Author Archives: Giri Radhakrishnan
Author Archives: Giri Radhakrishnan
Last quarter we announced Calico Cloud’s ‘Cluster Security Score’ feature as part of cluster security posture management. Today, we are excited to announce product and user experience improvements and better user experience for the Calico platform. This blog covers all major updates including VXLAN-based cluster mesh networking, advanced observability and troubleshooting features, improved support for Windows-based containers, third-party integration using webhooks, and enhanced egress gateway high-availability.
By leveraging these new features, organizations can streamline their Kubernetes cluster management, enhance network visibility, and ensure reliable connectivity and security for their applications across clusters.
Kubernetes does not natively support inter-cluster pod to pod communication. While routable IPs is a way to solve this, it requires changes to the underlying network which is both challenging and time consuming. Calico’s new capability solves this by implementing VXLAN support. You no longer need to make any changes to the network to enable pod to pod connectivity across multiple clusters. This allows you to easily deploy applications and services across multiple clusters, and manage them as a single entity.
Calico’s cluster mesh is fully integrated with its policy and security features, so that policies and security controls can be applied Continue reading
This release, we’re really excited about major improvements to Calico’s workload-centric WAF. We’ve made it much easier for users to configure and deploy the WAF in just a few clicks and we’ve also made it much easier to review and manage WAF alerts through our new Security Events feature.
Application security teams have deployed perimeter-based WAFs for decades to protect against common web attacks, with a focus on browser-based and client-side attacks. But with the rise of microservice architecture, there’s now a significant amount of HTTP traffic related to internal APIs. Moreover, with the growing use of open source and third-party software, all deployed within your Kubernetes cluster, you can no longer trust that the software running in your cluster is safe or secure. With this growing attack surface within your cloud environment, it’s critical to employ a workload-based WAF.
We know that security teams are struggling to keep up with the rapid pace of software development in their organizations, so we wanted to simplify the way that security teams secure application traffic. Further, we wanted to ensure that security teams can secure all workloads, not just their Continue reading
DDoS or Distributed Denial of Service attacks have been around for a while and are notorious and painful to deal with (as with any other attack). As the name suggests, a DDoS attack causes an application or service to become unavailable to users due to resources exceeding it’s capacity and causing the app to either crash or become unresponsive. DDoS is a form of DoS where the attack comes from multiple sources (bots), usually spread across geographical locations. Imagine getting thousands of spam calls on your phone within a very short time and there is one legitimate call that is trying to contact you. How will you make sure you attend the legitimate call?
In a Kubernetes environment, DDoS can hit the application from external sources when a service is exposed to the Internet. For attackers who gain a foothold of the environment within the Kubernetes cluster and are looking to infect multiple workloads with malware to further amplify a DoS attack, you need a strong zero-trust workload access control policies in place to restrict lateral movement.
Before we look at the technical aspects of a DDoS attack Continue reading
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:
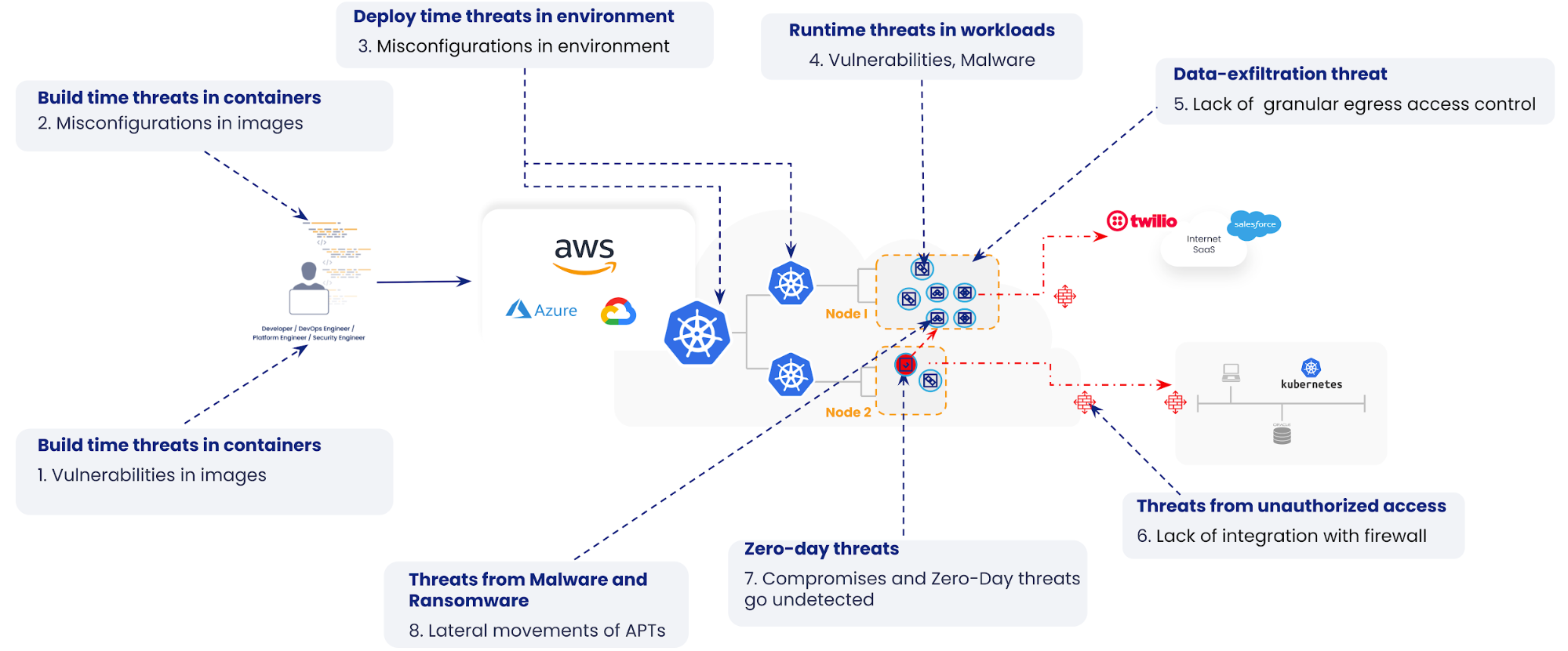
In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading
Containerized applications are complex, which is why an effective container security strategy is difficult to design and execute. As digitalization continues to push applications and services to the cloud, bad actors’ attack techniques have also become more sophisticated, which further challenges container security solutions available on the market.
Despite the discussion around agent vs agentless in the cloud security landscape and which type of solution is better, the most valuable solution is one that provides a wide breadth of coverage. Calico is unique as it is already installed as part of the underlying platform and provides the dataplane for a Kubernetes cluster. When Calico Cloud or Calico Enterprise is deployed, security and observability capabilities can be enabled on top of these core components. We provide a simple plug-and-play active security solution that focuses on securing workloads and the Kubernetes platform with the least amount of complexity and configuration.
Cloud-native applications are susceptible to many attack vectors. We have broken them down to eight, as seen in the following illustration:

In previous blogs, we have explained how the use of vulnerability management, zero-trust workload security, and microsegmentation can help reduce the Continue reading
We are excited to announce the early preview of Calico Enterprise 3.16. This latest release extends the active security platform’s support for egress access controls, improves the usability of network-based threat defense features, and scales visualization of Kubernetes workloads to 100s of namespaces. Let’s go through some of the highlights of this release.
Egress gateways allow you to identify the source of traffic at the namespace or pod level when it leaves a Kubernetes cluster to communicate to external resources. This makes it highly beneficial for security teams to apply access controls to specific traffic instead of opening up a larger set of IP addresses. Calico Enterprise 3.16 has added egress gateway support for Microsoft Azure and AKS in addition to our support for AWS and EKS. Check out our documentation, Configure egress gateways, Azure, to learn more.
Calico Enterprise now includes operator-managed deployments of egress gateways. This reduces operational overhead and eliminates additional steps required during software upgrades. With the Tigera Operator, egress gateways will always be automatically upgraded.
Calico Enterprise’s unique workload-centric web application Continue reading
This is part 2 of the blog series on the MITRE ATT&CK framework for container security, where I explain and discuss the MITRE ATT&CK framework. For those who are not familiar with what the MITRE framework is, I encourage you to read part 1.
In my previous blog post, I explained the first four stages of the MITRE ATT&CK framework and the tactics used by adversaries to gain a foothold in the network or the environment within a containerized application. What happens next?
Imagine a military battalion trying to invade its enemy’s territory. What would a soldier do once they’ve infiltrated the opposition? They would take cover and wait for the right opportunity to attack. Similarly, in cyber crime, an attacker will take time to make sure they evade any type of defense that has been put in place. This is the fifth stage in the MITRE ATT&CK framework. In this article, I will explore this fifth stage, along with stages six through nine, and look at how Calico can help mitigate the attack techniques used in these stages.
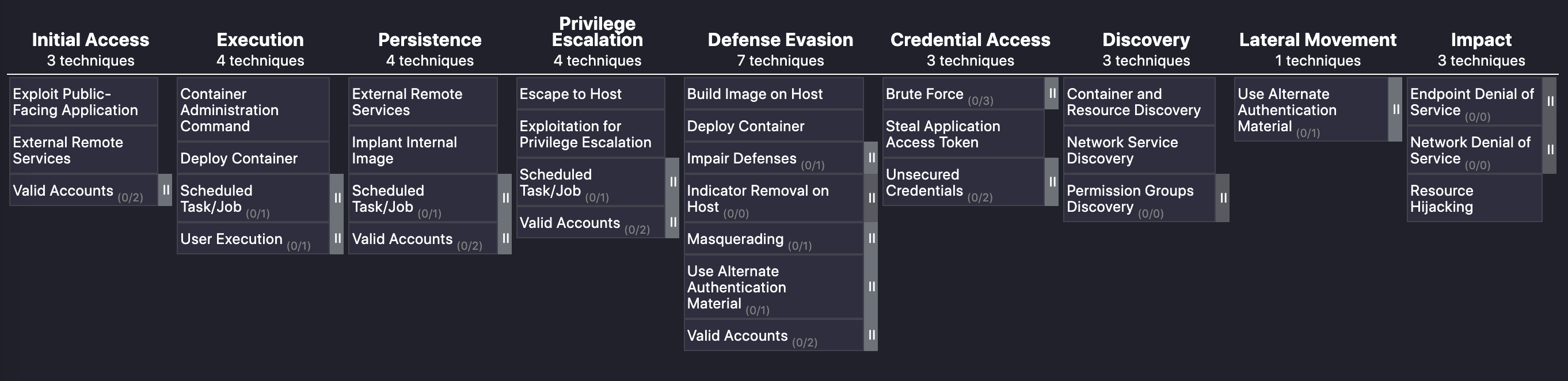
Many security solutions offer Continue reading
As innovations in the world of application development and data computation grow every year, the “attack surface” of these technologies grows as well. The attack surface has to be understood from two sides—from the attacker’s side and from the organization being attacked. For the attacker, they benefit from the entry point into a system, either through the ever-growing perimeter of public-facing applications or the people managing these applications, because the probability of finding a weakness to enter from these entry points is higher. For the organization, managing the attack surface requires investing in more security tools and personnel. This can cascade into bigger security issues, which is why addressing the attack surface is essential.
The MITRE adversarial tactics, techniques, and common knowledge (ATT&CK) framework can help us understand how this large attack surface can be exploited by an adversary and how they strategize an attack. In this two-part blog, I will cover the new ATT&CK matrix for containers and how Calico provides mitigation solutions for each tactic in the matrix. In this blog, we will explore the first four tactics, which mostly deal with reconnaissance. In the second part, we will discuss the techniques and mitigation strategies once an attacker Continue reading
A couple of days ago, I was checking my Twitter feed and saw a tweet from someone saying how frustrated he was that DockerHub (a renowned container registry) was down. Someone else replied to the tweet, recommending the tweet’s author to check out Google’s repository, where they have DockerHub mirrors in Google Cloud.
My first reaction was “Nice! How clever of this person (or Google) to have thought of this idea.” My next thought was, wait. This could lead to potential security risks for some developers who are not familiar with how these registries are updated and what images go into these mirrored sites. Imagine when application developers are busy scrambling to check-in their latest update to the CI/CD pipeline of the software they are building, and in that time crunch, their go-to container registry is down. Do developers really have the time to check if there are vulnerable images in every registry they use? Will there be an easy, streamlined way to automatically scan the images no matter which registry developers use to pull their images? The short answer is yes, and we will look into that in this blog.
In my previous blog, I introduced the brief history of zero trust, the core pillars of a zero-trust model, and how to build a zero-trust model for cloud-native workloads. In this blog, you will learn how Calico can help mitigate vulnerabilities such as the recent zero-day Log4j vulnerability with its zero-trust workload security approach.
The starting point for building a zero-trust model is understanding your attack and protect surface. The outcome of designing your security plan should be eliminating the attack surface completely.
Enterprises are realizing that the best approach to mitigating breaches and protecting their sensitive assets from both internal and external threats is by applying the three principles of zero trust to their security plan. These three principles are:
While stakeholders are busy creating design architectures, collecting asset information, and considering tools required to achieve their zero trust goals, there are also new challenges that some decision-makers should consider. As microservices are becoming the de facto standard for application developers, it has introduced new technologies and methodologies Continue reading
There has been a huge uptick in microservices adoption in the data analytics domain, primarily aided by machine learning (ML) and artificial intelligence (AI) projects. Some of the reasons why containers are popular among ML developers is the ease of portability, scalability, and quick access to data using services—specifically network services. The rise of cloud-native applications, especially for big data in the analytics sector, makes these applications a prime target for cyber crime.
Preventing threat actors from breaching the network and accessing critical data or applications is a daunting task for one team or individual to take on alone. DevOps and security engineers, SREs, and platform architects all need to work together to facilitate the process. These teams are usually presented with two challenges:
This article talks about what organizations need to know about zero trust for cloud-native workloads, and how zero trust Continue reading