IPv6 Security Frequently Asked Questions (FAQ)

The Internet Society recognises that global deployment of the IPv6 protocol is paramount to accommodating the growth of the Internet. Given the scale at which IPv6 must be deployed, it is also important that the possible security implications of IPv6 are well understood and considered during the design and deployment of IPv6 networks, rather than as an afterthought.
We are therefore publishing our IPv6 Security Frequently Asked Questions (FAQ), which highlights and provides answers to the most important aspects of IPv6 security.
Be sure also to check our IPv6 Security page as well!
Further Information
The post IPv6 Security Frequently Asked Questions (FAQ) appeared first on Internet Society.
The Week in Internet News: Companies Encouraged to Conduct Q & AI
Uncomfortable AI: Inc.com has a story asking 16 “uncomfortable” questions that companies should ask about Artificial Intelligence. Among them: Are your reasons for deploying AI in the best long-term interests of humanity? And, how can we ensure that our behavior is inclusive?
Russia attacks fake news: Russian lawmakers have passed two bills, one that outlaws the spreading of fake news, at least as determined by the government there. Another bill makes it illegal to “disrespect” authorities in Russia, the BBC reports. Both bills come with heavy fines, and critics said the laws will limit the ability of journalists to report critical information.
The way forward: Facebook believes encrypted communications and privacy are its future, Recode reports. CEO Mark Zuckerberg outlined the website’s commitments to private messaging in a lengthy blog post.
The way backward: A teen who decided to get himself vaccinated said his mother got misinformation about the dangers of vaccines on Facebook, USA Today says. Ethan Lindenberger, an 18-year-old from Ohio, asked Reddit users if he should get vaccinated as an adult. There’s never misinformation on Reddit, of course.
Break ‘em up: U.S. Senator Elizabeth Warren, who is running for president in 2020, wants to break Continue reading
How IPv6 SLAAC responds to Renumbering Events

If you follow the IPv6 Maintenance (6man) Working Group of the Internet Engineering Task Force (IETF), you may have noticed the 300+ message email thread on an Internet Draft that was recently published on the “Reaction of Stateless Address Autoconfiguration (SLAAC) to Renumbering Events”. This was prompted by the experiences of developing Best Current Operational Practice on IPv6 prefix assignment for end-users, an activity led by ISOC’s Jan Žorž and published as ripe-690.
SLAAC is used to automatically assign an IPv6 address to a host, but there are a number of scenario where hosts may end up using stale configuration information and thereby leading to interoperability problems.
For example, a typical IPv6 deployment scenario is when a CPE (Customer Premises Equipment) router requests an IPv6 prefix to an ISP via DHCPv6-PD, and advertises a sub-prefix of the leased prefix on the LAN-side via SLAAC.
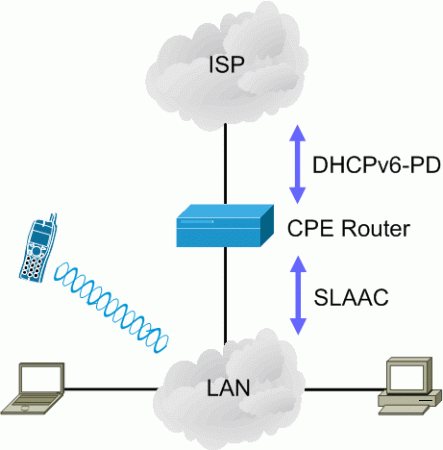
In such scenarios, if the CPE router crashes and reboots, it may lose all information about the previously leased prefix. Upon reboot, the CPE router may be leased a new prefix that will result in a new sub-prefix being advertised on the LAN-side of the CPE router. As a result, hosts will normally configure addresses for the newly-advertised prefix, Continue reading
Seven Women Using the Internet to Make a Difference

We’re celebrating International Women’s Day this year with great news: The Internet Society welcomes a new Chapter in Lesotho – and the Chapter’s president, vice president, treasurer, secretary, as well as a board member are all talented tech women.
Lesotho is a small landlocked country within South Africa, where less than a third of its population is connected to the Internet. One of the Lesotho Chapter’s key priorities this year is to start an “Internet for Education” project, which aims to encourage five schools to use the Internet to support teaching and to improve the quality of education.
Please join us in welcoming the Lesotho Chapter, then learn about its President Ithabeleng Moreke and other women around the world who are using the Internet to make a difference in their communities!

Ithabeleng Moreke enjoys the world of the Internet and all things networks, the technology behind it, and Internet security – and how they affect our everyday lives. She’s worked as network engineer for the government of Lesotho and is now with Vodacom Lesotho.

In Jazmin Fallas Kerr’s hometown, Desamparados, Costa Rica, nearly half of all families with women as head of household are in Continue reading
Deutsche Welle Profiles Community Networks Around the World

How can the Internet change lives in rural and remote regions? Deutsche Welle, Germany’s public broadcaster, asks these questions in three stories that explore community networks in Zimbabwe, the Republic of Georgia, and South Africa.
Read about the community networks and listen to their stories!
Murambinda Works started as an Internet café in 2002 in the Buhera District in eastern Zimbabwe. Since then it’s grown to provide training in computer literacy for teachers at nearly 218 primary and secondary schools. Murambinda Works, in partnership with the Internet Society and others, is also working to connect eight schools, one nurse training school, and offices of the Ministry of Education.
Tusheti, a mountainous, isolated region in the Republic of Georgia, had been left unconnected by commercial operators. The Internet Society partnered with its Georgian Chapter and other local organizations to help build access to the Internet, which was completed in 2017. (The Tusheti community network was also profiled in The New York Times.)
The Zenzeleni Network in Mankosi, is one of South Africa’s most economically disadvantaged communities. Zenzeleni – which means “do it yourself” in the local language, isiXhosa – was launched in 2012 to provide affordable voice service Continue reading
The Week in Internet News: Many Ugandans Quit Internet Services After Tax on Social Media

Taxing the Internet: A social media tax in Uganda has prompted many users to quit those same sites, The Guardian reports. The tax, intended to raise government revenues and discourage “idle talk,” amounts to 200 Ugandan shillings, or about U.S. 5 cents, per day. More than one million people have quit taxed mobile apps, the story says.
Tough measures: A large majority of Europeans support a proposal to require social media companies to direct all users who have seen take news toward fact-checks, Time.com says. A recent poll suggest that more than 86 percent of European residents surveyed support the Correct the Record proposal from advocacy group Avaaz.
Blockchain goes to pot: Blockchain technology can help marijuana dispensaries enforce daily legal limits on individual purchases, Forbes reports. Blockchain could help dispensaries keep track of attempts at smurfing, the practice of purchasing more than the daily legal limit by going to different dispensaries, and looping, purchasing more than the limit by returning later to the same seller, the story says.
Blockchain vs. censorship: A follow-up to a trend we noted earlier this year: China’s residents are turning to blockchain technologies to fight government censorship, The Conversation reports. Some users Continue reading
Internet Society Welcomes the Dominica Chapter

A new Internet Society Chapter had been founded within the Regional Bureau in Latin America & Caribbean. The creation of the Internet Society Dominica Chapter was officially launched on January 11, at the Fort Young Hotel in Roseau City. The event was attended by 25 people, several key stakeholders from two major ISPs, as well as government representatives.
We would like to extend a warm welcome to all members and to the new Chapter executives (pictured above from left to right): Craig Nesty (President), Grayson Stedman Jr. (Vice President), Ishmael Joseph (Secretary), and Austin Lazarus (Treasurer).
 “The Chapter was founded by staff members of the National Telecommunications Regulatory Commission” says Melisha Toussaint, NTRC Assistant Engineer and Chapter member. “In recent times, the NTRC has updated its mandate not only to regulate the telecommunications industry in Dominica, but also to create an enabling environment for the growth and development of the Internet and ICTs.”
“The Chapter was founded by staff members of the National Telecommunications Regulatory Commission” says Melisha Toussaint, NTRC Assistant Engineer and Chapter member. “In recent times, the NTRC has updated its mandate not only to regulate the telecommunications industry in Dominica, but also to create an enabling environment for the growth and development of the Internet and ICTs.”
What are the key interests of the new Chapter?
One of the key goals is to support the Dominica government’s idea to create a climate resilient country following the passage of Hurricane Maria in 2017. The disaster helped realize the importance of communication post-disaster. In 2019, Continue reading
NDSS 2019 Honors Timeless Papers

The papers and presentations are done, the awards and appreciation certificates have been handed out, and the boxes are packed and labeled for shipping. NDSS 2019 has come to a successful close. It was a record setting event with over 550 registrations, 89 papers, 36 posters, and four workshops. It was inspiring to see such energetic and passionate security research professionals gathered together in one place discussing their work. All of the highlights can be found at the NDSS 2019 website, including the Distinguished Paper and Distinguished Poster Awards for this year and the full program. It is worthwhile, however, to highlight a new award series initiated this year.
NDSS Test of Time Awards
This year, to kick off the second 25 years of NDSS, an NDSS Test of Time annual award was created. This award is for papers that were published more than ten years ago and have had a significant impact on both academia and industry in the years since. There were three awardees in the inaugural class.
The first Test of Time award is from 1996: SKEME: A Versatile Secure Key Exchange Mechanism for Internet by Hugo Krawczyk. SKEME was an integral component of early versions of Continue reading
The Global Internet Report: Consolidation in the Internet Economy

The 2017 Global Internet Report: Paths to Our Digital Future focused attention on the significant potential of the Internet for innovation and sustainable development, but without denying or shirking the challenges it also introduces. This forward-looking analysis is a powerful advocacy tool for anyone who wants to protect and build the open Internet.
Over the past year, we spent time working with our community on a new report. It takes a closer look at one of those forces and how it may impact the future: Consolidation in the Internet Economy. Understood as growing forces of concentration, vertical and horizontal integration, and fewer opportunities for market entry and competition, this topic includes the impact of consolidating forces on all stakeholders as well as on the Internet’s underlying and evolving technology.
We chose this theme because findings from the 2017 report, and what’s happened since, are showing increasing concerns about a growing concentration of power in the Internet economy. They point to market and technical forces that may be driving consolidation at different “layers” of the Internet, from network developments and hosting services to applications. Among these trends are processes that enable some companies to own our experience at almost every stage.
The Week in Internet News: IoT Botnets Come for Video Conferencing Systems

Botnets attack: A handful of botnets using compromised Internet of Things devises are now targeting enterprise video conferencing systems, reports CSO Online. Three recently identified botnets are based on the Mirai botnet, which had its source code leaked back in 2016. The original Mirai is no longer active, but its source code has served as the base for at least 13 other botnets.
Pulling the plug: Internet shutdown are common, but ineffective, argues a journalist and researcher on The Conversation. Shutdowns “seem to animate dissent and encourage precisely the kind of responses considered subversive by many governments,” writes George Ogola. “Internet shutdowns don’t stop demonstrations. Nor do they hinder the production and circulation of rumours: they encourage them instead.”
The war on porn: Meanwhile, the government of Bangladesh has shutdown about 20,000 websites, including some popular social media sites, in the name of banishing pornography, the Guardian reports. Authorities believe some social media sites are contributing to the problem, apparently.
Digital colonies? The BBN Times has a provocative opinion piece suggesting that the Internet, and Internet Governance, is aiding in a process of “digital colonization.” The U.S. is sending its language, culture, and tech products Continue reading
RIRs enhance support for routing security

BGP hijacking and route leaks represent significant problems in the global Internet routing systems, along with source address spoofing. BGP hijacks are where allocated or unallocated address space is announced by entities who are not holders and are not authorized to use it.
The announcement of allocated address space often creates big news, such as when 53 route prefixes of Amazon were hijacked, but the announcement of unallocated address space (whether IPv4, IPv6 or AS numbers) which are also known as ‘bogons’ often does not generate much publicity as it does not cause immediate disruptions to service or business. With depletion of the IPv4 address space though, the announcement of bogons are on the rise with miscreants scraping the unallocated address space from all RIRs and abusing it.
Resource Public Key Infrastructure (RPKI) was therefore developed to try to solve these problems, and APNIC (the Routing Internet Registry for the Asia-Pacific region) recently announced it will honour the creation of AS0 ROA objects. They join ARIN, AfriNIC and the RIPE NCC in supporting AS0 ROA objects, with only LACNIC yet to implement this.
APNIC members can create AS0 ROAs for the prefixes they manage using the MyAPNIC platform.
So, Continue reading
NDSS 2019 Highlights the Best in Security Research

Tomorrow, the 26th consecutive Network and Distributed System Security Symposium (NDSS) is set to kick off in San Diego, CA. NDSS is a premier academic research conference addressing a wide range of topics associated with improving network and system security. A key focus of the Internet Society has long been improving trust in the global open Internet and all of its connected devices and systems. In today’s world, we need new and innovative ideas and research on the security and privacy of our connected devices and the Internet that connects them together.
NDSS 2019 (24-27 February) will be the biggest NDSS symposium yet, featuring 89 peer-reviewed papers, 35 posters, 4 workshops, and a keynote. Record registration numbers are a key indicator that NDSS 2019 is featuring vital and timely topics. Below are some of the highlights expected in the coming week.
Workshops
This year’s program officially starts with four workshops on Sunday, 24 February. NDSS workshops are organized around a single topic and provide an opportunity for greater dialogue amongst researchers and practitioners in the area. Each of this year’s workshops have dynamic agendas.
The Workshop on Binary Analysis Research (BAR) is returning for its second year at NDSS after a Continue reading
Philippines Adopts the Multistakeholder Model for Policy Development

Yesterday in Manila, the Philippines launched its national information and communications technology (ICT) framework, which lays out how digital transformation will empower citizens and the economy as a whole.
The National ICT Ecosystem Framework (NICTEF), is a successor to the Philippine Digital Strategy initiative from 2011-2016. Its plans, programs, and projects will be updated periodically as the government continually considers comments from all sectors of society and other indicators and results.
The release of NICTEF is remarkable in many ways. It was developed in a collaborative way, with stakeholders from multiple sectors engaged in dialogue and discussions to help inform and build an inclusive framework.
NICTEF is a living document. Subcommittees will gather ongoing feedback and updates will be made available on the framework’s website.
Considering the faltering international cooperation in Internet policymaking and the trend towards unilateral policies, it takes determination and belief for a government to embark on a landmark multi-year initiative that has at its core a multistakeholder approach.
This commitment is all the more remarkable for a developing country like the Philippines, where the levels of Internet use and literacy vary greatly from region to region. The Department of Information Communications Technology (DICT) recognized right from Continue reading
Developing good BGP neighbour relationships @ APRICOT 2019

Routing Security is featuring heavily on the APRICOT 2019 programme, which is being held on 23-28 February 2019 in Daejeon, South Korea. This helps build on the MANRS initiative being supported by the Internet Society,
On Wednesday, 27 February (09.30-13.00 UTC+9) there will be a Routing Security session that will discuss the latest problems, developments, and how routing security measures can be implemented. Speakers include Job Snijders (NTT) who’ll be discussing changes to BGP in the coming 18 months; Töma Gavrichenkov (Qrator Labs) on how BGP hijacks can be used to compromise the digital certificates used to secure online transactions; and from Anurag Bhatia (Hurricane Electric) who’ll analyse the top misused ASNs.
During the second part of the session, Tashi Puntsho (APNIC) will cover the practical issues and implications of deploying your own RPKI Certificate Authority; Tim Bruijnzeels (NLnet Labs) will discuss the use of route servers at Internet Exchange Points; whilst Ed Lewis (ICANN) will discuss the issues with using the RIR Whois databases.
Following on from this, our colleague Andrei Robachevsky will be raising awareness of the MANRS Initiative during the FIRST Technical Colloquium (16.30-18.00 UTC+9).
FIRST is the global organisation of Computer Security Continue reading
DNS Privacy & IPv6 Security @ APTLD 75

The Internet Society will be actively contributing to the APTLD 75 meeting on 20-21 February 2019 in Dubai, United Arab Emirates.
Our colleague Jan Žorž will not only be presenting on DNS-over-TLS (DoT) and DNS-over-HTTPS (DoH) during the DNS Operations, Security, and Privacy session (20 February, 11.30-12.30 UTC+4), but will then be presenting on IPv6 connectivity issues during the Security in IPv6-enabled TLDs session (20 February, 14.30-15.30 UTC+4).
He’ll be in good company in what’s shaping up to be a great programme featuring a number of DNS luminaries covering technical, policy, internationalisation and data protection issues, as well as abuse handling and registry and registrar training. Other sessions of particular interest include 5G mobile networks, the implications of Alternative DNS Root Servers, and emerging trends in the DNS.
The Asia-Pacific Top-Level Domain (APTLD) Association is a non-profit organisation of ccTLD (Country Code Top-Level Domains) registries in the Asia-Pacific region that was founded in 1998. It organises two meetings each year for its members, with APTLD 75 being held in conjunction with the 6th Middle East DNS Forum.
If you’re interested in attending then you can register at http://www.aptld75.ae/reg/end.php
Further Information
The Week in Internet News: Researchers Develop AI Writing App but Worry about Fake News

Too easy to fake: OpenAI, a research institute in San Francisco, has developed an Artificial Intelligence program to write news articles, but has declined to release a full-featured version of it because of fears that the AI could easily produce fake news, the MIT Technology Review says. OpenAI, associated with AI skeptic Elon Musk, will make only a simplified version publicly available. The institute will publish a research paper outlining its work.
Secure your IoT: Eleven organizations, including the Internet Society and Mozilla, have asked retailers to stop selling Internet-connected devices that don’t meet minimum security and privacy requirements, Techbizweb reports. A letter from the organizations, sent to Target, Walmart, Best Buy, and Amazon, asks them to publicly endorse minimum security and privacy guidelines for Internet of Things devices.
Competing in AI: U.S. President Donald Trump has signed an executive order meant to boost AI development in the country, The Hill reports. The order comes as some AI experts fear the U.S. is losing ground to China. Trump’s order directs federal agencies to prioritize and set aside funding for AI programs.
Broadband for all: Botetourt County in Virginia, where only about 70 percent of residents have access to Internet Continue reading
Learn More about IXPs at the Middle East Network Operators Group

Internet Exchange Points are now considered to be an integral part of the Internet infrastructure worldwide. In very simple terms they are layer 2 switches that are used to route traffic that can be kept local instead of sending that traffic to the nearest major Internet node (usually located in Europe) and back. None of the countries of the Middle East contain enough globally-connected major Internet infrastructure so basically, all Internet traffic generated and terminated in the same country has to be routed through Europe. With well-implemented Internet Exchange Points, local Internet traffic stays local. Examples of local Internet traffic are financial transactions with your bank through online banking, requesting copies of your birth record from an e-government service, or any interaction with locally-hosted content.
Internet Exchange Points have three main benefits: lower latency, better cost efficiency, and control-of-traffic-sovereignty.
In the day and age of instant gratification and communications through social media and videos, latency, or the time it takes to fetch a web page, needs to be minimal and under 10ms as per industry standard (every 100km causes 1ms delay). In order to optimize the user experience, content providers have built their own global networks and spread their servers Continue reading
We Are on This Road Together

Twenty-six-year-old software engineer Akah Harvey N L has fun building things and sharing his knowledge with local communities in Cameroon. While an undergraduate, Akah took part in the Google Summer of Code, giving him the opportunity to develop an application for one of the largest software organizations in the world. He is now a code reviewer for the online learning platform, Udacity, and leads software development training at Seven Academy in Cameroon. Akah is a 25 under 25 awardee and a cofounder of Traveler, a road safety and emergency app.
I am a software engineer and it’s hard to talk about anything I do without talking about the Internet. Beyond using the Internet for communication – reducing the distance between people with a speed that’s yet unrivaled – lies the gamut of useful services that help me accomplish my day-to-day tasks, like running client-server applications, downloading tools for my work, synchronizing software projects, collaborating on global impactful software projects with people I have never met, mentoring people online who are learning how to code on MOOC platforms, and even traveling the world. The ways in which the Internet simplifies peoples’ lives is difficult to accurately quantify. From social media Continue reading
Do You Want Privacy With That?

You may have heard about CloudPets being pulled off shelves for recording kids’ voices and that data being leaked, or the EU recalling kids’ smart watches for giving away children’s location in real time. If you’re shopping for any sort of Internet-connected device, you should be worried about your privacy and investigating how much data your new gadget is collecting. That’s why we’ve joined Mozilla in calling on big retailers in the US like Target, Walmart, Best Buy, and Amazon to publicly endorse and apply our minimum security and privacy guidelines and stop selling insecure connected devices.
From the letter: “Given the value and trust that consumers place in your company, you have a uniquely important role in addressing this problem and helping to build a more secure, connected future. Consumers can and should be confident that, when they buy a device from you, that device will not compromise their privacy and security. Signing on to these minimum guidelines is the first step to turn the tide, and build trust in this space.”
In total, the letter is co-signed by 11 organizations: Mozilla, Internet Society, Consumers International, ColorOfChange, Open Media & Information Companies Initiative, Common Sense Media, Story of Continue reading
Future Thinking: Alissa Cooper on the Technical Impact of Internet Consolidation

In 2017, the Internet Society unveiled the 2017 Global Internet Report: Paths to Our Digital Future. The interactive report identifies the drivers affecting tomorrow’s Internet and their impact on Media & Society, Digital Divides, and Personal Rights & Freedoms. While preparing to launch the 2019 Global Internet Report, we interviewed Alissa Cooper to hear her perspective on the forces shaping the Internet’s future.
Alissa Cooper is a Fellow at Cisco Systems. She has been serving as the Chair of the Internet Engineering Task Force (IETF) since 2017. Previously, she served three years as an IETF Applications and Real-Time (ART) area director and three years on the Internet Architecture Board (IAB). She also served as the chair of the IANA Stewardship Coordination Group (ICG). At Cisco, Cooper was responsible for driving privacy and policy strategy within the company’s portfolio of real-time collaboration products before being appointed as IETF Chair. Prior to joining Cisco, Cooper served as the Chief Computer Scientist at the Center for Democracy and Technology, where she was a leading public interest advocate and technologist on issues related to privacy, net neutrality, and technical standards. Cooper holds a PhD from the Oxford Internet Institute and MS and BS Continue reading