Quick ACL Entry Comparison Script
The ACL_compare function takes two lists of strings and compares the first to the second and returns a list comprising strings that are present in the first that are not in the second.
The listconvert function converts a file read into memory into a list of strings. Handy for when you use filenames as arguments when you run the script.
Essentially it’s all just string comparison really.
def ACL_compare(fwsm_ACL,asa_ACL):
comparison=[]
for line in fwsm_ACL:
if line in asa_ACL:
pass
else:
comparison.append(line)
return comparison
def listconvert(file):
newlist=file.readlines()
return newlist
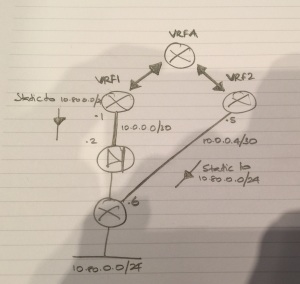
VRF Race Condition
A while ago I observed an interesting problem due to a routing misconfiguration. An asymmetric route was introduced across two discrete switches/routing instances. The route was then imported in a separate location.
When I began troubleshooting I was under the impression that the importer preferred one route over another because of admin distance or some other metric, or perhaps it was some sort of BGP esoterica you’d only encounter if you were using VRFs and MP-BGP to learn routes. However, the truth was probably something more prosaic.
Both routes were static routes. This meant their learning mechanism across importers was the same. The reason the importer preferred one route over another was probably due to one entering the routing table before the other.
Simple Bash Ping Script
Been looking for something like this for a while:
http://etherealmind.com/tech-notes-ping-sweep-ip-subnet/
for i in `seq 1 255`; do ping -c 1 192.168.1.$i | tr \n ‘ ‘ | awk ‘/1 received/ {print $2}'; done
I usually use nMAP for this, but in some instances you may not have access to it. For those times, Bash should work really well.
Android Bugs
I have a little Samsung Galaxy S2 which is a perfectly adequate phone. I use the Google Apps on it to keep some semblance of order in my life. However, I run into some occasional bugs which require a bit of work to solve. So I’m putting in the fixes here so they’re easily available.
1. Weather widget displays an incorrect location. Documentation date 03.11.2014
This is fixed by going to Settings->Application Manager and performing a forced stop on the TouchWiz Home application.
2. Lockscreen displaying an incorrect location. Documentation date 03.11.2014
First I thought this was related to the first problem. However, this can be fixed by going to Applications->Security and changing the location detection to refresh automatically. It looks like adding a new city in the weather widget updates the location in the lockscreen, but removing it doesn’t force an update to the lockscreen.
More bugs will be documented here as they’re found.
Fun With Optics
I recently had a deployment where we needed to connect Cisco 6500s to Juniper MX960s.
There was a lot of confusion surrounding what fibre and optic modules needed to be used, so I’m documenting the initial state and the successful state here.
Initially, the Junipers had the following model numbers used for the optics:
XFP-10G-LR (identified using a “show chassis hardware”)
The 6500s:
10Gbase-SR
Interestingly, one of the links came up between the devices, while one did not. I tried swapping the cable (Single Mode) for Multimode for the non-working link, and that did not fix the issue. We then swapped the Cisco optic for an LR optic and used Single Mode fibre which did the trick.
Confusingly for someone from a Cisco background like me, the Juniper optic was labelled XFP-10G-L-OC192-SR1. I assumed the SR stood for short reach/range (it does) and tried to use Multimode fibre, as you would with Cisco SR optics. However, it turns out that the Juniper SR optic in this case used Single Mode fibre as its interface.
It is documented in this handy link here, which turned up with some Googling.
The confusion stems due to the reference to Short Reach differing between Continue reading
Quick’n’dirty Nslookup BASH Script
I’m always wondering if the addresses I’m assigning to interfaces aren’t already in DNS. So I came up with a little BASH script that takes a list of IP addresses and performs an nslookup on them to ensure they’re not in use already:
$nslookup < input-filename > output-filename
The addresses in the input file are carriage return delimited.
A better use for this would be to check if DNS entries already have an IP address assigned to them.
The 5 Year Plan
I was recently asked what my 5 year career plan was and whether I wanted to go down the architect route. It threw me a little bit because I’ve never really been a 5 year type person. I have real trouble seeing where I’ll be beyond a year to 18 months.
So, this is my attempt to try and put something together. It doesn’t hurt to have a plan right?
Ideally, you need a short, medium and long term plan. A couple of these could be tech related (e.g: get to CCIE), but the pace technology moves at means the longest term one (if it’s longer than 3 years could well have moved goalposts, or died out). So, without ado, I give you the 3 – 6- 12 – 24 – 36 plan. Or 3,6,1,2,3 plan. This is my way of putting down what I want to have achieved in the next 3-6 months, year, 2 and 3 years.
3-6 months: Get my CCNP Security finished with, and maybe another associate level non-Cisco vendor certification.
1 year: Complete my CCIE written and be on my way to lab revision.
2 years: Completed, or have attempted the CCIE lab once.
Configuring SNMPv3 On NX-OS
We’re currently trying to allow a client to perform an operation using SNMP set commands on a Cisco NX-OS switch (namely a 5548).
It’s possible using SNMPv2c and community strings, but this does not generate a log message, making it completely unaccountable. SNMPv3 seems to have the answer. According to the documentation, it provides:
- Integrity
- Encryption
- Authentication
I’ve tested using a set operation to change a MIB using the following command:
snmpset -v 3 -u test -l authpriv -a MD5 -A Testpass01 -x DES -X Testpass01 hostname system.sysLocation.0 s TESTLOCATION
Which works fine.
However, the problem arises when trying to back off the authentication of the SNMP operation to TACACS/RADIUS. My interpretation of the documentation suggests this is possible. My Cisco SE has not denied it either. However, I reckon some changes need to be made to the authentication server. According to what I’ve read:
You can use the VSA cisco-av-pair on AAA servers to specify user role mapping for the Nexus 5000 Series switch using this format:
shell:roles="roleA roleB ..."
If you do not specify the role option in the cisco-av-pair attribute, the default user role is network-operator.
You can also specify your SNMPv3 authentication and privacy Continue reading
OSPF Summary Routes and BGP
Recently I was in a situation where I needed to advertise some OSPF routes created using the area range command into BGP. When advertising routes into BGP there are a few considerations:
- Does the routing table know the exact route you’re trying to advertise into BGP?
- Is any route filtering being performed? Don’t forget to check at the source of the BGP route and the destination it’s being advertised to!
- Is soft-reconfiguration supported on the software you’re running?
- Will you need to do a “clear ip bgp neighbor”? Seems IOS 12.4 doesn’t require it but 12.2 does. I tested 12.4 on GNS3, and 12.2 on a live 6500.
Using the area range command will automatically generate an OSPF intra-area route to Null 0 IF the router the command is issued on is an ABR. This is visible here:
Switch#sh ip route 10.253.0.0 255.255.240.0
Routing entry for 10.253.0.0/20
Known via "ospf 1", distance 110, metric 0, type intra area
Routing Descriptor Blocks:
* directly connected, via Null0
Route metric is 0, traffic share count is 1
This route will not be created on a non-ABR router, so watch Continue reading
Checksum Verification
Occasionally I have to install software that is no longer available for download via the official channels. This is due to us having pretty strict standards on which IOS versions are stable and suitable for use via a bug scrub process that Cisco are party to.
I could speak to our Cisco SE and ask for the image to be provided, but it’s simpler and quicker to find a similar piece of kit on the network and FTP/SCP the image across.
I did this today, and then realised that I couldn’t rely on CCO to give me the MD5 sum for the image. A quick google tells me that I can perform a checksum on the switch using this command:
verify /md5 <file-location>:<file-name>
Location choices are:
bs: File to be verified
cns: File to be verified
flash: File to be verified
ftp: File to be verified
http: File to be verified
https: File to be verified
null: File to be verified
nvram: File to be verified
rcp: File to be verified
scp: File to be verified
system: File to be verified
tar: File to be verified
tftp: File to be verified
tmpsys: File to be verified
xmodem: File to be Continue reading
ACE Management
Was knocking my head against a brick wall trying to configure an ACE for management for a couple of days. Turns out, it does not permit ICMP to it by default.
This is a good place to start:
So you need to configure a class map classifying ICMP traffic from specific sources as being interesting, a policy map referencing the class map, an action for matching traffic and then apply that using the “service-policy” command to the interface you want to permit traffic to.
Everything is well as long as it’s only management traffic you want to permit to this address.
Notes On AAA
Enabling aaa new model means the switch will try and match all login attempts using a aaa method.
First, define the TACACS or RADIUS server using:
tacacs-server host <IP-address> <optional key value>
There are some other values you can use, but I’ve never had to use these.
Now, give your authentication method a name:
aaa group server tacacs+ <method-name> server <IP-address>
Call the method for authenttication
aaa authentication login default group <method-name> group <fallback method name if configured> local
You should now be good to go!
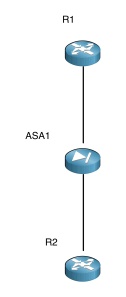
Layer 2 ASA And OSPF
So recently I had to configure an OSPF adjacency between two routers.
I thought simply permitting multicast traffic to the All Routers and All DR/BDR Routers would permit OSPF Hellos across the link and allow OSPF adjacencies to form. In fact what I saw was routers entering the EXSTART state and the neighbourship failing. I checked the manual, for an OSPF adjacency to form, the following conditions need to be satisfied:
- Area IDs need to match
- Neighbours need to be on the same subnet
- MTUs need to match
- Hello/Dead timers need to match
- Authentication (if any is configured)
So, what I saw was the routers entering the EXSTART state and the neighbourship dropping. Bear in mind, at this point, the only thing permitted through the firewall both ways was multicast traffic to 224.0.0.5 (the AllSPF Routers multicast address) using the OSPF protocol (IP protocol 89). So for some reason the DBD exchange was not taking place.
My initial reaction was to check MTU size. I’d seen a similar issue before where an MTU mismatch (jumbo frames on one side, 1500 bytes on the other side) meant while the non-backbone area’s routes made Continue reading
Multiple Probes In Serverfarm Configuration
Serverfarms allow probes to be associated with them when configured.
Any rserver in the serverfarm configuration will inherit probes from the serverfarm config.
Default probe behaviour is to use OR logic. A single probe failure will cause the rserver to be marked as down.
AND logic for probes can be applied using the fail-on-all command. This means all probes must fail for the serverfarm to be marked as down.