Author Archives: ddib
Author Archives: ddib
A long long time ago, BGP implementations would use a Maximum Segment Size (MSS) of 536 bytes for BGP peerings. Why 536? Because in RFC 791, the original IP RFC, the maximum length of a datagram is defined as follows:
Total Length: 16 bits
Total Length is the length of the datagram, measured in octets,
including internet header and data. This field allows the length of
a datagram to be up to 65,535 octets. Such long datagrams are
impractical for most hosts and networks. All hosts must be prepared
to accept datagrams of up to 576 octets (whether they arrive whole
or in fragments). It is recommended that hosts only send datagrams
larger than 576 octets if they have assurance that the destination
is prepared to accept the larger datagrams.
The number 576 is selected to allow a reasonable sized data block to
be transmitted in addition to the required header information. For
example, this size allows a data block of 512 octets plus 64 header
octets to fit in a datagram. The maximal internet header is 60
octets, and a typical internet header is 20 octets, allowing a
margin for headers of higher level protocols.
The idea was to Continue reading
Link state protocols like OSPF and IS-IS use the Shortest Path First (SPF) algorithm developed by Edsger Dijkstra. Edsger was a Dutch computer scientist, programmer, software engineer, mathematician, and science essayist. He wanted to solve the problem of finding the shortest distance between two cities such as Rotterdam and Groningen. The solution came to him when sitting in a café and the rest is history. SPF is used in many applications, such as GPS, but also in routing protocols, which I’ll cover today.
To explain SPF, I’ll be working with the following topology:
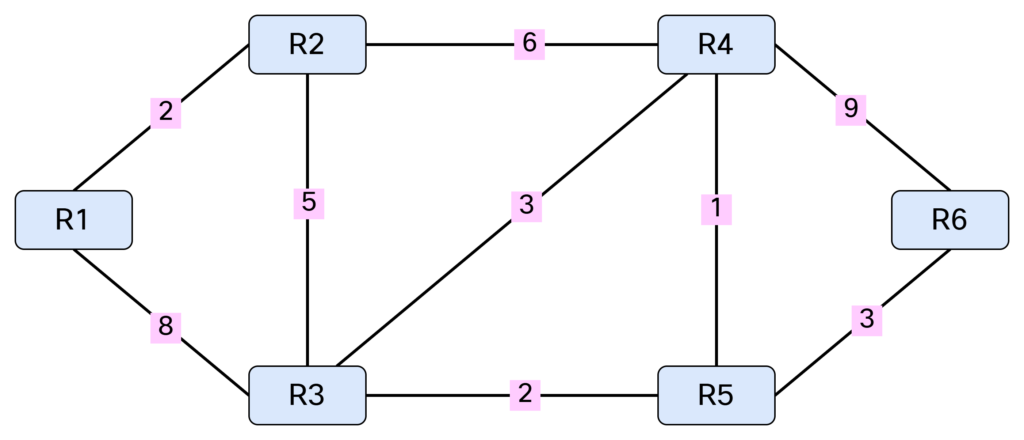
Note that SPF only works with a weighted graph where we have positive weights. I’m using symmetrical costs, although you could have different costs in each direction. Before running SPF, we need to build our Link State Database (LSDB) and I’ll be using IS-IS in my lab for this purpose. Based on the topology above, we can build a table showing the cost between the nodes:
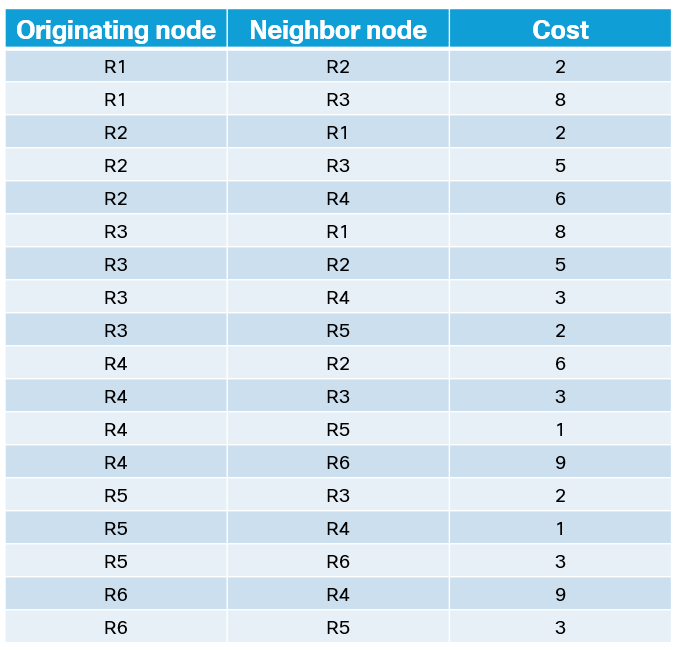
This triplet of information consists of originating node, neighbor node, and cost. It can also be represented as [R1, R2, 2], [R1, R3, 8], [R2, R1, 2], [R2, R3, 5], [R2, R4, 6], [R3, R1, 8], [R3, R2, 5], [R3, R4, Continue reading
In many ways, IS-IS is a simpler, and perhaps more elegant, routing protocol than OSPF. However, it often gets misunderstood. Perhaps due to its roots in OSI or perhaps because it’s not as widely deployed as OSPF. Some of the confusion come from how it behaves on multi-access networks. What is a Designated Intermediate System (DIS)? Why do we need a pseudonode? How do we flood Link State PDUs (LSPs)? In this post, I’ll cover all of that and more. This is going to be a deep dive so save this blog for when you have some time to focus.
IS-IS is a link state protocol, which means that we need to build a link state database that describes how all the intermediate systems (routers) are interconnected, and what prefixes they are associated with. Simply put, we need to build a graph. Let’s do a quick recap of graph theory.
A graph consists of vertices (nodes) and edges (links). When referring to a single node, it’s called a vertex. This is shown below:
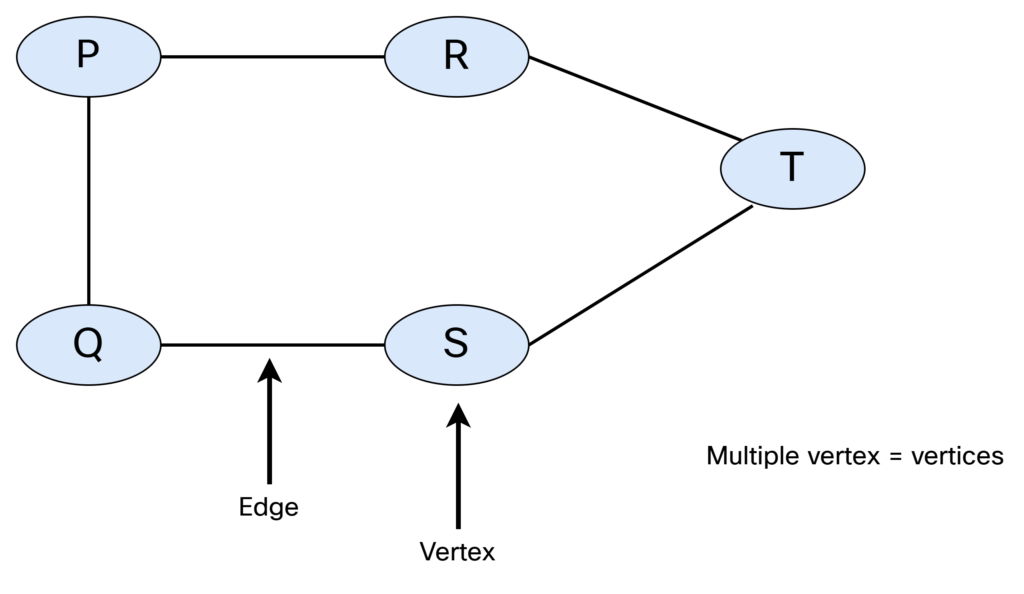
There are different types of graphs. They can be undirected and unweighted:
With this type of graph, there is no weight assigned and there is no way Continue reading
In this post we’ll add a Network Authentication Device (NAD) to ISE to perform TACACS+ authentication and authorization. We’ll also do a deep dive on AAA commands on the NAD. First let’s start with the overall goal of the lab and an overview of how TACACS+ works.
The goal of the lab is to have two users, Bob and Alice, where Bob works in the NOC and Alice is a network admin. Based on the AD group they belong to, they should get different permissions when administrating devices. Alice will be able to use all commands, while Bob will only be able to use basic commands. This is shown below:
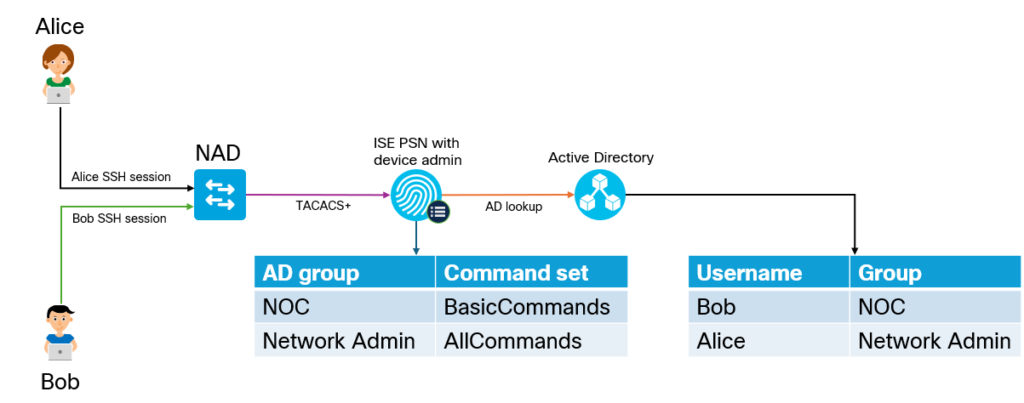
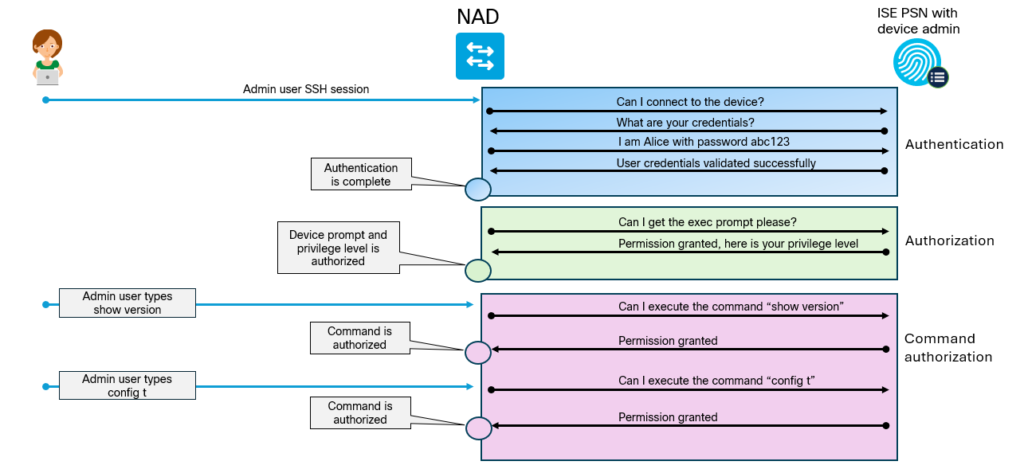
Why would we use TACACS+ over RADIUS? The main reason is that it gives us per command authorization and accounting. The overall flow of TACACS+ is shown below:
To get things started, we must first enable TACACS+ on the PSN. Go to Administration -> Deployment located under System:
Click the > symbol next to Deployment and select your PSN that you want to enable TACACS+ on:
Scroll down to the Policy Service part. Notice that Device Admin is currently not enabled:
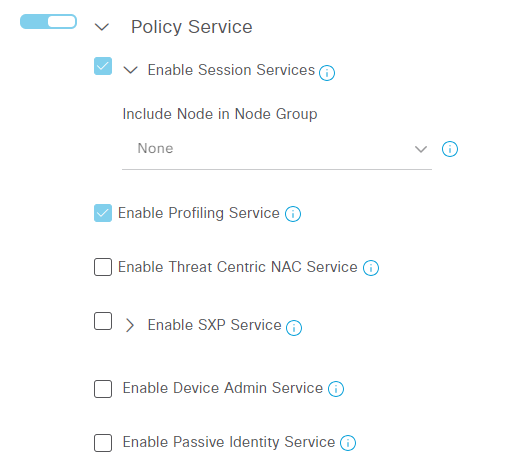
Select Enable Device Admin Service. You Continue reading
The ISE evaluation license gives you 90 days of full access and after that you won’t be able to make any changes. Currently, my server has 28 days remaining:
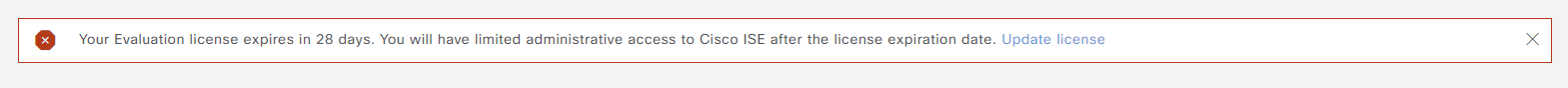
As I intend to keep labbing, I’m going to perform a backup and restore where I’ll restore the configuration on another VM that I’ll be installing. Note that this can be automated, but in this post we’re going to focus on the process of doing it manually to understand what steps are involved.
The steps that will be performed are:
The configuration backup will give us everything we need to restore all the system settings and policies. The operational backup gives us data such as logs. While the configuration backup includes the trusted- and system certificates, it’s good to also export them separately in case you need to perform a restore using another method.
The first thing I’m going to do is to install SFTP on my Windows server using Continue reading
This is a quick post to describe the default behavior of the admin user GUI access in ISE, which gets locked after 45 days, if you haven’t changed the password. You’ll get something like this in the GUI:

While GUI access is prevented, you can still login via SSH and that’s how you’re going to recover the account. SSH to ISE using the admin account. Then issue the following command:
ise01/admin#application reset-passwd ise admin Enter new password: Confirm new password: Password reset successfully.
If you want to change the password policy, go to Administration -> Admin Access under System and click Password Policy:

Notice the checkbox that says that the account expires after 45 days:

Uncheck this box if you don’t want to have the account expire:

Don’t forget to click Save. That’s it! That’s how you recover the account and prevent it from happening again. Note that this is for a private lab. You should adhere to any policies you have on password rotation in your organization.
In this post we’ll domain join a Windows 10 VM to test the GPOs that were created in a previous post. First, let’s verify that the computer is not joined to a domain:
There is currently no user certificate:
There is also no computer certificate:
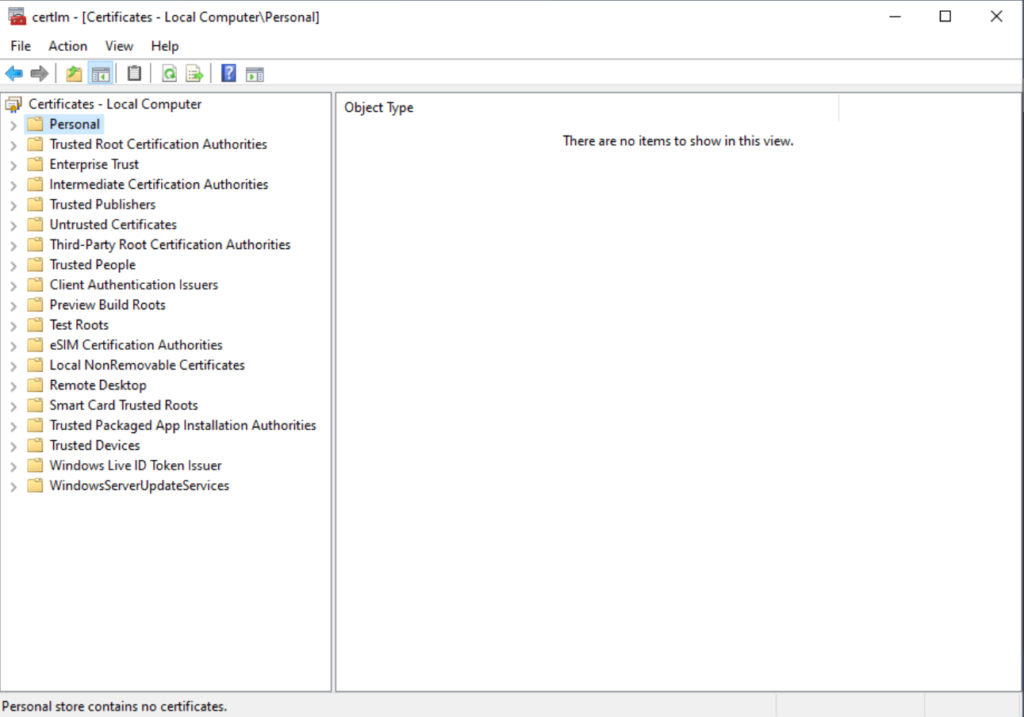
To domain join the computer, we’ll go to Control Panel -> System and Security -> System and the click Advanced system settings:
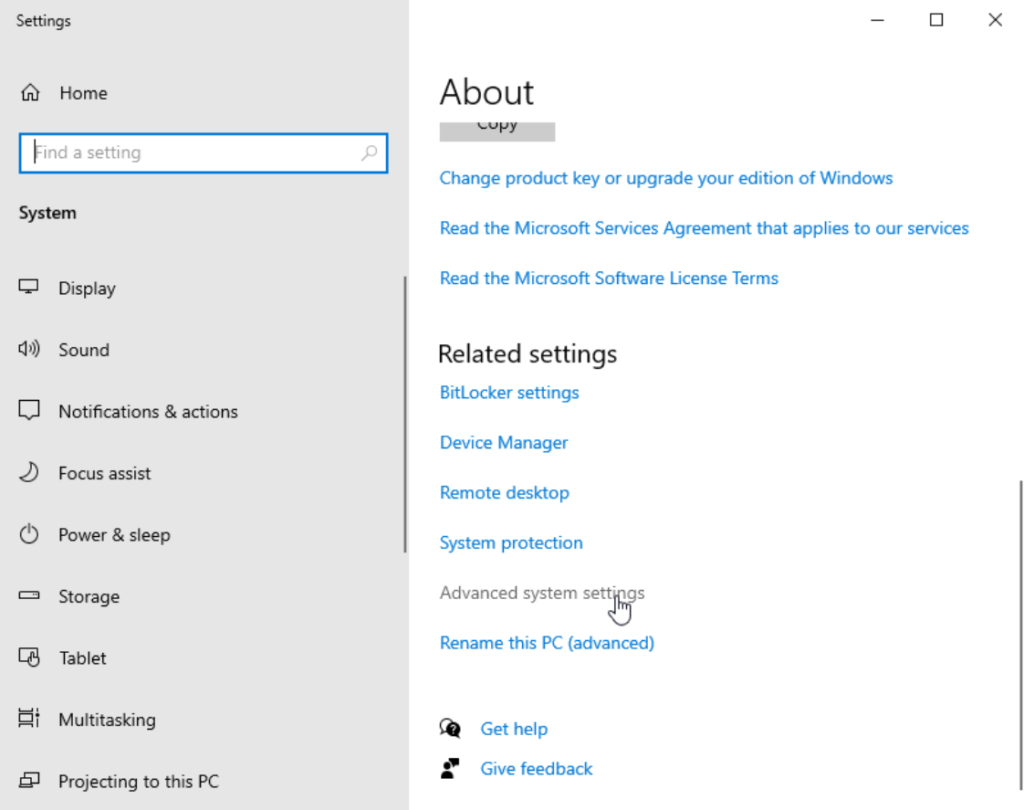
Go to Computer Name and click Change…:
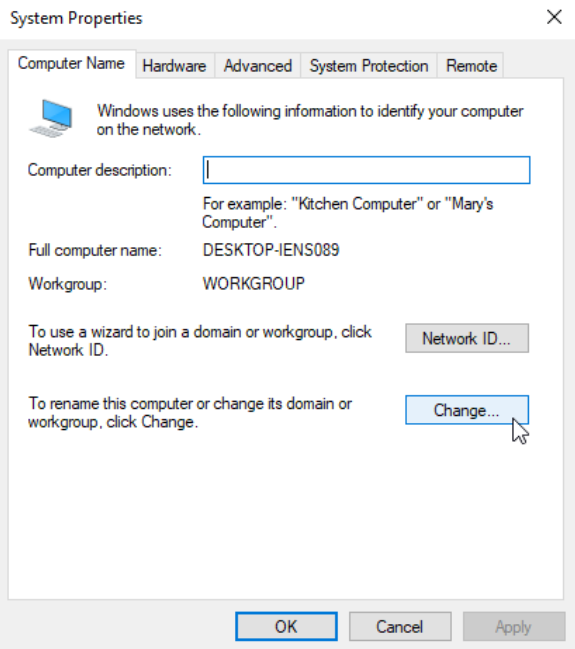
Select Member of Domain and enter the domain name (iselab.local in my lab):
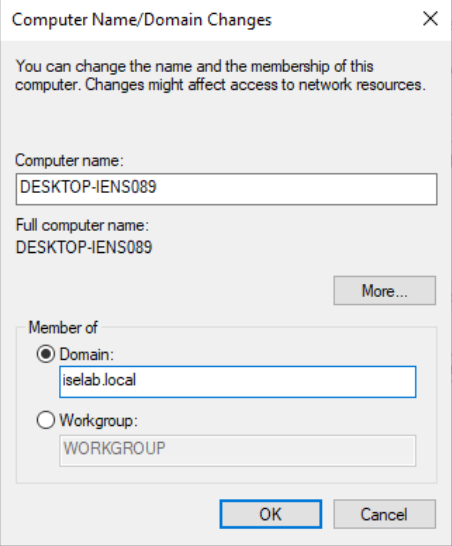
Click OK. You’ll then be prompted for credentials with permission to join the domain:
The computer has been joined to the domain:
The computer will have to be restarted as part of joining the domain:
Select Restart Now to restart:
It will take some time…:

After logging in, certificates will be created for both the user and computer. We can verify this on the CA:
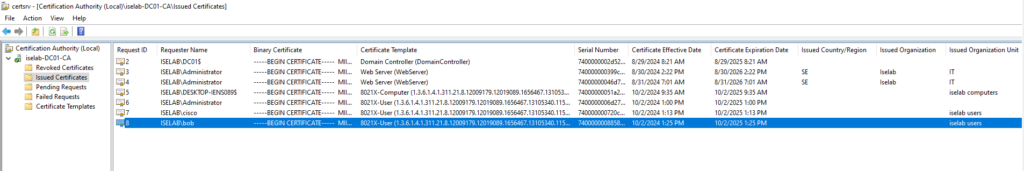
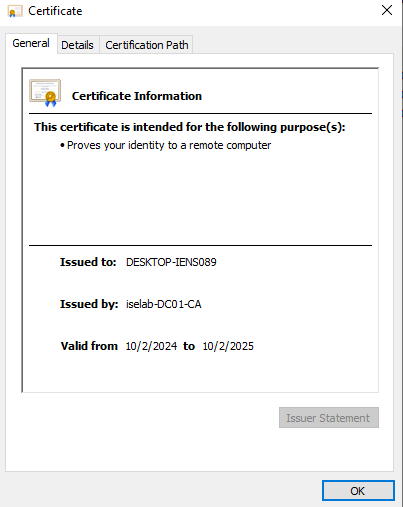
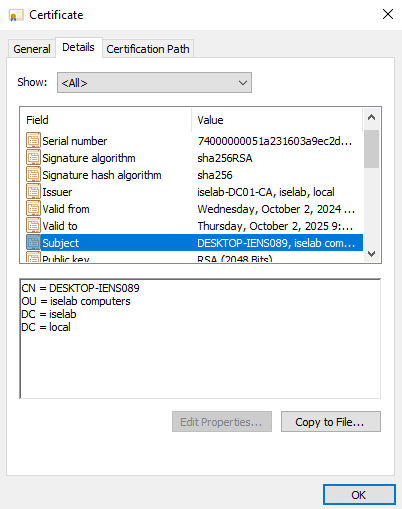
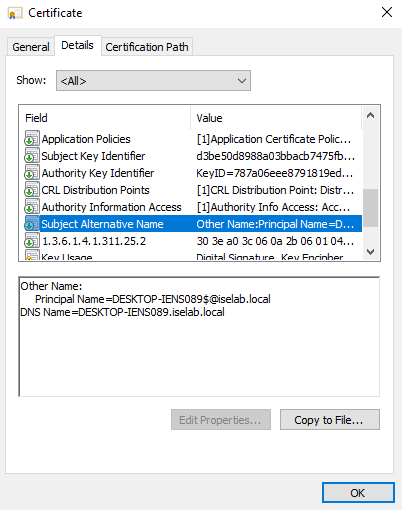
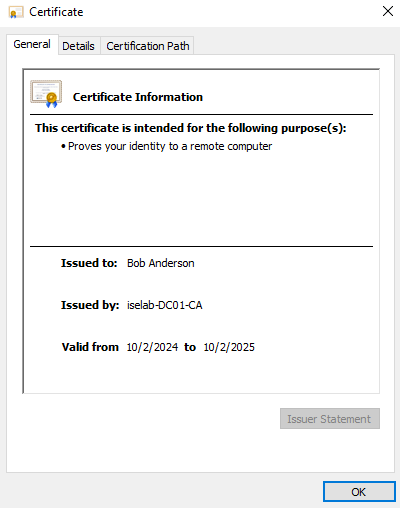
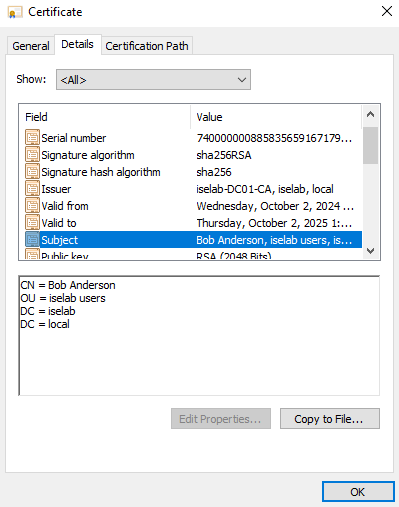
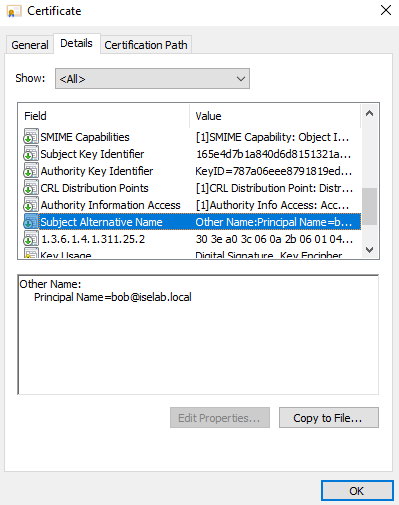
You can also use the cert manager on the client to verify the certificates. Below is the computer certificate:
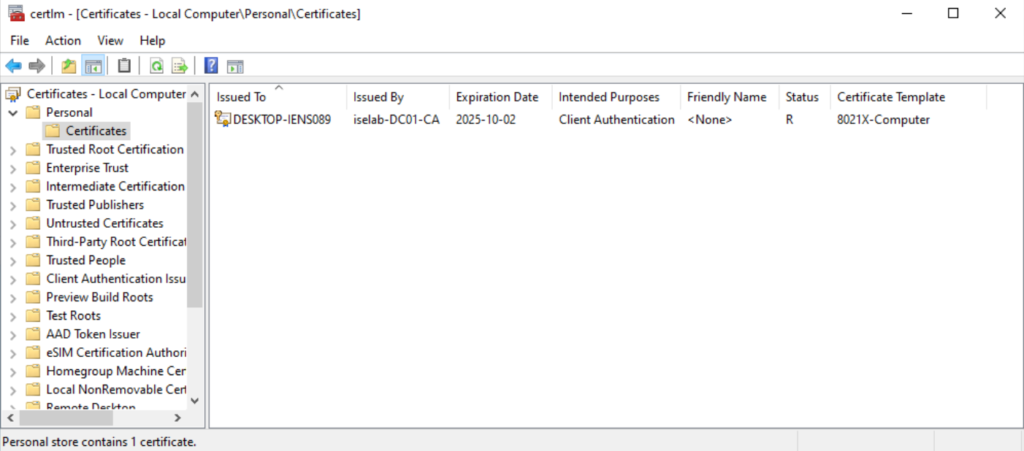
The trusted root CA for computer certificates:
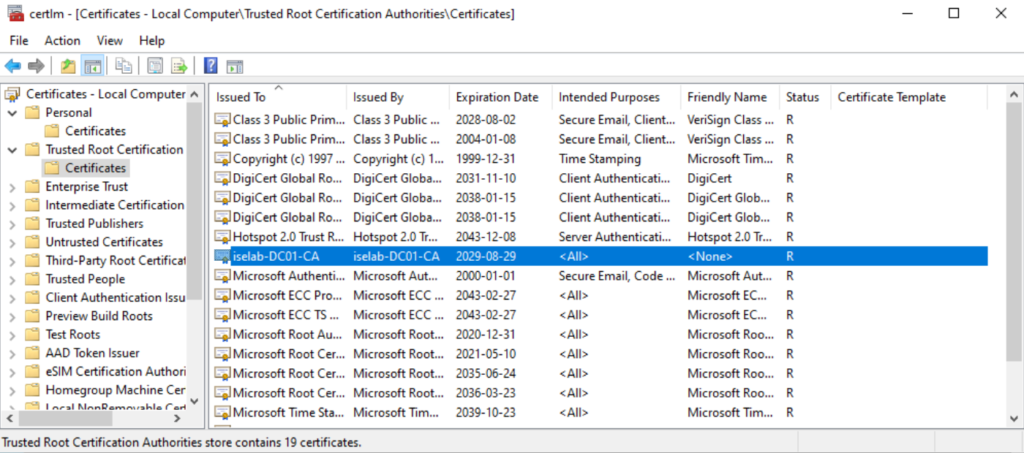
The user certificate:
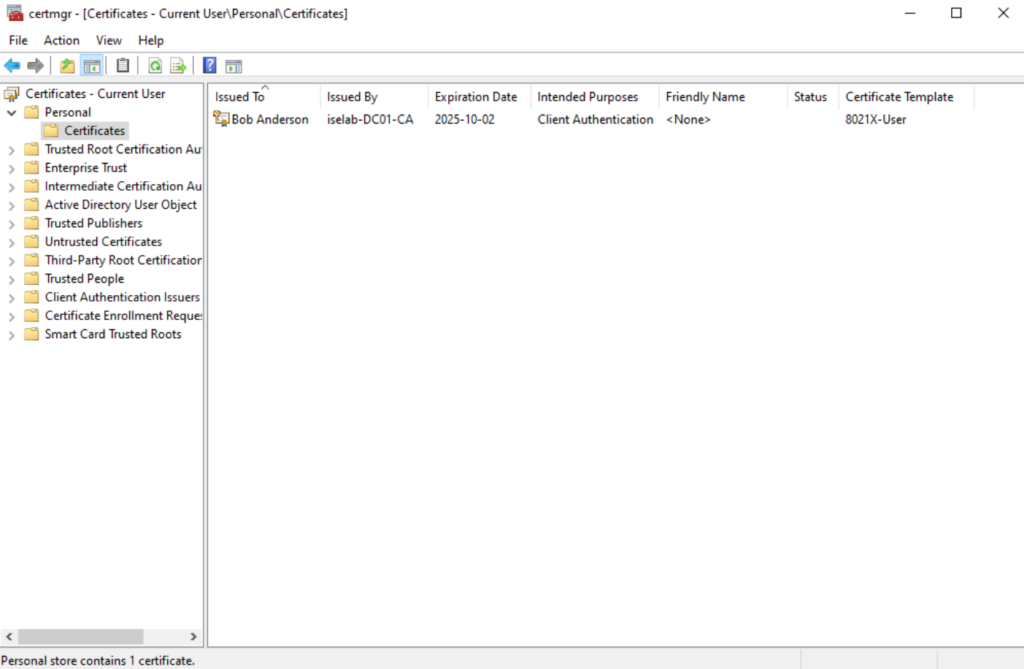
Trusted root CA for user certs:
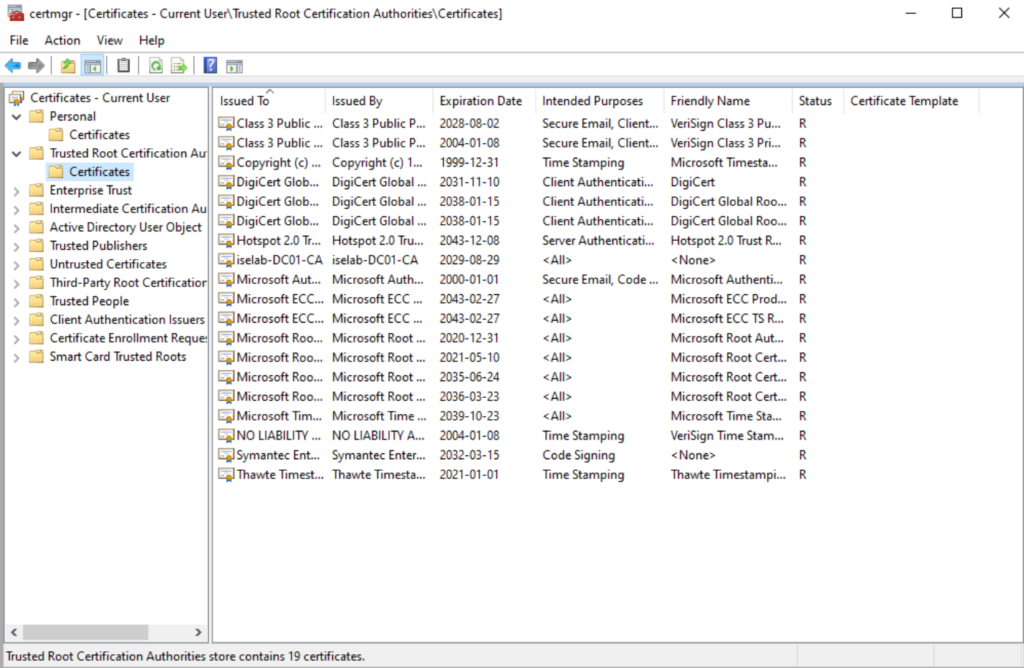
Before I got my setup working, I had to do Continue reading
By default, users and computers will be placed in containers in AD. These containers don’t support the use of GPOs, which is one of the reasons to create OUs to hold the objects instead. To verify what the default user and computer container is, we’ll leverage Powershell. First, we’ll check the computers container:
PS C:\Users\Administrator> Get-ADDomain | select computerscont* ComputersContainer ------------------ CN=Computers,DC=iselab,DC=local
Then, we’ll check the users container:
PS C:\Users\Administrator> Get-ADDomain | select userscont* UsersContainer -------------- CN=Users,DC=iselab,DC=local
Now, in my lab I have created iselab users and iselab computers where I want the user- and computer objects to be placed:

We’re going to user some Powershell to modify where the user- and computer objects get placed, but first we’ll get the Distinguished Name (DN) of these OUs. To do this, we’ll first have to enable Advanced Features under View:

This will display some additional containers:

Now right click the OU, such as iselab computers, and select Properties:

This will display the following window:

Now go to Attribute Editor tab, double click distinguishedName and right click and select Copy:

Then, we’ll user Powershell to redirect to this OU:
PS C:\Users\Administrator> redircmp "OU=iselab computers,DC=iselab,DC=local" Redirection was successful.
Let’s verify what Continue reading
The use of Group Policy Objects (GPO) can be really powerful in a Windows environment. In this post we’re going to leverage GPO to distribute certificates to the user and computer as well as enabling the 802.1X supplicant.
First, let’s see if there are any certificates on the Windows 10 VM in my lab:
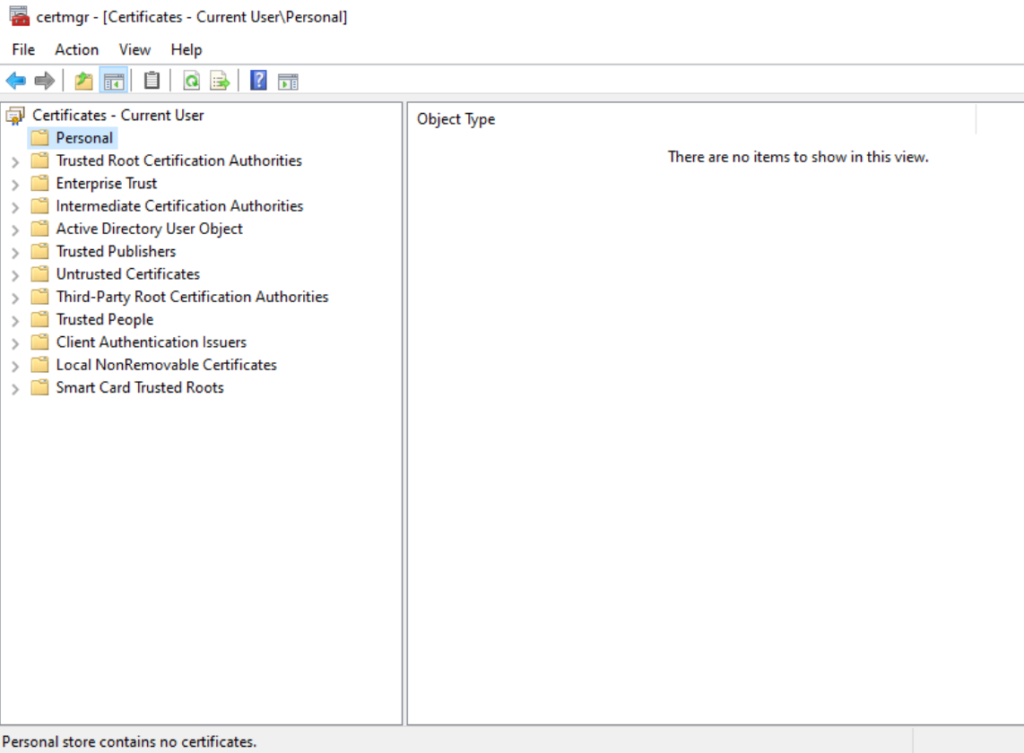
Currently, there are no certificates present on the VM. It has also not been joined to the domain.
First, open the GPO app:
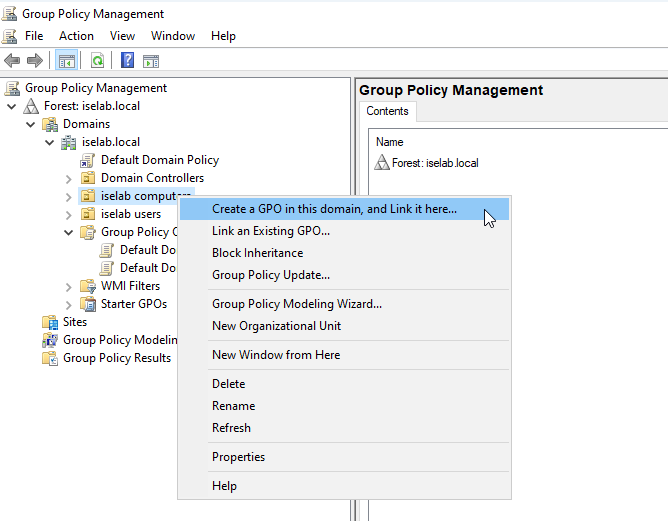
There’s a default domain policy that can be used, but I’m going to create new policies, one for users, and one for computers. First, let’s create a policy for computers. I’m going to right click my computer OU, named iselab computers, and then select Create a GPO in this domain, and Link it here…:
Give the GPO a name:
The GPO has been created:
Right click the GPO and select Edit…:
The GPO Editor window opens:
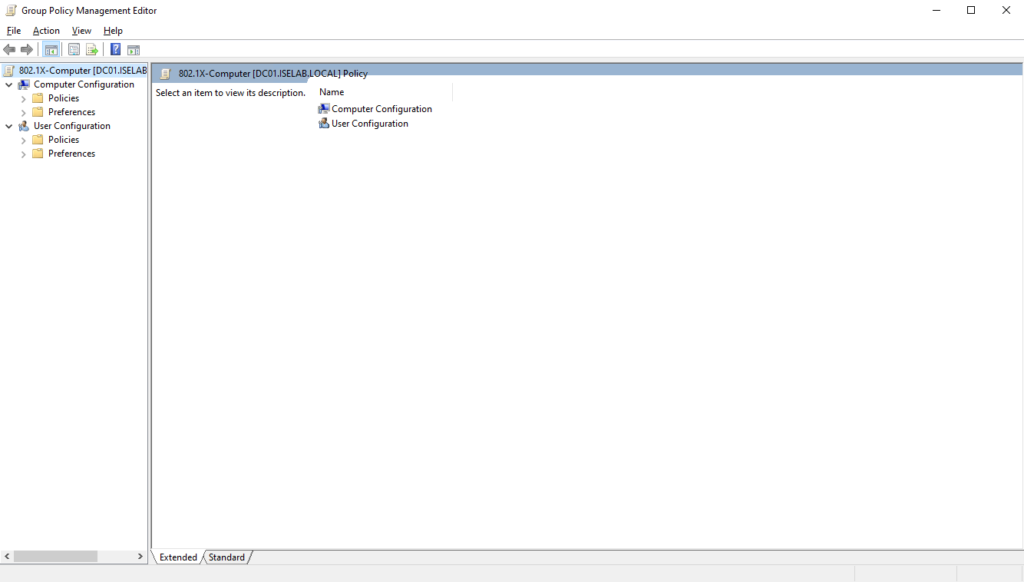
Then we’re going to navigate to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies and select Certificate Services Client – Auto Enrollment and then Properties:
A new window opens up:
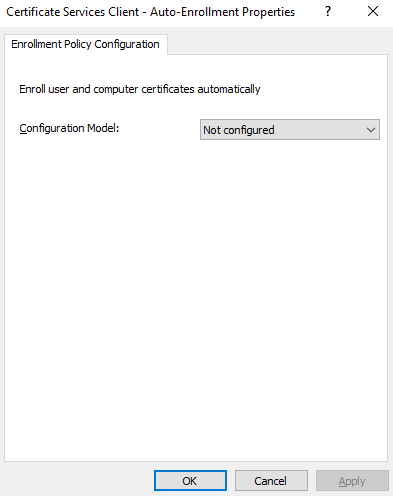
Change the Configuration Model to Enabled and Continue reading
Most ISE deployments use a join to Active Directory to be able to query AD groups, perform user lookups, etc. In this post, I’ll join my ISE lab server to AD. First I’m going to create two OUs in my AD, one for users and one for computers. Why not use the default ones? They are containers, not OUs, which means you can’t apply GPOs to them. Additionally, it makes for cleaner separation from the built-in accounts and allows for applying policies that won’t affect them. I’m creating two OUs:
This is done by going to Active Directory Users and Computers, then right clicking the AD domain and selecting New -> Organizational Unit:
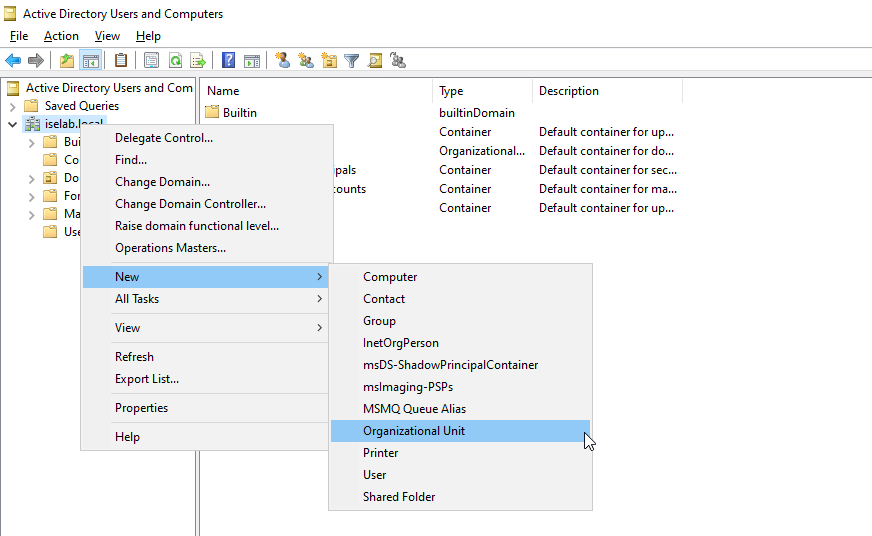
Give the OU a name and then click OK:
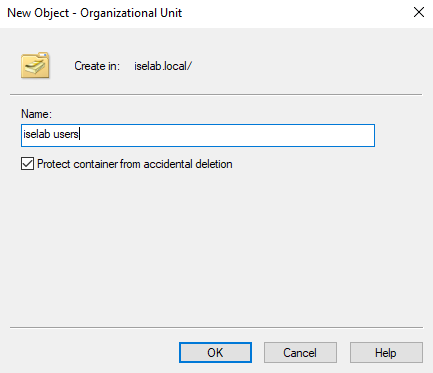
Repeat for the computers OU. You should now be able to see the OUs:
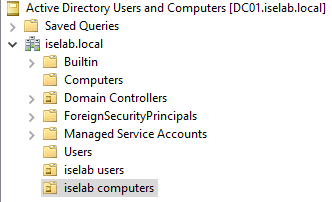
I’m going to create a user named Bob that I’ll be using to test login later. Right click the users OU and then select New -> User:
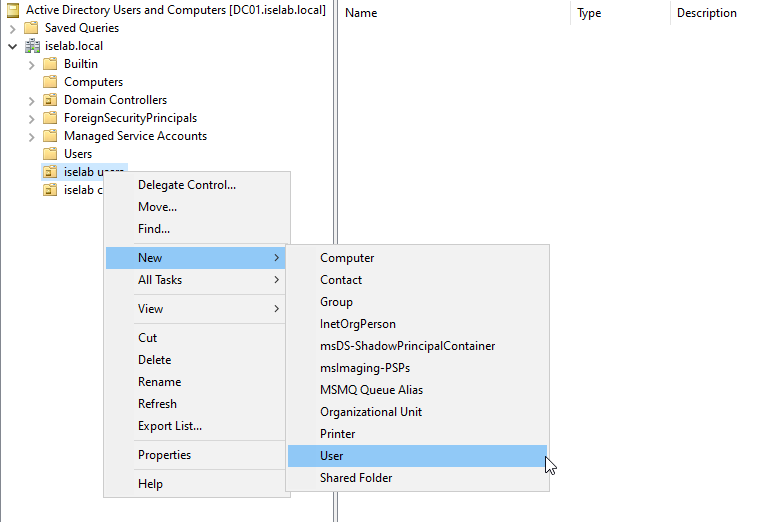
Enter the name and logon name:
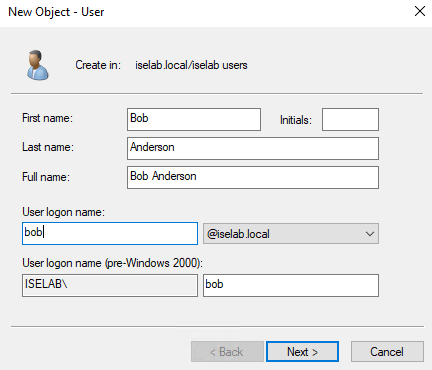
Click Next. Enter a password for the user. As this is a lab, I won’t require that the user changes the password and the Continue reading
When ISE is installed, all the certificates used for different services such as EAP, Admin portal, etc., are self signed. Below is a short summary of the certificates that ISE uses:
The certificates can be seen by going to Administration -> System -> Certificates:
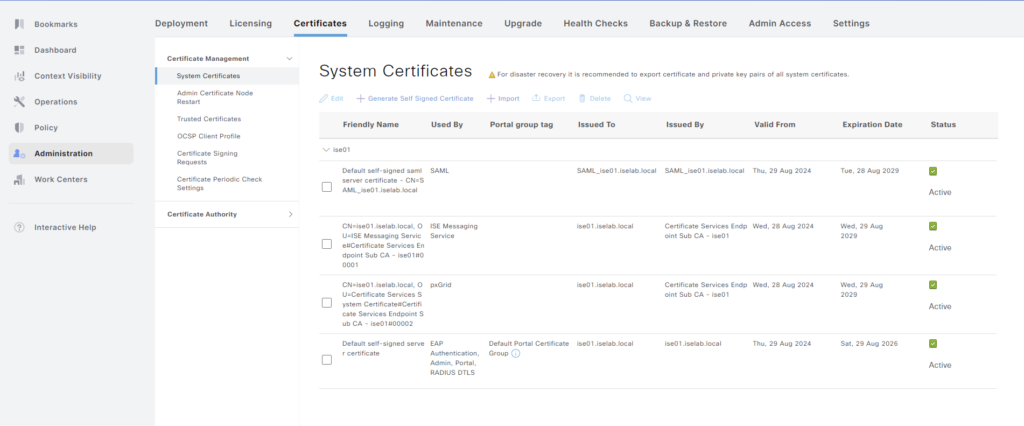
A certificate can be viewed by selecting the checkbox and clicking View:
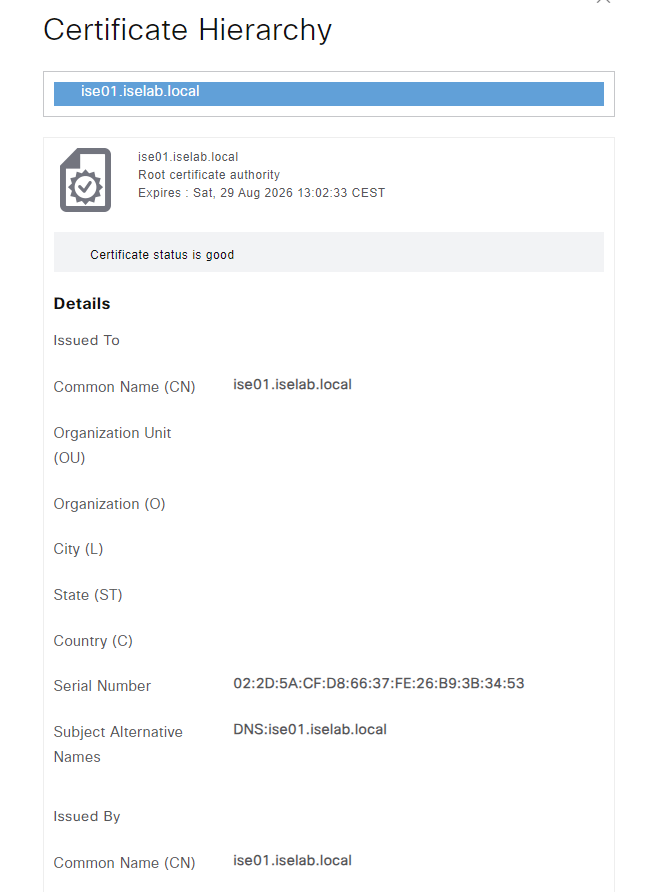
Self-signed certificates aren’t good. Certificates should be signed by a trusted CA. That could be a public root CA, or more commonly, especially for labs, an internal CA. Before such a certificate can be installed, ISE must be configured to trust that CA. This is done by importing the root CA certificate. I’ll download the certificate from the web service on the ADCS server. The web service is reachable on https:://<IP of ADCS server>/certsrv/. Click Download a CA certificate, certificate chain or CRL:
On the next page, change to Base 64 and then click Download CA certificate:
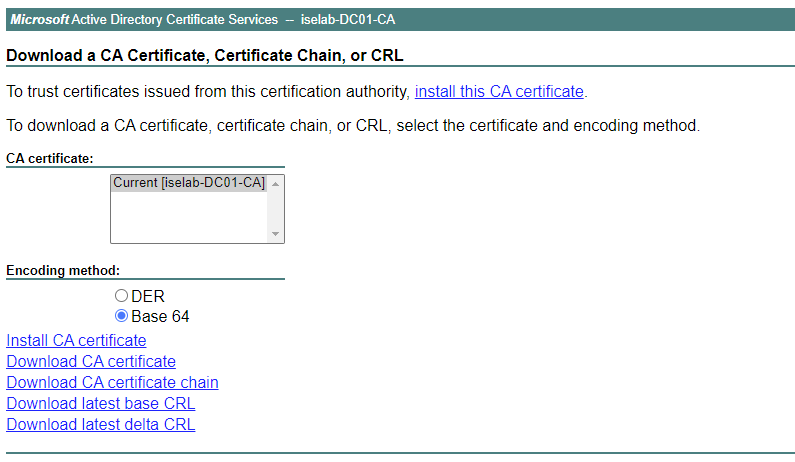
The file is downloaded Continue reading
This post describes how to install a Cisco ISE evaluation VM for labbing. The VM will run for 90 days, providing a full feature set for up to 100 endpoints.
Start by downloading the software. I’ll be using an OVA as I’m going to run my VM on ESX:

Deploy the OVA and select Eval version:
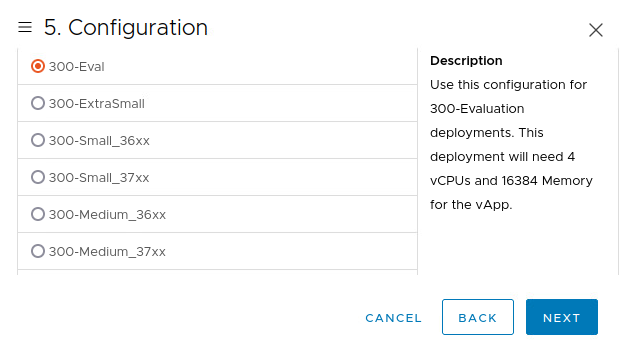
Power on the VM. When the VM boots, the following prompt is shown:

Type setup and press enter:
You will have to configure the hostname, IP address, name server, and so on:
Press 'Ctrl-C' to abort setup Enter hostname[]: ise01 Enter IP address []: 192.168.128.102 Enter IP netmask []: 255.255.255.0 Enter IP default gateway []: 192.168.128.1 Do you want to configure IPv6 address? Y/N [N]: N Enter default DNS domain []: iselab.local Enter primary nameserver []: 192.168.128.100 Add secondary nameserver? Y/N [N]: N Enter NTP server[time.nist.gov]: ntp.netnod.se Add another NTP server? Y/N [N]: N Enter system timezone[UTC]: CET Enable SSH service? Y/N [N]: Y Enter username [admin]: admin Enter password: Enter password again: Bringing up the network interface...
The installation will take some time…
When the installation Continue reading
In my ISE lab I’m going to be using EAP-TLS and TEAP, which means I’ll be needing user and computer certificates. The goal is to be able to enable the 802.1X supplicant via GPO and to distribute certificates automatically without requiring any user input. Another post will cover GPO, in this post I’ll cover creating the certificate templates in ADCS.
When opening the CA app, there are a number of templates provided by default:
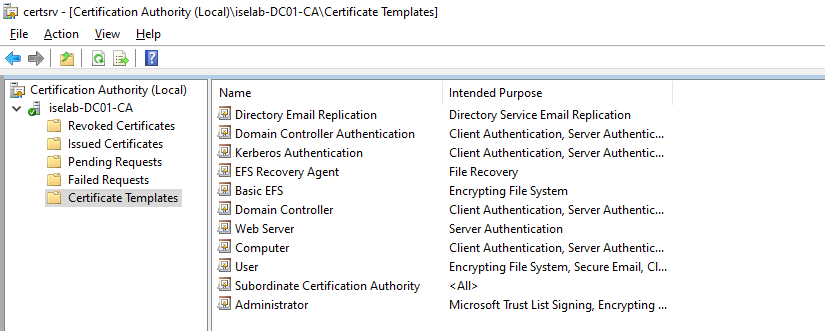
There are already templates for User and Computer, but it’s better to leave the default templates alone and create new ones. First, we’ll create a template for user certificates. Start by right clicking Certificate Templates and selecting Manage:
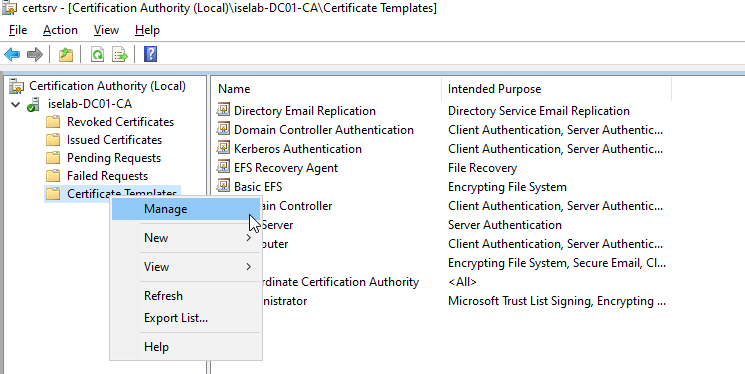
Then we’re going to right click the User template and select Duplicate Template:
This is going to open up a new window with properties of the template:
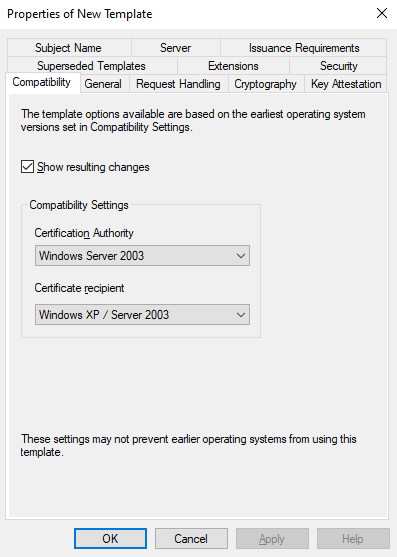
Go to General and give the template a name:
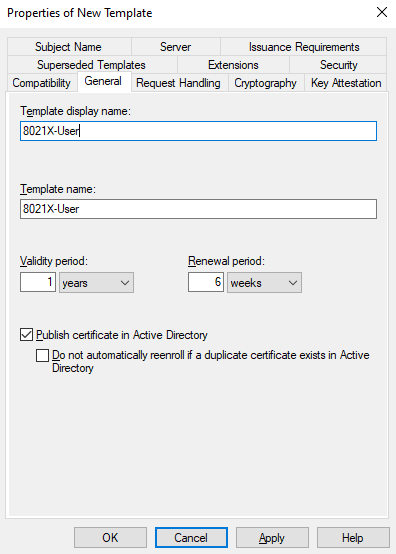
Don’t select the Do not automatically reenroll option or it won’t be possible to renew certs before they expire.
Then go to Request Handling. We’re going to uncheck the Allow private key to be exported option as this is considered more secure:
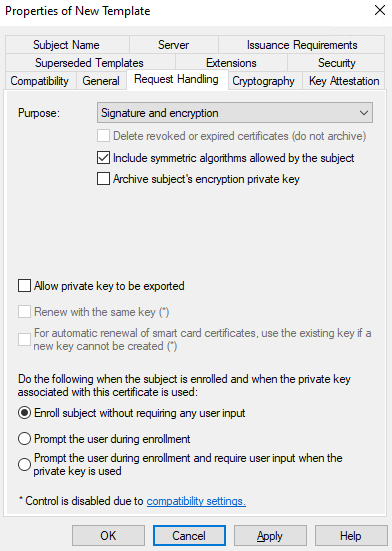
Make sure Enroll subject without requiring any Continue reading
This post describes how to install Active Directory Certificate Services (ADCS) onto a domain controller. It’s for labbing purposes which means I’m going to run this all on a single server instead of a more realistic setup with offline root, issuing CA, and possibly intermediate CA. Don’t use this post for anything designed to go into production!
To add the ADCS role. Go to Server Manager, click Add roles and features. Click Next until you get to Server Roles. Select Active Directory Certificate Series:

Click Add Features. Click Next. Click Next. Then a warning is displayed that it’s not possible to change the computer name or domain settings:

Click Next. Select Certification Authority and Certification Authority Web Enrollment:

Selecting Certification Authority Web Enrollment will install IIS and a small web site will be built to provide certificate services.
Click Add Features. Click Next. Click Next. Select Restart the destination server automatically if required:

Click Install. The installation starts:

When the installation has finished, click Close. Click AD CS in Server Manager. Click More… where it says Configuration required for Active Directory Certificate Services:

Click Configure Active Directory Certificate Services on the destination server:

Select an Continue reading
In the previous post, Setting up Active Directory for ISE Lab, we enabled Active Directory Domain Services. The DNS role was also added automatically as part of this process. In this post, we’ll add DHCP to the server.
Go to Server Manager, click Add roles and features. Click Next until you get to Server Roles. Select DHCP Server. This will display a window asking if required services should be installed:

Click Add Features. Click Next until getting to the Confirmation screen. Select Restart the destination server automatically if required. Since this is a lab, it’s OK to restart.

Select Yes. Then Click Install. The installation starts:

After the installation finishes, click Close.
The DHCP role has been added:

Let’s configure two DHCP scopes, one for employees and one for guests. Open the DHCP app, then expand the server and then IPv4. Right click on IPv4 and select New Scope…

This launches the New Scope Wizard:

Give the scope a name and a description:

Click Next. Then configure starting IP, ending IP, and the subnet mask:

Click Next. I’m not adding any exclusions so clicking Next again. Then configure the lease duration, I’m setting it to 1 day instead of Continue reading
A question I often get is, how do you get experience in IT? For people trying to break into this industry, what can they do to gain experience? How can they showcase that experience to a potential employer even if they are applying for their first job? Breaking into a new industry can be the most difficult thing, you lack experience and most of all you probably lack a network. Here are my thoughts on how you can gain that experience.
The ROI on university studies will vary depending on if you live in a country like me where studies are financed by tax and there is no tuition, or in a country where it can be very costly. That’s not the argument here, university studies can give some things that is difficult to achieve in any other way. I did three years at a university and here’s why I think it’s really valuable.
Time – Having two or three years of dedicated studies is a luxury you won’t have at any other point in your career. You have a full-time job and trying to learn a new discipline on top of that is going to be much Continue reading
A key component of an ISE home lab is having Active Directory installed. In this post I’ll go through setting up basic AD for use with ISE. This post is not going to cover licensing. I’m assuming you are running the eval version, which is good for 180 days, or that you already have a valid license.
My server is running in an ESX environment based on the following specs:
I’m using more than the minimum requirements. Spec it as you like based on what capacity you have available.
The first step is installing the OS. This part is easy and pretty much only requires you to set an Administrator password.
When the server has booted, start by changing the name of the server. It’s better to do this before changing any roles. Go to System Settings -> Computer Name and click Change… Set the desired name. I’m using the name dc01 in my lab. Click OK.

Changing the name is going to trigger a restart. Choose Restart Now.
From Server Manager, click Add roles and features. Click Next until you get to Continue reading
One of the best ways of learning something is building a lab for it. Especially when it comes to complex topics like network authentication. When I started learning about network authentication and Cisco Identity Services Engine (ISE), I found that there wasn’t a lot of clear information on how you build a lab. Not in Cisco documentation and also not on blogs, etc. In this post I’ll explain how I built my lab using CML and ESX.
Having a lab with ISE only is not going to get you very far. At a minimum, I think the following devices are needed in a network authentication lab:
For my lab, I’m using only virtual devices. The focus is on learning network authentication and ISE which is why I’ve setup a very simple PKI, ignoring best practices such as offline root, intermediate CA, and so on. I might lab that at a later stage, but that’s not the current focus.
The topology of my lab is shown below:
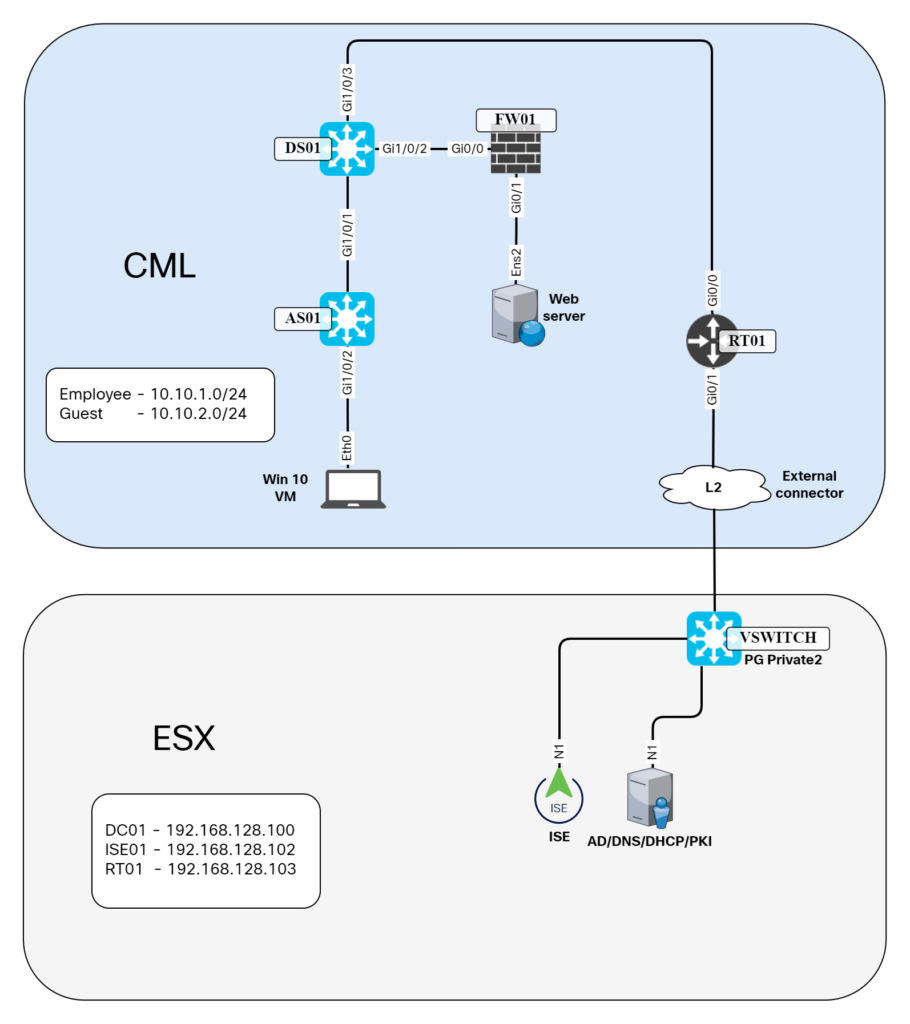
Note that some VMs such as the virtual Catalyst Continue reading
This is a quick post to describe how to reclaim disk space being used by an old Windows install. Recently, I upgraded to Windows 11 from Windows 10. I noticed that I was starting to run a bit low on disk space on my SSD. I have a 512 GB SSD and had less than 100 GB available:

I noticed that there is a folder named Windows.old that is 40 GB in size:

The instructions to reclaim the space seemed clear. Go to Settings -> System -> Storage and reclaim the space labeled as Previous Windows installation. However, ther was no such category when I tried:

After some searching and a little bit of thinking, I realized that this is probably a privileges problem. I became local admin by using the PAM tool. Then I ran the disk cleanup util as administrator:

I can now see that there are previous Windows installations:

I select to delete Previous Windows installations:

You have to confirm that it’s OK to delete:

The deletion process starts:

This will take some time…
There is now more space available:

If you’re running low on disk, check if you have previous Windows installations that you can Continue reading
This is a quick post on how to perform NAT overload (PAT) towards a specific host only. I have an inside network of 10.10.1.0/24. I need a host in this network to reach the host 192.168.0.1. They don’t have direct connectivity so I need to PAT it behind the router which has an IP of 192.168.128.103. I don’t want to PAT all the traffic from 10.10.1.0/24, though, only towards this specific host. There are hosts in 192.168.128.0/24 that the VM should access using its original source. The network is shown in the diagram below:
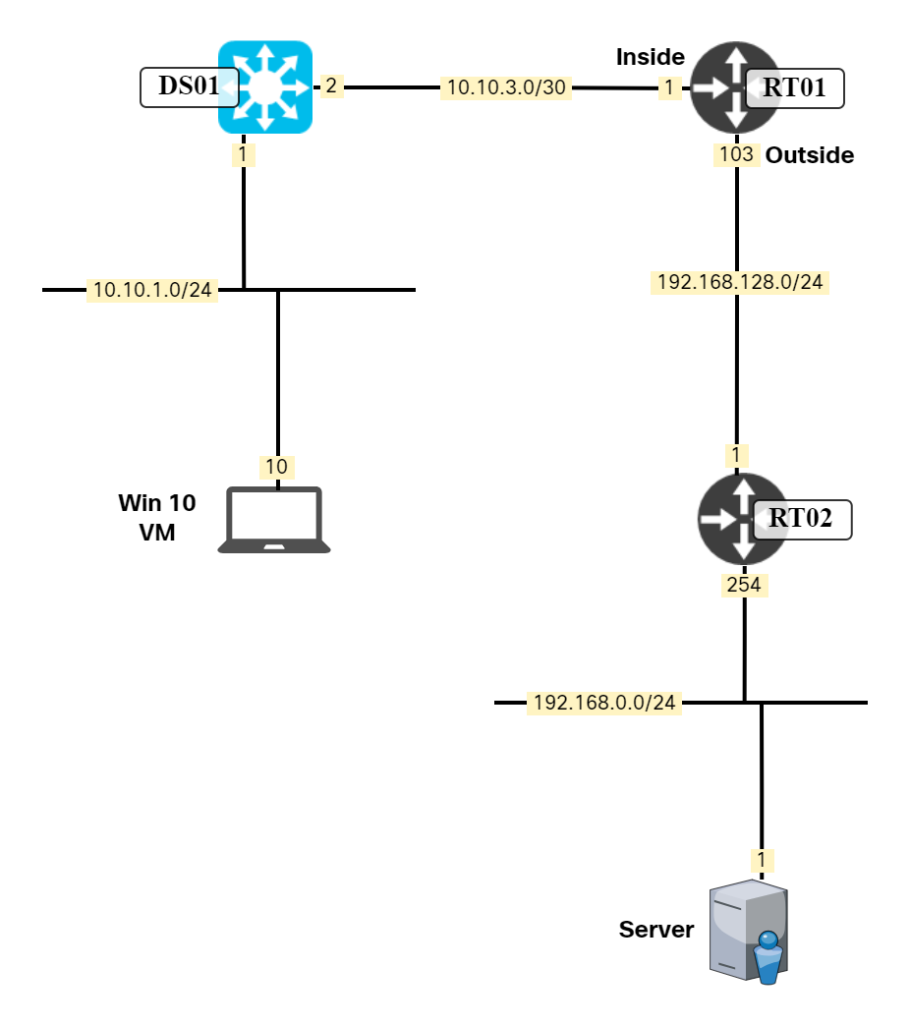
First, I’ll define my inside and outside interface:
RT01(config)#int gi0/0 RT01(config-if)#ip nat inside RT01(config-if)#int gi0/1 RT01(config-if)#ip nat outside
Then I’m going to create the ACL that matches on traffic from the 10.10.1.0/24 network to the host 192.168.0.1:
RT01(config)#ip access-list extended NAT-SRC-10.10.2.0/24 RT01(config-ext-nacl)#permit ip 10.10.2.0 0.0.255.255 host 192.168.0.1
Then, I’ll configure the NAT statement to match on the ACL and do an overload to interface Gi0/1:
RT01(config)#ip nat inside source list NAT-SRC-10.10.2. Continue reading