Cisco Live – The Complaints
You should know by now that I always find something to complain about. Is that a bad thing? Probably. Does it help improve things? Absolutely!
Again, I love going to Cisco Live every year. Without question, it’s my favorite event of the year. It’s a great event with great people and great things to do. With that said, let’s look at what could have been a bit better this year.
- Seating – There was a terrible lack of seating around the convention center this year. I spent a good part of the time standing around when I wasn’t in a session, which is not good for a lazy, fat guy like me. We’re talking standing for 5 days here. In the past, there have been plenty of places to sit throughout the event, so I don’t really know what happened here.
- Logistics at the CAE – This happens every year. You’re told to go in one gate at the CAE, but no one listens or your information is wrong; you wind up standing in line behind 18849298 people who were all behind you at one point. Then you have to get your bag searched. Then they take half your swag Continue reading
Cisco Live 2015 – Helping Others
Another year, another Cisco Live. Boy, was it a good one. San Diego is a great city, and convention center there is plenty big to take care of all 25k attendees. On top of that, the city itself is equipped to handle groups of 40 roaming the streets looking for food and entertainment.
This year’s event had the usual stuff that everyone talks about – breakout session, keynotes, exams, etc. – but Cisco stepped outside of technology this year by helping others.
- Stop Hunger Now Volunteer Space – Cisco partnered with Stop Hunger Now and set up a space where attendees could assemble meal kits to fight hunger worldwide. I believe the final number was 100,656 kits assembled, which is a fantastic number. I’m ashamed to say, though, that I missed this due to scheduling issues, but I’m proud of Cisco and the attendees for participating.
- Mike Rowe Works Foundation – The keynote speaker this year was Mike Rowe, whom most of us know from his TV show Dirty Jobs. His foundation helps to support skilled labor movements in order to keep all jobs meaningful. As part of his appearance, Cisco gave his foundation a nice check for $20,000 and promised another Continue reading
FEMA and Your Business Continuity Plan
I passed the ROUTE exam a few days/weeks/months/something ago and decided to pursue certifications of another sort for a while. The wife and I are trying our best to help the community through our ham radio training, so I decided to go down that path a bit further. One thing I was interested in doing is to do EmComm during declared emergencies. That meant I had to take two FEMA courses online to be allowed in the EOC. I thought they would be terribly boring, but I found them to be quite familiar.
The first course was on the Incident Command System (ICS). The main idea is that, in the event of an emergency of any kind or size, an Incident Commander (IC) is assigned to be responsible for the recovery effort. This mean analysis of the incident, generating an action plan (a very key component), and execution of said plan. If the IC can complete the action plan by himself, then off he goes. If he or she needs some additional resources like people or equipment, then he or she is empowered to draft that help from any entity that’s involved.
Another one of the big points of ICS is Continue reading
Summary Post – Methods to Manipulate OSPF Costs
There are three ways to manipulate the interface cost in OSPF. One is very direct, one changes the presentation of the interface, and the other changes the calculations for every interface.
Set the cost of the interface directly – Just give it the number you want. Easy. This is the number OSPF will use in the SPF calculations without doing any math on the interface.
R1(config-if)#ip ospf cost 8482
Set the bandwidth of the interface – The formula that OSPF uses to calculate interface cost is pretty easy to remember – (reference bandwidth) / (interface bandwidth). Changing the interface bandwidth will obviously change the result of the calculation. The same caveat for EIGRP route manipulation holds true here; if you change the bandwidth of the interface, you may affect other things like QoS…or EIGRP, now that I mention it.
R1#sh ip ospf inter brief Interface PID Area IP Address/Mask Cost State Nbrs F/C Fa0/0 1 0 192.0.2.1/24 10 DR 0/0 R1#conf t Enter configuration commands, one per line. End with CNTL/Z. R1(config)#int f0/0 R1(config-if)#bandwidth 10 R1(config-if)#do show ip ospf interf brief Interface PID Area IP Address/Mask Cost State Nbrs F/C Fa0/0 1 0 192.0.2.1/24 Continue reading
Summary Post – OSPF Network Statement Order and Matching
When you configure OSPF network statements, IOS orders them most-specific to least-specific then does a top-to-bottom match of the interfaces. It doesn’t matter which order you put them in, the configuration will always be ordered with the longest prefix matches first. Lab time!
I have router R1 with these interfaces.
R1#sh ip int brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 10.0.0.1 YES manual up up FastEthernet0/1 unassigned YES unset administratively down down Loopback100 10.0.101.1 YES manual up up Loopback200 10.2.101.1 YES manual up up
Let’s add the OSPF configuration where 10.0.0.0/8 is in area 2 then check what OSPF thinks is happening.
R1(config)#router ospf 1 R1(config-router)#network 10.0.0.0 0.255.255.255 area 2 ... R1#show ip ospf interface brief Interface PID Area IP Address/Mask Cost State Nbrs F/C Lo100 1 2 10.0.101.1/24 1 LOOP 0/0 Lo200 1 2 10.2.101.1/24 1 LOOP 0/0 Fa0/0 1 2 10.0.0.1/24 10 WAIT 0/0
All the interfaces are in area 2 as expected. Now let’s add 10.0.0.0/16 into area 1 to see what happens.
R1(config-router)#network 10.0.0.0 Continue reading
Advertising a Default Route Into EIGRP
Let’s get an IPv4 default route into EIGRP. There are a few methods to do it. I hate most of them, though. I think it will be obvious which one I like.
Here’s the lab I have set up to test everything. I want R4 to generate the default in each case.
Default Network – Candidate default. I don’t think I’ve ever used that all my years in networking, but here’s how to use it in EIGRP for a default route. You basically say “If you don’t know where to send a packet, send it to where network X lives.” We’re going to set the 192.168.1.0/24 as the default network, so, in our case X = 192.168.1.0. R4 will tag that route as a default candidate when it advertises it to the rest of the network. The config is easy but requires a stateful (yes, stateful) network to beconfigured as the default.
R4 config: R4(config)#ip default-network 192.168.1.0 ! R1 routes: R1#sh ip route ... 4.0.0.0/24 is subnetted, 1 subnets D 4.4.4.0 [90/435200] via 192.0.2.3, 00:08:33, FastEthernet0/0 [90/435200] via 192.0.2.2, Continue reading
EIGRP and OSPF – Are We Connected?
For both OSPF and EIGRP routers to become neighbors, their interface’s primary IP address must be on the same subnet. That statement is true. There is a difference in the definition of “same subnet”, though.
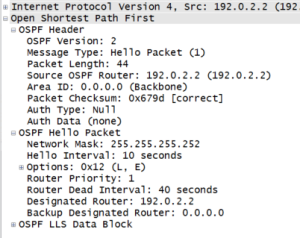
In OSPF, both routers have to be configured to be on the same subnet with the same mask or else they won’t neighbor up. When an hello packet is sent, the subnet mask is sent embedded in there. The router does a quick look to be sure the subnets are defined the same way on both ends. If everything doesn’t match, they don’t neighbor. Here’s a Wireshark screenshot to show you the OSPF hello. Note: See edit below.
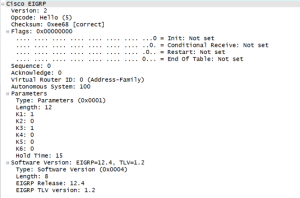
In EIGRP,the subnet mask isn’t sent in the hello packet, so that doesn’t come into play. Each router does a subnet calculation on the source address of the potential suitor, and, if that guy falls within the connected network, the peering magic happens. Here’s another Wireshark shot for you to enjoy.
Send any Wireshark certification vouchers questions my way.
Edit: I did some further research on Julius’s comment about point-to-point links in OSPF. It is absolutely true that point-to-point links do indeed ignore the subnet Continue reading
EIGRP Redistribution – Default Metrics of Connected and Static Routes
I wanted to do some analysis of the EIGRP topology table last night, so I fired up a small lab. I was especially interested in how external routes appear there and compare to internal entries. Like all good scientific endeavors, the whole thing got derailed when I made a realization.
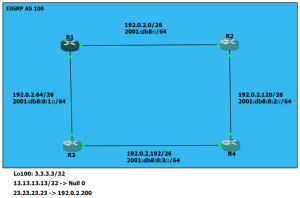
Here’s the lab I set up. You can ignore the IPv6 info for this exercise.
It’s a simple little thing. All the networks you see are included in EIGRP 100 for simplicity. I limited the network statements to 192.0.2.0/24 to keep my options open. I went ahead and added Loopback100 on R3 with an address of 3.3.3.3/32 and added a redistribute connected with a route-map to get the route out in the wild. Here’s what I had.
R3#show run | section eigrp router eigrp 100 redistribute connected route-map RM-REDIST-CONN network 192.0.2.0 no auto-summary ! route-map RM-REDIST-CONN permit 100 match interface Loopback100
Alright. All looks good there, so I checked the topology table on R1 and saw it in there as an external and everything.
R1#sh ip eigrp topology 3.3.3.3/32 IP-EIGRP (AS 100): Topology entry for 3.3.3.3/32 State Continue reading
Recap – Cisco Live US 2014
I don’t think I’m going to give a direct review of Cisco Live US this year. The conference was great with lots of stuff going on, but I really can’t contribute any more than the vast library of other posts on the subject. What I will do, though, is give my take on where I think the conference is headed. These are all my thoughts and have little to do with reality in some cases.
Social Events Passes. My wife had one of these this year, and it worked very well for meatspace networking and seeing the sites. So did Bob. And many others. This was the trendy thing to do this year, and it was successful for sure. I didn’t hear a single “I wish I could have seen that session” at all thanks to everything being available online afterward. Next year, I predict that a good number of attendees in my circles will opt for the cheaper pass; I would say 40% or so of the group will do so. After all, we go to see people and exchange ideas. Traditional learning can come when you get home.
Host City. San Francisco’s a great city (as others say…not me) Continue reading
My Schedule for Cisco Live 2014
Everything is in order for my trip to Cisco Live 2014 in San Francisco. Conference passes are purchased. Hotels are reserved. Flights are booked. It’s going to be a great event, and I can’t wait!
Note: My wife will be with me again this year, and she is trying to get a tour group going to look around the city while others are in sessions. If you want to be in on the tourist action, contact her via Twitter.
As per tradition (a new tradition, but a tradition nonetheless), here is my schedule for the week. Also as tradition, I’m bound to only do about 20% of what’s documented here. If you’ve ever been, you know what I mean. Here we go.
<strong>Saturday, May 17</strong>
<strong>13:00</strong> - Arrive in SFO
<strong>Sunday, May 18</strong>
<strong>14:00</strong> - Exam
<strong>16:00</strong> or so - Tweetup
<strong>Monday, May 19</strong>
<strong>08:00</strong> - <a href="https://www.ciscolive2014.com/connect/sessionDetail.ww?SESSION_ID=2182">BRKCRT-2001 - NX-OS, IOS, IOS-XR,
</a> <a href="https://www.ciscolive2014.com/connect/sessionDetail.ww?SESSION_ID=2182">Unique and Similar at the Same Time</a> w/ <a href="https://www.ciscolive2014.com/connect/speakerDetail.ww?PERSON_ID=767D7F27ADC21F9EC5B18A984682E57E/?cid=000334090">Joseph Rinehart</a>
<strong>10:00</strong> - <a href="https://www.ciscolive2014.com/connect/sessionDetail.ww?SESSION_ID=3114">BRKCRT-2000 - HardCore IPv6 Routing - No Fear</a>
w/ Scott Morris, Donnie Moss
<strong>13:00</strong> - <a Continue reading
Taking the Old Approach to Cisco Live 2014
I was just reading through Bob’s blog post from today and wanted to give a rebuttal of sorts. In his post, Bob tells us that’s he’s going to be at Cisco Live US in San Francisco this year but he won’t be coming on the Full Conference pass like he usually does. He’s going with the Social Event pass this year, which is actually a great, great way to attend. I know several people who are thinking about scaling back to the Social Event pass as well, and there’s nothing wrong with doing it like that. There are some things that it doesn’t get you, though.
The Social Event pass means no breakout sessions. These are the bread-and-butter of the conference and the real technical reason that I try to go each year (listen to me talk like I’m a 20-year NetVet…LOL). Yes, most of the sessions are available on Cisco Live 365 afterwards, but that leaves two problems for me. First of all, I will never actually make the time to go back and sit through these sessions after the event. It’s just something that won’t happen with life and work and everything going on. Secondly, I cannot sit Continue reading
Read This if You’re Going to Cisco Live in May!
Do not tell anyone I told you, but I heard a rumor today. It looks like the attendees will be in for quite a treat for the 25th Anniversary of the Customer Appreciate Event. It seems that we’re all going to be shipped off to AT&T Park for the show! It’s the home of the San Francisco Giants and a beautiful stadium. And guess who’s going to be there? Yes, me. And my wife. And about 984572 of my friends. But so will Lenny Kravitz and Imagine Dragons!
AT&T Park I can’t imagine a better place to spend the evening with your friends than here. McCovey Cove. The Giants Wall of Fame. The 1927 Glove. The Willie Mays statue. Ballpark food. And, for the network angle, it boasts one of the largest public hotspots in the world.
Lenny Kravitz We all know he plays Cinna in the Hunger Games, but did you know he actually plays music on the side? I had no idea! Ok…maybe I did. And maybe I’m a fan. And maybe I’ve never read Hunger Games. (All are true, by the way.)
Lenny’s a Grammy winner. Four of them, to Continue reading