Palo Alto Traps: The End for AV and EDR?
The world of malware and exploits has a long history, and anyone involved in this industry knows that we are at a tipping point. Threats continue to evolve, from the first viruses seen in the wild back in 1982, to the modern day malware of today that’s capable of spreading laterally in the blink of …Chinese Malware ‘Fireball’ Has Infected 250 Million Devices
A malware attack dubbed Fireball has infected more than 250 million computers worldwide and is redirecting web browsers on compromised machines to generate revenue for its attackers. First discovered by cybersecurity firm Check Point Threat Intelligence, the browser-hijacking malware attack of Chinese origin has reportedly spread to 20 percent of corporate computer networks. Read: Android …Continue reading "Chinese Malware ‘Fireball’ Has Infected 250 Million Devices"
Intel’s new chip puts a teraflop in your desktop. Here’s what that means
It’s as fast as a turn-of-the-century supercomputer. Intel’s Core i9 Extreme Edition processor costs about $2,000. Intel Corporation Earlier this week in Taipei, Intel announced the most powerful desktop chip for consumers that it has ever sold. With 18 cores and a price tag of $1,999, the processor is known as a teraflop chip, meaning …Continue reading "Intel’s new chip puts a teraflop in your desktop. Here’s what that means"
Juniper Data Center Cohesion Wrap Up
Finally getting caught up with work since my time in Cali and although this post is a little late, I wanted to take a moment to capture my thoughts on Juniper Network’s Data Center Cohesion event which took place in Sunnyvale at Juniper’s Aspiration Dome last week. I had an awesome time and the sessions …Preparing for the Juniper Networks Certified Design Associate (JNCDA) Exam
Recently I set my sights on Juniper Networks‘ Design track as I am working with customers on an almost daily basis with regards to Data Center design. As such the Juniper Network Design – Data Center curriculum and associated JNCDS-DC certification looked very appealing. To top that off, according to Certification Magazine, the JNCDA and the JNCDS-DC certifications …Continue reading "Preparing for the Juniper Networks Certified Design Associate (JNCDA) Exam"
Understanding the Federal Government’s Rapid Adoption of Cloud
One of the biggest trends in the IT industry at the moment is enterprise adoption of the public cloud. It’s obvious that it’s been accelerating over the recent years, but perhaps more importantly, Federal agencies are beginning to take a serious look at the cloud in an effort to reform IT and to achieve greater agility …Continue reading "Understanding the Federal Government’s Rapid Adoption of Cloud"
Network Modernization Webinar Now Available Online
On February 8th I gave a webinar on network modernization initiatives with Doug Nash, the Deputy Chief Information Officer, Operations & Infrastructure at the USDA. I thoroughly enjoyed the opportunity to speak with Doug and discuss some of the new directions that various Federal agencies are undertaking to create more modernized and agile networks. This webinar is now available …Continue reading "Network Modernization Webinar Now Available Online"
An Inside Look at Juniper Networks’ Forthcoming JNCIE-DC Exam
Data Centers and the Cloud are all the rage right now, and Juniper has been at the forefront of the Data Center revolution from the very beginning – early on with their introduction of the QFX and the much maligned QFabric, and more recently with the addition of Virtual Chassis Fabric (VCF), various open architectures …Continue reading "An Inside Look at Juniper Networks’ Forthcoming JNCIE-DC Exam"
How to Hack an Election
Now that the election is behind us, the discussion has turned to potential involvement by foreign governments and whether they had their hand in altering the course of US democracy by tampering with the integrity of our election systems. The CIA has all but admitted that there was definite Russian interference aimed at tilting our election. The Green … Continue reading How to Hack an ElectionJuniper Ambassador
I am delighted to announce that earlier this week I was accepted into Juniper’s Ambassador program. To say that I am completely honored is an understatement. Working with Juniper’s products and technologies has been a labor of love for me dating back almost 18 years, since my first introduction to Junos back in early 1999 — … Continue reading Juniper AmbassadorHow to Spot a Fake Facebook Account
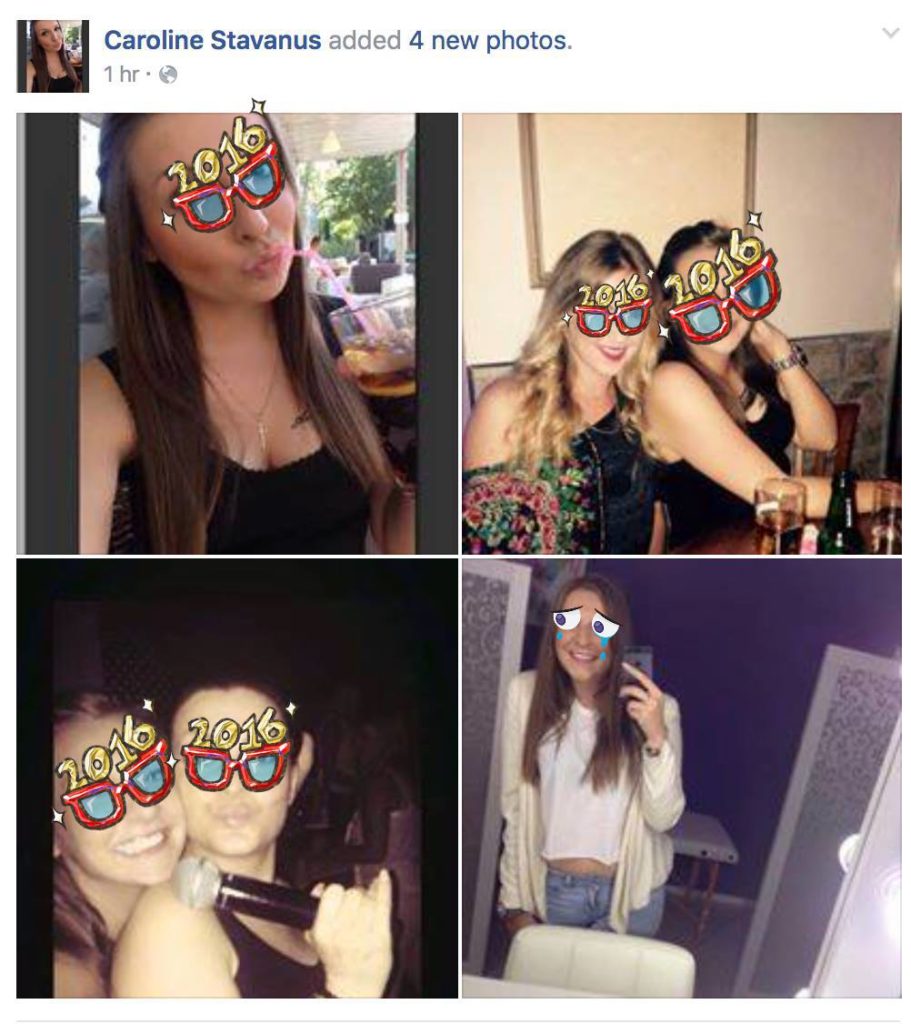
Ever get a friend request from someone you don’t know and have never met before? More often than not, these accounts are created by criminals looking to harvest your personal information, or scam you in some other fashion.
It typically starts when you receive a friend request from someone you don’t know. And you have no mutual friends in common:
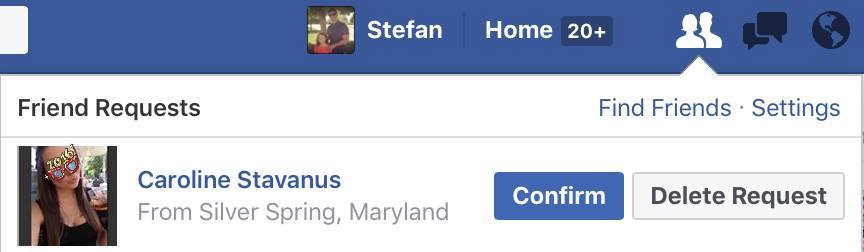
A dead giveaway is looking at their Recently Added Friends. In this case, this person has accumulated a lot of new friends in a very short period of time. Notice they are all guys. Guys are more willing to accept a friend request from someone they don’t know, especially if it’s attached to a pretty face.
Also note that there are no mutual friends in common:
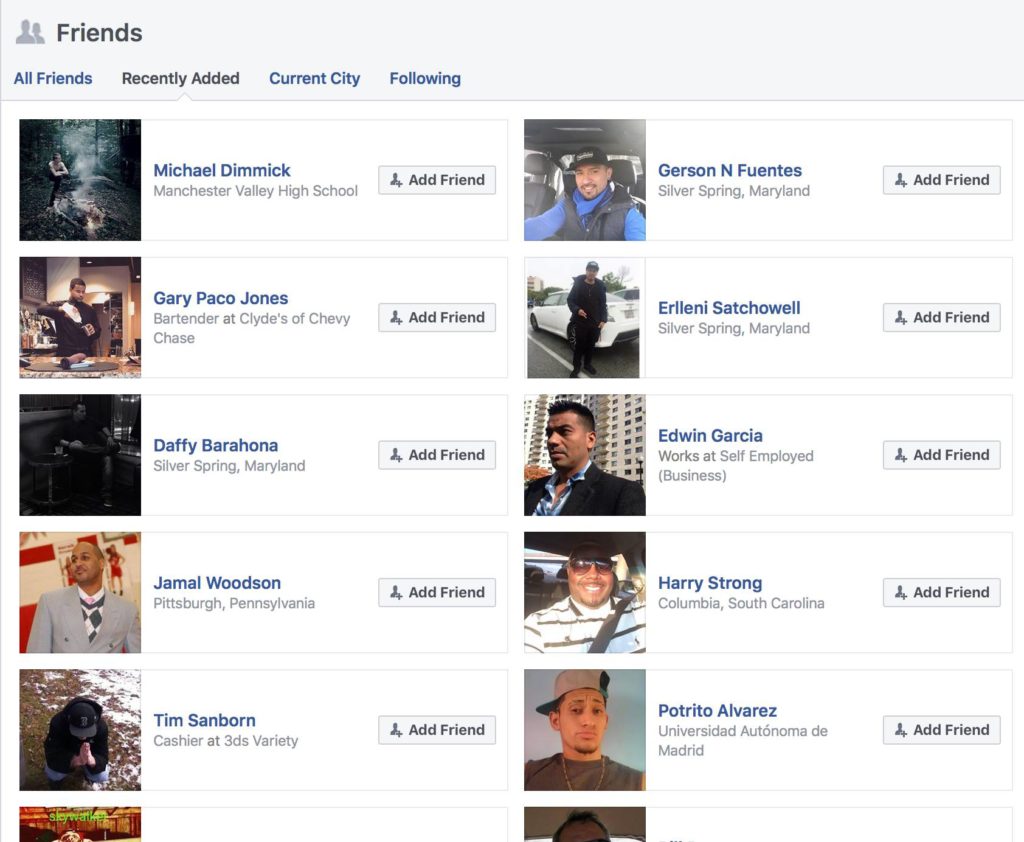
Another tell tale sign is that all the pictures associated with the account have been added quite recently, in this case, in the last hour. This indicates this is a new account, not one that has been a legitimate account for a long time:
NOTE: Pictures have been masked to protect the innocent. In this case, some unknowing girl has had her pictures harvested by the scammer for the purpose of running this endeavor.
If they don’t respond to an inquiry Continue reading
The Changing Landscape of Selling in the Age of SDN
There are massive waves of technology upheaval taking place in the marketplace, causing disruption and providing a challenge to technology salespeople who are used to selling in the traditional ways. Cloud, Automation, Mobility, Adaptive Security and the Internet of Things are just a few of the major changes affecting the landscape right now. And while these technologies are certainly challenging in their own right, there is one technology that stands on it’s own, not only in terms of how technology decisions are made, but also how technology is bought.
That technology is Software Defined Networking (SDN). SDN is causing a fundamental shift in the way that technology is procured. There is a major shift away from buying point products and technologies which only meet a specific need and instead looking at the bigger picture with an aim of technology procurement fitting into a larger ecosystem that is providing broader solutions, enabling shorter ROI and better business agility.
Application-Centricity Creates New Stakeholders
The buying process used to be relatively straightforward, and different technology groups within an organization could procure technology within their own silo with little regard to how it fit within the broader ecosystem. Often times, the technology implemented would dictate and limit what applications could Continue reading
Book Review :: Juniper QFX5100 Series: A Comprehensive Guide to Building Next-Generation Networks
 Juniper QFX5100 Series: A Comprehensive Guide to Building Next-Generation Networks
Juniper QFX5100 Series: A Comprehensive Guide to Building Next-Generation Networks
by Douglas Richard Hanks, Jr.
Paperback: 3 pages10
Publisher: O’Reilly Media
ISBN-13: 978-1491949573
![]()
Much more than just a book about the QFX5100
This was an easy weekend read, and quite honestly I’d never thought I’d say this about a technical book but I literally could not put the book down. Doug has amassed a wealth of great information, approaching the subject matter from a standpoint of brevity, applying the Goldilocks principle — not too much and not too little — but rather just the right amount of information.
Do not be confused by the title — this is not JUST a book about the QFX5100 series. As the subtitle might indicate, it’s more of a book on building next-gen networks, specifically Data Center networks, and serves as a fantastic primer on the various protocols and technologies that are becoming the mainstay of this world.
As the networking world works overtime to catch up to the virtualization offered by storage and compute resources, the reader tasked with creating the network of tomorrow will appreciate the coverage of building various types of fabrics of varying dimensions — whether it’s coverage of Juniper’s Virtual Chassis Fabric for building small to Continue reading
Carrier Grade NAT and the DoS Consequences
Republished from Corero DDoS Blog:
The Internet has a very long history of utilizing mechanisms that may breathe new life into older technologies, stretching it out so that newer technologies may be delayed or obviated altogether. IPv4 addressing, and the well known depletion associated with it, is one such area that has seen a plethora of mechanisms employed in order to give it more shelf life.
In the early 90s, the IETF gave us Classless Inter-Domain Routing (CIDR), which dramatically slowed the growth of global Internet routing tables and delayed the inevitable IPv4 address depletion. Later came DHCP, another protocol which assisted via the use of short term allocation of addresses which would be given back to the provider's pool after use. In 1996, the IETF was back at it again, creating RFC 1918 private addressing, so that networks could utilize private addresses that didn't come from the global pool. Utilizing private address space gave network operators a much larger pool to use internally than would otherwise have been available if utilizing globally assigned address space -- but if they wanted to connect to the global Internet, they needed something to translate those addresses. This is what necessitated the development of Network Address Translation (NAT).
NAT Continue reading
Is DDoS Mitigation as-a-Service becoming a defacto offering for providers?
Republished from Corero DDoS Blog
It’s well known in the industry that DDoS attacks are becoming more frequent and increasingly debilitating, turning DDoS mitigation into a mission critical initiative. From the largest of carriers to small and mid-level enterprises, more and more Internet connected businesses are becoming a target of DDoS attacks. What was once a problem that only a select few dealt with is now becoming a regularly occurring burden faced by network operators.
In my daily engagements with various customers of all shapes and sizes, it’s truly interesting to see how the approach to DDoS mitigation is changing. Much of this is the result of DDoS mitigation services shifting from a “nice to have” technology to a “must-have”, essential in order to maintain business continuity and availability.
When I built DDoS mitigation and detection services for Verizon back in 2004, the intent was to offer value-add revenue producing services to offer subscribers, in an effort to build out our security offerings. For many years, this concept was one that pretty much every provider I worked with was looking into; build a service with the intent of generating new revenue opportunity from customers when traditional avenues such as Continue reading
Juniper Networks Announces New Network Design Training Curriculum and Certification Program
Juniper took a big step forward in rounding out their certification programs by announcing a new Design Training and Certification curriculum, focusing on best practices and techniques that can be used across the spectrum of network architecture and design. Slated to be included in this program are also technologies around software-defined networking (SDN) and network functions virtualization (NFV).
This is a huge step forward for Juniper's training and certification program and will round out their education portfolio with something similar to Cisco's design certification. Furthermore with the advent of network automation, and SDN and NFV technologies becoming more commonplace, the benefits from such a training and certification curriculum can't be overstated.
The design curriculum will eventually include a portfolio of training offerings, starting with the first course which is available now, the Juniper Networks Design Fundamentals course. These courses and their corresponding design certifications will focus on the latest techniques, resources and various tools that companies can use to fully design, secure, and automate their networks. Trainings will range all the way from design fundamentals on through to more advanced courses covering the design specific requirements of Data Center and WAN networks. The first certification, Juniper Networks Certified Design Associate (JNCDA) is available for registration now, Continue reading
What’s a Steiner Tree?
Any of you who have worked with VPLS or NG-MVPNs are likely already familiar with using Point-to-Multipoint (P2MP) LSPs to get traffic from a single ingress PE to multiple egress PEs. The reason that P2MP LSPs are desired in these cases is that it can reduce unnecessary replication by doing so only where absolutely required, for example where a given P2MP LSP must diverge in order to reach two different PEs.
However, typically the sub-LSPs which are part of a given P2MP LSP traverse the shortest-path from ingress to egress based on whatever user defined constraints have been configured. While this is fine for many applications, additional optimizations might be required such that additional bandwidth savings can be realized.
We will take a look at something called a Steiner-Tree which can help the network operator to realize these additional savings, when warranted, reducing the overall bandwidth used in the network and fundamentally changing the way in which paths are computed.
Let's start by taking a look at a simple example in which RSVP is used to signal a particular P2MP LSP, but no constraints are defined. All the links in this network have a metric of 10. Continue reading
Preparation Tips for the JNCIE-SEC Exam
Not a day that goes by since having passed the JNCIE-SEC exam that I don't receive an inquiry in one form or another regarding how I prepared for the exam. It seems that there is an incredible amount of interest in this exam, especially from all those die-hard ScreenOS folks that are now converting to Junos. So instead of constantly repeating myself, I figured I'd just put it up on the blog so others can benefit (leaving me more time to do other things, 'heh).
NOTE: For full disclosure, I must reveal that I am an Technical Trainer and Certification Proctor at Juniper Networks. As such, I take EXTRA responsibility towards protecting the content and integrity of the exam and I take the certification credentials very seriously. Not only that, I worked REALLY, REALLY hard to achieve my JNCIE certifications, and I believe everyone else should too! As such, I kindly ask that candidates refrain from asking me questions which would be considered a violation of the NDA. Also, I should add that although I work for Juniper, the viewpoints expressed in this article are my own and may not necessarily be shared by my Continue reading
Black Hat OSPF Vulnerabilities: Much Ado About Nothing
Imagine a group of researchers planning to speak at a conference regarding a previously undiscovered vulnerability present in most homes that would allow a thief to rob your home of its valuables with complete ease. You would probably be interested in hearing what they had to say so you could take the necessary precautions to protect your home.
Now imagine when they presented their findings, they went on to state that it was incredibly easy to do, so long as you left your front door open and also provided them with the security code for any alarm systems. You would probably find this implausible and simply the proliferation of fear, uncertainty, and doubt.
That's precisely what happened last week at the well-respected Black Hat security conference in Las Vegas when researchers from the Israel Institute of Technology and Advanced Defense Systems, Ltd. presented their findings of a serious vulnerability present in OSPF. So serious in fact, the researchers stated the only way to properly mitigate the threat, short of fixing the protocol, is to switch to another routing protocol such as RIP or IS-IS.
The researchers went on to present their research of two previously undiscovered methods Continue reading
Juniper SRX Tips :: Altering Default-Deny Behavior
In our previous article, we looked at using apply-groups to alter all the security policies uniformly on an SRX device such that they would all have an implicit logging statement. And while this is fine for all existing policies, it doesn't log traffic which doesn't match any explicitly defined security policy.
The reason for this is due to the fact that in Junos, traffic which doesn't match an explicitly defined security policy matches against the default-deny policy. However, given the fact that the default-deny policy is implicitly defined, apply-group configurations are of little benefit as apply-groups can only be inherited by those elements which have been explicitly defined.
Often in these cases, administrators will simply choose to create their own deny policies with the desired options and place this deny policy as the last policy for traffic going from one zone to another. However, in instances where there are many zones, it might prove too cumbersome and time consuming to manually configure this to accommodate all zones.
Clearly it would be more beneficial to have something akin to the Global Zone in ScreenOS which can be used to match on all traffic which doesn't match against any of Continue reading