Author Archives: chris marget
Author Archives: chris marget
 |
| Yeah, it looks just like this. |
crypto key generate rsa label mykey modulus 2048
crypto ca trustpoint throwaway
keypair mykey
enrollment self
crypto ca enroll throwaway noconfirm
no terminal pager
crypto ca export throwaway pkcs12 <passphrase>
-----BEGIN PKCS12-----
MIIJZwIBAzCCCSEGCSqGSIb3DQEHAaCCCRIEggkOMIIJCjCCCQYGCSqGSIb3DQEH
BqCCCPcwggjzAgEAMIII7AYJKoZIhvcNAQcBMBsGCiqGSIb3DQEMAQMwDQQI4KTD
...etc...
ru1WrVnO7wFa+83BK8D+aQ7UedzQuU6NOiDrjPR0w8uWSLwKmmSVgnZN4BEwPTAh
MAkGBSsOAwIaBQAEFGA2bfp4y+a/R29RZ9TA8sCUSZ+jBBRvppgVbM8rBbW62096
L/HnJErexgICBAA=
-----END PKCS12-----
no crypto ca trustpoint throwaway noconfirm
mkdir usbflash:/MY_ROOT_CA
crypto key generate rsa label MY_ROOT_CA modulus 2048 exportable storage nvram:
 |
| Bogus dMAC on most of these frames |
lab-catalyst#show spanning-tree mst configuration
Name [lab]
Revision 3 Instances configured 4
Instance Vlans mapped
-------- ---------------------------------------------------------------------
0 4-9,40-99,101-199,201-299,301-4094
1 1,10-19,100
2 2,20-29,200
3 3,30-39,300
-------------------------------------------------------------------------------
lab-catalyst#show spanning-tree mst configuration digest
Name [lab]
Revision 3 Instances configured 4
Digest 0x37D94E0098E3418C046F217A71077FB1
Pre-std Digest 0xFC2190275BBB19CD9A6F1BB116DB10E7
lab-catalyst#
lab-procurve# show spanning-tree mst-config
MST Configuration Identifier Information
MST Configuration Name : different
MST Configuration Revision : 4
MST Configuration Digest : 0x37D94E0098E3418C046F217A71077FB1
IST Mapped VLANs : 4-9,40-99,101-199,201-299,301-4094
Instance ID Mapped VLANs
----------- ---------------------------------------------------------
1 1,10-19,100
2 2,20-29,200
3 3,30-39,300
lab-procurve#
 |
| Don't do it! |
! IP SLA monitor on R1
ip sla 1
icmp-echo 192.168.1.2 source-interface FastEthernet0/1
ip Continue reading |
| MXC connector. Image from Corning-Intel Whitepaper. |
 |
| Greg's shot of CLR4 transceivers with MXC connectors. |
/etc/libvirt/hooks/lxc MyAwesomeContainer prepare begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer start begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer started begin -
/etc/libvirt/hooks/lxc MyAwesomeContainer stopped end -
/etc/libvirt/hooks/lxc MyAwesomeContainer release end -
 |
| CC BY-NC-ND 2.0 licensed photo by smif Needs deduplication |
| New C881 on top, old CISCO881 (not wireless - don't believe the stickers) on bottom. |
| New C881 on top |
| Twin screw holes on the new C881... |
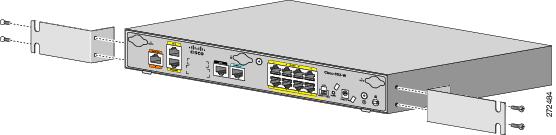 |
| ...make the ACS-890-RM-19= work on the C881. |
# run adb as root:
adb root
# connect to the phone over WiFi (the phone's owner had
# already enabled this feature with 'adb tcpip' via USB):
adb connect <phone's wifi ip address>
# check that we get a root shell on the phone:
adb shell 'id'
adb shell '/data/data/lv.n3o.shark/files/tcpdump -c 2'
tcpdump: verbose output suppressed, use -v or -vv for Continue reading sed -i 's/localhost.localdomain/postfix-relay.marget.com/' /etc/sysconfig/network yum install -y nfs-utils wget tcpdump unzip autofs
service rpcbind start
service autofs restart
ln -s /net/my_nfs_server/path/to/CentOS/ /CentOS
cp /etc/yum.repos.d/CentOS-Media.repo Continue reading |
| Beware the honeypot army! |
This film could have ended much differentlyif Jerry were running Cumulus Linux |
ROUTER#sh ip bg vpnv4 vr Continue reading
 |
| SDN Joke from Brent Salisbury's awesome ONUG presentation. I don't know these cats nor the owner of the photo. |