Author Archives: Ivan Pepelnjak
Author Archives: Ivan Pepelnjak
TL&DR: FRRouting advertises the IP prefix on the lo loopback interface with zero cost.
Let’s start with the background story. When we added FRRouting containers support to netlab, someone decided to use lo0 as the loopback interface name. That device doesn’t exist in a typical Linux container, but it’s not hard to add it:
$ ip link add lo0 type dummy
$ ip link set dev lo0 up
One of my friends is running a large IPv6 network and has already experienced a shortage of IPv6 neighbor cache on some of his switches. Digging deeper into the root causes, he discovered:
In my larger environments, I see significant neighbor table cache entries, especially on network segments with hosts that make many long-term connections. These hosts have 10 to 20 addresses that maintain state over days or weeks to accomplish their processes.
What’s going on? A perfect storm of numerous unrelated annoyances:
One of my friends is running a large IPv6 network and has already experienced a shortage of IPv6 neighbor cache on some of his switches. Digging deeper into the root causes, he discovered:
In my larger environments, I see significant neighbor table cache entries, especially on network segments with hosts that make many long-term connections. These hosts have 10 to 20 addresses that maintain state over days or weeks to accomplish their processes.
What’s going on? A perfect storm of numerous unrelated annoyances:
Lasse Haugen had enough of the never-ending “we can’t possibly deploy IPv6” excuses and decided to start the IPv6 Shame-as-a-Service website, documenting top websites that still don’t offer IPv6 connectivity.
His list includes well-known entries like twitter.com, azure.com, and github.com plus a few unexpected ones. I find cloudflare.net not having an AAAA DNS record truly hilarious. Someone within the company that flawlessly provided my website with IPv6 connectivity for years obviously still has some reservations about their own dogfood ;)
Lasse Haugen had enough of the never-ending “we can’t possibly deploy IPv6” excuses and decided to start the IPv6 Shame-as-a-Service website, documenting top websites that still don’t offer IPv6 connectivity.
His list includes well-known entries like twitter.com, azure.com, and github.com plus a few unexpected ones. I find cloudflare.net not having an AAAA DNS record truly hilarious. Someone within the company that flawlessly provided my website with IPv6 connectivity for years obviously still has some reservations about their own dogfood ;)

All the Kubernetes Ingress videos from the Kubernetes Networking Deep Dive webinar with Stuart Charlton are now public. Enjoy!
I decided not to get involved in the EVPN-versus-LISP debates anymore; I’d written everything I had to say about LISP. However, I still get annoyed when experienced networking engineers fall for marketing gimmicks disguised as technical arguments. Here’s a recent one:
I decided not to get involved in the EVPN-versus-LISP debates anymore; I’d written everything I had to say about LISP. However, I still get annoyed when experienced networking engineers fall for marketing gimmicks disguised as technical arguments. Here’s a recent one:

Dmitry Perets wrote an excellent description of how typical firewall cluster solutions implement control-plane high availability, in particular, the routing protocol Graceful Restart feature (slightly edited):
Most of the HA clustering solutions for stateful firewalls that I know implement a single-brain model, where the entire cluster is seen by the outside network as a single node. The node that is currently primary runs the control plane (hence, I call it single-brain). Sessions and the forwarding plane are synchronized between the nodes.
Dmitry Perets wrote an excellent description of how typical firewall cluster solutions implement control-plane high availability, in particular, the routing protocol Graceful Restart feature (slightly edited):
Most of the HA clustering solutions for stateful firewalls that I know implement a single-brain model, where the entire cluster is seen by the outside network as a single node. The node that is currently primary runs the control plane (hence, I call it single-brain). Sessions and the forwarding plane are synchronized between the nodes.
A long-time friend sent me this question:
I would like your advice or a reference to a security framework I must consider when building a green field backbone in SR/MPLS.
Before going into the details, keep in mind that the core SR/MPLS functionality is not much different than the traditional MPLS:
A long-time friend sent me this question:
I would like your advice or a reference to a security framework I must consider when building a green field backbone in SR/MPLS.
Before going into the details, keep in mind that the core SR/MPLS functionality is not much different than the traditional MPLS:
netlab release 1.8.1 added a interesting few features, including:
This time, most of the work was done behind the scenes1.
netlab release 1.8.1 added a interesting few features, including:
This time, most of the work was done behind the scenes1.
Another cybersecurity rant worth reading: cybersecurity is broken due to lack of consequences.
Bonus point: pointer to RFC 602 written in December 1973.
Another cybersecurity rant worth reading: cybersecurity is broken due to lack of consequences.
Bonus point: pointer to RFC 602 written in December 1973.
Dan left an interesting comment on one of my previous blog posts:
It strikes me that the entire industry lost out when we didn’t do SPB or TRILL. Specifically, I like how Avaya did SPB.
Oh, we did TRILL. Three vendors did it in different proprietary ways, but I’m digressing.
Dan left an interesting comment on one of my previous blog posts:
It strikes me that the entire industry lost out when we didn’t do SPB or TRILL. Specifically, I like how Avaya did SPB.
Oh, we did TRILL. Three vendors did it in different proprietary ways, but I’m digressing.
Here’s another challenge for BGP aficionados: build an MPLS-based transit network without BGP running on core routers.
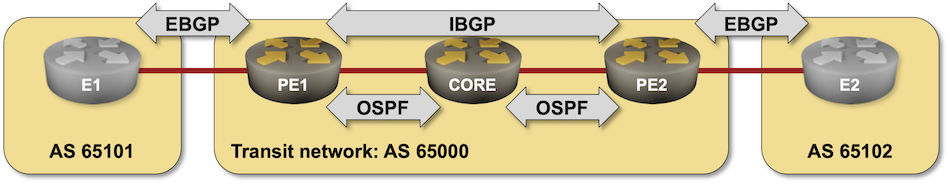
That should be an easy task if you configured MPLS in the past, so try to spice it up a bit:
Here’s another challenge for BGP aficionados: build an MPLS-based transit network without BGP running on core routers.

That should be an easy task if you configured MPLS in the past, so try to spice it up a bit: