Author Archives: Wade Holmes
Author Archives: Wade Holmes
authors – Geoff Wilmington, Mike Lonze
Healthcare organizations are focusing more and more on securing patient data. With Healthcare breaches on the rise, penalties and fines for lost or stolen PHI and PII data is not only devastating to the patients, but to the Healthcare organization as well. The Ponemon Institute Annual Benchmark Study on Privacy & Security of Healthcare Data has shown that nearly 50 percent of Healthcare organizations, up 5 percent from a previous study, that criminal attacks are the leading cause of Healthcare breaches. [1] With breaches on the rise and Healthcare organizations feeling the pain, how can we help Healthcare start layering security approaches on their most critical business applications that contain this highly critical data?
The principle of least privilege is to provide only the necessary minimal privileges for a process, user, or program to perform a task. With NSX, we can provide a network least privilege for the applications that run on the vSphere hypervisor using a concept called Micro-segmentation. NSX places a stateful firewall at the virtual network card of every virtual machine allowing organizations to control very granularly how virtual machines communicate or don’t communicate with each Continue reading
co-author Geoff Wilmington
Traditional data center endpoint security products focus on detecting and responding to known bad behavior. There are hundreds of millions of disparate malware attacks, with over a million getting added every day. In addition, there is the threat of zero-day attacks exploiting previously unknown vulnerabilities. It becomes a never-ending race to “chase bad” without ever staying ahead of the threat landscape. What if we took an opposite approach to security? What if, instead of “chasing bad” we started by “ensuring good”?
![]() VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
VMware AppDefense is a new security product focused on helping customers build a compute least privilege security model for data center endpoints and provide automated threat detection, response, and remediation to security events. AppDefense is focused on “ensuring good” versus “chasing bad” on data center endpoints. When we focus our attention on what a workload is supposed to be doing, our lens for seeing malicious activity is much more focused and as a result, we narrow the exploitable attack surface of the workload down to what we know about.
Changing The Way We Secure Compute
AppDefense applies the concept of “ensuring good” by using three main techniques:
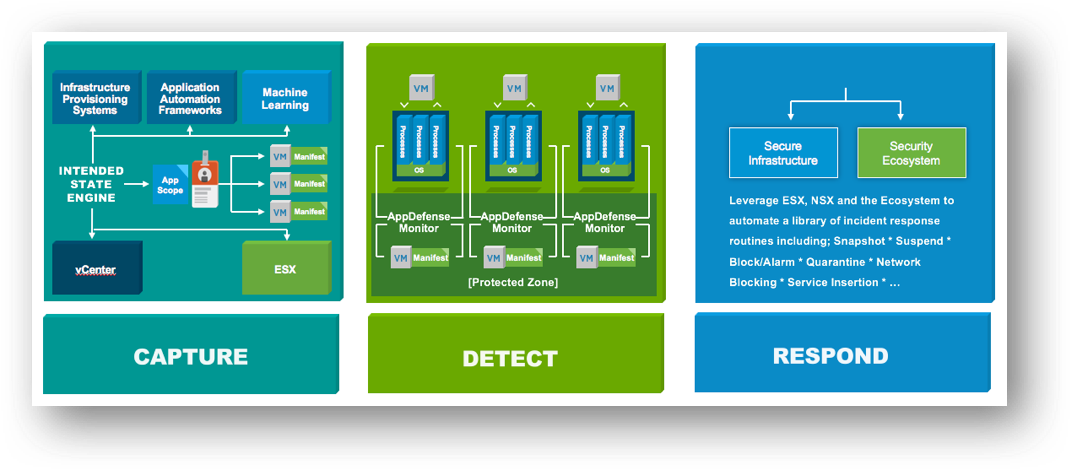
Capture
AppDefense starts by capturing Continue reading
 VMware NSX Micro-segmentation Day 1 is available for free download! VMware NSX Micro-segmentation Day 1 is a concise book that provides the necessary information to guide organizations interested in bolstering their security posture through the implementation of micro-segmentation.VMware NSX Micro-segmentation Day 1 highlights the importance of micro-segmentation in enabling better data center cyber hygiene. It also provides the knowledge and guidance needed to effectively design and implement a data center security strategy around micro-segmentation.
VMware NSX Micro-segmentation Day 1 is available for free download! VMware NSX Micro-segmentation Day 1 is a concise book that provides the necessary information to guide organizations interested in bolstering their security posture through the implementation of micro-segmentation.VMware NSX Micro-segmentation Day 1 highlights the importance of micro-segmentation in enabling better data center cyber hygiene. It also provides the knowledge and guidance needed to effectively design and implement a data center security strategy around micro-segmentation.
VMware NSX Micro-segmentation covers the following topics.
 Micro-segmentation Definition
Micro-segmentation Definition
The post VMware NSX Micro-segmentation Day 1 Book Available! appeared first on The Network Virtualization Blog.
 The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
The VMware NSX Micro-segmentation Cybersecurity Benchmark report has been released! As previewed in part six of the Micro-segmentation Defined – NSX Securing Anywhere blog series , independent cyber risk management advisor and assessor Coalfire was sponsored by VMware to create an industry first Micro-segmentation Cybersecurity Benchmark report. Coalfire conducted an audit of the VMware NSX micro-segmentation capabilities to develop this benchmark report detailing the efficacy of NSX as a security platform through a detailed “micro-audit” process, testing NSX against simulated zero-day threats.
Testing included five different network design patterns, and demonstrated how NSX micro-segmentation can provide stateful, distributed, policy-based protection in environments regardless of network topology. Topologies included –
Coalfire’s examination and testing of VMware NSX technology utilized simulated exploits that depict likely malware and Continue reading
Welcome to part 6 of the Micro-segmentation Defined– NSX Securing “Anywhere” blog series. Previous topics covered in this series include
• Part I – Micro-segmentation Defined
• Part II – Securing Physical Environments
• Part III – Operationalizing Micro-segmentation
• Part IV – Service Insertion
• Part V – Context, Visibility, and Containment
Previous posts set the stage by introducing and defining the characteristics of micro-segmentation; showing how it has utility in the modern data center; how we might apply it to our existing software-defined and physical networks; how policy-driven NSX management may be used to deliver comprehensive security; and, that we can use physical and virtual third-party security appliances in conjunction with NSX to create a service chain and apply special processing to our vital network flows.
In this sixth part of the NSX Securing “Anywhere” blog, Chris Krueger of Coalfire Systems will preview some of our work in comprehensively benchmarking VMware NSX micro-segmentation. The Micro-segmentation Benchmark is a project being delivered by Coalfire Systems, Inc. an internationally recognized third party audit organization (3PAO) and leading provider of IT advisory services for security in retail, payments, healthcare, financial services, higher education, hospitality, government,and utilities. Coalfire has Continue reading
 The landscape of the modern data center is rapidly evolving. The migration from physical to virtualized workloads, move towards software-defined data centers, advent of a multi-cloud landscape, proliferation of mobile devices accessing the corporate data center, and adoption of new architectural and deployment models such as microservices and containers has assured the only constant in modern data center evolution is the quest for higher levels of agility and service efficiency. This march forward is not without peril as security often ends up being an afterthought. The operational dexterity achieved through the ability to rapidly deploy new applications overtakes the ability of traditional networking and security controls to maintain an acceptable security posture for those application workloads. That is in addition to a fundamental problem of traditionally structured security not working adequately in more conventional and static data centers.
The landscape of the modern data center is rapidly evolving. The migration from physical to virtualized workloads, move towards software-defined data centers, advent of a multi-cloud landscape, proliferation of mobile devices accessing the corporate data center, and adoption of new architectural and deployment models such as microservices and containers has assured the only constant in modern data center evolution is the quest for higher levels of agility and service efficiency. This march forward is not without peril as security often ends up being an afterthought. The operational dexterity achieved through the ability to rapidly deploy new applications overtakes the ability of traditional networking and security controls to maintain an acceptable security posture for those application workloads. That is in addition to a fundamental problem of traditionally structured security not working adequately in more conventional and static data centers.
Without a flexible approach to risk management, which adapts to the onset of new technology paradigms, security silos using disparate approaches are created. These silos act as control islands, making it difficult to apply risk-focused predictability into your corporate security posture, causing unforeseen risks to be realized. These actualized risks cause an organization’s attack surface to grow as the adoption of new compute Continue reading