Private Companies, Public Squares
Daphne Keller, Director, Stanford Center for Internet & Society, and Lee Rowland, Senior Staff Attorney, ACLU Speech, Privacy & Technology Project
Moderator: Matthew Prince, Co-Founder & CEO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MP: Technology and law seem like they are colliding more and more. Tech companies are being asked to regulate content. For a largely non-lawyer audience, give us some foundations about basic rules when you have content on your network?
LR: Communications 2.0 makes the 1st amendment almost quaint. The vast majority of speech that we exchange happens online. When it is hosted by private companies, the 1st amendment doesn’t constrain it. So this is a space governed by norms and individual choices of people like Matthew. In the wake of Cloudflare's decision to take down the Daily Stormer, Matthew penned a piece saying it’s scary that we have this power, and I exercised it. We have a completely unaccountable private medium of communication.
MP: There are shields for companies for this; What is intermediary liability and why is this a position at Google/Stanford?
DK: No one knows what it means; it’s a set of laws that tell platforms when they have to take down Continue reading
Betting on Blockchain
Juan Benet, Founder, Protocol Labs, and Jill Carlson, GM, Tezos Foundation
Moderator: Jen Taylor, Head of Product, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
JT: Tell us about what BlockChain is
JC: Going back to 2008, advent of blockchain came with bitcoin white paper.
The word Blockchain wasn’t mentioned at that point, but that was the advent of this tech.
What it solved was niche problem called double spend problem. Creation of digital cash.
What you see in a bank account isn’t digital cash. The problem in cryptography was how to create digital cash that doesn't rely on 3rd party intermediary. This is what Bitcoin created.
JB: Blockchain packs in lots of stuff: useful as brand. Like internet/web in early 90s, the meaning is fuzzy.
Properties that all of these apps have in common:
Academic definition: A blockchain is an indelible chain of blocks; once you insert information into one of them it remains.
Marketing definition: many applications have been developed over last few years, all have to do with public verifiability. Reliance on cryptographic methods to achieve goals on clearing payments and the ability to check and verify.
Across the board, removing 3rd parties from equation. Establishing publicly verifiable Continue reading
The New Breed of Patent Trolls
Lee Cheng, President & Co-CLO, Symmetry IP LLC, and Vera Ranieri, Staff Attorney, Electronic Frontier Foundation
Moderator: Doug Kramer, General Counsel, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
DK: Patent--IP issues and challenges are accelerating important supreme court cases. there’s also a flurry of legislative activity about patents. Good idea to talk about this topic: where is this going? How to push world in virtuous direction?
DK: current state of affairs. Vera: at the core is the patent itself, which is issued by and often adjudged by the patent office… is this where the problem lies?
VR: I like to blame everyone. How does someone get a patent in the first place? Someone comes up with an invention, patent attorney, documents it with opaque language, and files. The examiner then interprets the patent and searches for prior art, and says “I think this is what the patent owner is trying to claim.”
In the software space, it’s especially difficult. A lot of where inventing happens in software is right here, in businesses. People have a problem and find a solution by developing software. They don’t patent and publish.
Patent office tends to focus on patents.
DK: Talk about the Continue reading
If I Knew Then What I Know Now: Tales from the Early Internet
Paul Mockapetris, Inventor, DNS, and David Conrad, CTO, ICANN
Moderator: Matthew Prince, Co-Founder & CEO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MP: You guys wrote all this stuff; why is the internet so broken?
PM: People complain about security flaws, but there is no security in original design of dns. I think of it that we haven’t had the right investment in rebuilding the infrastructure.
Original stuff was only good for 10 years, but we’ve been using it for 30.
DC: The fact that we were able to get Packard from one machine to another in the early days was astonishing in itself.
MP: So what are you worried about in terms of Internet infrastructure that we aren’t even thinking about?
PM: i’m worried about the fact that a lot of places like the ITF are very incremental in their thinking, and that people aren’t willing to take the next big jump. E.g. hesitancy to adopt blockchain
Being able to experiment and try new stuff is important.
The idea that you can't change anything because it will affect the security and stability of the internet. we need to weigh benefits and risks or we will eventually die of Continue reading
Making the World Better by Breaking Things
Ben Sadeghipour, Technical Account Manager, HackerOne, and Katie Moussouris, Founder & CEO, Luta Security
Moderator: John Graham-Cumming, CTO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
JGC: We’re going to talk about hacking
Katie Moussouris helps people how to work around security vulnerabilities.
Ben Sadeghipour is a technical account manager at HackerOne, and a hacker at night
JGC: Ben, you say you’re a hacker by night. Tell us about this.
BS: It depends who you ask: if they encourage it; or, we do it for a good reason. “Ethical hacker” - we do it for a good reason. Hacking can be illegal if you’re hacking without permission; but that’s not what we do.
JGC: You stay up all night
BS: I lock myself in the basement
JGC: Tell us about your company.
KM: I was invited to brief Pentagon when I worked at Microsoft; The pentagon was interested in the implementation of this idea in a large corporation like Microsoft.
“Hacking the pentagon”
The adoption of Bug Bounty has been slow. We were interested in working with a very large company like Microsoft. There was interest in implementing ideas from private sector at Pentagon. I helped the internal team at Continue reading
A Cloud Without Handcuffs
Brandon Philips, Co-Founder & CTO, CoreOS, and Joe Beda, CTO, Heptio, & Co-Founder, Kubernetes
Moderator: Alex Dyner, Co-Founder & COO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
We’re exploring increasing risk of few companies locking in customers gaining more power over time.
AD: I want to hear your stories about how you got into what you do.
JB: Kubernetes faced problem of either having googlers use rbs or bring X to rest of world. We wanted to have Googlers and outside people using something similar. We chose to do it as open source because you play a different game when you’re the underdog. Through open source we could garner interest. We wanted to provide applicational mobility.
AD: Brandon, talk about your mission and why you started company.
BP: We started CoreOS four years ago; We spent a lot of time thinking about this problem and containers were natural choice. They are necessary for achieving our mission. We wanted to allow people to have mobility around their applications. We wanted to enable new security model through containers. So we started building a product portfolio
AD: There are tradeoffs between using a container or an open source tech; how do you think Continue reading
Making Mobile Faster than Fixed Line
Cole Crawford, Founder & CEO, Vapor IO, and Chaitali Sengupta, Consultant, Qualcomm Datacenter Technologies
Moderator: Michelle Zatlyn, Co-Founder & COO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
CC: moved between private and public sector.
CS: her company added 100 million customers in India.
MZ: Let’s start with where we are today: trends or things you’re seeing in the marketplace that weren’t there 5 years ago.
CC: What’s interesting is combination of data mass and data velocity, resulting in a more dynamic internet. E.g. Latency wasn’t mentioned by customers at first; AI is helping to create a new low-latency internet.
CS: One of the biggest things is applying lessons of cloud to telecom to see how we can make systems more centralized and virtualized. Network function virtualization; putting things on general service servers. Now dovetailing into 5G, where we see more bandwidth.
MZ: We’re currently in 4G world; when will 5G standard get finalized?
CS: Standards are getting finalized; trials are getting started. Many 5G systems are up and running NWC America ... is running trials already. I would say end of next year or 2019
MZ: So the future is here and it’s almost distributed? 4G took 2 years to Continue reading
Disruptive Cryptography: Post-Quantum & Machine Learning With Encrypted Data
Shay Gueron, Associate Professor of Mathematics, University of Haifa, Israel, and Raluca Ada Popa, Assistant Professor of Computer Science, UC Berkeley
Moderator: John Graham-Cumming, CTO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
Raluca is also a Co-Director of the RISELab at UC Berkeley as well as Co-Founder and CTO of a cybersecurity startup called PreVeil. She developed practical systems that protect data confidentiality by computing over encrypted data as well as designed new encryption schemes that underlie these systems.
Shay was previously a Senior Principal Engineer, serving as Intel’s Senior Cryptographer and is now senior principal at AWS, and an expert in post-quantum, security, and algorithms.
JGC: Tell us about what you actually do.
RP: Computing on encrypted data is not just theoretical; it’s also exciting because you can keep data encrypted in the cloud. It covers hacking attacks while still enabling the functionality of the system. This is exciting because we can cover so many hacking attacks in one shot.
SG: I’m working on making new algorithms; also on making solutions for quantum computers that are increasingly strong.
SG: I’ve been working on cryptography: making it faster, recently I’ve been thinking about solutions for what will happen when we Continue reading
What Will AI Mean for Everyday Life?
Willie Tejada, Chief Developer Advocate, IBM and Anthony Goldbloom, CEO, Kaggle
Moderator: Jen Taylor, Head of Product, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
JT: Our focus today is really what does AI mean for everyday life. I’m hearing a lot about AI. What is your assessment about where we are and how it is making a difference?
WT: we’re in an unprecedented, interesting era. From a consumer perspective, negative connotation.
It’s an interesting era we are in; these technologies are going to do a tremendous amount in terms of consumers selecting what they buy, Helping patient-centric care.
Combination of data set & availability of resources is fueling AI.
You might hear 90% of the world’s data has been created in the past two years. AI will help us deal with that kind of information overload.
The big difference with programming systems is that AI knows how to understand, reason, learn, interact.
AG: There is a set of techniques through which we can more accurately predict fraud, insurance plans, credit scoring.
This is a jump in the past 15 years.
5 years ago, the ability to do very exciting things with unstructured data, i.e. automating radiology. Then digital networks Continue reading
The View from Washington: The State of Cybersecurity
Avril Haines, Former Deputy National Security Advisor, Obama Administration
Moderator: Doug Kramer, General Counsel, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
Avril began her career on the National Security Council, and went on to become the first female deputy at the CIA.
DK: How will cyber will play a role in military operations?
AH: We look at it from the perspective of “asymmetric threats”; state actors (those who have high-value assets that they can hold at risk with no threat to them). The US is more technologically advanced and relies on cyber more and more; we are as a consequence more vulnerable to cyber threats. Asymmetric threats thus hold at risk those things that are most important to us.
In the cyber realm we can’t quite define what constitutes a use of force, and saying so can be used against us. So this is an area that is crucial to continue working in; in many respects the US has the most to lose from using a framework that doesn’t work.
“The private sector is utterly critical in creating a framework that is going to work.”
We want to have widely-accepted norms and rules so that we can ask other countries Continue reading
Understanding the prevalence of web traffic interception


This is a guest post by Elie Bursztein who writes about security and anti-abuse research. It was first published on his blog and has been lightly edited.
This post summarizes how prevalent encrypted web traffic interception is and how it negatively affects online security according to a study published at NDSS 2017 authored by several researchers including the author of this post and Nick Sullivan of Cloudflare. We found that between 4% and 10% of the web’s encrypted traffic (HTTPS) is intercepted. Analyzing these intercepted connections further reveals that, while not always malicious, interception products most often weaken the encryption used to secure communication and puts users at risk.
This blog post presents a short summary of our study’s key findings by answering the following questions:
- How is encrypted web traffic intercepted? This section offers a short recap of how man-in-the-middle (MITM) interception is performed.
- How prevalent is HTTPS interception? This section explains how we measured the prevalence of HTTPS interception in the 8 billion connections we analyzed. Next, it summarizes the key trends observed when grouping these interceptions by OS (operating system), browser, and network.
- Who is intercepting secure web communication and why? This section provides an overview of Continue reading
Delivering Dot
Since March 30, 2017, Cloudflare has been providing DNS Anycast service as additional F-Root instances under contract with ISC (the F-Root operator).
F-Root is a single IPv4 address plus a single IPv6 address which both ISC and Cloudflare announce to the global Internet as a shared Anycast. This document reviews how F-Root has performed since that date in March 2017.
The DNS root servers are an important utility provided to all clients on the Internet for free - all F root instances including those hosted on the Cloudflare network are a free service provided by both ISC and Cloudflare for public benefit. Because every online request begins with a DNS lookup, and every DNS lookup requires the retrieval of information stored on the DNS root servers, the DNS root servers plays an invaluable role to the functioning of the internet.
At Cloudflare, we were excited to work with ISC to bring greater security, speed and new software diversity to the root server system. First, the root servers, because of their crucial role, are often the subject of large scale volumetric DDoS attacks, which Cloudflare specializes in mitigating (Cloudflare is currently mitigating two concurrently ongoing DDoS attacks as we write this). Continue reading
Hurricane Irma
Yesterday, we described how Hurricane Irma impacted several Caribbean islands, with the damage including a significant disruption to Internet access.
As Irma is now forecast to hit southern Florida as category 5 this weekend with gusty winds reaching up to 155mph, it is also expected that Internet infrastructure in the region will suffer.
At the time of writing, we haven’t noticed any decrease in traffic in the region of Miami despite calls to evacuate.

Resilient Data Centers
Contrary to popular belief, Internet wasn't built for the purpose of resisting a nuclear attack. That doesn't mean that datacenters aren't built to resist catastrophic events.
The Miami datacenter housing servers for Cloudflare and other Internet operators is classified as Tier IV. What does this tiering mean? As defined by the ANSI (American National Standards Institute), a Tier IV datacenter is the stringent classification in term of redundancy of the critical components of a datacenter: power and cooling. It guarantees 99.995% uptime per year, that is only 26 minutes of unavailability. Tier IV datacenters provide this level of uptime by being connected to separate power grids, allowing their customers to connect their devices to both of these grids. They Continue reading
The Story of Two Outages

Over the last two days, Cloudflare observed two events that had effects on global Internet traffic levels. Cloudflare handles approximately 10% of all Internet requests, so we have significant visibility into traffic from countries and networks across the world.
On Tuesday, September 5th, the government of Togo decided to restrict Internet access in the country following political protests. The government blocked social networks and rate-limited traffic, which had an impact on Cloudflare.
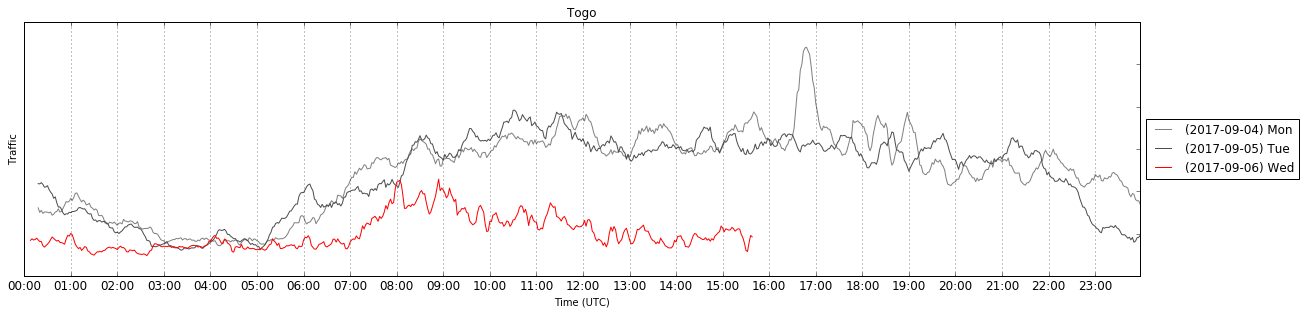
This adds Togo to the list of countries like Syria (twice), Iraq, Turkey, Libya, Tunisia, etc that have restricted or revoked Internet access.
The second event happened on Wednesday, September 6th, when a category 5 hurricane ravaged the Caribbean Islands.
The affected countries at the moment are:
- Anguilla
- Antigua and Barbuda
- British Virgin Islands
- Puerto Rico
- Saint Barthelemy
- Saint Kitts and Nevis
- Saint Martin
- Sint Maarten
- U.S. Virgin Islands
Losing the routes
Most of the network cables are buried underground or laying at the bottom of the oceans but the hardware which relies on electricity is the first one to go down.
Cell towers sometime have their own power source thus allowing local phone calls but without a backbone no outside Continue reading
SIDH in Go for quantum-resistant TLS 1.3
The Quantum Threat
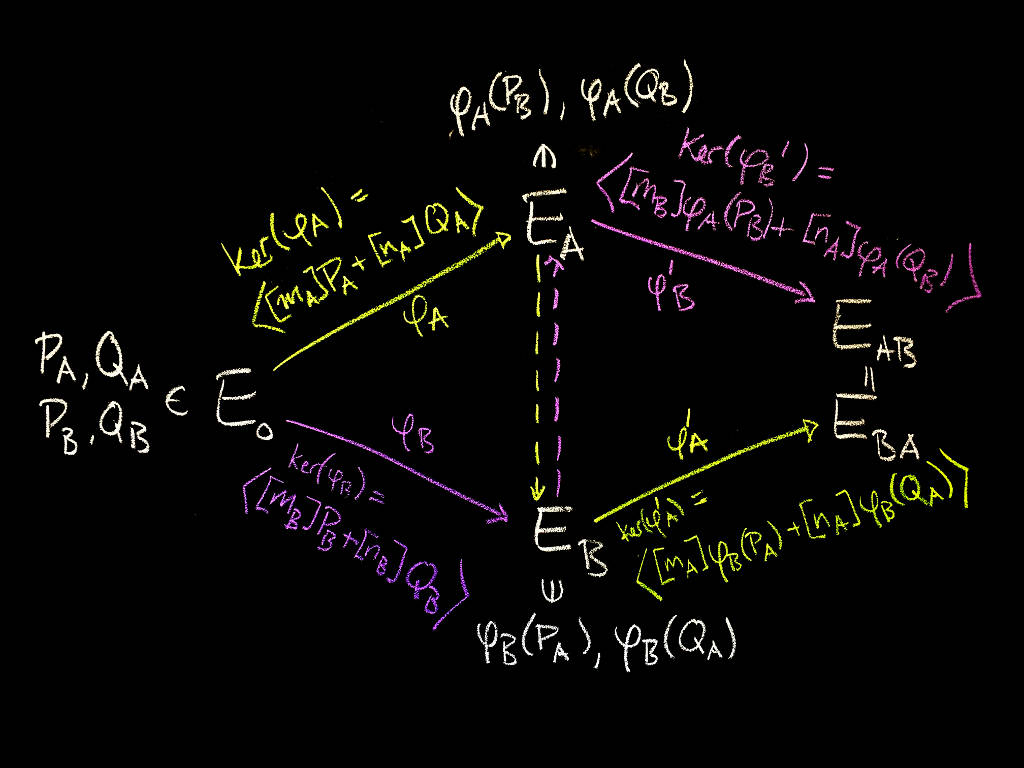
Most of today's cryptography is designed to be secure against an adversary with enormous amounts of computational power. This means estimating how much work certain computations (such as factoring a number, or finding a discrete logarithm) require, and choosing cryptographic parameters based on our best estimate of how much work would be required to break the system.
If it were possible to build a large-scale quantum computer, many of the problems whose difficulty we rely on for security would no longer be difficult to solve. While it remains unknown whether large-scale quantum computers are possible (see this article for a good overview), it's a sufficient risk that there's wide interest in developing quantum-resistant (or post-quantum) cryptography: cryptography that works on ordinary computers we have today, but which is secure against a possible quantum computer.
At Cloudflare, our biggest use of cryptography is TLS, which we use both for serving our customers' websites (all Cloudflare sites get free HTTPS), as well as for internal inter-datacenter communication on our backend.
In the TLS context, we want to create a secure connection between a client and a server. There are basically three cryptographic problems here:
Authenticity: the server Continue reading
Portland (Oregon): Cloudflare’s 117th Data Center!

Even as the luckiest amongst us across the US West Coast dashed off to Oregon to be closer to the solar eclipse path of totality, Cloudflare engineers were busy turning up our newest data center in Portland.
This deployment serves as our 27th data center in North America alone, and our 117th globally. It also provides additional redundancy to our Seattle and San Jose data centers, while increasing our capacity to run services and fight growing attacks.
Special History
The Silicon Forest corridor around Portland holds a special place in the hearts of the Cloudflare team. It is both new (by way of our latest edge deployment bringing us closer to millions of Oregon Internet users), and familiar (since we have had an internal data center in this region for many years, enabling services such as analytics and enterprise logs).
The greater Portland area has played a pivotal area in building high-technology products from companies such as Tektronix (test and measurement equipment), Mentor Graphics (electronic design automation) and Intel (with nearly 20,000 employees across Oregon).
Expanding the edge
At our Portland data center, we locally interconnect with ISPs such as Comcast (into their regional area networks such as Beaverton and Continue reading
One way to help Hurricane Harvey victims
Photo Credit: Texas Military Department (Flickr)
Hurricane Harvey hit Texas last Friday as a Category 4 storm. Although Harvey's category was quickly downgraded, the storm lingered around for days, bringing 50 inches of rain to the greater Houston area.
As someone who was born in Houston, it's hard to see my former city hit with such destruction, and to know that many of my friends and fellow Houstonians are in need of help and assistance. Many families have had their entire house flooded out by the storm. Displaced residents are in a state of stagnation and are seeing their supplies diminishing by the day.
The Hurricane Relief app will allow visitors to your site to donate to one of the charities helping those impacted in Houston:
The Hurricane Relief App takes two clicks to install and requires no code change. The charities listed are recommended by NPR.
If you wanted to add your own custom list of charities for disaster relief or other causes, feel free to fork the source of this app and make your own.
The WireX Botnet: How Industry Collaboration Disrupted a DDoS Attack
Introduction
On August 17th, 2017, multiple Content Delivery Networks (CDNs) and content providers were subject to significant attacks from a botnet dubbed WireX. The botnet is named for an anagram for one of the delimiter strings in its command and control protocol. The WireX botnet comprises primarily Android devices running malicious applications and is designed to create DDoS traffic. The botnet is sometimes associated with ransom notes to targets.
A few days ago, Google was alerted that this malware was available on its Play Store. Shortly following the notification, Google removed hundreds of affected applications and started the process to remove the applications from all devices.
Researchers from Akamai, Cloudflare, Flashpoint, Google, Oracle Dyn, RiskIQ, Team Cymru, and other organizations cooperated to combat this botnet. Evidence indicates that the botnet may have been active as early as August 2nd, but it was the attacks on August 17th that drew the attention of these organizations. This post represents the combined knowledge and efforts of the researchers working to share information about a botnet in the best interest of the internet community as a whole. This blog post was written together by researchers from numerous organizations and released Continue reading
Going Global – a Localization Case Study at Cloudflare
Today Cloudflare serves nearly 10% of all global internet requests and more than 80% of our customers are based outside of the United States. Cloudflare is rapidly growing and there is nothing more important to us than being able to better serve our users across the world beyond our global offices in San Francisco, Austin, Champaign, Washington D.C., New York, London, and Singapore.
Earlier this year, we launched a team to focus on global expansion and growth. In June, we presented our agile global market expansion experiment framework at LocWorld Barcelona and wanted to report back on how things were going.
Getting started
"If you talk to a man in a language he understands, that goes to his head. If you talk to him in his language, that goes to his heart" – Nelson Mandela
At Cloudflare, we are motivated by our users from all around the world. Of our top 15 countries by traffic volume, 10 have official languages other than English. As a large part of our users do not speak our primary language of business, our priority is to reach and engage with these users in their native languages through localization.

As a growing company, Continue reading
Advancing Privacy Protection with the GDPR
A game-changer
The road towards implementation of the new European GDPR (the General Data Protection Regulation) has been a long one, even though public awareness of its impact, especially outside of Europe, is only now really starting to take hold. This game-changing piece of EU legislation will require companies to fundamentally change how they process and use personal data (broadly defined) they receive from EU citizens, including through consent and data handling agreements with their customers, supply chains, and vendors. It will come into effect on 25th May, 2018, and will have tremendous reach, touching on all business sectors. More than that, the GDPR has extra-territorial scope and will apply to any business that processes the personal data of European users, irrespective of whether that business has any physical presence in the European Union.
The aim of the GDPR, which will replace the currently applicable European Data Protection Directive of 1995, is to both meet the challenges of globalization and address dynamic new products and services, while also trying to create a future-proof framework that will comfortably accommodate emerging technologies and scenarios, including the Internet of Things. It is also a response to Europeans’ growing concerns over the control and Continue reading
 Source: accuweather.com
Source: accuweather.com
