Author Archives: Geoff Wilmington
Author Archives: Geoff Wilmington
We are excited to share that as of July 2022, VMware NSX-T version 3.1 has passed Common Criteria certification for Network Devices under Collaborative Protection Profile 2.2e, also known as NDcPP 2.2e. This is one of many testaments to our commitment to providing industry-leading certified solutions for customers from federal departments and agencies, international governments and agencies, and other highly regulated industries and sectors. Along with FIPS, DISA-STIG, ICSA Labs firewall certification, and several other independent evaluations, the NDcPP 2.2e certification validates NSX as a reliable network virtualization platform that satisfies rigorous government security standards.
VMware NSX 3.1 is now listed:
From the NIAP Security Evaluation Summary:
The evaluation was carried out in accordance with the Common Criteria Evaluation and Validation Scheme (CCEVS) process and scheme. The criteria against which the VMware NSX-T Data Center 3.1 was evaluated are described in the Common Criteria for Information Technology Security Evaluation, Version 3.1 rev 5. The evaluation methodology used by the evaluation team Continue reading
It’s that time of year again; VMworld! This VMworld is unprecedented in its delivery this year. VMworld 2020 will be entirely online and general sessions available for anyone who wants to attend for free! There is a small fee track for Premier pass which has access to additional sessions. More on that in the links below. The numbers we’re seeing for potential attendees is staggering and people who may not have been able to attend in the past, can now join their industry peers for discussions, hands-on labs, and breakout and keynote sessions.
At previous VMworld events, it could be difficult to attend all the sessions you wanted, as they may have had times where one or more overlapped. This year, the majority of our sessions are on-demand for the attendee convenience. Log on and watch whatever the session you want, whenever you want. To ensure you don’t miss out on all the deepest technical NSX content the Network and Security Business Unit at VMware as created, we’ve come up with a list of sessions for you to check out:
Security
Apply Consistent Security Across VMs, Containers and Physical Server with NSX-T [ISNS1272]
Continue reading
It should come as no surprise how much emphasis organizations place on security today. Threats are becoming more and more sophisticated and the number of threats grow to uncontrollable rates every day.
One of the biggest downsides is that the rising cost of data breaches in 2019 alone, a global average of $3.92 million as reported by the Ponemon Institute and IBM Security July 2019 report, is enough to cause organizations to rethink or increase emphasis on their security strategies and how they can help secure their most important assets by improving the cyber hygiene in their organizations.
Cyber hygiene refers to what an organization can do to improve their security postures around physical hardware, software, and applications. If you’ve seen Pat Gelsinger’s keynote from 2017, he goes into the 5 pillars of good cyber hygiene and what organizations can do to improve basic and fundamental security for their business.
Over the last several years, VMware has been focusing on helping organizations move to Software-Defined Data Centers (SDDC) to improve their agility and meet the speed of business. As more organizations adopted the SDDC model, VMware found itself in a unique position Continue reading
When it comes to VMware NSX, support for VMware Horizon deployments have been a staple ask every release. NSX compliments Horizon deployments tremendously by:
Earlier this year, NSX-T Data Center 2.4 was released which brought identity firewalling, endpoint protection, and other necessary features for customers to consume equivalent to NSX Data Center for vSphere. The release of NSX-T Data Center 2.5 takes those features and provides even further scale enhancements to support small, medium, and the largest Horizon deployments.
The NSX-T and EUC Design Guide takes information provided in the VMware Horizon Reference Architecture and the VMware NSX-T Reference Design Guide, and brings the two platforms together into a single solution.
Let’s take a look at what all is covered and the use cases that NSX-T Data Center has for Horizon deployments:
NSX-T Data Center 2.5 supports massive scale that can cover an entire Horizon Pod scale, and more in some cases. This design guide Continue reading
The Guest Introspection platform has been included in NSX Data Center for vSphere for several years, mostly as a replacement for the VMware vShield Endpoint product and providing customers the ability to plug in their VMware certified partner solutions to allow agent-less anti-virus and anti-malware protections for a variety of data center workloads.
The Guest Introspection platform provides customers several outcomes.

Simplified AV management – Manual installation of agents into the guest operating system requires massive operational overhead just getting the agents deployed out on every virtual workload, managing the agent life-cycle post deployment, and for troubleshooting issues with the in-guest agents in day 2 operations.
Guest Introspection provides a centralized management interface for deploying the agentless components to the vSphere hosts, including the security policies, all while using vSphere objects and grouping of those objects to associate the endpoint policy. This provides granular policy creation and association in the workload environments.
Improved endpoint performance – When several or all of the virtual workloads kick off a scheduled AV scan, this can produce a massive resource drain from host resources where workloads might suffer performance concerns during Continue reading
Authors – Sridhar Subramanian and Geoff Wilmington
VMware NSX Data Center was built with the goal of consistent networking and security services independent of changing application frameworks or physical infrastructure. In the last couple of years, NSX Data Center has focused on delivering network and security abstractions for applications on any compute platform. In our journey, we have handled VM’s, containers, cloud, and now we are also looking to help our customers with scenarios where they need a unified experience for bare-metal workloads. The goal being to maintain a consistent security experience regardless of location or platform the workload is running on.
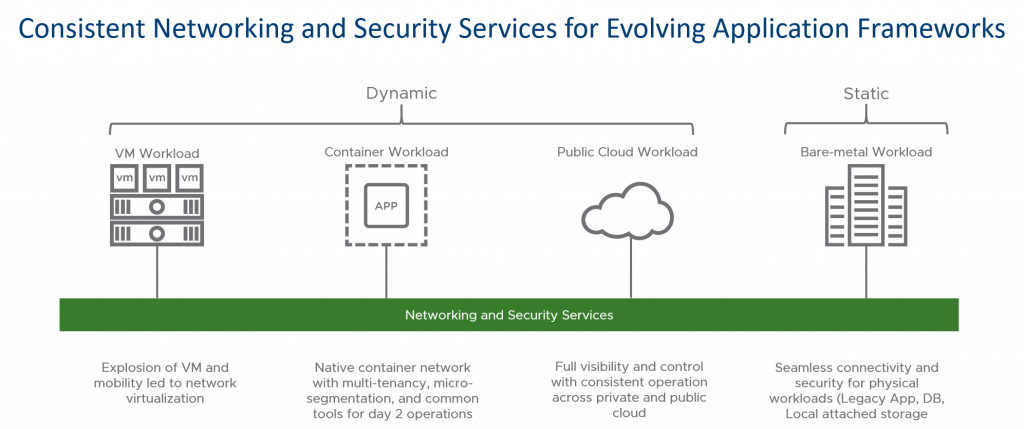
This experience means being able to take any workload, add it to an NSX Data Center Security Group and through the NSX Data Center Distributed Firewall have a consistent policy applied regardless of location and workload type. This consistent approach leverages the NSX DFW capabilities with stateful firewalling for the workloads. This is accomplished outside of using native OS capabilities like IP Tables or Windows Firewall so security admins only need to understand how to apply security through NSX DFW, and not have to understand the myriad of native OS approaches and complexity. By centralizing Continue reading
In a previous post by my colleague, Stijn, discussed the new changes to how NSX for vSphere 6.4 handles Remote Desktop Session Host, RDSH, systems with the Identity-based Firewall and context-aware micro-segmentation.
RDSH is an underlying technology from Microsoft that many vendors take advantage of to provide overlay management and application deployment technologies for. In this post, we’re going to discuss how NSX 6.4 and the new changes to support RDSH hosts works with Citrix XenApp systems.
Citrix XenApp can provide multiple users the ability to connect to a single system to access their applications using the RDSH technology. These users can be of the same type, for example all HR users, or of multiple types, HR and Engineering users. NSX has supported User Identity based firewalling for Virtual Desktops since the 6.0 release, but it did not address RDSH in which multiple user sessions are connecting to the same host This meant less flexibility in controlling what users could access data center application servers without isolating one set of users to one RDSH server. This model created a very rigid architecture for XenApp customers to follow, which brought about the use of Continue reading
In a previous post my colleague, Stijn, discussed the enhancements to how NSX for vSphere 6.4 handles Remote Desktop Session Host, RDSH, systems with the Identity-based Firewall and Context-Aware Micro-segmentation.
Remote Desktop Services is an underlying technology from Microsoft that many vendors take advantage of to provide overlay management and application deployment technologies for. In this post, we’re going to discuss how NSX for vSphere 6.4 allows customers to run RDS hosts with granular security for VMware Horizon systems.
VMware Horizon can provide multiple users the ability to connect to a single system to access their applications using the RDSH technology. These users can be of the same type, for example all HR users, or of multiple types, HR and Engineering users. In previous versions of NSX, it was not possible to individually secure user sessions and create Distributed Firewall (DFW) rule sets according to the user session logged into an RDSH server. This meant less flexibility in controlling what users could access data center application servers without isolating one set of users to one RDSH server. This model created a very rigid architecture for Horizon customers to follow.
Horizon allows customers Continue reading