Author Archives: Suresh Vina
Author Archives: Suresh Vina

I’m going to start by saying I’m totally new to LLMs and running them locally, so I’m not going to pretend like I know what I am doing. I’ve been learning about Ollama for some time now and thought I would share it with my readers as always. This is such an interesting topic and I’m ready to go into the rabbit hole.
As always, if you find the content useful, don’t forget to press the ‘clap’ button to your left. This is one way for me to know that you like this type of content, which means a lot to me. So, let's get started.
LLMs, or Large Language Models, are a type of artificial intelligence designed to process and generate natural language. They are trained on vast amounts of text data, enabling them to understand context, identify patterns, and produce human-like responses. These models can perform various tasks such as answering questions, translating languages, summarising text, generating creative content, and assisting with coding. LLMs have gained significant attention in recent years due to their impressive performance and versatility.

Let me start by saying that I usually run Containerlab on a dedicated Ubuntu 22.04 VM, which sits on top of Proxmox. All my labs run on this setup. However, I recently wanted to try running Containerlab directly on my MacBook (M3 Pro with 18GB of RAM) for a few reasons. For example, I might need to run labs while I’m away, work offline, or use a MacBook at work where I can’t access my home network. So, I decided to test whether I could run Cisco IOL and Arista EOS on macOS. The answer is yes, and here’s how you can do it.
As always, if you find this post helpful, press the ‘clap’ button on the left. It means a lot to me and helps me know you enjoy this type of content.
If you’re new to Containerlab and trying to understand what it is, I highly recommend checking out my introductory post, which is linked below. It covers the basics and will help you get started.

Most websites we access today use HTTPS, and to fully leverage a Next-Generation Firewall (NGFW) like Palo Alto, inspecting encrypted HTTPS sessions is crucial. Configuring SSL decryption isn't just a set-it-and-forget-it task. It requires careful consideration and ongoing improvements. In this blog post, we'll explore how to configure SSL decryption in Palo Alto firewalls and highlight some pitfalls to be aware of. So, let's get to it.
As always, if you find this post helpful, press the ‘clap’ button on the left. It means a lot to me and helps me know you enjoy this type of content.

As I mentioned earlier, configuring SSL decryption isn’t as simple as flipping a switch. Decryption allows your firewall to inspect the contents of encrypted sessions. Normally, HTTPS traffic is encrypted from your browser to the server, ensuring the sessions are private. However, with SSL decryption, the firewall acts as a man-in-the-middle, inspecting the traffic in plain text. It’s crucial Continue reading

If you follow my blogs, you might know that I recently switched to Proxmox from VMware Workstation Pro for my home lab. I’ve already migrated most of my VMs, including Cisco CML, to Proxmox, and the last piece left was EVE-NG. In this blog post, we’ll go through the steps to install EVE-NG in Proxmox. Let’s get started!
As always, if you find this post helpful, press the ‘clap’ button on the left. It means a lot to me and helps me know you enjoy this type of content.

EVE-NG doesn’t have official documentation for Proxmox, but it works perfectly fine, and I haven’t faced any issues so far. For this example, I’m using
Most of the VM’s settings can be left at their default values, but there are a couple of changes I had to make. Before diving in, let's have a quick look at Nested Virtualization.
Nested virtualization allows you to run virtual machines Continue reading

In my previous InfraHub introductory post, we covered installation and the basics of InfraHub. In this second post, let’s explore the ‘Schema Library’ provided by OpsMill, the team behind InfraHub. As mentioned in the previous post, InfraHub doesn’t include any user-defined schemas out of the box, so we need to create our own. However, the Schema Library repository offers a collection of schemas that we can easily import into InfraHub. In this post, we’ll take a closer look at the Schema Library and how to use it.
If you are new to Infrahub and want to learn the basics of what it is and how to install it, feel free to check out my introductory post below.

The way I think about schema is that it is a blueprint that defines the structure of your data. It specifies the nodes (like devices and interfaces), their attributes, and the relationships between them. This allows you to customize how you Continue reading

In my previous blog posts (linked below), we looked at how to allow or block specific websites using URL filtering. In this post, we'll look into how to use URL filtering with SSL decryption for more granular control.


Previously, we saw how to block sites like facebook.com or cnn.com, or allow specific websites blocked by a URL Filtering profile. However, these methods fall short when more granular access is required. Most website traffic today is encrypted with HTTPS, meaning the firewall cannot inspect what's happening within those sessions.
Without SSL decryption, the Palo Alto firewall (or any NGFW) relies on the SNI or CN of the certificate Continue reading

When working with Next-Generation Firewalls (NGFWs), you may come across situations where you need to block specific websites. In this blog post, we'll explore how to block specific sites using a Palo Alto firewall. There are two ways to achieve this, and we'll cover both options.
This blog post assumes you have some familiarity with URL filtering. In a typical setup, you create a URL Filtering profile, configure the categories to allow or block, and attach this profile to your security policies.
Depending on your security requirements, you might block entire categories such as gambling, terrorism, or proxy sites. However, there are times when you only need to block specific sites rather than an entire category.
In this blog post, we'll use cnn.com and samsung.com as examples (no hard feelings toward them, these were just the first sites that came to mind, haha 🙂).

If you use URL filtering on your Palo Alto firewalls, you may come across situations where a specific URL category is set to block, but you need to allow certain sites. For example, you might block the 'social networking' category but still want to allow access to Facebook. Similarly, you may block 'newly registered domains,' but need immediate access to a site categorized as such. While you can request Palo Alto to re-categorize the site, sometimes you need a quicker solution.
In this blog post, we'll look at how to allow access to specific URLs that match a blocked URL category. There are two ways to achieve this, and I’ll cover both.
This blog post assumes you have some familiarity with URL filtering. In a typical setup, you create a URL Filtering profile, configure the categories to allow or block, and attach this profile to your security policies. For instance, if you block the 'proxy-avoidance' category and try to access a site like expressvpn.com, the traffic will be blocked.
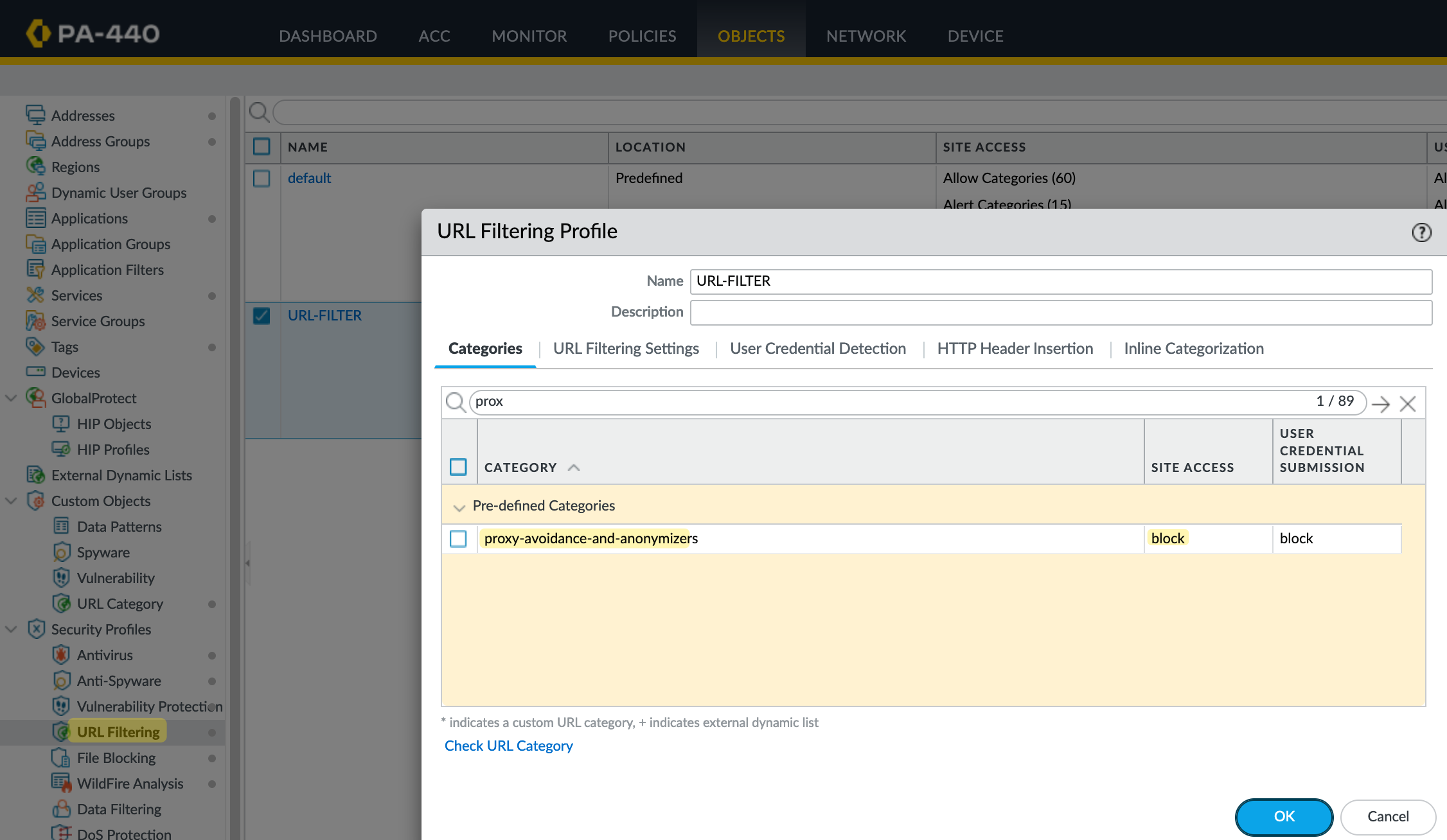
To demonstrate this, I'll set the 'proxy-avoidance' category to block. This means that if I try to access expressvpn.com, it will be blocked. Continue reading

XtendISE is a user-friendly web application integrated with Cisco ISE and designed to simplify daily tasks and common challenges related to 802.1X without requiring extensive training on Cisco ISE. XtendISE helps manage MAC addresses, troubleshoot 802.1X authentication issues, and simplify the management of switch 802.1X configurations. It also validates configurations to ensure they are set up correctly and as intended.
We covered the basics of XtendISE in a previous article linked below. In this blog post, we will explore in detail three key features that XtendISE offers.

Typically, when a device doesn’t support 802.1X, we collect its MAC address and add it to a specific group in Continue reading

For the past few years, I’ve been running all my virtual machines on VMware Workstation Pro, installed on Windows 11. While it worked well for the most part, there were a few recurring issues. Windows would occasionally reboot to install updates, and when it did, my VMs would go down with it. This dependency on Windows to keep my VMs running became frustrating. Recently, I switched to Proxmox, a type-1 hypervisor, and the difference has been night and day.
In this blog post, we'll go through how to install Cisco CML (specifically CML 2.8 Free Tier) on Proxmox. If you're looking to install Cisco CML on VMware Workstation, check out my other blog post linked below.

Head over to the Cisco download page and select CML (2.8 Free Tier). You need a Cisco account, which is easy to create. Once you create the account and log Continue reading

If you're in the Network Automation space or attended one of the last two Autocon events, you might have come across a new tool called 'Infrahub' from OpsMill. I've been keeping an eye on it and experimenting with the product for some time now. In this blog post, we'll cover how to install Infrahub, what it is, and walk through a simple example to get you started. Let's dive in.
Installing Infrahub is straightforward if you're familiar with Docker and have it installed. For this example, I'm using an Ubuntu 22.04 server with Docker and Docker Compose already set up. Here's all I had to do.
suresh@infrahub:~$ git clone https://github.com/opsmill/infrahub.git
Cloning into 'infrahub'...
remote: Enumerating objects: 95389, done.
remote: Counting objects: 100% (5707/5707), done.
remote: Compressing objects: 100% (2801/2801), done.
remote: Total 95389 (delta 3698), reused 4482 (delta 2877), pack-reused 89682
Receiving objects: 100% (95389/95389), 136.18 MiB | 40.26 MiB/s, done.
Resolving deltas: 100% (69451/69451), done.suresh@infrahub:~$ cd infrahub/
suresh@infrahub:~/infrahub$ docker-compose up -d[+] Running 70/7
✔ message-queue 10 layers [⣿⣿⣿⣿⣿⣿⣿⣿⣿⣿] 0B/0B Pulled
✔ task-manager 13 layers Continue reading
Palo Alto firewalls come with a default master key used to encrypt passwords, secrets, and certificates. If your firewall is compromised or someone gains unauthorized access, they can easily decrypt these secrets, posing a significant security risk. In this blog post, let's explore why you should change the master key, important considerations, and how to configure it. Let's get started.
Palo Alto firewalls come with a default master key. Anyone with unauthorized access to the firewall can easily decrypt your secrets or export the configuration to another firewall to retrieve those secrets. For this reason, Palo Alto strongly recommends changing the master key as soon as possible.
Configuring the master key isn’t something you can just set and forget; it requires careful consideration. Here are some important points to keep in mind.

Auto-tagging allows the firewall to tag a policy object when it receives a log that matches specific criteria, creating an IP-to-tag or user-to-tag mapping. For example, when the firewall generates a traffic or threat log, you can configure it to tag the source IP address or User associated with that log using a specific tag name. These tags can then be used to automatically populate policy objects like Dynamic User Groups or Dynamic Address Groups, which in turn can automate security actions within security policies.
For example, let's say I have a policy that denies traffic from the Internet to the firewall's public IP or subnet whenever someone attempts to access random ports. This policy blocks the traffic and generates a traffic log. Now, if someone tries to target our public IP on port 22 (SSH), we might want to add them to a blacklist, which is a Dynamic Address Group. We can then create another policy that references this Dynamic Address Group to block any further traffic from this IP address.
A realistic use case is when you want to block a source IP after multiple failed authentication attempts to GlobalProtect. Typically, you can use Continue reading

I first came across this on LinkedIn that Cisco is introducing a free tier of their Cisco CML platform (starting from version 2.8). My initial reaction was, 'Cisco giving something away for free? That can't be true!' But it turns out, it is. I couldn't wait to try it. I believe it’s limited to five nodes, but I’ll take it.
I could never justify paying $199 per year when there are free alternatives available (EVE-NG, GNS3, Containerlab). If it were a one-time purchase, I might have gone for it, but $199 every year is just too much for me.
In this post, I'll cover how to get the free version and how to install it on VMware Workstation.
Head over to the Cisco download page and select CML version 2.8 Free Tier. As I mentioned earlier, you need a Cisco account, which is easy to create. Depending on your installation method, you can choose either the bare-metal or OVA Continue reading

The Python Client for eAPI (pyeapi) is a Python library that simplifies working with Arista eAPI, removing the need to deal with the specifics of its implementation. It's straightforward to configure and use. In this blog post, we'll look at how to install pyeapi and go through some examples.
If you're familiar with Arista's eAPI, you know that you can browse to the device's IP in a browser, run commands, and get the output directly. You can also achieve the same result using Python, but it typically requires understanding which libraries to use and how to construct the REST API requests.
However, pyeapi simplifies all of this. You don't need to worry about what's happening behind the scenes. Below is a screenshot of running show vlan command via the REST API, and in the following examples, we'll see how to get the same output using pyeapi.

To install pyeapi, you can use pip, which is the standard package manager for Python. It's a good practice to use a virtual environment (venv) to keep your dependencies isolated and avoid conflicts with other projects. First, create and activate a virtual environment. Once your virtual Continue reading

In this blog post, we will look at how to set up port mirroring on Juniper EX switches. The goal is to mirror all the traffic coming in and going out of one switch port to another port. By doing this, we can connect a laptop to the mirrored port and capture all the traffic. This is particularly useful when you can't directly capture traffic from a device, such as a CCTV camera, TV, or other similar devices. Let's get started.

In this example, we have a database server connected to port ge-1/0/1, and we want to mirror all traffic going in and out of this port to port ge-1/0/4, where our laptop is connected. With this setup, we can use Wireshark on the laptop to capture the mirrored traffic.
configure
edit forwarding-options
edit analyzer my_capture
set input ingress interface ge-1/0/1
set input egress interface ge-1/0/1
set output interface ge-1/0/4
commitThe ingress and egress parts of the configuration refer to the traffic coming into the port (ingress) and leaving the port (egress). Ideally, we want to capture traffic in both directions, but you have the option to mirror traffic in only one direction if needed.
If you Continue reading

We all know that firewalls are limited by hardware resources. Larger devices support higher throughput, while smaller ones may not perform as well. When experiencing slow traffic or latency issues on a firewall, we typically check resource usage and session counts to see if we are reaching these limits. If we are, that often concludes our troubleshooting. But what if we aren't hitting these limits and still experience traffic slowness? In this blog post, we'll explore a few methods to troubleshoot high latency issues on Palo Alto firewalls.
Please note that this troubleshooting is applicable when the dataplane CPU and session count are well below the limit, but you are still experiencing some form of latency issues or random packet loss. If this issue sounds familiar, please continue reading.
If you find yourself in a situation where resource usage is well under the limit but you are still experiencing high latency, the next step is to identify sessions that consume too much of the on-chip packet descriptor.
You can run the following command on any hardware-based firewall model (not a VM-Series firewall) to identify, for each slot and dataplane, the on-chip packet descriptor percentage used, the top Continue reading

Containerlab v0.58.0 supports running Cisco IOL images, which is something I was very much looking forward to. IOL nodes are an implementation of Cisco IOS-XE that does not run as a full virtual machine. Therefore, the IOL nodes generally consume much less CPU and memory.
Containerlab already has great documentation on how to use Cisco IOL devices, but I'll cover it here as well for any of my readers who are interested. You can check out the official documentation for more info.
If you have Cisco CML (you may need version 2.7 or later), it should include the IOL images. You'll need to use vrnetlab to convert the binary file into a Docker container, which can then be used within Containerlab like any other container/image.
First, I have downloaded these two Cisco IOL files to the Downloads folder. One for L3 and another one for L2.
x86_64_crb_linux-adventerprisek9-msx86_64_crb_linux_l2-adventerprisek9-ms.binNext, clone the hellt/vrnetlab repository to your local machine.
git clone https://github.com/hellt/vrnetlab.gitThen, copy these two images into the vrnetlab/cisco/iol directory Continue reading

I currently run multiple Docker containers across two hosts, each hosting various applications on different ports. UniFi Controller exposes the web GUI on 8443, Pi-hole on 8080, and Memos on 5230. Remembering each port number for every application started to become a hassle.
Additionally, most of these applications, like Pi-hole and Memos, do not support HTTPS out of the box. After searching for a solution to simplify this setup, I found that Caddy Reverse Proxy offers one of the simplest and most effective ways to manage these services. In this blog post, we’ll look at how to use Caddy Reverse Proxy with my Docker containers running across two hosts.
A reverse proxy is a server that sits in front of one or more web servers and forwards client requests to them. It acts as an intermediary, handling incoming traffic and distributing it to the appropriate server. This setup can help improve security, manage SSL/TLS encryption, and simplify network traffic management by consolidating multiple services under a single domain.
Caddy is an open-source web server and reverse proxy software that is known for its simplicity and ease of use. It automatically handles HTTPS Continue reading

In this blog post, we will look at how to use Entra-ID SAML SSO with GlobalProtect VPN. This guide assumes you are already familiar with GlobalProtect VPN and have an existing VPN solution with other forms of authentication. If you are new to GlobalProtect VPN, feel free to check out my other blog post, which is linked below.


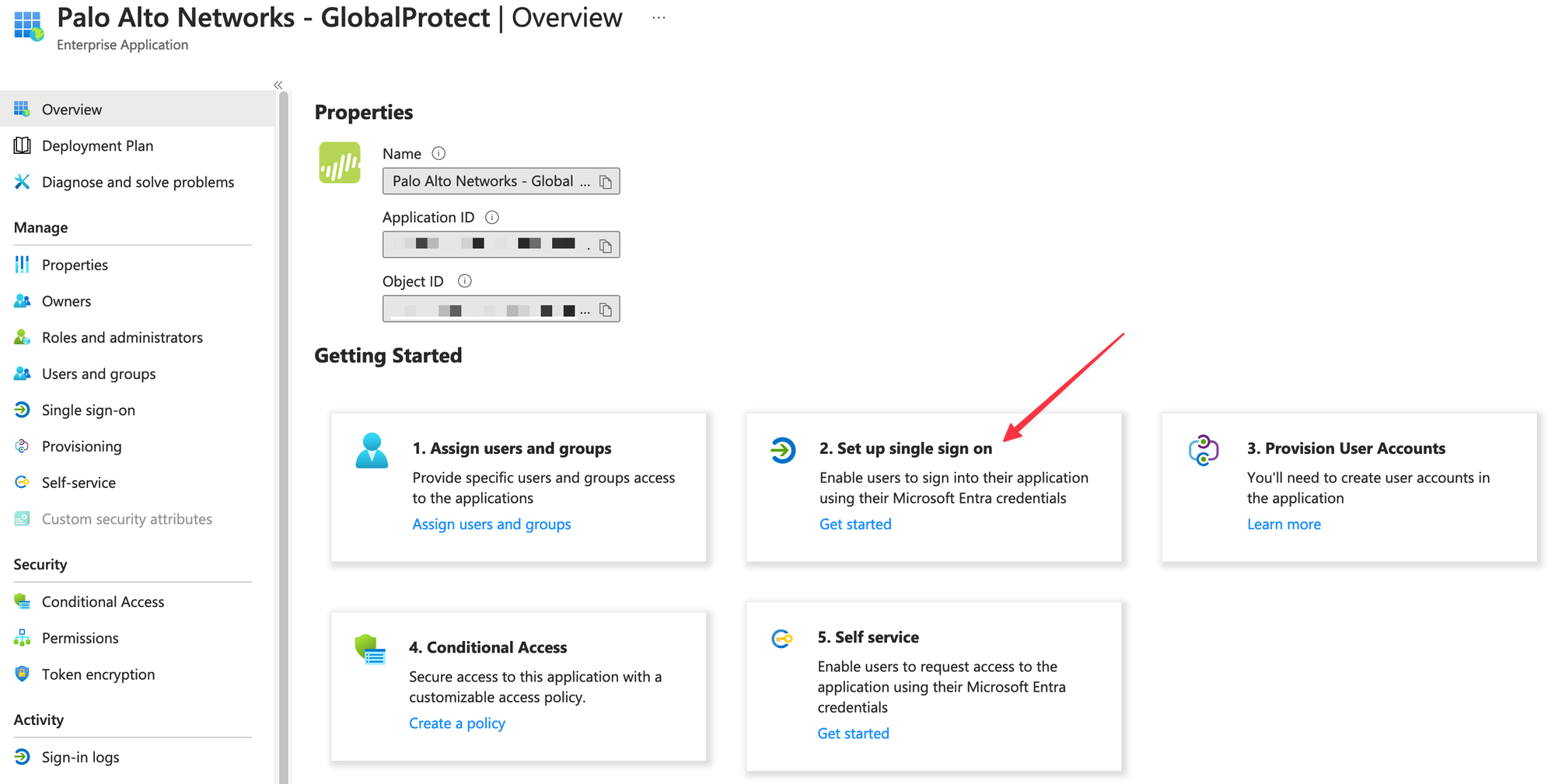
On the Set up single sign-on with SAML page, click the pencil icon in the Basic SAML Configuration section to edit the settings.
:443 after the URL, otherwise, it won't work. I Continue reading