OAuth Auth Server through Workers
Let’s pretend I own a service and I want to grant other services access to my service on behalf of my users. The familiar OAuth 2.0 is the industry standard used by the likes of Google sign in, Facebook, etc. to communicate safely without inconveniencing users.
Implementing an OAuth Authentication server is conceptually simple but a pain in practice. We can leverage the power of Cloudflare Worker to simplify the implementation, reduce latency, and segregate our service logic from the authentication layer.
For those unfamiliar with OAuth, I highly recommend reading a more in depth article.
The steps of the OAuth 2.0 workflow are as follows:
- The consumer service redirects the user to a callback URL that was setup by the auth server. At this callback URL, the auth server asks the user to sign in and accept the consumer permissions requests.
- The auth server redirects the user to the consumer service with a code.
- The consumer service asks to exchange this code for an access token. The consumer service validates their identity by including their client secret in the callback URL.
- The auth server gives the consumer the access token.
- The consumer service can now use Continue reading
The truth about Black Friday and Cyber Monday

At Cloudflare we handle a lot of traffic on behalf of our customers. Something we all see and hear a lot about at this time of year are Black Friday (23 November this year) and Cyber Monday (26 November) - but just how important are these days on the Internet?

To try and answer this question, we took a look at anonymised samples of HTTP requests crossing our network. First of all, let’s look at total page views from across our global network from the last few weeks and see if we can spot Black Friday and Cyber Monday:
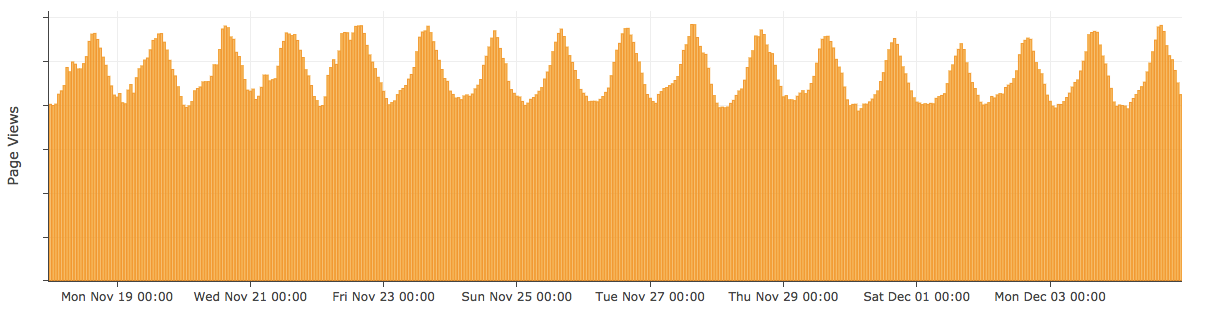
So this is total page views by day (UTC) from November 19 (a week before Cyber Monday) until Monday December 3. Other than follow-the-sun fluctuations in a repeating daily pattern, each whole day is pretty similar in shape and size compared to the last. Black Friday and Cyber Monday aren’t visible in overall traffic patterns.
Get specific
We have a very diverse set of customers across 12 million domain names and not all of them are selling products or doing so directly online. To identify those websites Continue reading
A new look on your Cloudflare dashboard
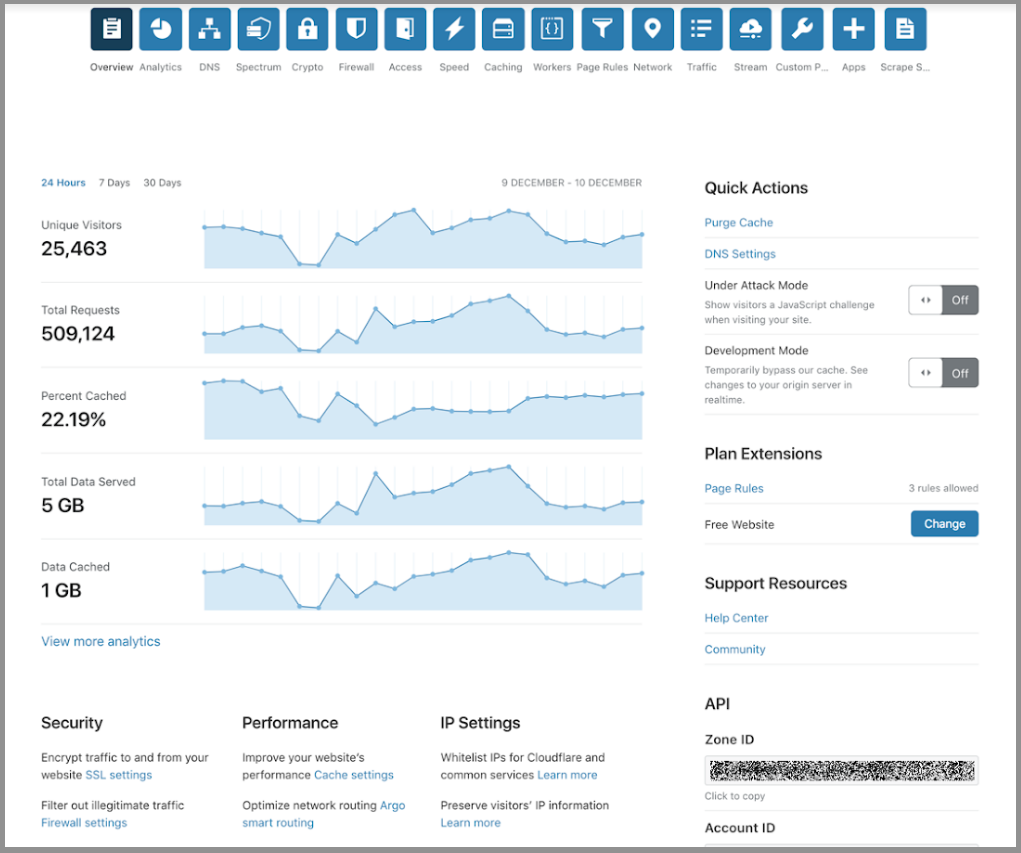
Building a great customer experience is a top priority here at Cloudflare. Over the last week, we have been slowly rolling out an improvement to our customer dashboard - specifically the zone overview page. We are now ready to share the new dashboard with everyone.
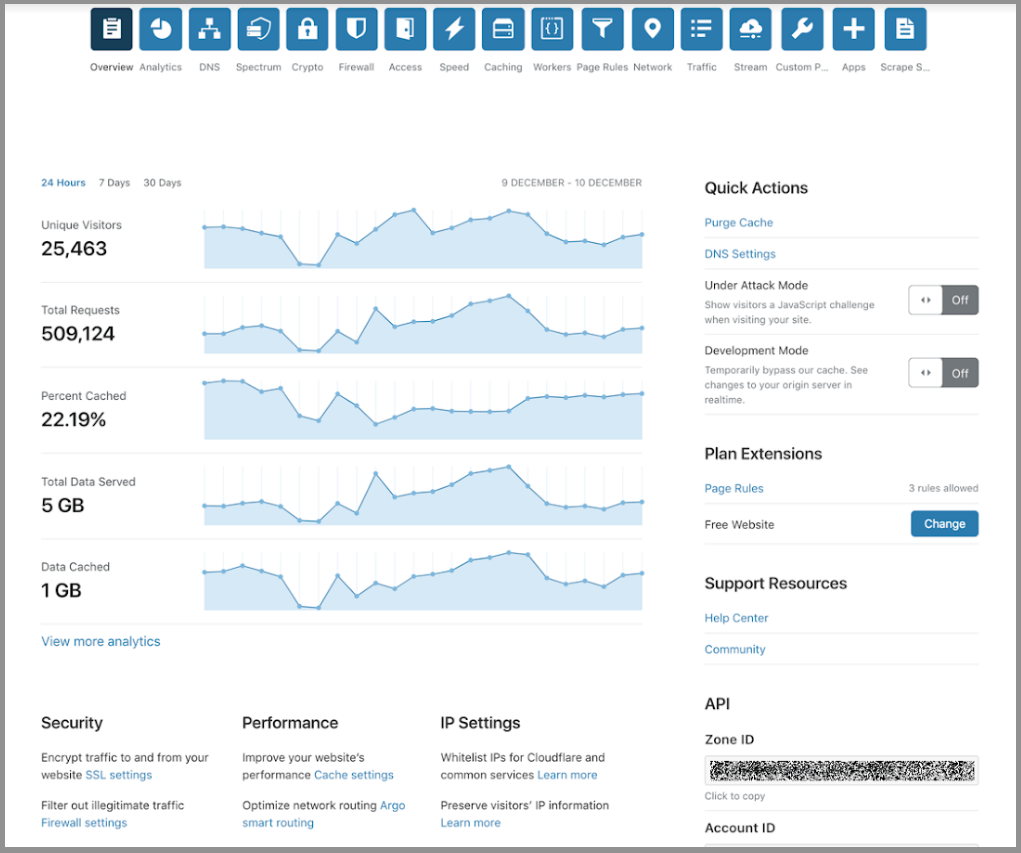
Many of the changes you’ll notice first were driven directly by customer feedback. We’ve heard time and time again that site owners would like better visibility of their key analytics, and for it to be easier to apply certain common settings changes. This new dashboard provides both, with a snapshot of several of your key analytics, and a new toolkit area for easy access to key functions. This page has also been redesigned from top to bottom for responsiveness across various devices and screen widths.
Even more interesting is all the work under-the-hood that went into making this release and how it sets the stage for improvements to our customer experience as we look ahead to 2019. This is one of the first pieces of production Product work shipped using our new prototyping framework. We will soon be sharing details of the design systems work that underlies the new experience on Continue reading
Ampere Targets Hyperscalers, Challenges Intel With Arm-Based Chips
 The year-old startup, founded by former Intel president Renee James, is also partnering with Packet, Cloudflare, and other companies on 5G and edge computing proof of concepts.
The year-old startup, founded by former Intel president Renee James, is also partnering with Packet, Cloudflare, and other companies on 5G and edge computing proof of concepts.
EU Terrorist Content Online proposal – political haste and unintended consequences


In September, the European Commission presented a legislative proposal to address the removal of terrorist content online. There has been significant political pressure, particularly as the EU elections of 2019 approach, towards internet companies taking on increased responsibility in the area of terrorist propaganda online. This proposal would be a marked move from various voluntary initiatives taken up by some social media companies in recent times towards a legal responsibility framework for many.
While appreciating the concerns around terrorism, Cloudflare is not only troubled by the late presentation of this proposal – which leaves inadequate time for a thorough review before this EU legislative term expires – but also much of the substance. Along with others such as CDT, GSMA/ETNO and Mozilla, we have significant concerns around the legal implications, practical application and possible unintended consequences of the proposal, some of which we outline below. Furthermore, we believe that little evidence has been presented as to the necessity of the proposed measures.
Concerns and shortcomings
The Commission’s proposal does not account for the complexity and range of information society services having a storage component - not all services have the same Continue reading
How well do you know website performance?


How quickly did this blog post load? Did you happen to notice?
Most website visitors do notice that sort of thing, even if they don't realize it consciously. In fact, virtually all visitors have strong opinions about how quickly a website should load, how responsive it should be, and how often it should go down (preferably, never). Most users strongly prefer webpages that take under 5 seconds to load, and they're much more likely to leave without buying products or reading content if a page takes too long to render.
Everyone should understand how to keep websites fast
Part of the Cloudflare mission is to make the Internet better by helping it perform better. One way we are delivering on our mission is by sharing easy-to-read educational content to assist anyone with a web property.
We recently launched a performance-themed Learning Center: a series of educational articles on why performance matters, the factors affecting performance, and some of the best practices for making websites faster. Check out the Performance Learning Center!
This Learning Center is for anyone who wants to really do a deep dive into the complex topic of website performance, no matter what their technical background Continue reading
Cloudflare Apps Fund 2.0
Today we are launching the second iteration of the Cloudflare App Developer Fund.
This is an investment fund started in partnership with Venrock, Pelion Venture Partners, and New Enterprise Associates. We created the fund to provide developers with resources so that they can build apps using the Cloudflare network and our serverless product, Workers, which enables developers to create applications without configuring or maintaining infrastructure. The goal is to fuel a new economy that grows into a thriving ecosystem so that developers’ serverless innovations can enjoy commercial success.
Cloudflare Apps with Workers allows developers to package Workers, delivering new worker-powered experiences to Cloudflare customers, all within a few clicks via Cloudflare Apps.
Our CTO, John Graham-Cumming talks about it in a recently recorded video:
In short, Cloudflare is looking for apps that will advance our mission to help build a better Internet: one that is safe, fast and reliable. We are seeking out apps that have a clear vision, delight customers by the ease of use and align with our vision. Having already seen multiple use cases around custom application security, data loss prevention, and bot mitigation, we can’t wait to see what else you come up Continue reading
Logs from the Edge

With Cloudflare Workers, our JavaScript environment at the edge, it is possible to send traffic logs to arbitrary locations. In this post we are going to discuss an example Worker implementation on how to achieve this. So if you are building or maintaining your own traffic logging/analytics environment, read on.
To build the underlying script we are going to leverage sub requests. Sub requests, which can be spawned from the initial HTTP/S request, can be used to aggregate and compose a response from several back end services, or, like in the example discussed here, to post data to a specific endpoint. Sub requests can be made asynchronously and after the initial request has been fully served to avoid adding unnecessary latency to the main request.

The Worker Code
In this example we assume an Elastic stack has been set up at elk.example.com and has been configured to receive via HTTP/S PUT requests a number of fields for each log line. The full script that we are going to look at can be found below:
addEventListener('fetch', event => {
event.respondWith(fetchAndLog(event));
})
async function fetchAndLog(event) {
const response = await fetch(event.request);
event.waitUntil(logToElk(event.request, response));
return response;
Continue readingKnow your SCM_RIGHTS
As TLS 1.3 was ratified earlier this year, I was recollecting how we got started with it here at Cloudflare. We made the decision to be early adopters of TLS 1.3 a little over two years ago. It was a very important decision, and we took it very seriously.
It is no secret that Cloudflare uses nginx to handle user traffic. A little less known fact, is that we have several instances of nginx running. I won’t go into detail, but there is one instance whose job is to accept connections on port 443, and proxy them to another instance of nginx that actually handles the requests. It has pretty limited functionality otherwise. We fondly call it nginx-ssl.
Back then we were using OpenSSL for TLS and Crypto in nginx, but OpenSSL (and BoringSSL) had yet to announce a timeline for TLS 1.3 support, therefore we had to implement our own TLS 1.3 stack. Obviously we wanted an implementation that would not affect any customer or client that would not enable TLS 1.3. We also needed something that we could iterate on quickly, because the spec was very fluid back then, and also something Continue reading
L4Drop: XDP DDoS Mitigations

Efficient packet dropping is a key part of Cloudflare’s distributed denial of service (DDoS) attack mitigations. In this post, we introduce a new tool in our packet dropping arsenal: L4Drop.

We've written about our DDoS mitigation pipeline extensively in the past, covering:
- Gatebot: analyzes traffic hitting our edge and deploys DDoS mitigations matching suspect traffic.
- bpftools: generates Berkeley Packet Filter (BPF) bytecode that matches packets based on DNS queries, p0F signatures, or tcpdump filters.
- Iptables: matches traffic against the BPF generated by bpftools using the
xt_bpfmodule, and drops it. - Floodgate: offloads work from iptables during big attacks that could otherwise overwhelm the kernel networking stack. Incoming traffic bypasses the kernel to go directly to a BPF interpreter in userspace, which efficiently drops packets matching the BPF rules produced by bpftools.
Both iptables and Floodgate send samples of received traffic to Gatebot for analysis, and filter incoming packets using rules generated by bpftools. This ends up looking something like this:

This pipeline has served us well, but a lot has changed since we implemented Floodgate. Our new Gen9 and ARM servers use different network Continue reading
Working out Backend Knots and Building Routers (Austin Real World Serverless Video Recap)
I work in Developer Relations at Cloudflare and I'm fortunate to have top-notch developers around me who are willing to share their knowledge with the greater developer community. I produced a series of events this autumn called Real World Serverless at multiple locations around the world and I want to share the recorded videos from these events.
Our Austin Real World Serverless event (in partnership with the ATX Serverless User Group Meetup) included two talks about Serverless technology featuring Victoria Bernard and Preston Pham from Cloudflare. They spoke about working out backend knots with Workers and building a router for the great good.
About the talks
Working out Backend Knots with Workers - Victoria Bernard (0:00-15:19)
Cloudflare Workers is a platform the makes serverless development and deployment easier than ever. A worker is a script running between your clients' browsers and your site's origin that can intercept requests. Victoria went over some popular use cases of how proxy workers can dramatically improve a site's performance and add functionality that would normally require toying with complicated back-end services.
Build a Router for Great Good - Preston Pham (15:20-33:53)
Serverless computing is great, but requires routing or some kind of API Continue reading
My Second Cloudflare Company Retreat

Last week, 760 humans from Singapore, London, Beijing, Sydney, Nairobi, Austin, New York, Miami, Washington DC, Warsaw, Munich, Brussels, and Champaign reunited with their San Francisco counterparts for our 9th annual Cloudflare company retreat in the San Francisco Bay Area. The purpose of the company retreat is to bring all global employees together under one roof to bond, build bridges, have fun, and learn – all in support of Cloudflare’s mission to help build a better Internet.
It’s easy to write off corporate retreats as an obligatory series of meetings and tired speeches, but Cloudflare’s retreats are uniquely engaging, personalized, fun, and inspiring. Having grown with Cloudflare over the last year (I started just before our 2017 retreat), I wanted to share some of my experiences to highlight Cloudflare’s incredible culture.
The office was buzzing with different languages and laughter as people hugged and shook hands for the first time after working online together for a year or more. Everyone’s Google calendar looked like a rainbow as we each mined for white space to squeeze in those coveted 1:1s, all-hands presentations, and bowling offsites with our global colleagues. The buses and Google chats felt like summer camp, with people claiming Continue reading
Every 7.8μs your computer’s memory has a hiccup


Modern DDR3 SDRAM. Source: BY-SA/4.0 by Kjerish
During my recent visit to the Computer History Museum in Mountain View, I found myself staring at some ancient magnetic core memory.

Source: BY-SA/3.0 by Konstantin Lanzet
I promptly concluded I had absolutely no idea on how these things could ever work. I wondered if the rings rotate (they don't), and why each ring has three wires woven through it (and I still don’t understand exactly how these work). More importantly, I realized I have very little understanding on how the modern computer memory - dynamic RAM - works!
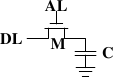
Source: Ulrich Drepper's series about memory
I was particularly interested in one of the consequences of how dynamic RAM works. You see, each bit of data is stored by the charge (or lack of it) on a tiny capacitor within the RAM chip. But these capacitors gradually lose their charge over time. To avoid losing the stored data, they must regularly get refreshed to restore the charge (if present) to its original level. This refresh process involves reading the value of every bit and then writing it back. During this "refresh" time, the memory is busy and it can't perform normal operations Continue reading
Serverless Progressive Web Apps using React with Cloudflare Workers
Let me tell you the story of how I learned that you can build Progressive Web Apps on Cloudflare’s network around the globe with one JavaScript bundle that runs both in the browser and on Cloudflare Workers with no modification and no separate bundling for client and server. And when registered as a Service Worker, the same JavaScript bundle will turn your page into a Progressive Web App that doesn’t even make network requests. Here's how that works...
"Any resemblance to actual startups, living or IPO'd, is purely coincidental and unintended" - @sevki
A (possibly apocryphal) Story
I recently met up with some old friends in London who told me they were starting a new business. They did what every coder would do... they quickly hacked something together, bought a domain, and registered the GitHub org and thus Buzzwords was born.
The idea was simple: you could feed the name of your application into a machine learning model and it would generate the configuration files for your deployment for various container orchestrators. They achieved this by going through millions of deployment configurations and training a linear regression model by gamifying quantum computing because blockchain, or something (I told you this Continue reading
Fast Google Fonts with Cloudflare Workers
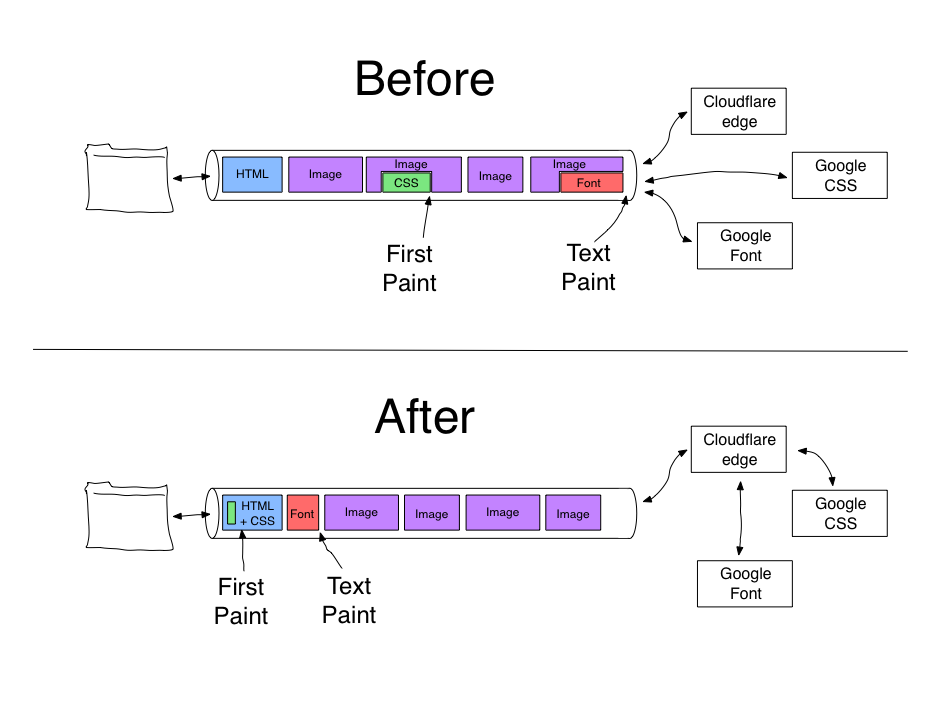
Google Fonts is one of the most common third-party resources on the web, but carries with it significant user-facing performance issues. Cloudflare Workers running at the edge is a great solution for fixing these performance issues, without having to modify the publishing system for every site using Google Fonts.
This post walks through the implementation details for how to fix the performance of Google Fonts with Cloudflare Workers. More importantly, it also provides code for doing high-performance content modification at the edge using Cloudflare Workers.
Google fonts are SLOW
First, some background. Google Fonts provides a rich selection of royalty-free fonts for sites to use. You select the fonts you want to use, and end up with a simple stylesheet URL to include on your pages, as well as styles to use for applying the fonts to parts of the page:
<link href="https://fonts.googleapis.com/css?family=Open+Sans|Roboto+Slab"
rel="stylesheet">
<style>
body {
font-family: 'Open Sans', sans-serif;
}
h1 {
font-family: 'Roboto Slab', serif;
}
Your visitor’s browser fetches the CSS file as soon as the HTML for the page is available. The browser will request the underlying font files when the browser does layout for the page and discovers that it needs Continue reading
My time as an intern (thus far)

It has been over three months since I started as a marketing intern at Cloudflare. Even before joining the Cloudflare team, I enjoyed reading the technical blog posts about Cloudflare’s use cases and solutions, as well as the inclusive and creative culture. Educating the world about the threats we face on the Internet is something that I found truly valuable. I figured that I would give my own spin on what it’s like to join and work at Cloudflare by writing a blog post too.
Chapter 1: The Path towards the Orange Cloud

Before starting as a freshman in university, I created an online portfolio for my photography. It has been a passion of mine for about 9 years. I tried a multitude of platforms but none afforded me the aesthetic control that I wanted. The only solution was to build and host my own site. I started learning HTML/CSS, a bit of JavaScript and jQuery and so on.
This led to me using the Koken CMS, and hosting it on DigitalOcean in a Docker container. What was left was SSL/TLS encryption and a CDN (my friends in Europe find the loading times unbearable). Continue reading
Cloudflare’s Response to a Privacy Framework


Why We Weighed In on US Privacy Efforts
Cloudflare’s mission is to help build a better internet, and privacy has to be at the heart of that effort. That’s why we submitted comments last week on the National Telecommunications and Information Administration (NTIA)’s request for comment on its proposed approach to advance consumer privacy.
We think it is important for Internet infrastructure companies like us to be a part of the conversation about the future of internet privacy. We want to advocate for an internet that remains accessible to all, while becoming more secure and protective of privacy.
What is NTIA and what is it trying to do?
In 2018, we’ve seen high profile data breaches and data misuse, Europe’s sweeping data protection law – the General Data Protection Regulation (GDPR) – come into effect, and California pass its own comprehensive Consumer Privacy Act (CCPA). All of this has captured the attention of Washington, D.C. lawmakers and regulators.
On September 25, 2018, NTIA began a process to solicit feedback from stakeholders on a proposed approach to consumer data privacy. NTIA is the Executive Branch agency in the Department of Commerce that is principally Continue reading
Introducing Apps with Workers
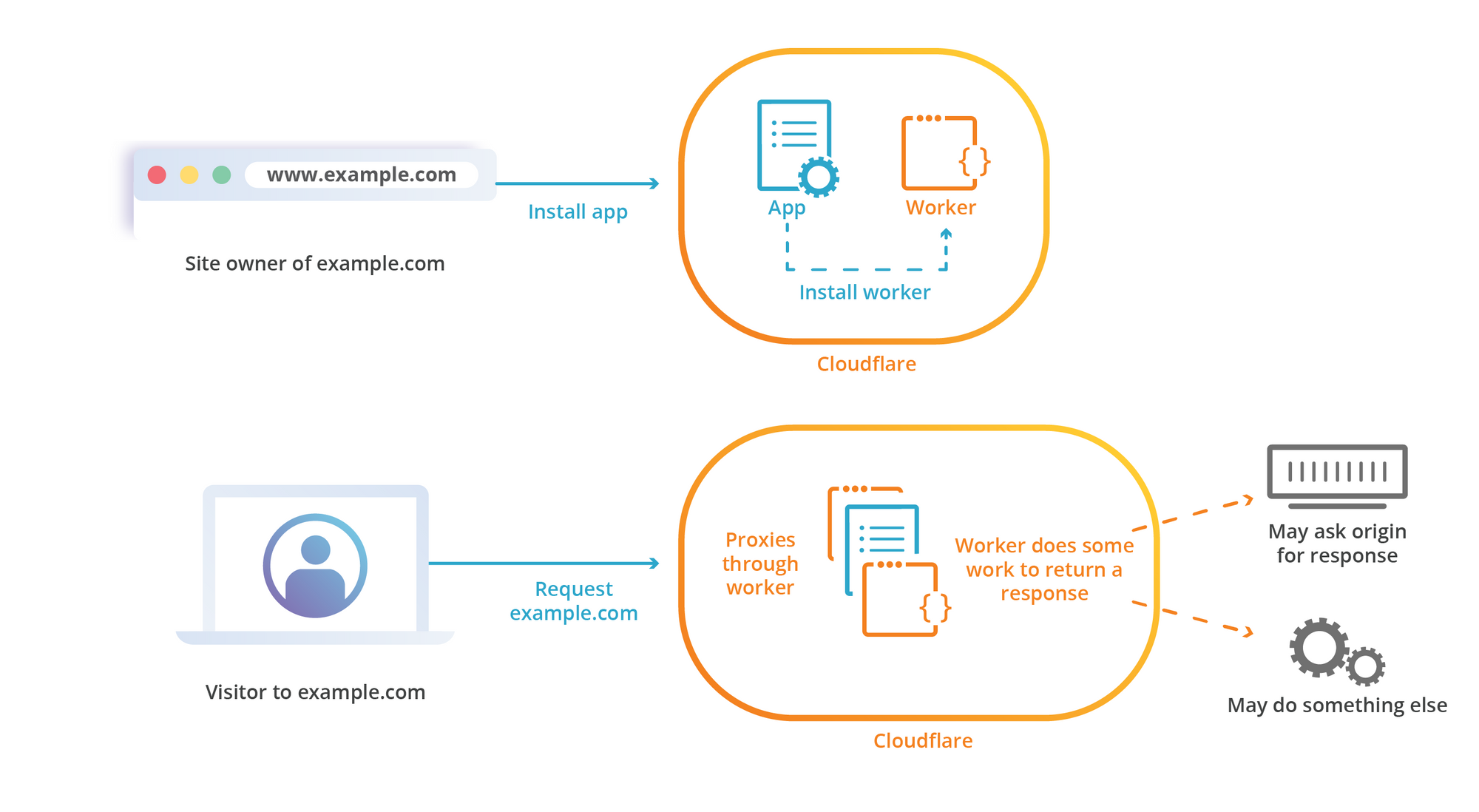
Since its inception, Cloudflare Apps has made it possible for website owners to install a tool or a service directly onto a domain they have that lives on the Cloudflare network. As an App Developer, you’ve had the ability to deliver your product by modifying traffic and content of a user’s website using a combination of Javascript, HTML, CSS injection with the ability to modify Cloudflare features such as DNS.
Today we are announcing a public beta for our Cloudflare Apps with Workers! If you are a developer who has been using Workers or Cloudflare Apps, this is a significant step forward to bring together our server-less platform allowing you the next wave of innovation in the Cloudflare marketplace.
Wait! Yet more Workers news? It’s already been a furious year of releases for Workers, from our GA launch in February to numerous improvements including the beta of Cache API and a flurry of updates during Cloudflare’s Birthday week, where we made available our K/V Storage and WASM support. With this beta, developers can now package all Workers capabilities, deliver new worker-powered experiences to Cloudflare customers all within a few clicks via Cloudflare Apps.
Now your Apps can be more powerful, Continue reading
Announcing SSH Access through Cloudflare

We held our annual Cloudflare Retreat last week. Over 750 team members from nearly a dozen offices spent three days learning, bonding and some of them got to smash a VPN piñata on stage with a baseball bat. Yes, you read that right.
The latest feature added to Cloudflare Access let us celebrate the replacement of our clunky VPN with a faster, safer way to reach our internal applications. You can now place applications that require SSH connections, like your source control repository, behind Cloudflare Access. We’re excited to release that same feature so that your team can also destroy your own VPN (piñata not included).

How we smashed our VPN
We built Access to replace our corporate VPN. We started with browser-based applications, moved to CLI operations, and then began adding a growing list of single sign-on integrations. Our teammates added single sign-on support to the Cloudflare dashboard by combining Access and our serverless product, Workers. We improved the daily workflow of every team member each time we moved another application behind Access. However, SSH connections held us back. Whenever we needed to push code or review a pull request, we had to fall back to our Continue reading
Bandwidth Alliance Partners – Exciting Choices
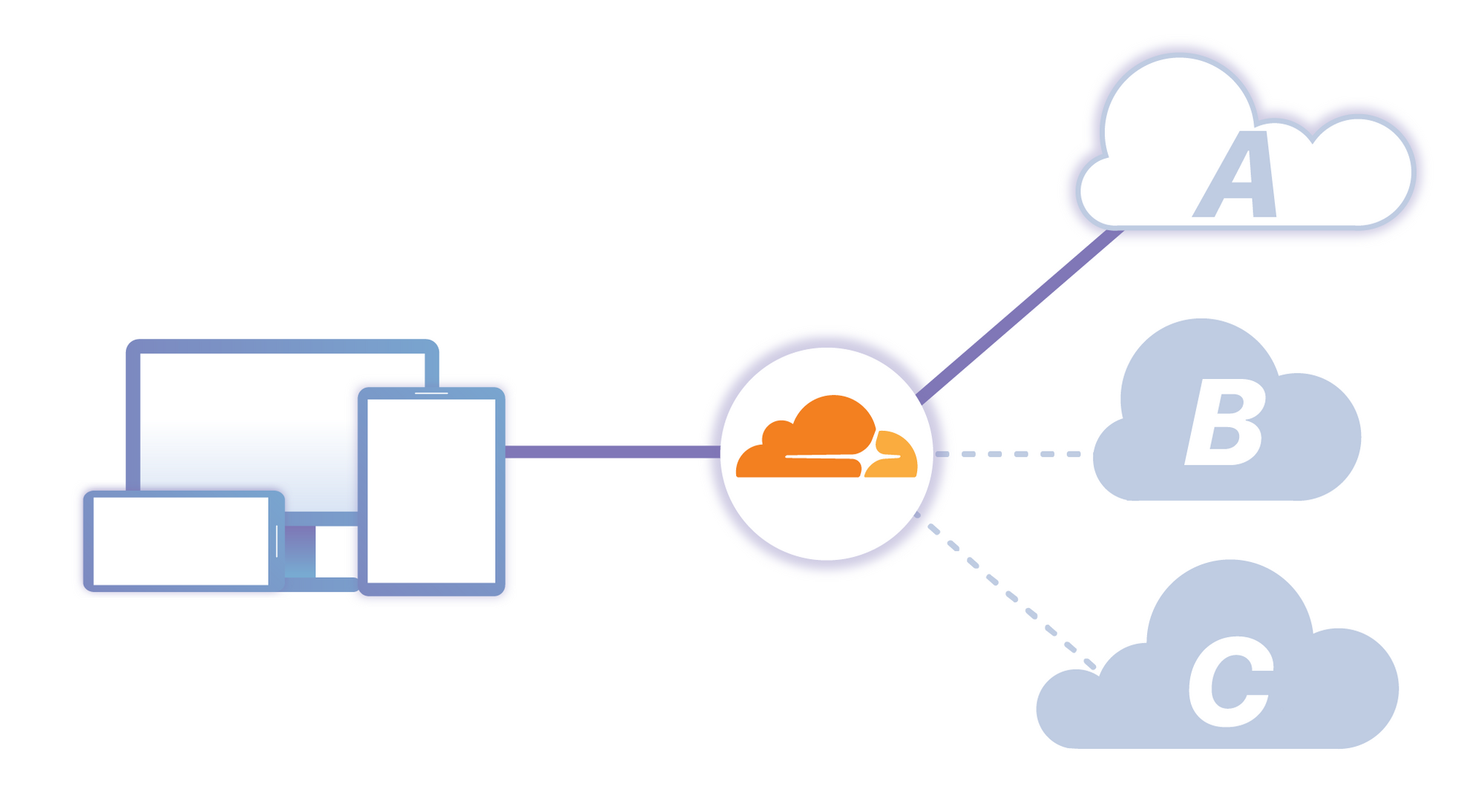

We are tremendously excited about the value our Bandwidth Alliance partner ecosystem adds to our customers. We’re on a mission to help make the internet a better place; and ensuring everyone can access cloud resources at zero-egress rates supports that mission in many ways. It’s an easy way for our clients to build modern, cloud-centric applications without the design constraint and financial burden of egress fees.
The cloudflare bandwidth alliance partner landscape continues to grow, and incorporate a diverse group of partners, with today’s second wave announcement. With over a dozen different partners, the range of choices can quickly become overwhelming. And, while these are all high-quality platforms which we are happy to recommend to our clients - their important differences will help determine the best fit for you, the customer.
In this post, I’ll lay out some of Cloudflare’s approach to this solution design question through the lens of a large client we recently worked with. We apply this approach across our full range of products and services, including many use cases far different from the Storage need we’ll dig into in this post. I hope that this can help all of our clients, or anyone else interested, mirror Continue reading