QoS Design Notes for CCDE
Trying to get my CCDE studies going again. I’ve finished the End to End QoS Design book (relevant parts) and here are my notes on QoS design.
Basic QoS
Different applications require different treatment, the most important parameters are:
- Delay: The time it takes from the sending endpoint to reach the receiving endpoint
- Jitter: The variation in end to end delay between sequential packets
- Packet loss: The number of packets sent compared to the number of received as a percentage
Characteristics of voice traffic:
- Smooth
- Benign
- Drop sensitive
- Delay sensitive
- UDP priority
One-way requirements for voice:
- Latency ≤ 150 ms
- Jitter ≤ 30 ms
- Loss ≤ 1%
- Bandwidth (30-128Kbps)
Characteristics for video traffic:
- Bursty
- Greedy
- Drop sensitive
- Delay sensitive
- UDP priority
One-way requirements for video:
- Latency ≤ 200-400 ms
- Jitter ≤ 30-50 ms
- Loss ≤ 0.1-1%
- Bandwidth (384Kbps-20+ Mbps)
Characteristics for data traffic:
- Smooth/bursty
- Benign/greedy
- Drop insensitive
- Delay insensitive
- TCP retransmits
Quality of Service (QoS) – Managed unfairness, measured numerically in latency, jitter and packetloss
Quality of Experience (QoE) – End user perception of network performance, subjective and can’t be measured
Tools
Classification and marking tools: Session, or flows, are analyzed to determine what class the packets belong to Continue reading
Unique RD per PE in MPLS VPN for Load Sharing and Faster Convergence
This post describes how load sharing and faster convergence in MPLS VPNs is possible by using an unique RD per VRF per PE. It assumes you are already familiar with MPLS but here is a quick recap.
The Route Distinguisher (RD) is used in MPLS VPNs to create unique routes. With IPv4, an IP address is 32 bits long but several customers may and probably will use the same networks. If CustomerA uses 10.0.0.0/24 and CustomerX also uses 10.0.0.0/24, we must in some way make this route unique to transport it over MPBGP. The RD does exactly this by prepending a 64 bit value and together with the IPv4 address, creating a 96-bit VPNv4 prefix. This is all the RD does, it has nothing to do with the VPN in itself. It is common to create RD consisting of AS_number:VPN_identifier so that a VPN has the same RD on all PEs where it exists.
The Route Target (RT) is what defines the VPN, which routes are imported to the VPN and the topology of the VPN. These are extended communities that are tagged on to the BGP Update and transported over MPBGP.
MPLS uses Continue reading
Book Review – End-to-End QoS Network Design: Quality of Service for Rich-Media & Cloud Networks, Second Edition
As part of my CCDE studies, I needed a good resource on QoS. There have basically been two good books on QoS before, the first edition of End to End Qos Network Design and Qos-Enabled Networks: Tools and Foundations. The first edition of this book is good but very dated, it was released back in 2004. Qos-Enabled Networks is a great book but it’s written to not be vendor specific, so you will not get details on platforms or configuration snippets.
In my opinion, earlier books gave a good foundation to understand QoS concepts but there were too few design cases, they were lacking platform information and not enough examples to be able to act as a reference. Since the first edition of this book, a lot has happened, new products and new Places In the Network (PIN) such as Datacenter, Wireless and to some degree MPLS.
The book is written by Tim Szigeti, Christina Hattingh, Robert Barton and Kenneth Briley Jr. Tim is a long time CCIE, technical leader at Cisco. He is the QoS gury responsible for a lot of the Cisco Validated Designs (CVDs) and a frequent presenter at Cisco Live. Christina is a former Technical Marketing Continue reading
The Tale of the Mysterious PIM Prune
Christmas is lurking around the corner and in the spirit of Denise “Fish” Fishburne, I give you the “The Tale of the Mysterious PIM Prune”.
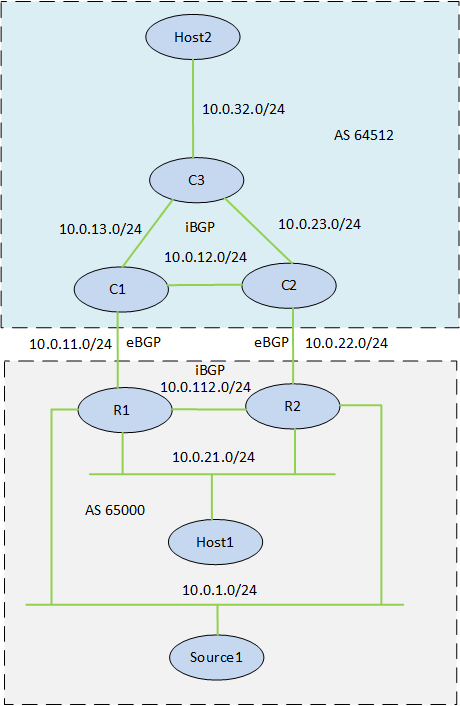
I have been working a lot with multicast lately which is also why I’ve blogged about it. To start off this story, let’s begin with a network topology.
The multicast source is located in AS 65000 and contains two routers that are connected to the multicast source. The routers run BFD, OSPF, iBGP, PIM internally and the RP is located on C1. There is a local receiver in AS 65000 and a remote one in AS 64512. The networks 10.0.1.0/24 and 10.0.21.0/24 come off the same physical interface. If you want to replicate this lab, all the configs are provided here.
This network requires fast convergence and I have been troubleshooting a scenario where the active multicast router (R1) has its LAN interface go down, meaning that the traffic from the source must come in on R2. In this scenario I have seen convergence in up to 60 seconds which is not acceptable. The BGP design is for R2 to still exit out via R1 if the link is Continue reading
Using EEM to Speed up Multicast Convergence when Receiver is Dually Connected
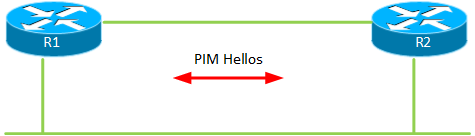
When deploying PIM ASM, the Designated Router (DR) role plays a significant part in how PIM ASM works. The DR on a segment is responsible for registering mulicast sources with the Rendezvous Point (RP) and/or sending PIM Joins for the segment. Routers with PIM enabled interfaces send out PIM Hello messages every 30 seconds by default.
After missing three Hellos the secondary router will take over as the DR. With the standard timer value, this can take between 60 to 90 seconds depending on when the last Hello came in. Not really acceptable in a modern network.
The first thought is to lower the PIM query interval, this can be done and it supports sending PIM Hellos at msec level. In my particular case I needed convergence within two seconds. I tuned the PIM query interval to 500 msec meaning that the PIM DR role should converge within 1.5 seconds. The problem though is that these Hellos are sent at process level. Even though my routers were barely breaking a sweat CPU wise I would see PIM adjacencies flapping.
The answer to my problems would be to have Bidirectional Forwarding Dectection (BFD) for PIM but it’s only supported on Continue reading
Lessons Learned from Deploying Multicast
Lately I have been working a lot with multicast, which is fun and challenging! Even if you have a good understanding of multicast unless you work on it a lot there may be some concepts that fall out of memory or that you only run into in real life and not in the lab. Here is a summary of some things I’ve noticed so far.
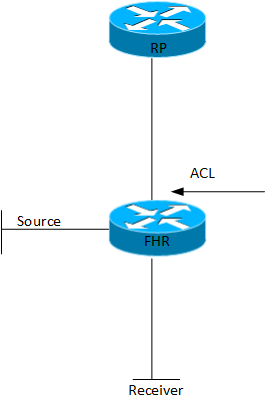
PIM Register
PIM Register are control plane messages sent from the First Hop Router (FHR) towards the Rendezvous Point (RP). These are unicast messages encapsulating the multicast from the multicast source. There are some considerations here, firstly because these packets are sent from the FHR control plane to the RP control plane, they are not subject to any access list configured outbound on the FHR. I had a situation where I wanted to route the multicast locally but not send it outbound.
Even if the ACL was successful, care would have to be taken to not break the control plane between the FHR and the RP or all multicast traffic for the group would be at jeopardy.
The PIM Register messages are control plane messages, this means that the RP has to process them Continue reading
CCIE SP version 4 has been announced
Cisco has been updating their certifications lately. The CCIE RS got bumped to version 5 and went all virtual. The CCNP RS was then also updated and now it’s time for the CCIE SP.
It seems that Cisco has done a better job lately of tying all the certifications together and providing a more unified exam format. At least this is the indications I’m getting for the CCIE track.
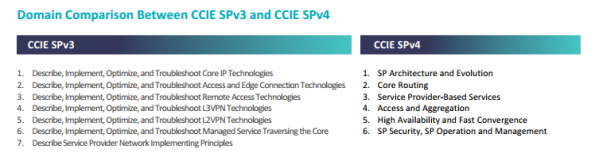
CCIE SP v4 will use the same exam format as the CCIE RS v5. This means that there will be a diagnostic (DIAG) and troubleshooting (TS) module at the CCIE SP lab. First let’s go over the exam domain.
My impression from this is that the v4 blueprint is a bit more generic. This makes it easier to develop the exam content and I also get the feeling that it’s getting more important to have a high level understanding of the different technologies and architecture.
The exam is designed to be dual stack, so you can’t afford to be weak on v6, you must master the v6 topics at the same level as v4. If you get certified you may use the IPv6 Forum Gold logo.
The following topics have been Continue reading
Checking community interest for a new kind of networking site
A couple of days ago I got an idea for a new kind of networking site. The idea is to do something similar to dpreview.com but for network products.
I work a lot on network designs these days and part of the design is always what device to choose. Maybe I need a product that does NAT, IPSEC, 200 Mbit/s of throughput and has at least 4 ports. This is the kind of knowledge that you get from working on design and staying up to date with products from different vendors. There is not a community for people where they can find a broad range of products and get help choosing the right one based on different search criteria such as number of ports, features and the throughput.
What I would like to do as well is to have people write about the products. The product page said 200 Mbit/s but I got 500 Mbit/s with IMIX traffic. After enabling IPSEC I only got 80 Mbit/s. These kind of figures are very difficult to find. There could then be some kind of rating or voting system to rate if the post is helpful to sort out if people are Continue reading
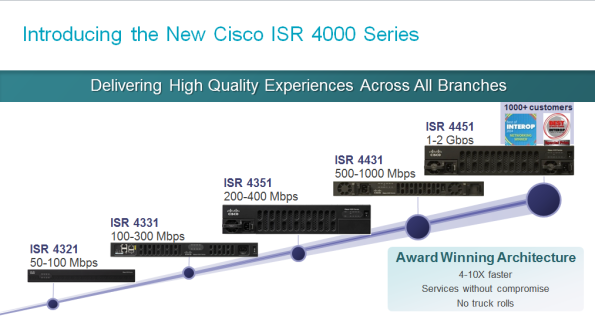
Cisco Adds New Routers In the ISR 4000 Family
The Cisco ISR G2 routers have been around for a while now. Roughly a year ago, Cisco released the Cisco 4451-X router which was the first ISR running IOS-XE. Cisco has now added new routers to the 4000 family, which means that the ISR G2 family will eventually go away. Don’t panic though! That will not happen for a while but if you are looking to buy new ISR routers, then take a look at the new 4000 family.
One great thing about the new ISR 4000 routers is that they support upgrading of the bandwidth capacity by buying a license. That means that you can keep the same router for a longer time and grow into it, rather than doing a complete replacement as your demand for bandwidth increases. The new models are ISR 4321, 4331, 4351 and 4431.
If you need a router that does 10 Mbit/s, then you can get the 4321 and you can keep using it until you reach 100 Mbit/s. The 4331 will get you from 100-300 Mbit/s which would cover a lot of customers that I currently have.
The next slide shows some of the new features of the ISR 4000:
The ISR Continue reading
A Quick Look at NAT64 and NAT46
Introduction
In the best of worlds we would all be using native IPv6 now, or at least dual
stack. That is not the case however and IPv4 will be around for a long time yet.
During that time that both protocols exist, there will be a need to translate
between the two, like it or not.
Different Types of NAT
Before we begin, let’s define some different forms of NAT:
NAT44 – NAT from IPv4 to IPv4
NAT66 – NAT from IPv6 to IPv6
NAT46 – NAT from IPv4 to IPv6
NAT64 – NAT from IPv6 to IPv4
The most commonly used type is definitely NAT44 but here we will focus on translating
between IPv4 and IPv6.
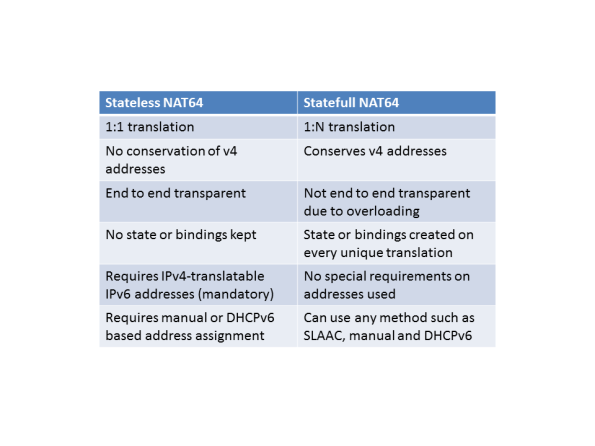
NAT64
There are two different forms of NAT64, stateless and statefull. The stateless version
maps the IPv4 address into an IPv6 prefix. As the name implies, it keeps no state.
It does not save any IP addresses since every v4 address maps to one v6 address.
Here is a comparison of stateless and statefull NAT64:
DNS64
When resolving names to numbers in IPv4, A records are used. When doing the same
in IPv6, AAAA records are used. When using NAT64, the device doing Continue reading
A Quick Look at MPLS-TE
Introduction
I’m currently designing and implementing a large network which will run MPLS.
This network will replace an old network that was mainly L2 based and did not
run MPLS, only VRF lite. There are a few customers that need to have diverse
paths in the network and quick convergence when a failure occurs.
This led me to consider MPLS-TE for those customers and to have plain MPLS
through LDP for other customers buying VPNs. What is the usage for MPLS-TE?
Weaknesses of IGP
When using normal IP forwarding a least cost path is calculated through an IGP,
such as OSPF or ISIS. The problem though is that only the least cost path will
be utilized, any links not on the best path will sit idle, which is a waste of
bandwidth. IGP metrics can be manipulated but that only moves the problem to
other links, it does not solve the root cause. Manipulating metrics is cumbersome
and prone to error. It’s difficult to think of all the traffic flows in the network
and get all the metrics correct. IGPs also lack the granularity in metrics to
utilize all the bandwidth in the network.
RSVP-TE
RSVP in the past was Continue reading
400k Views in 4 Years – A Review of My Last 4 Years
Very often in our lives we are fully focused on what is going to happen in the
future. We rarely look back at what we have done and how we got to where we
are now. People that know me, know that I’m a very focused person that is always
looking to improve my skillset.
In July of 2010 I decided that I wanted to become a CCIE. I was a CCNP at that
time and I was working in a role where I did 2nd level support. I decided that
I wanted to blog to keep my notes for the CCIE online. I wrote my first blog
post on July 16, 2010. Today on August 16, 2014, almost four years later I passed
400k views on the blog. It’s been an amazing journey and here is a look back at
what has happened since then. This post is meant to be inspirational, to see
what can be accomplished in four years if you put your heart to it, please don’t
take it as boasting :)
For my CCIE studies I used INE workbooks, I decided that it would be good practice
to answer questions on their forums to keep Continue reading
The New CCNP – Combining Exams
The new CCNP RS was just released. The last day to test with the old exams is
January 29, 2015.
What is usually seen is that people start to panic, they want to complete the
old exams before they are removed. There is no reason to panic though, you can
mix and match the old exams and the new exams. If you have taken the old
ROUTE and SWITCH, you can take the new TSHOOT and become a CCNP. If you have
the old SWITCH, you can take the new ROUTE and TSHOOT and become a CCNP.
All the valid combinations are available through a comparison tool from Cisco.
Which exams should you take? This depends on how far you are into your studies
and what your future plans are. If you plan to take the CCIE, the new ROUTE looks like
a good stepping stone to me. If you want to finish as quickly as possible, then take
the old exams. As mentioned above, if you don’t complete all three in time, you can take
one of the new ones to round off the CCNP.
Good luck to all the CCNP candidates out there!
CCNP RS Version 2
I woke up to the news that CCNP RS Version 2 is now live. As usual, there is no
reason to panic. If you have been studying for the old version, nothing has been
wasted. OSPF is still OSPF, EIGRP is still EIGRP. The new exams are:
Implementing Cisco IP Routing (300-101)
Implementing Cisco IP Switched Networks (300-115)
Troubleshooting and Maintaining Cisco IP Networks (300-135)
The last day to take the old exams will be January 29, 2015.
The good news with the new blueprint is that Cisco is doing what they have been
for a while now, producing more detailed blueprints on what to study. There is also
a weighting included, which shows how much weight each section holds of the entire exam.
Implementing Cisco IP Routing (300-101)
This is the new version of the ROUTE exam. The old version was 642-902. The
new blueprint is here.
The routing protocols are still there, as expected. Let’s go through the blueprint to
see what has been added or clarified from the old blueprint.
1.0 Network Principles 10%
1.1 Identify Cisco Express Forwarding concepts
1.1.a FIB
1.1.b Adjacency table
1.2 Explain general network challenges
Continue reading
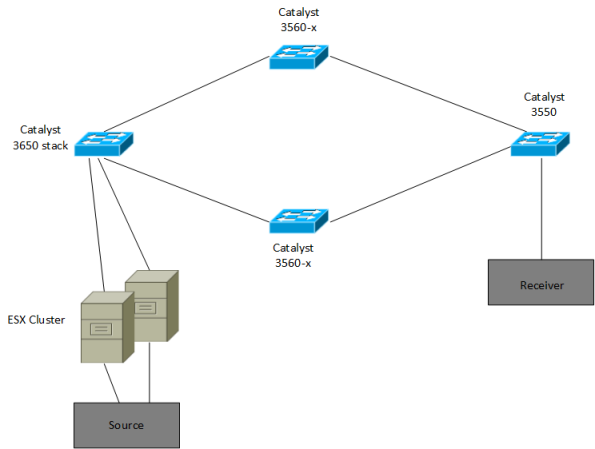
Potential Issues with Multicast within a VLAN Spanning Switches
Background
I ran into an interesting issue yesterday at work. There is a new video system
being installed, which takes the video output from computers, encodes it and
sends it as multicast to a controller. The controller then displays it on
a video wall. I had been told that the network has to support multicast.
As all the devices were residing in the same VLAN, I did not expect any issues.
However, the system was not able to receive the multicast. At first we expected
it could be the virtual environment and that the vSwitch did not support multicast,
because one server was deployed on the ESX cluster. The topology was this:
Multicast at Layer 2
Before describing the issue, let’s think about how multicast at layer 2 works.
The source will send to a multicast destination IP. This IP is the converted to a
destination MAC address. If the group is 227.0.0.1, this would map to the MAC
address 0100.5e00.0001. Switches forward multicast and broadcast frames to all
ports in a VLAN. This is not effective in the case of multicast as the traffic
may not have been requested by the host connected to Continue reading
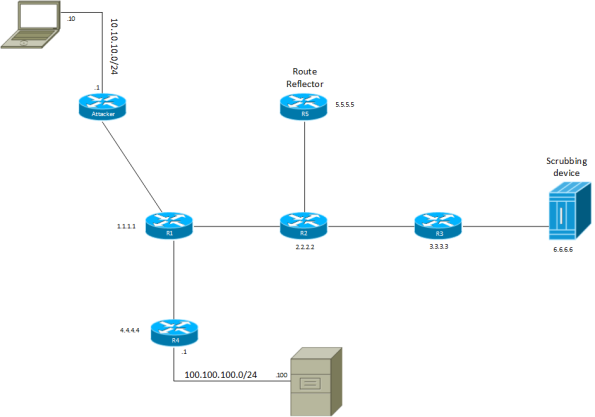
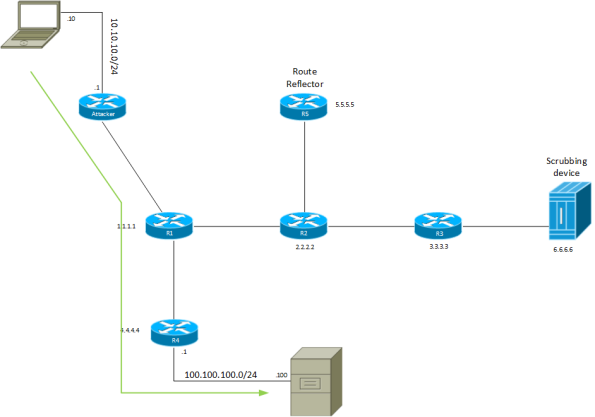
Routing Considerations in DDoS Protection Environments
Lately I have done some studying for the CCDE and one of the things I was
looking at is how to protect against DDoS attacks. I’m not expecting it
to be a big topic for the CCDE but it has some interesting concepts relating
to routing. Take a look at the following topology:
There is an attacker at the top left. R1 is the edge device and then there are a
few more routers, all peering BGP with the RR, which is R5. The server of interest
is 100.100.100.100 and there is a scrubbing device to the far right. All routers
peer iBGP from their loopbacks to the RR, including the scrubbing device.
Normally traffic to 100.100.100.100 would flow through R1 to R4 and then to the
server.
The attacker now starts to flood the server with malicious traffic. This is detected
by the DDoS scrubbing device which starts to announce via BGP a more specific route
than the one advertised by R4. R4 normally advertises 100.100.100.0/24 but the
scrubbing device advertises 100.100.100.100/32. All the other routers will start
to forward traffic to 100.100.100.100 towards Continue reading
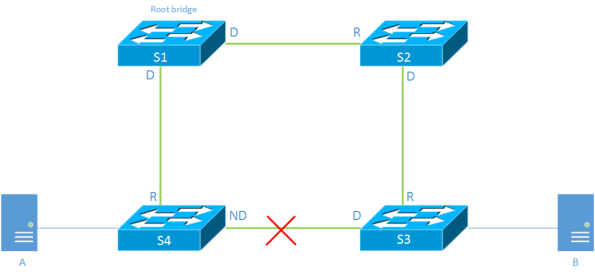
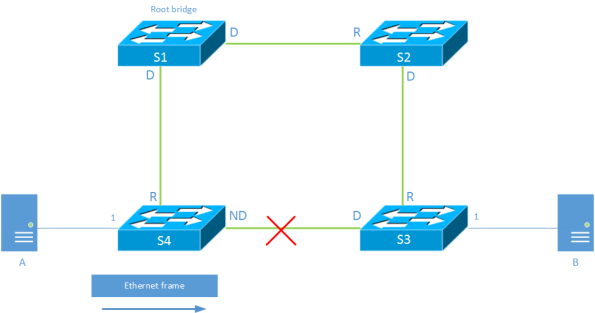
Ethernet, STP, Topology change and the behaviour of Ethernet
Introduction
This post is inspired by a post at IEOC about Uplinkfast and TCN which
can be found here.
Before we get to those parts, let’s recap how Ethernet and STP work together.
Spanning Tree
The Spanning Tree Algorithm builds a loop free tree by comparing Bridge ID(BID) and
least cost paths to the root bridge. By doing this it blocks all links not leading
to the root.
MAC Learning
Switches learn where to forward frames by looking at the source MAC address of the frame
on the port that the frame was received on. This learning is done in the data plane
as opposed to routing where the routes are learned in control plane. I will come back
to this later in the post.
S4 learns that A is located on port 1 after A has sent a frame. This is stored in
the MAC address table located in Content Addressable Memory (CAM). The CAM is a
fast memory optimized for quick lookups in the table. By default there is a 300
second aging timeout for learned MAC addressesm, meaning that if the switch
does not see any traffic from a source MAC within five minutes the entry will
Continue reading
Cisco now #1 on bladeservers in US with the Cisco UCS
Five years ago, Cisco started out on their journey to get in on the server market.
Very few people believed that Cisco would get a big share of the market.
Today, just five years later we are reached by the news that Cisco is now
the largest seller of blade servers in the US! From nothing to #1 in five
years, that is an impressive feat for sure!
This slide provides a summary of some of the statistics for UCS:
Over 33000 customers are now using UCS and it’s growing! Cisco is still showing
significant growth at 39% The only other vendors to show growth are Dell and Hitachi.
Cisco now has 40.9% of the blade server market in the US. Worldwide, Cisco is at #2
behind HP. I’m expecting this gap to decrease and I wouldn’t be surprised if Cisco
passes HP globally within a year or two as well.
The next slide is very interesting. Cisco went from nothing to #1 in five years.
IBM used to be a major player but now only has 10% of the market.
Not only has UCS been selling really well, it also has a lot of performance records.
Currently UCS Continue reading
A Short Update on CML from #CLUS
Hey everyone,
I’ve been having a really good time here at Cisco Live US. Here is a short update on CML.
General Info
CML is being released end of June or beginning of July. The corporate edition with
a base license and support for up to 15 nodes will be listed at around 13000$ per year.
If you subscribe for two years, the discount is 5% and for three years it is 10%
Normally 15 nodes cost around 13000$ per year so basically you get 5 nodes for “free”
if you get the base package which has the SKU R-CML-CE-K9=.
IOS will be supported by running IOSv. Every IOSv image requires around 512 MB of memory.
System Requirements:
- The Cisco Modeling Labs server runs on VMware ESXi 5.0, 5.1, and 5.5.
- Recommended – Cisco UCS®
- C220 M3 Rack Server with 16 core CPU and 128 GB memory or Cisco UCS
- C460 M2 High-Performance Rack Server or higher model (actual memory and CPU consumption depends
on the number of virtual nodes and virtual network OS types). To help determine the appropriate memory
please find the Cisco Modeling Labs Calculator at http://www.cisco.com/go/cml. - Following are the minimum hardware Continue reading