Author Archives: Kausum Kumar
Author Archives: Kausum Kumar
As you plan to attend VMworld 2018 – Do you have questions like : how do I micro-segment? What grouping strategies do I use? How to do a Firewall-As-A-Service in hybrid VM and Container environments? Or you are a Pros and would like to know more of what is new? – We would like to help you answer and have the best possible help as you head back to your organizations. This blog captures the Micro-Segmentation sessions that are geared towards designing your micro-segmentation strategies. Meet with our experts go in details with you. Listen to our customers on their journeys and understand all the options that VMware can help you with this journey.
Monday: August 27, 2018
It starts at 11.30 am with:
Have lunch and then you have two choices:
OR
There are two digital explosions simultaneously happening in enterprises across all verticals. Enterprises are moving at a breakneck speed on every aspect of their business. From managing their supply-chain, making purchasing decisions, targeted marketing campaign to users, creating apps to connect with users and making it easier for users to consume their products.
The good news is technology is keeping pace and is a step ahead in helping the business achieve their goals. These business imperatives are forcing software iterations to be faster and be more efficient. This is leading to newer innovative models around people/processes/tools that we collectively call Continuous Integration(CI)/Continuous Development (CD). Teams leading the charge on CI/CD models are working in a “DevOps” model.
The second explosion is related to the first explosion. As complex software become easy-to-use and be ubiquitous, sophisticated tools can be used to attack enterprises. Managing Security is getting harder. Last decade – there was a belief – I am not going to be attacked. Fast forward today – enterprises expect to be attacked and breached. This is not just a baseless impression. Forrester’s 2018 survey shows that 66% of survey respondents have faced a major security incident.

VMware NSX is a network virtualization and security platform for the enterprise that is helping our customers make the transition to the digital era. As developers embrace new technologies like containers, and the percentage of workloads running in public clouds increases, network virtualization must expand to offer a full range of networking and security services, natively, in these environments.
Today, we are announcing the next version of NSX-T that can provide network virtualization for a multi-cloud and multi-hypervisor environment. The NSX technology that you are familiar with and use it for so many years is now be available for cloud and container environments. Circa VMworld 2016, we showed a prototype of NSX that can provide network virtualization and micro-segmentation for native AWS workloads. That journey is now complete and the initial availability of that service for some customers is already available for their AWS workloads.
NSX can now provide seamless network virtualization for workloads running on either VMs or Containers. VMs can be located either on-prem or on AWS. NSX will provide the entire feature set for either Vmware vSphere Hypervisors or KVM hypervisors. For native workloads on AWS, NSX will provide VMware NSX Secure Cloud to provide the Continue reading
 VMware NSX is a network virtualization and security platform for the enterprise that is helping our customers make the transition to the digital era. As developers embrace new technologies like containers, and the percentage of workloads running in public clouds increases, network virtualization must expand to offer a full range of networking and security services,... Read more →
VMware NSX is a network virtualization and security platform for the enterprise that is helping our customers make the transition to the digital era. As developers embrace new technologies like containers, and the percentage of workloads running in public clouds increases, network virtualization must expand to offer a full range of networking and security services,... Read more →
![]() Micro-segmentation with VMware NSX compartmentalizes the data center to contain the lateral spread of ransomware attacks such as WannaCry
Micro-segmentation with VMware NSX compartmentalizes the data center to contain the lateral spread of ransomware attacks such as WannaCry
On May 12 2017, reports began to appear of the WannaCry malware attacking organizations worldwide in one of the largest ransomware cyber incidents to date. The European Union Agency for Law Enforcement Cooperation (Europol) has reported more than 200,000 attacks in over 150 countries and in 27, with the full scope of the attack yet to be determined. Victims include organizations from all verticals.
WannaCry targets Microsoft Windows machines, seizing control of computer systems through a critical vulnerability in Windows SMB. It also utilizes RDP as an attack vector for propagation. It encrypts seized systems and demands a ransom be paid before decrypting the system and giving back control. The threat propagates laterally to other systems on the network via SMB or RDP and then repeats the process. An initial analysis of WannaCry by the US Computer Emergency Readiness Team (US-CERT) can be found here, with a detailed analysis from Malware Bytes here.
One foundational aspect of increasing cybersecurity hygiene in an organization to help mitigate such attacks from proliferating is enabling a least privilege (zero trust) model by embedding security directly into the data center network. The Continue reading
“Micro-Segmentation provides a way to build a zero-trust network – where all networks, perimeters and application are inherently untrusted.” – declared Forrester Consulting in 2015 with their white paper Leveraging Micro-Segmentation to build zero-trust model. The last mile in creating a truly zero-trust network implies not trusting each application and also tiers within an application (Figure 1). To complete the last mile, network, security and risk professionals are increasingly looking for tools to understand application communication patterns and providing access controls to them. With version 6.3.0, NSX has unveiled 2 new tools, namely, Application Rule Manager (ARM) and Endpoint Monitoring (EM), to help professionals understand application patterns.
 Figure 1: Zero-Trust Model using NSX
Figure 1: Zero-Trust Model using NSX
From Theory to Practice
Micro-Segmenting each application requires understanding of application communication patterns. Users should allow the flows required by the application. To accomplish zero-trust, users should be closing all unwanted flows & ports. Figure 2., is a sample practical firewall policy model to achieve that. In this model, ARM/EM provides application patterns and a one-click conversion of those patterns into distributed firewall rules to achieve inter/intra application rules.
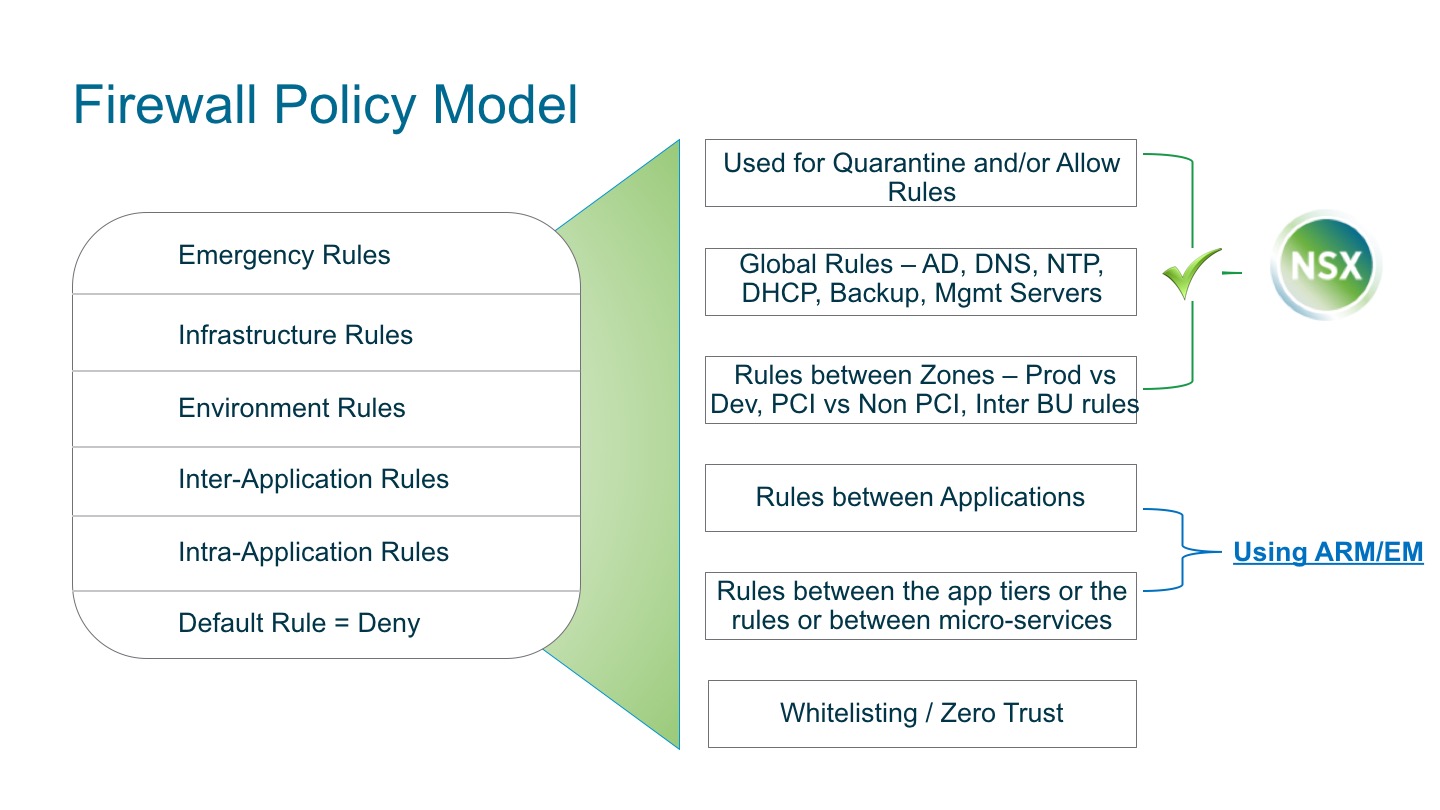 Figure 2: Firewall Policy Model
Figure 2: Firewall Policy Model
Generating Distributed Firewall Rules Rapidly
Any application in the datacenter can be Continue reading