Author Archives: Humair Ahmed
Author Archives: Humair Ahmed
NSX-V 6.3, released last month, introduced many new features. In my last blog post, NSX-V 6.3: Cross-VC NSX Security Enhancements, I discussed several new Cross-VC NSX security features. In this post I’ll discuss another new feature called Controller Disconnected Operation (CDO) mode which provides additional resiliency for the NSX control plane.
The NSX Controllers already offer inherint resiliency for the control plane by design in several ways:
For the reasons mentioned above, it’s a rare event and unlikely that communication would be lost with the entire NSX Controller Cluster. In NSX-V 6.3, this control plane resiliency is enhanced even further via CDO mode.
CDO mode targets specific scenarios where control plane connectivity is lost, for example, a host losing control plane connectivity, losing control plane connectivity to the controller cluster, or NSX controllers are down. CDO mode enhances control plane Continue reading
NSX-V 6.2 introduced the Cross-NSX feature to allow for NSX logical networking and security across multiple vCenter domains. The ability to apply consistent networking and security across vCenter domains provides for mulitple use cases for Cross-VC NSX: workload mobility, resource pooling, multi-site security, ease of automation across sites, and disaster avoidance/recovery. With the recent release of NSX-V 6.3, several enhancements have been added to the Cross-VC NSX feature to provide for additional capabilities and overall robustness of the solution. In this blog post I’ll discuss the new Cross-VC NSX security enhancements in NSX-V 6.3. For additional information on Cross-VC NSX check-out my prior Cross-VC NSX blog posts.
The security enhancements for Cross-VC NSX can be grouped into two categories:
Active/Active and Active/Standby above refers to if the application is active at both sites or if it is active at one site and standby at another site (ex: disaster recovery). Enhancements for both of these respective categories are discussed in more detail below.
1.) General Enhancements (Apply Across both Active/Active and Active/Standby deployment models)

Figure 1: Cross-VC NSX Active/Standby and Continue reading
In this post, I’ll briefly expand on the benefits of utilizing NSX as part of a disaster recovery (DR) solution. For additional information check out my prior multi-site and disaster recovery with NSX posts on the VMware Network Virtualization blog. Additionally, I recently presented at 2016 US VMworld and Europe VMworld on multi-site and disaster recovery solutions and recorded sessions can be viewed here: US VMworld, Europe VMworld.
Prior NSX Multi-site and Disaster Recovery Posts:
With disaster recovery, two challenges in general are:
In a prior post, Multi-site with Cross-VC NSX: Consistent Security and Micro-segmentation Across Sites, we discussed how Cross-VC NSX provides micro-segmentation and consistent security across multiple sites. We looked at five reasons to seriously consider Cross-VC NSX for a multi-site solution in terms of security alone: centralized management, consistent security across vCenter domains/sites, security policies follow the workload(s), ease of security automation across vCenter domains/sites, and enhanced disaster recovery use case. In this post, we’ll discuss how advanced third party security services can also be leveraged in a Cross-VC NSX environment.
Prior Cross-VC NSX Blogs:
Multi-site with Cross-VC NSX: Consistent Security and Micro-segmentation Across Sites
Cross-VC NSX: Multi-site Deployments with Ease and Flexibility
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
NSX provides a solid platform for security in general: inherent isolation via logical networks, micro-segmentation via distributed firewall, edge firewall capabilities, third party guest introspection services, third party network introspection services, and a robust security policy orchestration and automation framework.
With Cross-VC NSX, micro-segmentation and consistent security policies for workloads expands beyond a single vCenter boundary. Typically, customers who have multiple sites also have multiple vCenters – at least one vCenter Continue reading
Several posts have been written prior on multi-site with Cross-VC NSX describing the fundamentals, use cases, deployment models, and flexibility Cross-VC NSX provides. In this post, we focus on the security benefits of a multi-site Cross-VC NSX solution.
Prior Cross-VC NSX Blogs:
Cross-VC NSX: Multi-site Deployments with Ease and Flexibility
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
So, why multi-site with Cross-VC NSX? The following five reasons should be enough for you to seriously consider Cross-VC NSX as a solution for your multi-site needs:
1.) Centralized Management
Centralized management of security policies across multiple vCenter domains/sites. You have one central location to configure security policies and only write the security policy once, which is then applied across all vCenter domains/sites.
2.) Consistent Security Across vCenter Domains/Sites
Consistent security policies across vCenter domains/sites provided automatically by Cross-VC NSX enables enhanced workload mobility. Security policies are configured on the primary NSX Manager and automatically synced to the secondary NSX Managers providing for uniform security across all sites.

Figure 2 Consistent Security Across Sites Continue reading
As discussed in prior Cross-VC NSX/multi-site blogs, Cross-VC NSX allows for NSX logical networking and security across multiple vCenter domains which may also be across multiple sites. The benefits of this capability are immediately clear in terms of workload mobility, resource pooling, central management and application of consistent security policies across vCenter domains/sites, and disaster recovery. More details on these use cases can be found in the prior Cross-VC NSX blogs listed below or in the recently published NSX-V: Multi-site Options and Cross-VC NSX Design Guide. This blog post, focuses on the ease and flexibility in terms of application of Cross-VC NSX for multi-site.
Prior Cross-VC NSX Blogs:
NSX-V: Multi-site Options and Cross-VC NSX Design Guide
Enhanced Disaster Recovery with Cross-VC NSX and SRM
Cross-VC NSX for Multi-site Solutions
In this example, vCenter, the primary NSX Manager, and the Universal Controller Cluster (UCC) is deployed at site 1. A secondary NSX Manager which is registered with the primary NSX Manager is deployed at site 2 along with its corresponding vCenter. For a quick overview on primary NSM Manager, secondary NSX Manager, and the UCC see this prior blog. For more detailed information, see the NSX-V: Multi-site Options and Cross-VC NSX Continue reading
Check-out the new NSX-V Multi-site Options and Cross-VC NSX Design Guide
The goal of this design guide is to outline several NSX solutions available for multi-site data center connectivity before digging deeper into the details of the Cross-VC NSX multi-site solution. Learn how Cross-VC NSX enables logical networking and security across multiple vCenter domains/sites and how it provides enhanced solutions for specific use cases. No longer is logical networking and security constrained to a single vCenter domain. Cross-VC NSX use cases, architecture, functionality, design, and failure/recovery scenarios are discussed in detail.
Cross-VC NSX: Logical Networking and Security Across vCenter Domains and Sites
Outlined briefly below are several important use cases that Cross-VC NSX enables in regards to Application Continuity. For additional details on Cross-VC NSX and multi-site data center solutions see the NSX-V Multi-site Options and Cross-VC NSX Design Guide.
Use Case 1: Workload Mobility
Since logical networking and security can span multiple vCenter domains and multiple sites, Cross-VC NSX allows for enhanced workload mobility which can not only span multiple sites but also multiple vCenter domains across Active-Active data centers. Workloads can now move between vCenter domains/sites on demand for tasks such as data center migration, data center Continue reading
Check-out the new Automation Leveraging NSX REST API Guide.
Authors: VMware NSX Technical Product Management Team
Thanks to all the contributors and reviewers of this document. A brief overview of the guide is provided below. Continue reading
In some prior blogs, we demonstrated leveraging NSX REST API with Python. See prior blogs, Automating Security Group and Policy Creation with NSX REST API and Automating VMware NSX Security Rules Creation using Splunk and Some Code. In this blog, we demonstrate how NSX REST API can be used with the popular Perl programming language.
One of Perl’s key strengths is the vast amount of Perl modules/libraries available via the Comprehensive Perl Archive Network (CPAN). There is also a CPAN module included with Perl which is used to automatically download and install additional Perl modules from the CPAN repository. The example Perl code in this post demonstrates a simple program that uses a Perl REST client module/library with NSX REST API to retrieve NSX SpoofGuard information. Continue reading
Check-out the new Disaster Recovery with NSX and SRM white paper that explains how Cross-VC NSX + VMware’s SRM offers an Enhanced Disaster Recovery (DR) solution and solves many of the challenges related to traditional DR solutions. This solution provides consistent logical networking and security across protected and recovery sites and faster recovery upon disaster scenarios. A summary and overview of the solution is provided below. Continue reading
As we’ve seen in many of the prior posts, VMware NSX is a powerful platform decoupling networking services from physical infrastructure. NSX effectively enables logical networking and security within a virtualized environment; this brings many of the same benefits we’re familiar with gaining from server virtualization such as flexibility, faster provisioning, better utilization of hardware, cost savings, decreased downtime, etc. One of the major benefits of the software approach that NSX brings is the ability to automate easily via REST API. In this post, we’ll take a look at a simple yet realistic use case focused around security where automation can help. Continue reading
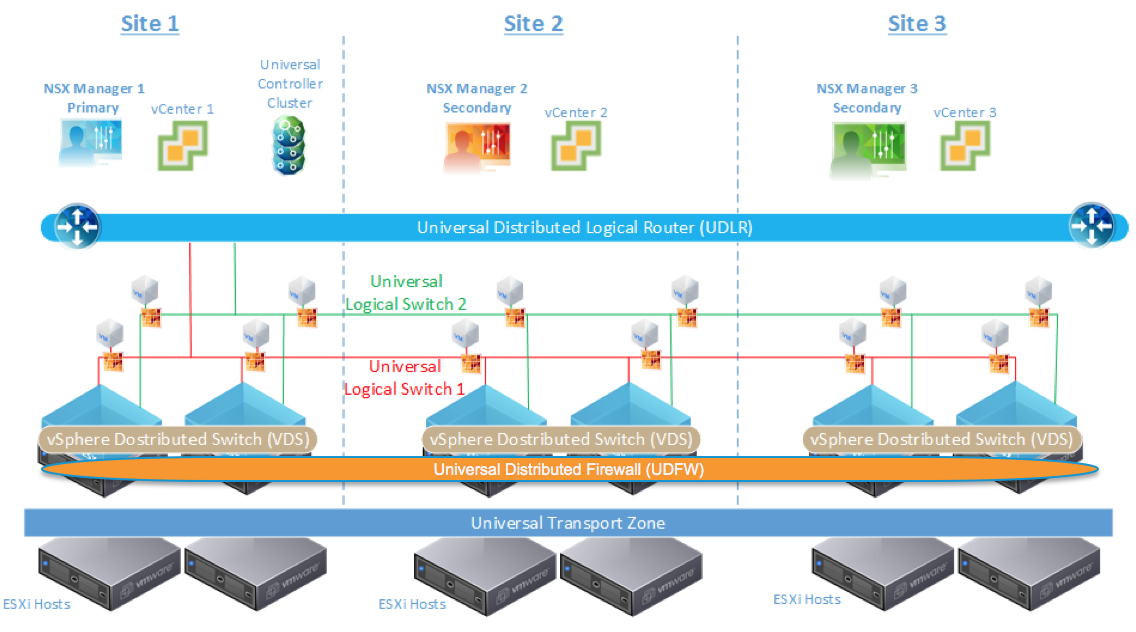
The Cross-VC NSX feature introduced in VMware NSX 6.2, allows for NSX logical networking and security support across multiple vCenters. Logical switches (LS), distributed logical routers (DLR) and distributed firewall (DFW) can now be deployed across multiple vCenter domains. These Cross-VC NSX objects are called Universal objects. The universal objects are similar to distributed logical switches, routers, and firewall except they have global or universal scope, meaning they can span multiple vCenter instances. With Cross-VC NSX functionality, in addition to the prior local-scope single vCenter objects, users can implement Universal Logical Switches (ULS), Universal Distributed Logical Routers (UDLR), and Universal DFW (UDFW) across a multi-vCenter environment that can be within a single data center site or across multiple data center sites. In this post we’ll take a look at how we do this. Continue reading
VMware NSX provides an integrated Distributed Firewall (DFW), which offers L2-L4 security at the vNIC level and protects East-West traffic, and an Edge Firewall provided by the Edge Services Gateway (ESG), which offers L2-L4 security at the edge and protects North-South traffic in and out of the Software Defined Data Center (SDDC).
The DFW is a kernel-level module and allows for enhanced segmentation and security across a virtualized environment. DFW enables a distributed security architecture allowing for micro-segmentation.
In addition to the DFW and ESG Firewall, there are many third party integrations with well-known security partners such as Check Point and Palo Alto Networks. In this blog, we’ll focus on the Check Point vSEC solution for NSX. For a complete list of security partner solutions and more information, see the supported NSX third party security products on the VMware NSX Technical Partners Webpage.
For this blog, the following VMware and Check Point components and corresponding versions are used:
The VMware NSX network virtualization platform allows us to build sophisticated networking and security constructs in software. NSX has a rich RESTful API which allows one to build highly flexible and automated environments. In this blog, we’re going to focus on operations and automation; we’ll demonstrate one example of automation around security policies/rules that can be done with NSX.
VMware NSX allows for micro-segmentation with a distributed firewall service (DFW). The DFW is a kernel-level module and allows for enhanced segmentation and security across a virtualized environment. One of the common questions we get asked is, “how do I decide what rules to build?” NSX allows for multiple options to create rules such as the use of NSX flow-monitoring or analyzing traffic patterns via logging to create the rules.
We’ll demonstrate how the VMware NSX DFW can be monitored with the popular Splunk platform. Further, we’ll demonstrate, along with using Splunk for monitoring traffic passing through the DFW, how the NSX REST API can be leveraged to automate workflows and creation of DFW rules. Continue reading