Author Archives: John Herbert
Author Archives: John Herbert

This week’s comedy gold was listening to a conversation emanating from a nearby inhabitant of our corporate cube accomodations, where one of my colleagues, Bob, was explaining to another coworker, George, the reasoning behind the decision to deploy firewalls to a particular new location.
Roughly summarized, the argument was this:
George, deploying a firewall is like having sex.
(No; I confess I had not anticipated ever typing that particular sentence, and I hope I never have to type it again.)
When you want to have sex, you decide whether you want a baby, and thus you choose whether or not to use contraception. If you don’t use contraception, while there’s no guarantee that a baby will arrive, there’s a real good chance that it will, so don’t be surprised if it does. Contraception isn’t perfect, but it at least reduces the likelihood of having a baby.
I confess I was laughing hard as I listened to the explanation because it’s an inspired analogy. However, buried somewhere in my subconscious was an Australian voice saying something like All these security products are a waste of money. It’s cheaper to save the money you would have spent, deal with a breach Continue reading

California Nurds
I know a place
Where the tech is truly awesome
Smart network folks; all clustered
inside CA’s borders
Cablin’ guys and gals
Running fibers to the servers.
We’re all hard core geeks, we are
certified nerf herders.
You may think you are sad,
But nothing comes close
To the silicon coast
Santa Clara’s just mad, you can’t
help your nerd lust
Oooooh Oh Oooooh
California nurds;
we are incredible!
Armed with Flukes,
we’re testing non stop.
Wi Fi smarts
so hot
we’ll melt your antenna
Oooooh Oh Oooooh
California nurds,
we like telemetry;
But we don’t
like SNMP.
West Coast time is lame
so we use UTC
Oooooh Oh Oooooh
We love unicorns, shooting
rainbows from their rear ends.
We’re Software Defined, running
everything in Python.
–John Herbert, with sincere apologies to Katy Perry
If you liked this post, please do click through to the source at California Nurds by Katy Sperry and give me a share/like. Thank you!

Last month, the announcement was made that after seven years, Netflix completed its move to the cloud. While offering my sincere congratulations to Netflix, it begs the question what chance smaller companies have of moving successfully to the cloud.
I love it when a plan comes together; it’s great seeing multiple threads in different places intersecting, and the news from Netflix pulled together a few things from the last 12 months in a rather interesting way.
I first heard about the Netflix announcement by listening to the Packet Pushers Network Break
episode 74. I don’t have enough time to keep up with all the industry news direct from all the sources out there, so I try to listen to podcasts on my drive into work. Network Break is one of my favorites, with Drew Conry-Murray and guests rounding up the week’s news and sharing their opinions.
The Netflix announcement explained that the company migrated from a monolithic app to hundreds of micro-services.
Rewinding the clock to ONUG Spring 2015, I listened to a presentation from Battery Ventures’ Adrian Cockroft, in which he espoused the benefits of containerized micro-services. The idea is that if Continue reading

There’s no avoiding the fact that the much-hyped Internet of Things
(IoT) is coming. Devices are popping up all over the place offering some form of wireless connectivity so that they can control (or be controlled) remotely, and if you want to run a Smart Building
, having control over all the elements of the environment could be a huge benefit. To that end, Cisco is playing with the idea that maybe we can offer power (via PoE), networking (Ethernet) and maybe even save a little money, by using Cat6 Ethernet cabling to connect those devices.
Not everything needs to be hard-wired, for sure. Some devices can be battery powered and may need to be placed in places where any wiring would be undesirable or impossible. Other devices though, may require more than battery power to operate, and that means running power to their location. If the device needs to send or receive a reasonable amount of data, it may also need to run 802.11 wireless, or have a wired connection; the common 802.15.4 Low-Rate Wireless Personal Area Network (LR-WPAN) solution utilized by many connected
devices may not provide enough bandwidth to be usable, and in Continue reading
The Naming of Hosts
The Naming of Hosts is a difficult matter,
It isn’t just one of your holiday games;
You may think at first I’m as mad as a hatter
When I tell you, a host must have THREE DIFFERENT NAMES.
First of all, there’s the CNAME you want to use daily,
Such as nms, intranet, HR or games–
Such as payroll, or passwordchange, IT or training,
All of them sensible everyday names.
There are fancier names if you think they sound better,
Vendors and products that all sound the same,
Such as PeopleSoft, OpenView, Cisco, or NetApp–
But all of them sensible everyday names.
But I tell you, a host needs a name that’s unusual,
A name that’s peculiar, and more dignified,
Else how can it justify license renewals,
Or memory upgrades, or hybrid flash drives?
For names of this kind, I can give you a standard,
Twelve bytes for location, and fifteen for app,
These names are the ones that are never remembered,
They’re cryptic, unreadable, frustrating crap.
But above and beyond there’s still one name left over,
And that is the name that you never will guess;
The name that no human research can discover–
But Continue reading
You will have to be a programmer if you’re going to be a network engineer in the future,
they say. I don’t agree, but it surely helps you do your job. But what language should you learn? Perl? (no) Python? (maybe) Ruby? (perhaps) Every time I say something about learning Python, a little voice on Twitter says Or Go!
. Go? Go. And so, sucker that I am, I gave it a go (pun intended). TLDR: I think you should, too.
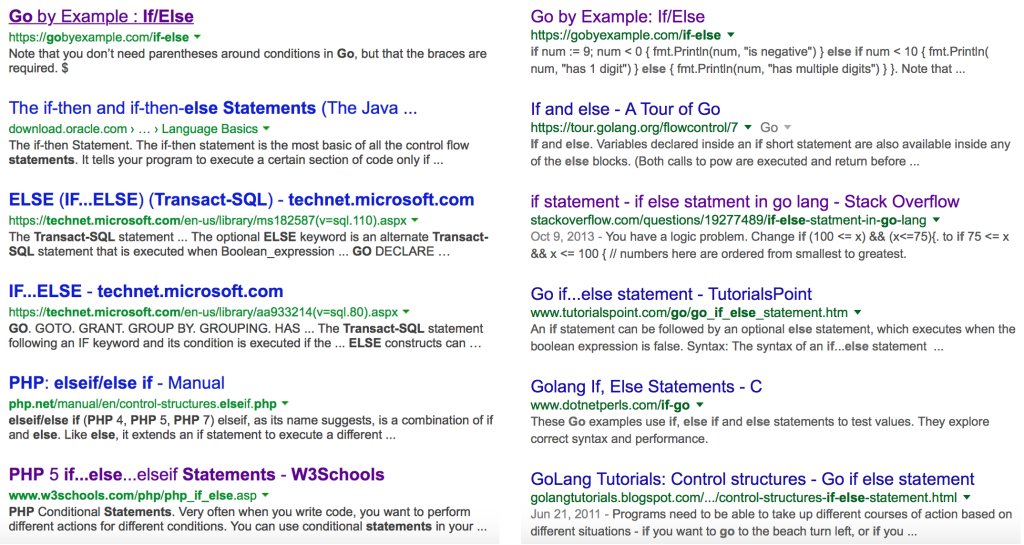
The name Go feels like it should be a terrible word to search for on the Internet because it’s so short, but searches actually work remarkably well if you use Google Search. Compare the results of a search for “go if then else” from Bing and Google below; I’ll let you guess which is which:
Maybe Google has learned from my search history. So, what’s important to know? Go is:
We had some great vendor presentations at Networking Field Day 11 and in the face of some pretty stiff competition, Citrix won my inaugural Best surprise
award, which I have just invented.
It’s not that the Citrix NetScaler Application Delivery Controller (ADC) is a particularly unique product; after all, I could as easily implement load balancing with the open source HAProxy, and there are impressive ADC hardware vendors in the commercial space, including the ubiquitously expensive F5 Networks and disruptive challenger A10 Networks. What grabbed my interest me however were the performance statistics of the NetScaler appliances, and specifically the process through which the performance was achieved by the Citrix engineering team.
If I might side track for a moment, at Networking Field Day 10, Intel discussed their DPDK (Data Plane Development Kit) designed to optimize soft-switched packet performance on their CPUs. Intel had noted that the performance of Open vSwitch (OVS) was nowhere near the native ability of the CPU, and consequently they invested time analyzing in scary detail exactly how packets flowed in order to find out where the bottlenecks were, and to see whether those could be eliminated or optimized in Continue reading

Today you get to play the SDN Definition Game: match the definition of Software Defined Neworking with the person who said it at the Networking Field Day 11 Delegate Roundtable. I’d make this exercise “drag and drop” but that sounds a bit complicated, so instead you’re on your honor not to cheat. Click on the image to see the answers in a new window.
I should note that the quotes I used were taken from conversation, so if I mis-transcribed anything or used it too far out of context I apologize to the speaker concerned. In actual fact though, who said what in this case doesn’t really matter. I shared the quotes to demonstrate that even when defined by a group of smart people like these, there doesn’t seem to be one definition of SDN that everybody can agree on. That has opened the door for marketing departments everywhere to use the SDN tag on anything and everything (aka “SDN Washing”) in the hopes that it sounds impressive and thus presumably increases sales. As a result, many people – both vendors and customers – believe that SDN is becoming a four letter word.

Ok, so Silver Peak offers yet another SD-WAN solution, you say? Well yes, but is it really possible to have too many options when it comes to broadband and hybrid WANs? I say no; the more choice we have, the more likely we can find the right solution for each situation and the more each vendor is encouraged to feature match with the others. With that in mind, let’s take a look at what Silver Peak offers and perhaps see how it is differentiated from the other solutions on the market.
Last year I wrote a brief definition of SD WAN as I see it, and for convenience I will reproduce that here as a reference point:
SD WAN is a solution that uses real time WAN link performance monitoring and data packet inspection to autonomously manage the distribution of network traffic across multiple, likely heterogenous, WAN links with the aim of improving and optimizing WAN performance in alignment with the business requirements.
My definition is intentionally vague about how such lofty goals should be accomplished, and that’s inevitably where the special sauce of each solution comes in.
Silver Peak sees two Continue reading

Isn’t SNMP just great? I love monitoring my network using an unreliable transport mechanism and an impenetrable and inconsistent data structure. Configuring my devices using automation is equally fun, where NETCONF has been subverted into something so ridiculously vendor-specific (and again, inconsistent), that each new device type (even from a single vendor) can mean starting again from scratch. Is there any hope for change? OpenConfig says yes.
Love it or hate it (hate it), SNMP remains the de facto standard for alerting and monitoring. I think we cling on to SNMP as an industry because we’re scared that any replacement will end up being just as clunky, and we’d simple be putting expensive lipstick on a particularly ugly pig. If we want to get rid of SNMP, whatever comes next will need to bring significant benefits.
If you’re dedicated to making changes manually, it’s likely you don’t care much about the mechanisms currently available to automate configuration changes. However, I can assure you that writing scripts to make changes to network device configurations is a frustrating activity, especially in a multi-vendor environment. I should add that I consider automating CLI commands and screen-scraping the Continue reading

“The future of the WAN is NOT . . . a router.”
These bold words were spoken by Riverbed’s Josh Dobies in a presentation to the delegates at Networking Field Day 10 this August, as a lead in to the first public announcement of “Project Tiger.”
Riverbed explained that the SteelHead appliances perform WAN optimization in sites with highly contended bandwidth. The SteelFusion appliances offer both “hyperconverged infrastructure” and WAN optimization. For sites that have plenty of bandwidth, however, there’s no Riverbed product you can put there and that–for Riverbed at least–is a problem. Riverbed’s proposed solution? Ironically, it’s an appliance that can act as a WAN router, but with some rather unusual features.
The headline features of Project Tiger as I see it, are:
Surprisingly absent from that list, however, is WAN Optimization. Despite being Riverbed’s core competency, this is not a feature of the Project Tiger appliance. Because Continue reading

Riverbed’s entry –or perhaps “expansion”– into the SD WAN market is interesting to me primarily because the approach being taken is a little different from the other solutions I have seen so far.
The solutions I’ve seen from vendors like Viptela, Silver Peak, Cisco, CloudGenix and VeloCloud mainly focus on providing reliable and optimized transport from spoke site to hub site, and in some cases also from spoke to spoke, and in fewer still, spoke to Internet. The underlying approach is to monitor various statistics for each of the available WAN links, and intelligently route data flows over the link that will best meet the application’s needs. Some solutions add error correction and/or packet duplication techniques to overcome packet corruption and loss as well. Let’s call this Link Selection, noting that both links are used so it’s not a “one or the other” kind of thing.
Riverbed has come at this problem from the angle they know best, WAN optimization. The presentation Riverbed gave at Networking Field Day 10 was not about how to choose which link to use, but more about how to effectively manage a hybrid WAN (say, MPLS for corporate access in Continue reading

I mentioned a few months ago that I had been asked to write some thought-provoking blogs on the subject of network management for the Solarwinds Thwack Community “Geek Speak” area. I’ve now finished my six posts, and while they won’t be reproduced on movingpackets.net, I’m linking to them here as I think they touch on some subjects close to my Software Defined Heart.
Click da pic to read the article.
I hope you find something to think about or react to there. I’ve tried to blend some hyperbole with a tablespoon of annoyance and a light dash of technical reality. If you have any specific comments on any of these posts, the right thing to do would be to login to Thwack and comment there, but I’ll take any feedback you want to give, wherever it is.
Disclosures
I am participating in the Solarwinds Thwack Ambassador program on a paid basis for July-September 2015. My posts Continue reading

When I made a stab at defining SD WAN recently, I noted that Cisco’s IWAN solution had provided a bit of a contrast to some of the other Software Defined WAN solutions I’d seen; not in a bad way, but I was certainly interested in the approach.
I’m going to “do a Joe Onisick” here and quote myself as a reference for what I might be hoping for from the Cisco IWAN solution:
“SD WAN is a solution that uses real time WAN link performance monitoring and data packet inspection to autonomously manage the distribution of network traffic across multiple, likely heterogenous, WAN links with the aim of improving and optimizing WAN performance in alignment with the business requirements.” – John Herbert
One thing my definition doesn’t mention is how these systems get deployed, and since that’s interesting, perhaps let’s start there.
It seems to me that ZTD has become a checkbox requirement for all the SD WAN solutions, and perhaps it’s about time. Zero Touch Deployment in the context of SD WAN means being able to ship a box to a spoke site, have ‘Dumb Hands’ on site plug in the Continue reading
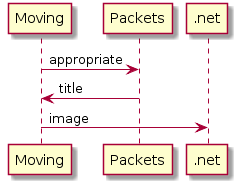
A colleague at work recently told me that I should check out PlantUML. His advice is usually good, and this is no exception.
PlantUML uses a relatively simple text language to describe the desired diagram, then makes generation of the image as simple as processing the UML file. It’s easy to try online at http://plantuml.com/ where there is a text editor with real time image updates as you add more content.
Sequence diagrams are probably the simplest to build, and are absurdly fast to create. Here’s a simple example of a TCP exchange:
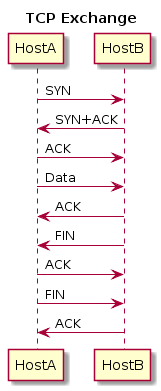 To create this, I used the following PlantUML:
To create this, I used the following PlantUML:
@startuml
title : TCP Exchange
HostA -> HostB : SYN
HostB -> HostA : SYN+ACK
HostA -> HostB : ACK
HostA -> HostB : Data
HostB -> HostA : ACK
HostB -> HostA : FIN
HostA -> HostB : ACK
HostA -> HostB : FIN
HostB -> HostA : ACK
@enduml
You’re not limited to two endpoints, of course:
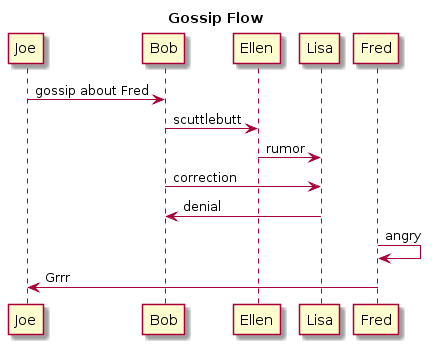
Here’s a simple use case with Fred and Joe again:
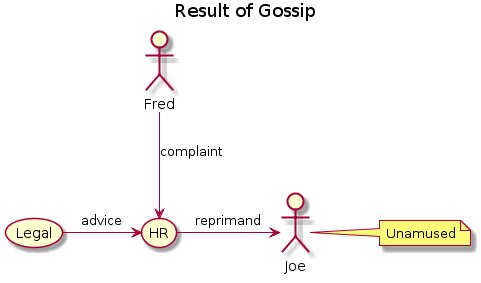 The PlantUML to generate this was:
The PlantUML to generate this was:
@startuml
title : Result of Gossip
Fred --> (HR) : complaint
(Legal) -> (HR) : advice
(HR) -> Continue reading
Software Defined Wide Area Networking (SD WAN) –sometimes known as SD-WAN and occasionally as Hybrid WAN– is evidently still the flavor of the month in Silicon Valley. Much as it seemed that anything with the word “Cloud” in it a few years back would have money thrown at it indiscriminately by investors, the current favored (funded) feature surely has to be SD WAN. As there doesn’t seem to be one unifying definition of what constitutes “SD WAN” any more than there’s a precise definition of Software Defined Networking, I’m going to define it in the way that I believe best encompasses the intent behind the current flock of solutions.
I’ve said before that SDN is a clever idea and eventually will change the way we do networking. However, many are hesitant to adopt SDN because it’s not always immediately obvious what the benefits are to the typical non-hyperscale datacenter other than having to do a lot of retraining. In other words SDN can potentially solve many problems, but it will most likely be necessary to find a ‘killer app’ that will encourage wider adoption, even in it’s only applicable to a limited Continue reading
For the new few months in addition to posting here, I’ll be making some blog posts over on Solarwinds‘ Thwack Community in their “Geek Speak” blogs, on the general topic of network management. I won’t be reposting the content here, but I’ll be sharing the links each time I post, and I hope you can find a moment to read them, rate the post if you are that way inclined, and maybe even comment! I know have some very smart readers, and Thwack has some smart users too, so the conversation should be great!
Solarwinds Thwack is a light-hearted community providing specific product support and templates for Solarwinds products, but also offering more general support on networking-related issues through blogs, community forums and product forums. It’s kind of a fun place to dig around, and the users are usually not short of an opinion on most topics. Signing up for an account is easy and free, and then you can post comments and join in the discussion!
Here’s the intro to the first post in the series, called “Do You Monitor Your Network Interfaces? at Geek Speak”
Hope to see you over there!
I am participating in the Solarwinds Continue reading

In the last two posts I described tools to validate the required intermediate SSL certificate chain for a given server certificate, and to validate that the private key and server certificate are a match. Once the SSL configuration is deployed though, how do we check that everything is working correctly and the new certificate is in place?
The simple answer is “use one of the tools already out there on the Internet.” That’s a fair answer, and I have been known to use some of these. A quick Google search shows a validator on SSLShopper:
There’s also a similar tool on DigiCert:
These are great tools and I strongly encourage using them to check your sites. However, there’s one situation where they can’t help you, and that’s when your site is only accessible internally. How do I do certificate validation for private sites?
Yet again, OpenSSL is my tool of choice because not only can it open an SSL connection to a VIP, but it can also show the certificates it is sent. You may be thinking “Why not just use a web browser?” Again, Continue reading

You’re asked to update the SSL certificate for movingpackets.net on a load balancer. The requestor (me, in this case) gives you the certificate file. I don’t need to give you the intermediate certificate bundle because you’re going to use the checkcert tool to sort that out. I also tell you to use the same private key as for the last certificate. How do you know that the old private key works with the new public certificate?
My good friend OpenSSL can help us match a certificate and key. The basic premise is that the modulus of both the key and the cert file should be the same. The openssl commands to do this are:
# openssl x509 -noout -modulus -in microsoft.com.crt
Modulus=B788D872FFB6C827EF5656A0535CC1E36343D6A29F1824564238793737BB2C17EAB7FF6A2032AB95174FDA4A24AFF438DFB23B85746E7B37D657F5EB3E3580291218CA66AC8CF872C2A62FD1A7F1DB85C554E4DE803E3F9397D251C8A283FA0EF4314210BFF88AE0AF656C5953A71A8D6A4C2A4476B6AD1EADE1920D1CEEEB8E0C16583698CC735861FA98D63DA3EB5632968751D099AAB7D22321920AE962B065100FFEA7BC5EF7E3DC1398935F3C6F8C43DC689BC290DAACEEDD487ECD81795BC7CA702B20369029CE6F7527D0E16CD9CC603671B05940433D49590EB15C6768DF0A326AEE7AE77084BCCC4707D1AE2694E6E0477C038598F5552B46D04C95
# openssl rsa -noout -modulus -in microsoft.com.key
Modulus=B788D872FFB6C827EF5656A0535CC1E36343D6A29F1824564238793737BB2C17EAB7FF6A2032AB95174FDA4A24AFF438DFB23B85746E7B37D657F5EB3E3580291218CA66AC8CF872C2A62FD1A7F1DB85C554E4DE803E3F9397D251C8A283FA0EF4314210BFF88AE0AF656C5953A71A8D6A4C2A4476B6AD1EADE1920D1CEEEB8E0C16583698CC735861FA98D63DA3EB5632968751D099AAB7D22321920AE962B065100FFEA7BC5EF7E3DC1398935F3C6F8C43DC689BC290DAACEEDD487ECD81795BC7CA702B20369029CE6F7527D0E16CD9CC603671B05940433D49590EB15C6768DF0A326AEE7AE77084BCCC4707D1AE2694E6E0477C038598F5552B46D04C95
Are they the same? Did you check every byte? The lazy way to do this, then, is to take an md5 hash of the output and compare those instead; it’s little easier and while there’s a remote chance that two non-equal moduli could have the same md5 hash, it’s pretty unlikely. And so:
# openssl x509 -noout -modulus -in microsoft. Continue reading