Notes on that StJude/MuddyWatters/MedSec thing
I thought I'd write up some notes on the StJude/MedSec/MuddyWaters affair. Some references: [1] [2] [3] [4].The story so far
tl;dr: hackers drop 0day on medical device company hoping to profit by shorting their stock
St Jude Medical (STJ) is one of the largest providers of pacemakers (aka. cardiac devices) in the country, around ~$2.5 billion in revenue, which accounts for about half their business. They provide "smart" pacemakers with an on-board computer that talks via radio-waves to a nearby monitor that records the functioning of the device (and health data). That monitor, "Merlin@Home", then talks back up to St Jude (via phone lines, 3G cell phone, or wifi). Pretty much all pacemakers work that way (my father's does, although his is from a different vendor).MedSec is a bunch of cybersecurity researchers (white-hat hackers) who have been investigating medical devices. In theory, their primary business is to sell their services to medical device companies, to help companies secure their devices. Their CEO is Justine Bone, a long-time white-hat hacker. Despite Muddy Waters garbling the research, there's no reason to doubt that there's quality research underlying all this.
Continue reading
Notes on the Apple/NSO Trident 0days
I thought I'd write up some comments on today's news of the NSO malware using 0days to infect human rights activist phones. For full reference, you want to read the Citizen's Lab report and the Lookout report.Press: it's news to you, it's not news to us
I'm seeing breathless news articles appear. I dread the next time that I talk to my mom that she's going to ask about it (including "were you involved"). I suppose it is new to those outside the cybersec community, but for those of us insiders, it's not particularly newsworthy. It's just more government malware going after activists. It's just one more set of 0days.
I point this out in case press wants to contact for some awesome sounding quote about how exciting/important this is. I'll have the opposite quote.
Don't panic: all patches fix 0days
We should pay attention to context: all patches (for iPhone, Windows, etc.) fix 0days that hackers can use to break into devices. Normally these 0days are discovered by the company itself or by outside researchers intending to fix (and not exploit) the problem. What's different here is that where most 0days are just a theoretical danger, these Continue reading
Another lesson in confirmation bias
The biggest problem with hacker attribution is the confirmation bias problem. Once you develop a theory, your mind shifts to distorting evidence trying to prove the theory. After a while, only your theory seems possible as one that can fit all your carefully selected evidence.You can watch this happen in two recent blogposts [1] [2] by Krypt3ia attributing bitcoin payments to the Shadow Broker hackers as coming from the government (FBI, NSA, TAO). These posts are absolutely wrong. Nonetheless, the press has picked up on the story and run with it [*]. [Note: click on the pictures in this post to blow them up so you can see them better].
The Shadow Brokers published their bitcoin address (19BY2XCgbDe6WtTVbTyzM9eR3LYr6VitWK) asking for donations to release the rest of their tools. They've received 66 transactions so far, totally 1.78 bitcoin, or roughly $1000 at today's exchange rate.
Bitcoin is not anonymous by pseudonymous. Bitcoin is a public ledger with all transaction visible by everyone. Sometimes we can't tie addresses back to people, but sometimes we can. There are a lot of researchers who spent a lot of time on "taint anlysis" trying to Continue reading
A lesson in social engineering: president debates
In theory, we hackers are supposed to be experts in social engineering. In practice, we get suckered into it like everyone else. I point this out because of the upcoming presidential debates between Hillary and Trump (and hopefully Johnson). There is no debate, there is only social engineering.Some think Trump will pull out of the debates, because he's been complaining a lot lately that they are rigged. No. That's just because Trump is a populist demagogue. A politician can only champion the cause of the "people" if there is something "powerful" to fight against. He has to set things up ahead of time (debates, elections, etc.) so that any failure on his part can be attributed to the powerful corrupting the system. His constant whining about the debates doesn't mean he'll pull out any more than whining about the election means he'll pull out of that.
Moreover, he's down in the polls (What polls? What's the question??). He therefore needs the debates to pull himself back up. And it'll likely work -- because social-engineering.
Here's how the social engineering works, and how Trump will win the debates.
The moderators, the ones running the debate, will do their best Continue reading
Bugs don’t come from the Zero-Day Faerie
This WIRED "article" (aka. thinly veiled yellow journalism) demonstrates the essential thing wrong with the 0day debate. Those arguing for NSA disclosure of 0days believe the Zero-Day Faerie brings them, that sometimes when the NSA wakes up in the morning, it finds a new 0day under its pillow.The article starts with the sentences:
WHEN THE NSA discovers a new method of hacking into a piece of software or hardware, it faces a dilemma. Report the security flaw it exploits to the product’s manufacturer so it gets fixed, or keep that vulnerability secret—what’s known in the security industry as a “zero day”—and use it to hack its targets, gathering valuable intelligence.But the NSA doesn't accidentally "discover" 0days -- it hunts for them, for the purpose of hacking. The NSA first decides it needs a Cisco 0day to hack terrorists, then spends hundreds of thousands of dollars either researching or buying the 0day. The WIRED article imagines that at this point, late in the decision cycle, that suddenly this dilemma emerges. It doesn't.
The "dilemma" starts earlier in the decision chain. Is it worth it for the government to spend $100,000 to find and disclose a Cisco 0day? Continue reading
EQGRP tools are post-exploitation
A recent leak exposed hackings tools from the "Equation Group", a group likely related to the NSA TAO (the NSA/DoD hacking group). I thought I'd write up some comments.Despite the existence of 0days, these tools seem to be overwhelmingly post-exploitation. They aren't the sorts of tools you use to break into a network -- but the sorts of tools you use afterwards.
The focus of the tools appear to be about hacking into network equipment, installing implants, achievement permanence, and using the equipment to sniff network traffic.
Different pentesters have different ways of doing things once they've gotten inside a network, and this is reflected in their toolkits. Some focus on Windows and getting domain admin control, and have tools like mimikatz. Other's focus on webapps, and how to install hostile PHP scripts. In this case, these tools reflect a methodology that goes after network equipment.
It's a good strategy. Finding equipment is easy, and undetectable, just do a traceroute. As long as network equipment isn't causing problems, sysadmins ignore it, so your implants are unlikely to be detected. Internal network equipment is rarely patched, so old exploits are still likely to work. Some tools appear to target Continue reading
Hey lawyers, I’m not your client
We can't talk casually with lawyers, at parties or infosec conferences. For one thing, it's an ethical problem for them, as they put a couple minute's thought into a question that can have lifelong consequences for a you. For another thing, it puts them legal jeopardy if you (falsely) think there is an attorney-client relationship. This makes lawyers boring people at parties, because all they can discuss is nonsense like sports scores.
In an attempt to remedy this situation, so I can talk casually about the law, I'm writing the following open-letter:
Dear Lawyers:
Unless there is a written agreement signed by you and me, I'm not your client. I understand that I should not interpret any comment as actual legal advice. I know that we are talking about hypothetical situations, and that I should not try to apply that information to my own situation. I know that we are often making jokes, and taking such things seriously as "legal advice" would be against my interests. I'm the one at fault, deliberately instigating you into discussing hypotheticals and making such jokes, for the lulz.
Sincerely,
Robert Graham
Of course, I don't know if this letter will actually help lawyers chillax Continue reading
National interest is exploitation, not disclosure
Most of us agree that more accountability/transparency is needed in how the government/NSA/FBI exploits 0days. However, the EFF's positions on the topic are often absurd, which prevent our voices from being heard.One of the EFF's long time planks is that the government should be disclosing/fixing 0days rather than exploiting them (through the NSA or FBI). As they phrase it in a recent blog post:
as described by White House Cybersecurity Coordinator, Michael Daniel: “[I]n the majority of cases, responsibly disclosing a newly discovered vulnerability is clearly in the national interest.” Other knowledgeable insiders—from former National Security Council Cybersecurity Directors Ari Schwartz and Rob Knake to President Obama’s hand-picked Review Group on Intelligence and Communications Technologies—have also endorsed clear, public rules favoring disclosure.The EFF isn't even paying attention to what the government said. The majority of vulnerabilities are useless to the NSA/FBI. Even powerful bugs like Heartbleed or Shellshock are useless, because they can't easily be weaponized. They can't easily be put into a point-and-shoot tool and given to cyberwarriors.
Thus, it's a tautology saying "majority of cases vulns should be disclosed". It has no bearing on the minority of bugs the NSA is interested in -- Continue reading
I gamergate Meredith Mciver
One of the basic skills of hackers is "doxxing". It's actually not a skill. All you need to do is a quick search of public records databases through sites like Spokeo, Intelius, and Ancestry.com and you can quickly dox anybody.During the Republican convention, Trump's wife plagiarized Obama's wife in a speech. A person in the Trump organization named "Meredith Mciver" took the blame for it. Trump haters immediately leapt to the conclusion that this person was fake, pointing out her Twitter and Facebook accounts were created after the controversy started.
So I'm going to go all gamergate on her and see what I can find.
According to New York public records, somebody named "Meredith Mciver" has been working for a company called the "The Trump Organization" as "Staff Writer" for many years. Her parents are Phyllis and James Mciver. Her older sister is Karen Mciver. She has an apartment at 588 W End Avenue in Manhattan (though I won't tell you which apartment -- find out for yourself). Through Ancestry.com, you can track down more information, such as her yearbook photo from 1962.
Now, all these public records could be fake, of course, but that would require Continue reading
NYTimes vs. DNCleaks
People keep citing this New York Times article by David Sanger that attributes the DNCleaks to Russia. As I've written before, this is propaganda, not journalism. It's against basic journalistic ethics to quote anonymous "federal officials" in a story like this. The Society of Professional Journalists repudiates this [1] [2]. The NYTime's own ombudsman has itself criticized David Sanger for this practice, and written guidelines to specifically ban it.Quoting anonymous federal officials is great, when they disagree with government, when revealing government malfeasance, when it's something that people will get fired over.
But the opposite is happening here. It's either Obama himself or some faction within the administration that wants us to believe Russia is involved. They want us to believe the propaganda, then hide behind anonymity so we can't question them. This evades obvious questions, like whether all their information comes from the same public sources that already point to Russia, or whether they have their own information from the CIA or NSA that points to Russia.
Everyone knows the Washington press works this way, and that David Sanger in particular is a journalistic whore. The NetFlix series House of Cards portrays this accurately in its Continue reading
My Raspeberry Pi cluster
So I accidentally ordered too many Raspberry Pi's. Therefore, I built a small cluster out of them. I thought I'd write up a parts list for others wanting to build a cluster.To start with is some pics of the cluster What you see is a stack of 7 RPis. At the bottom of the stack is a USB multiport charger and also an Ethernet hub. You see USB cables coming out of the charger to power the RPis, and out the other side you see Ethernet cables connecting the RPis to a network. I've including the mouse and keyboard in the picture to give you a sense of perspective.
Here is the same stack turn around, seeing it from the other side. Out the bottom left you see three external cables, one Ethernet to my main network and power cables for the USB charger and Ethernet hub. You can see that the USB hub is nicely tied down to the frame, but that the Ethernet hub is just sort jammed in there somehow.
The concept is to get things as cheap as possible, on per unit basis. Otherwise, one might as well just buy more expensive computers. My parts Continue reading
Use the freakin’ debugger
This post is by a guy who does "not use a debugger". That's stupid. Using a friendly source-level debugger (Visual Studio, XCode, Eclipse) to step line-by-line through working code is what separates the 10x programmers from the wannabes. Yes, it's a bit of a learning hurdle, and creating "project" files for small projects is a bit of a burden, but do it. It'll vastly improve your coding skill.That post quotes people like Rob Pike saying that stepping line-by-line is a crutch, that instead you should be able to reason about code. And that's true, if you understand what you are doing completely.
But in the real world, you never do. Programmers are constantly forced to stretch and use unfamiliar languages. Worse yet, they are forced to use unfamiliar libraries. Documentation sucks, there's no possible way to understand APIs than to step through code -- either watching the returned values, or compiling their source and stepping into it.
As an experienced programmer, it's true I often don't step through every line. The lines I understand completely, the ones I can fully reason about, I don't bother. But the programmer spends only a small percentage of their time on things Continue reading
Reverse Turing testing tech support
So I have to get a new Windows license for a new PC. Should I get Windows 10 Home or Windows 10 Professional? What's the difference?So I google the question, which gives me this website:
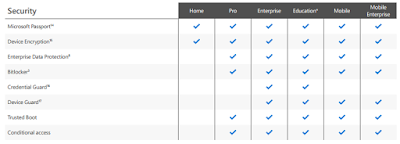
Ooh, a button that says "Download Table". That's exactly what I want -- a technical list without all the fluff. I scroll down to the parts that concern me, like encryption.
Wait, what? What's the difference between "Device Encryption" and "BitLocker"? I though BitLocker was Device Encryption?? Well, the purchase screen for Windows 10 has this friendly little pop out offering to help. Of course, as a techy, I know that such things are worse than useless, but I haven't tried one in a while, so I thought if I'd see if anything changed.
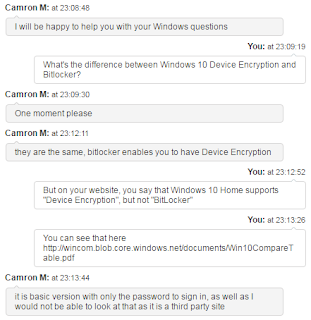
So up pops a chat window and we start chatting:
So at first he says they are the same. When I press him on the difference, he then admits they are different. He can't read the document I'm reading, because it's on a non-Microsoft "third party" site. While it's true it's on "windows.net", that's still a Microsoft site, but apparently he's not allowed to access it. Continue reading
Tesla review: What you need to know about charging
Before you buy an electric car, you need to understand charging. It’s a huge deal. You think it works almost like filling the gas tank. It doesn’t. Before going on long trips, you first need to do math and a bit of planning.The Math
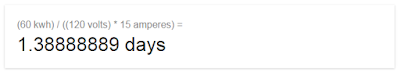
Like BMW model numbers indicate engine size, Tesla model numbers indicate the size of the battery, so my "Tesla S P90D" has a 90kwh (killowatt-hour) battery, with a 286mile range. Their lowest end model is the “Tesla S 60”, which has a 60kwh hour battery, or a 208mile advertised range.In the United States, a typical plug is a 120volt circuit with a maximum of 15amps. Doing the math, this is how long it’ll take for me to recharge the battery:
That’s right, 1.4 days (or 2.1 days for a 90kwh car). This is the absolute worse case scenario, mind you, but it demonstrates that you have to pay attention to charging. You can't simply drive up to a station, fill up the tank in a couple minutes, and drive away.
Let’s say you live in Austin, Texas, and you have a meeting in Dallas. You think that you can drive up to Continue reading
Ethereum/TheDAO hack simplified
The news in the Bitcoin world is the Ethereum/DAO hack. I thought I'd write up a simplified explanation.What is Bitcoin?
I'm sure you know, or have an idea what Bitcoin is, but I'll explain it again in terms that are important here.
Bitcoin is just a public ledger (the "blockchain"), of all transaction there ever was. This ledger is huge (80-gigabytes) and growing, but Moore's Law says computers grow even faster, so that shouldn't be a problem.
Each entry in the ledger says to move the coins received in these previous entries, and give them to this recipient. In other words:
move these coins I received there, to this guy here
In the future when that guy spends the coin in a new transaction, he'll refer back to this transaction here. That's why it's called a "chain" -- every transaction refers to a previous one, back to the original creation of the coins.
Actually, these transactions aren't fixed as simply moving money around. Instead, a script is used, written in a bitcoin-specific programming language that can do things like add, multiply, and compare numbers. However, it's not a full programming language. It can't call functions or execute loops. It's Continue reading
Scanning for ClamAV 0day
Last week an 0day was released for ClamAV. Well, not really an 0day so much as somebody noticed idiotic features in ClamAV. So I scanned the Internet for the problem.The feature is that the daemon listens for commands that tell it to do things like scan files. Normally, it listens only locally for such commands, but can be reconfigured to listen remotely on TCP port 3310. Some packages that include ClamAV sometimes default to this.
It's a simple protocol that consists of sending a command in clear text, like "PING", "VERSION", "SHUTDOWN", or "SCAN
So I ran masscan with the following command:
masscan 0.0.0.0/0 -p3310 --banners --hello-string[3310] VkVSU0lPTg==Normally when you scan and address range (/0) and port (3310), you'd just see which ports are open/closed. That's not useful in this case, because it finds 2.7 million machines. Instead, you want to establish a full TCP connection. That's what the --banners option does, giving us only 38 thousand machines that successfully establish a connection. The remaining machines are large ranges on the Internet where firewalls are configured to respond with SYN-ACK, with the express purpose of frustrating port scanners.
But of those 38k machines, most are actually Continue reading
No, Musky, Feudalism is best for Mars
Recently, the press fawned all over Elon Musk's comments at a conference. Among them was Musk's claim that "direct democracy" would be the best system, where citizen's vote directly for laws, rather than voting for (corrupt) representatives/congressmen. This is nonsense. The best political system would be feudalism.There is no such thing as "direct democracy". Our representatives in congress are only the first layer on top of a bureaucracy. Most rules that restrict us are not "laws" voted by congress but "regulations" decided by some bureaucrat.
Consider the BP Gulf Oil spill, as an example. It happened because oil companies got cozy with their regulators, the minerals Management Service (MMS), part of the Department of the Interior. The bureaucrats had a dual mandate: to protect the environment, and to promote economic activity. Oil companies lobbied them to risk the environment in favor of profits.
Consider Obamcare's controversial mandate that health insurers must pay for abortions. This was not part of the law pass by congress, but a decision by the bureaucrats in charge of all the little details in carrying out the law.
Consider the Federal Communication Commission (FCC) regulation of the Internet. It bases its Continue reading
Instrumenting masscan for AFL fuzzing
This blog post is about work in progress. You probably don't want to read it.So I saw this tweet today:
Fuzzing masscan by @ErrataRob with AFL by @lcamtuf.— Dr David D. Davidson (@dailydavedavids) June 5, 2016
Forgot to remove the crash-handler so crashes logged as hangs. pic.twitter.com/Yh5ElNyvOm
As it turns it, he's just fuzzing input files. This is good, he's apparently already found some bugs, but it's not a huge threat.
Instead, what really needs to be fuzzed is network input. This is chronic problem with AFL, which is designed for inserting files, not network traffic, into programs.
But making this work is actually pretty trivial. I just need to make a tiny change to masscan so that instead of opening a libpcap adapter, it instead opens a libpcap formatted file.
This change was trivial, successfully running it is tough. You have to configure the command-line so all IP addresses match up with the libpcap file content, which is a pain. I created a sample lipcap file and checked it into the project, along with a help document explaining it. Just git clone the project, run make, then run this command line to see it Continue reading
My fellow Republicans: don’t support Trump
Scott Adams, the creator of the Dilbert comic strip, has a post claiming a Trump presidency wouldn't be as bad as people fear. It's a good post. But it's wrong.Trump is certainly not as bad as his haters claim. Trump not only disables the critical-thinking ability of his supporters, but also of his enemies. In most conversations, I end up defending Trump -- not because I support him as a candidate, but because I support critical-thinking. He's only racist sometimes, most of the time I love his political incorrectness.
But with all that said, he would indeed be a horrible president. As a long-term Republican, I'd prefer a Hillary Clinton presidency, and I hate Hillary to the depths of my soul. She's corrupt, and worst of all, she's a leftist.
But there's a thing worse than being a leftist (or right-winger) and that's being a "populist demagogue". Populist demagogues tell you that all your problems are caused by them (you know, those people), and present unrealistic solutions to problems. They appeal to base emotion and ignorance.
When nations fail because of politics, it's almost always due to populist demagogues. Virtually all dictators are a "man of the people", protecting Continue reading
Drumpf: this is not how German works
In our willingness to believe any evil of Trump, some have claimed his original name was "Drumpf". This isn't true, this isn't how the German language works. Trump has the power to short-circuit critical thinking in both his supporters and his enemies. The "Drumpf" meme is just one example.There was no official pronunciation or spelling of German words/names until after Trump's grandfather was born. As this The Guardian article describes, in the city ("Kallstadt") where Trump's grandfather was born, you'll see many different spellings of the family name in the church's records. like "Drumb, Tromb, Tromp, Trum, Trumpff, Dromb" and Trump. A person might spell their name different ways on different documents, and the names of children might be spelled different than their parent's. It makes German genealogy tough sometimes.
During that time, different areas of German had different dialects that were as far apart as Dutch and German are today. Indeed, these dialects persist. Germans who grow up outside of cities often learn their own local dialect and standard German as two different languages. Everyone understands standard German, but many villagers cannot speak it. They often live their entire lives within a hundred kilometers of where they grew Continue reading