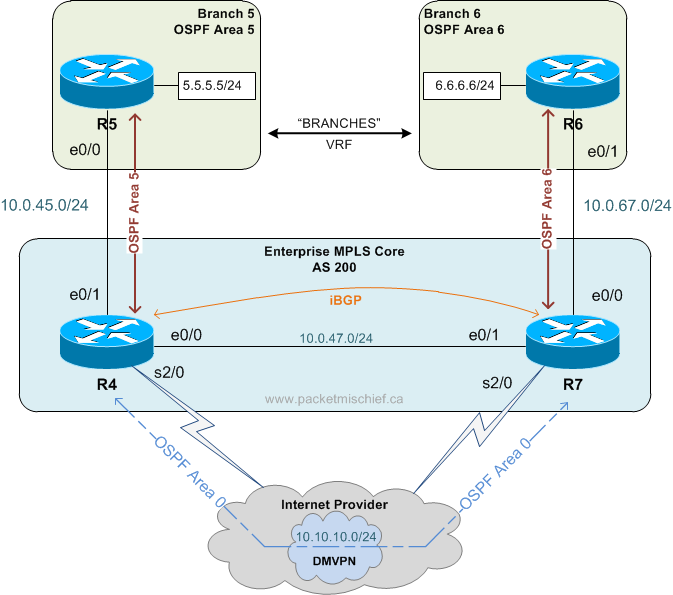
Here's the scenario: An enterprise network with an MPLS core and two branch locations connected to their own Provider Edge (PE) router. In addition to the MPLS link, the PEs are also connected via a DMVPN tunnel. The PEs are peering via iBGP (of course) and are also OSPF neighbors on the DMVPN. Both Customer Edge (CE) routers at the branch are OSPF neighbors with their local PE.
Task: Use the high speed MPLS network as the primary path between the CE routers and only use the DMVPN network if the MPLS network becomes unavailable.
Question: Is the solution as simple as adjusting the Admin Distance (AD) so that the iBGP routes are more preferred?
In Cisco IOS packets are forwarded through the router (or Layer 3 switch) by Cisco Express Forwarding (CEF). A data structure called the CEF table contains a list of known IP prefixes and the outgoing interface that packets should be put on in order to get them onwards to their destination. That's well and good. But how do the IP prefixes make it into the CEF table? To answer that question you have to work backwards and understand the order of operations that IOS goes through in order for a prefix to make it into the CEF table.
I don't believe this is well known: Cisco IOS has Role Based Access Control (RBAC) which can be used to create and assign different levels of privileged access to the device. Without RBAC there are two access levels in IOS: a read-only mode with limited access to commands and no ability to modify the running config (also called privilege level 1) and enable mode with full administrative access. There is no middle ground; it's all or nothing. RBAC allows creation of access levels somewhere between nothing and everything. A common use case is creating a role for the first line NOC analyst which might allow them to view the running config, configure interfaces, and configure named access-lists.
If you've ever done a traceroute from one IOS box to another, you've undoubtedly seen output like this:
R8# traceroute 192.168.100.7
Tracing the route to 192.168.100.7
VRF info: (vrf in name/id, vrf out name/id)
1 192.168.0.1 4 msec 3 msec 4 msec
2 192.168.100.7 4 msec * 0 msec
That msec * msec output. Why is the middle packet always lost?? And why only on the last hop??
This is a quick calculator I came up that I could use in the CCIE lab to translate between various IPv4 header QoS markings. As long as I could remember how to draw out the calculator, all I had to do was some basic math and I could translate between markings quite easily.
When I started studying in earnest for my CCIE, I started a log of how I was spending my time studying, which books and papers I'd read, videos I'd watched, and so on. I thought it would be a neat exercise to look back afterwards at what it took to achieve this goal. I'm also somewhat self-deprecating and tend to minimize my accomplishments, so having this data is a way for me to remember that this wasn't a small accomplishment at all.
Although I wasn't actively blogging this year, I've still been tracking views on the site and keeping an eye on number of visitors. I am looking forward to blogging again in 2015 so I wanted to collect the 2014 viewership statistics so I had something to compare to at the end of 2015.
Despite the lack of new content, I'm pretty happy that people are reading the existing articles and continue to post comments and email me questions. Please keep them coming!
I debated whether to write an article like this. It seems to be the “in vogue” thing to do if you're a blog author but I wasn't inclined to do it until I started looking at the data (I heart data). When I started looking at the data, I saw not only number of visitors and so on to the blog, but a breakdown of browser versions and operating systems (thank you Google Analytics for the rich reports). As is often the case, your data set can tell you more than you initially bargained on.
I was preparing a presentation the other day about the high level differences between IOS, IOS-XE and NX-OS and one of the things I included in the presentation was the various platform and branch identifiers that's used in each OS. It's just a bit of trivia that I thought would be interesting and might come in handy one day. I'm posting the information I collected below so everyone can reference it.