Author Archives: Dina Kozlov
Author Archives: Dina Kozlov
You can deploy a remote Model Context Protocol (MCP) server on Cloudflare in just one-click. Don’t believe us? Click the button below.
This will get you started with a remote MCP server that supports the latest MCP standards and is the reason why thousands of remote MCP servers have been deployed on Cloudflare, including ones from companies like Atlassian, Linear, PayPal, and more.
But deploying servers is only half of the equation — we also wanted to make it just as easy to build and deploy remote MCP clients that can connect to these servers to enable new AI-powered service integrations. That's why we built use-mcp, a React library for connecting to remote MCP servers, and we're excited to contribute it to the MCP ecosystem to enable more developers to build remote MCP clients.
Today, we're open-sourcing two tools that make it easy to build and deploy MCP clients:
use-mcp — A React library that connects to any remote MCP server in just 3 lines of code, with transport, authentication, and session management automatically handled. We're excited to contribute this library to the MCP ecosystem to enable more developers to build remote MCP clients.
Today, we're excited to collaborate with Anthropic, Asana, Atlassian, Block, Intercom, Linear, PayPal, Sentry, Stripe, and Webflow to bring a whole new set of remote MCP servers, all built on Cloudflare, to enable Claude users to manage projects, generate invoices, query databases, and even deploy full stack applications — without ever leaving the chat interface.
Since Anthropic’s introduction of the Model Context Protocol (MCP) in November, there’s been more and more excitement about it, and it seems like a new MCP server is being released nearly every day. And for good reason! MCP has been the missing piece to make AI agents a reality, and helped define how AI agents interact with tools to take actions and get additional context.
But to date, end-users have had to install MCP servers on their local machine to use them. Today, with Anthropic’s announcement of Integrations, you can access an MCP server the same way you would a website: type a URL and go.

At Cloudflare, we’ve been focused on building out the tooling that simplifies the development of remote MCP servers, so that our customers’ engineering teams can focus their time on building out the MCP tools for their Continue reading
In late November 2024, Anthropic announced a new way to interact with AI, called Model Context Protocol (MCP). Today, we’re excited to show you how to use MCP in combination with Cloudflare to extend the capabilities of Claude to build applications, generate images and more. You’ll learn how to build an MCP server on Cloudflare to make any service accessible through an AI assistant like Claude with just a few lines of code using Cloudflare Workers.
MCP is an open standard that provides a universal way for LLMs to interact with services and applications. As the introduction on the MCP website puts it,
“Think of MCP like a USB-C port for AI applications. Just as USB-C provides a standardized way to connect your devices to various peripherals and accessories, MCP provides a standardized way to connect AI models to different data sources and tools.”
From an architectural perspective, MCP is comprised of several components:
MCP hosts: Programs or tools (like Claude) where AI models operate and interact with different services
MCP clients: Client within an AI assistant that initiates requests and communicates with MCP servers to Continue reading
Chrome and Mozilla announced that they will stop trusting Entrust’s public TLS certificates issued after November 12, 2024 and December 1, 2024, respectively. This decision stems from concerns related to Entrust’s ability to meet the CA/Browser Forum’s requirements for a publicly trusted certificate authority (CA). To prevent Entrust customers from being impacted by this change, Entrust has announced that they are partnering with SSL.com, a publicly trusted CA, and will be issuing certs from SSL.com’s roots to ensure that they can continue to provide their customers with certificates that are trusted by Chrome and Mozilla.
We’re excited to announce that we’re going to be adding SSL.com as a certificate authority that Cloudflare customers can use. This means that Cloudflare customers that are currently relying on Entrust as a CA and uploading their certificate manually to Cloudflare will now be able to rely on Cloudflare’s certificate management pipeline for automatic issuance and renewal of SSL.com certificates.
With great power comes great responsibility Every publicly trusted certificate authority (CA) is responsible for maintaining a high standard of security and compliance to ensure that the certificates they issue are trustworthy. Continue reading
In today’s world, technology is quickly evolving and some practices that were once considered the gold standard are quickly becoming outdated. At Cloudflare, we stay close to industry changes to ensure that we can provide the best solutions to our customers. One practice that we’re continuing to see in use that no longer serves its original purpose is certificate pinning. In this post, we’ll dive into certificate pinning, the consequences of using it in today’s Public Key Infrastructure (PKI) world, and alternatives to pinning that offer the same level of security without the management overhead.
PKI exists to help issue and manage TLS certificates, which are vital to keeping the Internet secure – they ensure that users access the correct applications or servers and that data between two parties stays encrypted. The mis-issuance of a certificate can pose great risk. For example, if a malicious party is able to issue a TLS certificate for your bank’s website, then they can potentially impersonate your bank and intercept that traffic to get access to your bank account. To prevent a mis-issued certificate from intercepting traffic, the server can give a certificate to the client and say “only trust connections if Continue reading

In today’s world, technology is quickly evolving and some practices that were once considered the gold standard are quickly becoming outdated. At Cloudflare, we stay close to industry changes to ensure that we can provide the best solutions to our customers. One practice that we’re continuing to see in use that no longer serves its original purpose is certificate pinning. In this post, we’ll dive into certificate pinning, the consequences of using it in today’s Public Key Infrastructure (PKI) world, and alternatives to pinning that offer the same level of security without the management overhead.
PKI exists to help issue and manage TLS certificates, which are vital to keeping the Internet secure – they ensure that users access the correct applications or servers and that data between two parties stays encrypted. The mis-issuance of a certificate can pose great risk. For example, if a malicious party is able to issue a TLS certificate for your bank’s website, then they can potentially impersonate your bank and intercept that traffic to get access to your bank account. To prevent a mis-issued certificate from intercepting traffic, the server can give a certificate to the client and say “only trust connections if Continue reading

Let’s Encrypt, a publicly trusted certificate authority (CA) that Cloudflare uses to issue TLS certificates, has been relying on two distinct certificate chains. One is cross-signed with IdenTrust, a globally trusted CA that has been around since 2000, and the other is Let’s Encrypt’s own root CA, ISRG Root X1. Since Let’s Encrypt launched, ISRG Root X1 has been steadily gaining its own device compatibility.
On September 30, 2024, Let’s Encrypt’s certificate chain cross-signed with IdenTrust will expire. After the cross-sign expires, servers will no longer be able to serve certificates signed by the cross-signed chain. Instead, all Let’s Encrypt certificates will use the ISRG Root X1 CA.
Most devices and browser versions released after 2016 will not experience any issues as a result of the change since the ISRG Root X1 will already be installed in those clients’ trust stores. That's because these modern browsers and operating systems were built to be agile and flexible, with upgradeable trust stores that can be updated to include new certificate authorities.
The change in the certificate chain will impact legacy devices and systems, such as devices running Android version 7.1.1 (released in 2016) or older, as those exclusively Continue reading


This year, Cloudflare officially became a teenager, turning 13 years old. We celebrated this milestone with a series of announcements that benefit both our customers and the Internet community.
From developing applications in the age of AI to securing against the most advanced attacks that are yet to come, Cloudflare is proud to provide the tools that help our customers stay one step ahead.
We hope you’ve had a great time following along and for anyone looking for a recap of everything we launched this week, here it is:

今年,Cloudflare 正式成为踏入青春阶段,迎来了 13 岁生日。为了庆祝这个里程碑,我们发布了一系列公告,我们的客户和互联网社区都会从中受益。
从在人工智能时代开发应用,到防御尚未出现的最先进攻击,Cloudflare 很高兴能提供帮助我们的客户保持领先一步的工具。
我们希望您跟随我们度过了一段美好的时光,如果想要回顾我们本周发布的所有内容,请查看下文:

올해 Cloudflare에서는 공식적으로 13주년을 맞습니다. 우리는 이 이정표를 고객과 인터넷 커뮤니티 모두에 이점을 선사하는 다양한 발표로 기념했습니다.
AI 시대에 애플리케이션을 개발하는 것부터 아직 등장하지도 않은 최신 위협으로부터 보호하는 것까지 Cloudflare에서는 고객이 한 발자국 앞서 있을 수 있도록 도구를 제공한다는 사실을 자랑스럽게 여깁니다.
이러한 발표를 지켜보며 즐거운 시간이 되셨기를 바랍니다. 이번 주에 출시한 제품의 요약은 다음과 같습니다.

今年、Cloudflareは正式にティーンエイジャーとなり、13歳を迎えました。当社ではこの節目を、お客様とインターネットコミュニティの双方に有益な一連の発表で祝いました。
AI時代のアプリケーション開発から、これから起こる最先端の攻撃に対するセキュリティまで、Cloudflareはお客様が一歩先を行くためのツールを提供できることを誇りに思っています。
当社が今週発表したすべてのニュースをまとめてご紹介します:

Cloudflareが昨年12周年を迎えた折、Workers Launchpad Funding Programを発表しました。クラウドレアのデベロッパー・プラットフォーム上に構築する企業のためのスタートアップ加速プログラムのようなもので、企業の規模、ステージ、地域に制限はありません。
Launchpadの仕組みについての振り返り:四半期ごとに、私たちはスタートアップのグループを選出し、幅広い技術的アドバイス、指導、資金調達の機会を提供しています。これには、ファウンダーズ・ブートキャンプ、ソリューション・アーキテクトによるオープン・オフィス・アワー、デモ・デーなどが含まれます。また、資金調達の準備が整ったスタートアップは、40社以上のグローバルな大手ベンチャーキャピタルのコミュニティに参加することができます。
その代わり、率直な感想の提供を依頼しています。当社では、何がうまくいき、何がうまくいかず、何が必要なのかを知りたいのです。当社は、貴企業への出資者となることを求めることはなく、プログラムに参加するために費用を負担することも求めていません。
Targum (my startup) was one of the first AI companies (w/ @jamdotdev ) in the Cloudflare workers launchpad!
— Alex Volkov (@altryne) September 27, 2023
In return to tons of stuff we got from CF 🙏 they asked for feedback, and my main one was, let me do everything end to end on CF, I don't want to rent GPU servers… https://t.co/0j2ZymXpsL
ここまで、60か国近くからの応募を受けてきました。当社は、最初の2つのコホートに参加した50の見事な初期および成長段階の新興企業と緊密に協力する機会を得、当社のVCパートナー・コミュニティを40社以上に拡大し、Cloudflareを基盤とする新興企業への潜在的な投資額は20億ドルを超えました。
次は、コホート#3となります。 先日、第2コホートが終了し(デモ・デーをぜひご覧ください)、Launchpadの1歳の誕生日を祝い、そして先週行ったたくさんの発表の間に、皆様にすべてのニュースにキャッチアップしていただくために十分な時間をとることが必要だと考えました。そのため、第3コホートの締め切りを数週間延長し、2023年10月13日とします。また、先週水曜日に発表されたAIのいずれかをすでに利用している方のために、5名分の枠を確保しています。応募時には、現在お使いいただいているものを明記していただけるよう、お願いいたします。
お知らせをチェックし、コーヒーを飲んで休んだら、Workers Launchpadをチェックしてみてください。応募は簡単です。コーヒーが冷めないうちに、応募は完了するでしょう。
2023年のバースデーウィークは、以上です。また次回のイノベーション・ウィークでお会いしましょう!
i hate @Cloudflare launch week
— Dax (@thdxr) September 29, 2023
most launch weeks are underwhelming
cloudflare always makes me rethink everything i’m doing

Cette année, Cloudflare est officiellement entrée dans l'adolescence, puisque l'entreprise a fêté ses 13 ans. Nous avons fêté cet événement avec une série d'annonces qui profitent à la fois à nos clients et à la communauté Internet.
Du développement d'applications à l'ère de l'IA à la sécurisation contre des attaques extrêmement avancées et encore inconnues, Cloudflare est fière de fournir des outils qui aident nos clients à garder une longueur d'avance.
Nous espérons que vous avez passé un excellent moment à suivre notre actualité, et pour tous ceux qui souhaiteraient pouvoir consulter un récapitulatif de toutes les innovations que nous avons inaugurées cette semaine, le voici :

Este año, Cloudflare ha alcanzado oficialmente la adolescencia ¡cumplimos 13 años! Celebramos este hito con una serie de anuncios que benefician tanto a nuestros clientes como a la comunidad de Internet.
Desde el desarrollo de aplicaciones en la era de la IA hasta la protección contra los ataques más avanzados que están por llegar, Cloudflare se enorgullece de facilitar herramientas que ayudan a nuestros clientes a mantener una posición de ventaja.
Esperamos que te lo hayas pasado muy bien en este viaje. Si te interesa conocer un resumen de todos nuestros anuncios en esta semana, sigue leyendo:

Dieses Jahr ist Cloudflare offiziell ins Teenager-Alter eingetreten, denn wir feiern unser 13-jähriges Firmenjubiläum. Anlässlich dieses Meilensteins haben wir eine Reihe von neuen Produkten vorgestellt, von denen sowohl unseren Kunden als auch die Internet-Community im Allgemeinen profitieren werden.
Von der Anwendungsentwicklung im Zeitalter der KI bis hin zum Schutz vor den ausgefeiltesten Angriffen, die noch erdacht werden müssen: Mit den Werkzeugen von Cloudflare sind unsere Kunden dem Geschehen immer einen Schritt voraus.
Wir hoffen, dass unsere Ankündigungen für Sie von Interesse waren. Sollten Sie befürchten, etwas verpasst zu haben, finden Sie hier noch einmal ein Überblick über alles, was wir während der Birthday Week eingeführt haben:
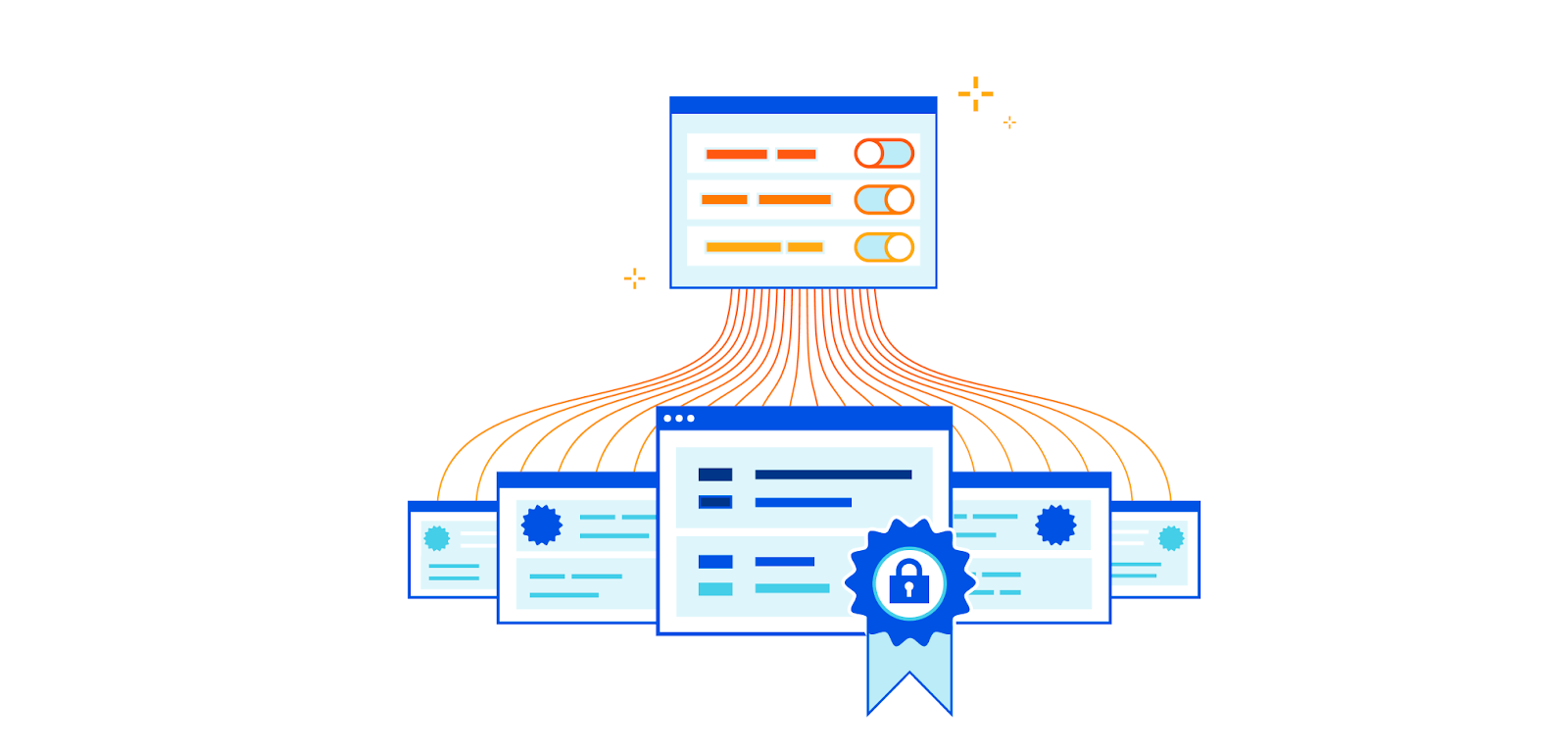
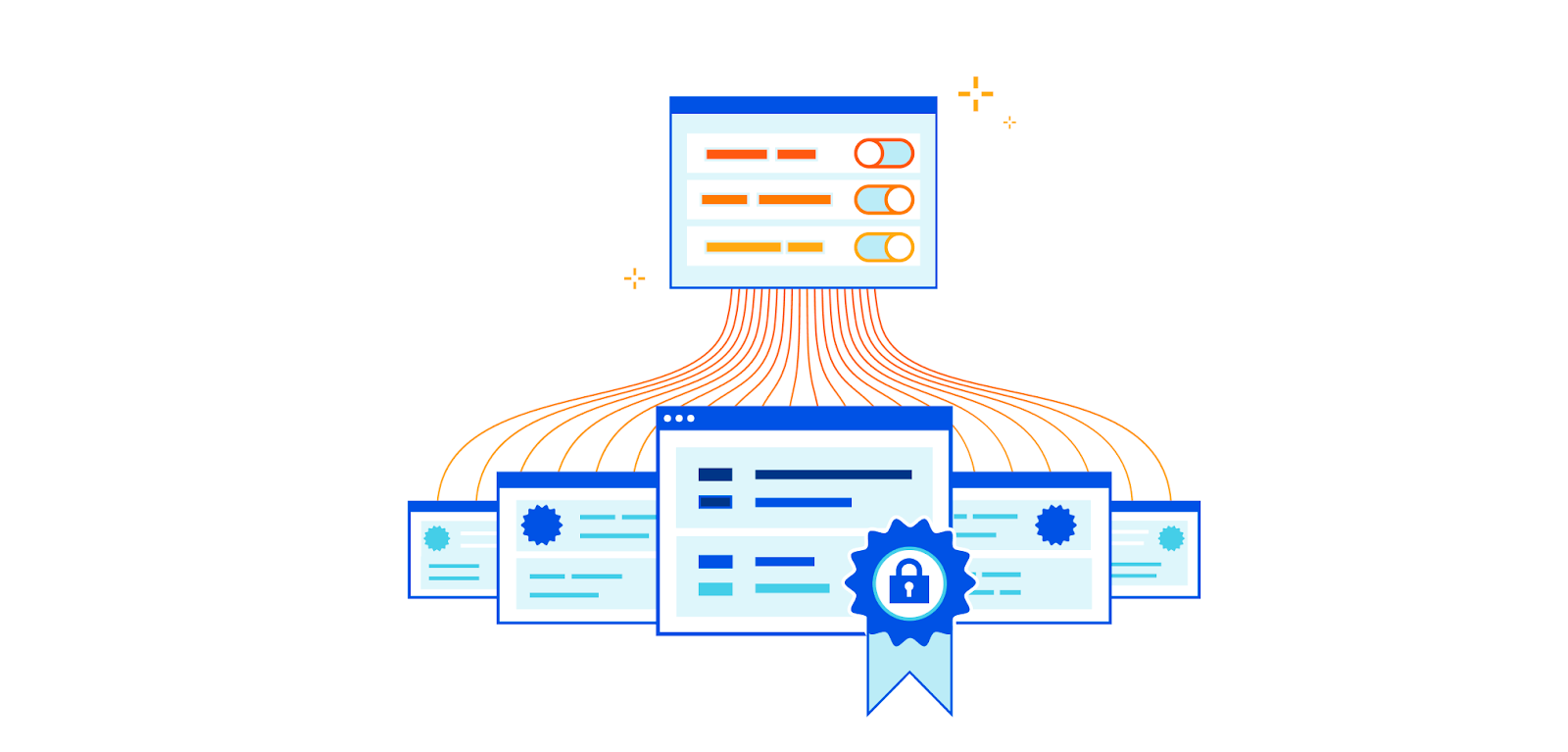
One of the goals of Cloudflare is to give our customers the necessary knobs to enable security in a way that fits their needs. In the realm of SSL/TLS, we offer two key controls: setting the minimum TLS version, and restricting the list of supported cipher suites. Previously, these settings applied to the entire domain, resulting in an “all or nothing” effect. While having uniform settings across the entire domain is ideal for some users, it sometimes lacks the necessary granularity for those with diverse requirements across their subdomains.
It is for that reason that we’re excited to announce that as of today, customers will be able to set their TLS settings on a per-hostname basis.
In an ideal world, every domain could be updated to use the most secure and modern protocols without any setbacks. Unfortunately, that's not the case. New standards and protocols require adoption in order to be effective. TLS 1.3 was standardized by the IETF in April 2018. It removed the vulnerable cryptographic algorithms that TLS 1.2 supported and provided a performance boost by requiring only one roundtrip, as opposed to two. For a user to benefit from Continue reading


APIs account for more than half of the total traffic of the Internet. They are the building blocks of many modern web applications. As API usage grows, so does the number of API attacks. And so now, more than ever, it’s important to keep these API endpoints secure. Cloudflare’s API Shield solution offers a comprehensive suite of products to safeguard your API endpoints and now we’re excited to give our customers one more tool to keep their endpoints safe. We’re excited to announce that customers can now bring their own Certificate Authority (CA) to use for mutual TLS client authentication. This gives customers more security, while allowing them to maintain control around their Mutual TLS configuration.
Traditionally, when we refer to TLS certificates, we talk about the publicly trusted certificates that are presented by servers to prove their identity to the connecting client. With Mutual TLS, both the client and the server present a certificate to establish a two-way channel of trust. Doing this allows the server to check who the connecting client is and whether or not they’re allowed to make a request. The certificate presented by the client - the client certificate Continue reading


We’re excited to announce Secrets Store - Cloudflare’s new secrets management offering!
A secrets store does exactly what the name implies - it stores secrets. Secrets are variables that are used by developers that contain sensitive information - information that only authorized users and systems should have access to.
If you’re building an application, there are various types of secrets that you need to manage. Every system should be designed to have identity & authentication data that verifies some form of identity in order to grant access to a system or application. One example of this is API tokens for making read and write requests to a database. Failure to store these tokens securely could lead to unauthorized access of information - intentional or accidental.
The stakes with secret’s management are high. Every gap in the storage of these values has potential to lead to a data leak or compromise. A security administrator’s worst nightmare.
Developers are primarily focused on creating applications, they want to build quickly, they want their system to be performant, and they want it to scale. For them, secrets management is about ease of use, performance, and reliability. On the other hand, security administrators are tasked Continue reading


To get a TLS certificate issued, the requesting party must prove that they own the domain through a process called Domain Control Validation (DCV). As industry wide standards have evolved to enhance security measures, this process has become manual for Cloudflare customers that manage their DNS externally. Today, we’re excited to announce DCV Delegation — a feature that gives all customers the ability offload the DCV process to Cloudflare, so that all certificates can be auto-renewed without the management overhead.
Security is of utmost importance when it comes to managing web traffic, and one of the most critical aspects of security is ensuring that your application always has a TLS certificate that’s valid and up-to-date. Renewing TLS certificates can be an arduous and time-consuming task, especially as the recommended certificate lifecycle continues to gradually decrease, causing certificates to be renewed more frequently. Failure to get a certificate renewed can result in downtime or insecure connection which can lead to revenue decrease, mis-trust with your customers, and a management nightmare for your Ops team.
Every time a certificate is renewed with a Certificate Authority (CA), the certificate needs to pass a check called Domain Control Validation (DCV). This is a process Continue reading


Today, we’re excited to announce a big security enhancement to our Keyless SSL offering. Keyless SSL allows customers to store their private keys on their own hardware, while continuing to use Cloudflare’s proxy services. In the past, the configuration required customers to expose the location of their key server through a DNS record - something that is publicly queryable. Now, customers will be able to use our Cloudflare Tunnels product to send traffic to the key server through a secure channel, without publicly exposing it to the rest of the Internet.
Security has always been a critical aspect of online communication, especially when it comes to protecting sensitive information. Today, Cloudflare manages private keys for millions of domains which allows the data communicated by a client to stay secure and encrypted. While Cloudflare adopts the strictest controls to secure these keys, certain industries such as financial or medical services may have compliance requirements that prohibit the sharing of private keys.In the past, Cloudflare required customers to upload their private key in order for us to provide our L7 services. That was, until we built out Keyless SSL in 2014, a feature that allows customers Continue reading
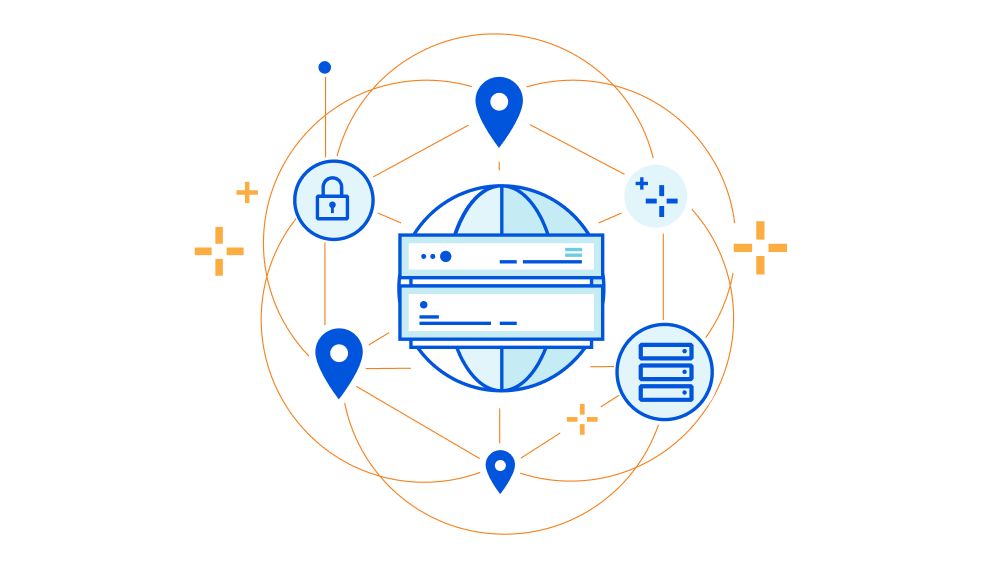
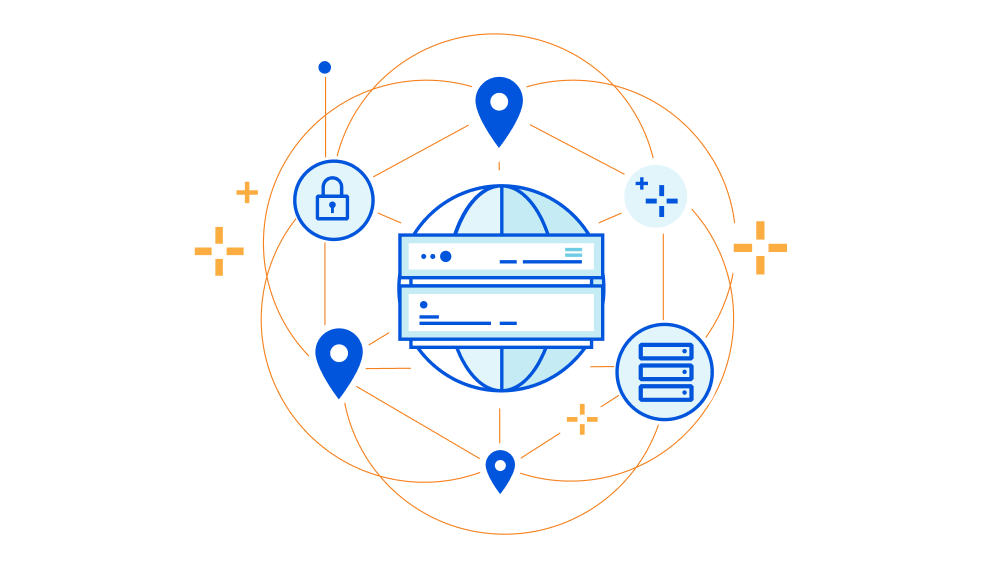
Today, traffic on the Internet stays encrypted through the use of public and private keys that encrypt the data as it's being transmitted. Cloudflare helps secure millions of websites by managing the encryption keys that keep this data protected. To provide lightning fast services, Cloudflare stores these keys on our fleet of data centers that spans more than 150 countries. However, some compliance regulations require that private keys are only stored in specific geographic locations.
In 2017, we introduced Geo Key Manager, a product that allows customers to store and manage the encryption keys for their domains in different geographic locations so that compliance regulations are met and that data remains secure. We launched the product a few months before General Data Protection Regulation (GDPR) went into effect and built it to support three regions: the US, the European Union (EU), and a set of our top tier data centers that employ the highest security measures. Since then, GDPR-like laws have quickly expanded and now, more than 15 countries have comparable data protection laws or regulations that include restrictions on data transfer across and/or data localization within a certain boundary.
At Cloudflare, we like to be prepared for the future. Continue reading