Author Archives: John Herbert
Author Archives: John Herbert
It’s one thing to learn the syntax for a programming language, but it’s another to have the ability to think through a problem and break it down into a logical set of tasks which the code can execute.
On the Solarwinds Thwack Geek Speak blog I worked through a real world automation process to see what the steps might be, and how it can sometimes be possible, and even advantageous, to reuse code or hand off a task to another tool. Please do take a trip to Thwack and check out my post, “New Coder: Real World Code Development“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at New Coder: Real World Code Development and give me a share/like. Thank you!
Having decided it’s time to learn how to code, and having chosen the right language to use, the next step is to find some resources and start programming that masterpiece. But what’s the best way to learn that language?
On the Solarwinds Thwack Geek Speak blog I spoke about how I started learning to code, and look at some of the different resources out there to kickstart your programming mastery. Please do take a trip to Thwack and check out my post, “New Coder: Getting Started and Finding Your Path“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at New Coder: Getting Started and Finding Your Path and give me a share/like. Thank you!
There are so many programming languages to choose from; as a new network or infrastructure coder, what are the best options to consider, and why? What are the differences between all these languages anyway?
On the Solarwinds Thwack Geek Speak blog I explain what interpreted and compiled languages are, what strong and weak typing means, I evaluate some common languages and make some recomendations. Please do take a trip to Thwack and check out my post, “New Coder: Which Language Is The Right One?“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at New Coder: Which language is the right one? and give me a share/like. Thank you!
How should somebody new to coding get started learning a language, writing code, and maybe even automating something? Where should they begin?
That’s the question I asked on the Solarwinds Thwack Geek Speak blog. In my post I look at what programming really is, and whether it’s going to be something that comes naturally, or will require a very conscious effort. Please do take a trip to Thwack and check out my post, “So you want to code? It’s only logical!“.
Please see my Disclosures page for more information about my role as a Solarwinds Ambassador.
If you liked this post, please do click through to the source at So You Want To Code? It’s Only Logical! (Thwack) and give me a share/like. Thank you!
It’s the bake off you’ve been waiting for; a five-month real life test of a Ubiquiti ERPro-8 (EdgeRouter Pro) and a tub of Play-Doh™! Over a period of five months I carefully evaluated these two very useful items and discovered their good and bad points. But after five months, which will I choose as the ultimate winner?
The first item to be evaluated is the tub of Play-Doh™. I didn’t skimp on quality, and bought genuine Play-Doh™ as part of a set which included tubs of both light blue and red. Accessories in the box included a roller, a plastic cutting knife, four shaped cutters and an extruder with four built-in shapes as well as four interchangeable extrusion heads.
The entire kit Continue reading
While at Dell EMC World 2017 I had a very interesting chat with Jason Shepherd, Dell EMC’s Director of IoT Strategy & Partnerships. To be clear, I’m not an expert on the Internet of Things (IOT), and our discussion was a useful reminder how much difference perspective makes when evaluating a technology.

When I think about IOT the first thing that comes to mind — naturally enough — are the items most applicable to me, like a smart thermostat, smart door locks, smart light bulbs, and so forth. I work in an enterprise, so I also think about building management in the enterprise, to include things like smart lighting, HVAC, presence sensors, temperature monitoring and more. Both of these environments are ripe for IOT functionality, and are the ones that most of us are likely to encounter on a daily basis.
However, it’s probably obvious that there are many more use cases for IOT devices, including for example:
I saw an advertisement for Pockethernet a few months ago and it looked pretty impressive; €167.23 (~$179 based on xe.com‘s published exchange rates at the time of writing) for a 200 gram rechargeable device offering 10/100/1000 Ethernet and cable testing features such as:
Over all, Pockethernet sounded like something I needed to look into more closely.

Pockethernet started off with the assistance of a crowdfunding campaign on Indiegogo, raising $185,000 of their $50,000 target. Unusually for an electronic device, Pockethernet is manufactured in Hungary, which was nice to see. Unboxing the Pockethernet I was surprised (but pleased) to discover that the device is packaged in a soft, zipped carry case.

The box also contains a small User Guide, and inside the case is the Pockethernet tester, an adaptor, a short Ethernet cable and a short USB charging cable. There’s also a strip of blue velcro which will be useful to hold the tester in place if needed.

As it turns out, keeping the Pockethernet Continue reading
I’m at the Dell EMC World 2017 conference in Las Vegas this week, and I’ve been enjoying catching up on what the network group has been up to. In my previous experience, the legacy Dell Networking products have unfortunately been seen as those things that get thrown in when you buy a rack of servers
. In other words, they lacked credibility or worse, the rack would come with another vendor’s switches in them, reinforcing the idea that Dell’s own products weren’t up to the job.

It’s my belief though, that two things in recent years have dramatically changed that perspective. The first is Dell EMC’s OS10, a modular network operating system which by all accounts is actually pretty capable. Previous OS incarnations were of varying quality, as has been the case with many vendor-branded switches, and with the release of OS10, Dell Networks (as it was at the time) put a stake in the ground and showed that they wanted things to be different.
The second element is disaggregation. Dell identified the opportunity to use what was becoming ubiquitous merchant silicon like the Broadcom Trident II chipset to be able to play at the exact same level as everybody Continue reading
In my response to The Network Collective’s group therapy session where the participants ‘fessed up to engineering sins, I promised to share my own personal nightmare story, as seen on Reuters. Grab a bag of popcorn, a mug of hot chocolate and your best ghost story flashlight
, and I will share a tale which will haunt you for years to come. If you have small children in the room, this may be a good time to send them outside to play.

At one point in my career I was a network engineer for a national mobile provider in the USA. The mobility market is a high-stakes environment, perhaps more so than most industry outsiders might expect. Users have surprisingly high expectations and are increasingly reliant on the availability of the network at all times of day or night.
Mobile networks are typically not just for consumers but are also used by a large number of private entities including fleet management companies, fire/burglar alarm systems, shipping companies and emergency services, so even a minor outage can potentially be a problem. These commercial organizations all had customized private connectivity to the mobile provider and thankfully we had a contractually-identified Continue reading
The end of March brought with it the first episode of a neat new project called The Network Collective, a video roundtable for networking engineers. The hosts and co-founders of this escapade are Jordan Martin (@BCJordo), Eyvonne Sharp (@SharpNetwork) and Phil Gervasi (@Network_Phil).
Episode 1 brought three guests to the virtual table: Carl Fugate, Mike Zsiga and Jody Lemoine, the latter of whom (top right on the YouTube video) is actually blurry in real life, and this is not a video artifact. The topic for discussion was the Top 10 Ways To Break Your Network.
Thankfully, the show didn’t actually provide tips on how to break your network — as if we need any help doing that — but instead looked at the shameful ways in which each participant had managed to cause network destruction in the past, and what lessons could be learned.
The fact that five of six experienced professionals are willing to own up to their blunders (one brought a colleague’s mistake to put up on the chopping block) actually signals one of the most important lessons that the episode highlighted, which is Continue reading
Over the last few months, I’ve noticed that some pages on this site have been returning what appear to be corrupted pages, looking something like this:

Or like this:
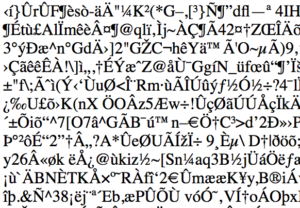
Pretty, aren’t they? Typically if the user hits refresh the page will come back as it should have done first time. I’ve been working for many weeks now to track down why this was happening. One thing I noted is that the corrupted files were smaller than the non-corrupted equivalent, suggesting that the file was either truncated or, more likely, compressed. Opening a downloaded file in a text editor showed that the header of these corrupted pages begins like this:

Some of you are probably feeling smug right now because you know that the first three bytes of a gzip file are 1F 8B 08. The ASCII code for 0x1F is Ctrl-_; there’s no code for 0x8B; ASCII 0x08 is the same as Ctrl-H (i.e. backspace). This should look familiar in the image above: ^_ <8B> ^H. In other words, the client is receiving a GZIPped version of the page but presumably was told that the mime type was text/html. The end result is the garbled mess we saw above. So now Continue reading
In my final post on Cisco’s Data Center Network Manager (DCNM), I’m taking a look at the deployment capabilities and templating features which allow configuration to be deployed automatically to multiple devices. In its simplest case, this might be used to set a new local username / password on all devices in the fabric, but in theory it can be used for much more.
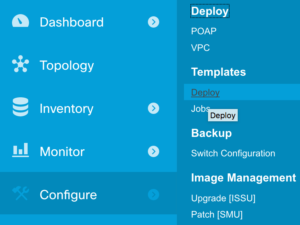
Let’s get one thing straight right out of the gate: this ain’t no Jinja2 templating system. While DCNM’s templates support the use of variables and some basic loop and conditional structures, the syntax is fairly limited and the only real-time interaction with the device during the execution of the template amounts to a variable containing the output of the last command issued. There are also very few system variables provided to tell you what’s going on. For example I couldn’t find a variable containing the name of the current device; I had to issue a hostname command and evaluate the response in order to confirm which device I was connecting to. That said, with a little creativity and a lot of patience, it’s possible to develop scripts which do useful things to the fabric.
Continuing my look at Cisco’s Data Center Network Manager (DCNM) software, I had to swap out a faulty spine switch recently, and got a chance to find out whether I could use DCNM to make the RMA process a little less painful than it would normally be.

If I had a dream, albeit a rather sad one, it would be to be able to swap out a hardware component in my network quickly and efficiently, and not have to mess around.
DCNM has all the elements to make this feasible. Given a device serial number, I’ve already confirmed that DCNM can automatically deploy the correct firmware version and base configuration when deploying a new fabric, so there’s no reason it couldn’t be used to do the same thing for a replacement switch, but this time deploying the complete, production configuration in one step. Happily I already have the configuration for the spine switch I’m replacing, because DCNM takes frequent backups. I also have the appropriate firmware loaded to DCNM’s software repository because I used it to build the fabric in the first place. So how do I approach the RMA?
Once the replacement switch was received Continue reading
If you’ve recovered from the shock of hearing me say something positive about Cisco’s Data Center Network Manager (DCNM) product, then you’ll want to hold on tightly to your underbritches as I tell you that I just used DCNM ISSU to perform disruptive software upgrades on eight of the switches in my ethernet fabric, and–spoiler alert–it was actually a fairly pleasant experience!

DCNM offers management of ISSU (In-Service Software Upgrade). ISSU usually implies some kind of hitless (to the revenue ports) upgrade, historically made possible on the Nexus 7000, for example, by having dual supervisor modules and using Non-Stop Forwarding (NSF) to keep the forwarding plane intact while the supervisors failover. With the single-CPU layer-2 Nexus 5600 switches, however, the data plane can be told to continue forwarding frames while the control plane reboots with new code, allowing for an upgrade to take place without interruption.
Unfortunately it’s not always possible to perform a non-disruptive upgrade. The code version I was installing included a fix to the linecard BIOS, so the linecards had to be reloaded as well as the main CPU. In other words, the switch has to be rebooted after the upgrade, and there’s Continue reading
It’s always a good idea to calculate an MD5 or SHA1 file checksum to validate file integrity after download or transfer, especially when dealing with firmware binaries. While most modern systems are smart enough to validate images before attempting an installation, not all are so wise, and I’m sure I’m not the only one to have seen a device bricked (or stuck in ROMMON or a similar bootloader or equivalent) after a bad image was uploaded.

Here’s a quick reference guide to creating file checksums on Macos (OSX), Windows and Linux.
There are various ways to check md5/sha1 checksums depending on your preferred platform. Vendors tend to publish the MD5 or SHA1 checksums (or both) for downloadable files, so it’s silly not to do checksum validation and confirm that the file has downloaded completely and uncorrupted. I try to validate after each time I transfer a file so that I don’t waste time sending a corrupted file on to the next hop. For example:
Recently I had a chance to try using Cisco’s Data Center Network Manager (DCNM) software in anger. I must confess that sometimes anger
was the right word, but at other times it definitely made me smile. Based on the state of the documentation it’s clear that there are a couple of areas where very few people have spent time digging in (if they had, the same errors wouldn’t be in the documentation for at least 5 releases of DCNM), so on that basis I’m using this post—and more to follow—to document some of the fun things I have discovered along the way. For reference, I am running DCNM version 10, so there have been nine previous versions of DCNM in which the behavior can be perfected, and I gather that version 10 is a big step up from version 9.
To put my testing in context, I have a specific FabricPath Leaf-Spine topology already designed, and I am only using the aspects of DCNM pertinent to my particular needs for an Ethernet LAN fabric. I say this up front because I know that I am not using all of DCNM’s functionality, and perhaps I’m missing out on some of the fabric automation Continue reading
It’s Thursday, so I think I’ll just leave this here:
... Info: 0/1/CPU0 (LC) (SDR: Owner) Proceed with this install operation (y/n)? [y] RP/0/RSP0/CPU0:Dec 16 08:29:48.835 : instdir[255]: %INSTALL-INSTMGR-4-INSTALL_OPERATION_WARNING : A warning occurred during install operation 19. See 'show install log 19 detail' for more information. Info: Install Method: Parallel Reload The install operation will continue asynchronously. RP/0/RSP0/CPU0:us-atl01-z1rt01(admin)# RP/0/RSP0/CPU0:us-atl01-z1rt01(admin)# RP/0/RSP0/CPU0:us-atl01-z1rt01(admin)#show install log 19 detail Fri Dec 16 08:30:10.472 UTC No log information available

Well, it made me smile, anyway.
If you liked this post, please do click through to the source at When Installs Go Bad… and give me a share/like. Thank you!
Over the last five years, there has been increasing noise about whether the growing automation and orchestration of networks (and infrastructure in general) will lead to our jobs being eliminated. Concerns about mass layoffs are understandable given what happened when large scale automation was introduced to manufacturing.
What is left after automation has taken its toll on an industry? Presumably there is work for those who create and maintain the automation systems and there will be a need for workers to do the tasks which cannot be adequately automated, but the people who don’t fit into these categories might be facing a tough future. Some workers will retrain or adapt their skills to shift themselves into one of the “needed” categories, but since the idea of automation in most industries is to reduce the need for salaried humans be more agile and respond faster to customer needs, the competition for those positions is likely to be strong.
Up front let me say that I believe that the predictions of imminent doom are utter codswallop. In order for the jobocalypse to occur, automation has to be present across the every industry because IT infrastructure exists pretty much everywhere as a business enabler, but only in subset of industries (e.g. Continue reading
While I’m giving out good wishes, I’d like to also give a shout out and a thank you to Mark Silver at SpecTechUlar for including me on his list of “6 Blogs All Product and IT Specialists Should Add to Their 2017 Reading List.”
6 Blogs All Product and IT Specialists Should Add to Their 2017 Reading List
I fear that Mark has discovered my secret as he points out that “[my] eccentric personality definitely shows through in this technology blog.” I quite like that 
Thank you, Mark, for the kind words and the inclusion on your list! Mark works as a Product Manager for WalkMe, and runs the SpecTechUlar blog, pulling together interesting stories and best practices about technology and product management written by himself and other guest authors. He has found some amazing images for his blog posts, and even a glance at the home page pulls you in to the articles (I should learn from this!).
Thanks, Mark; I enjoyed discovering SpecTechUlar too, and I think many of my readers may also enjoy visiting.
If you liked this post, please do click through to the source at MP on SpecTechUlar’s “6 Blogs for 2017” List and give me a share/like. Thank you!
This is a quick post to say thanks to the folks at Vertitech IT for listing movingpackets.net among their Best IT Blogs for 2017 (“Must-Read Resources for CIOs, IT & Security Pros”).
In their own words:
VertitechIT’s top 50 IT blogs were selected because they are among the most current, frequently updated, credible, and informative sources of information related to IT on the web today. From musings of industry leaders, to the veteran guys and gals in the trenches who chronicle their IT journeys, these 50 blogs all have something important to say about the IT world of today, and tomorrow.
Vertitech’s list is definitely worth a browse; I’m very flattered to be listed in such amazing company. I was also delighted to see that NetworkingNerd, Jeremy Stretch and Chris Wahl were featured as well; are all blogs I follow from people I respect.
Some other highlights include Cisco, Gigaom, the Forrester Blog for CIOs, Solarwinds’ Geek Speak (for whom – along with other contributors – I have written a number of blog posts), SC Magazine and TechCrunch Enterprise.
I’m delighted to even be on the same page as these other outlets. Go check the list out and perhaps you’ll also find some great Continue reading