Down the Rabbit Hole: The Making of Cloudflare Warp

In the real world, tunnels are often carved out from the mass of something bigger - a hill, the ground, but also man-made structures.
 CC BY-SA 2.0 image by Matt Brown
CC BY-SA 2.0 image by Matt Brown
In an abstract sense Cloudflare Warp is similar; its connection strategy punches a hole through firewalls and NAT, and provides easy and secure passage for HTTP traffic to your origin. But the technical reality is a bit more interesting than this strained metaphor invoked by the name of similar predecessor technologies like GRE tunnels.
Relics
Generic Routing Encapsulation or GRE is a well-supported standard, commonly used to join two networks together over the public Internet, and by some CDNs to shield an origin from DDoS attacks. It forms the basis of the legacy VPN protocol PPTP.
Establishing a GRE tunnel requires configuring both ends of the tunnel to accept the other end’s packets and deciding which IP ranges should be routed through the tunnel. With this in place, an IP packet destined for any address in the configured range will be encapsulated within a GRE packet. The GRE packet is delivered directly to the other end of the tunnel, which removes the encapsulation and forwards the original Continue reading
Introducing Cloudflare Stream: Fixing the Streaming Video Market

Cloudflare turns seven years old today. We launched on September 27, 2010.
It was only a few days after our launch that we got our first request to support video streaming. Yet, until today, we'd avoided it.
Why? Simply put: the video streaming market is screwed up. While there's a lot of money spent on video, there are only really about 1,000 customers that do any meaningful level of streaming.
This is in large part because it's technically far too complicated. If you want to move beyond just uploading your videos to a consumer service like YouTube, then you have to use at least three different services. You need someone to encode your video into a streamable format, you need someone else to act as the content delivery network delivering the bytes, and you need someone else still to provide the player code that runs on the client device. Further, since video encoding standards keep evolving and vary across generations of devices, it becomes challenging to ensure a consistently high quality experience for all visitors.
And if that sounds like a technical mess, the business side is even worse. Encoding companies charge based on CPU usage, which is driven by Continue reading
How Cloudflare Streams

Every day, close to 1 billion people watch video through Cloudflare. That’s 100 petabytes of video every month. Last year, video made up 73% of all internet traffic, which is why earlier today we announced Cloudflare Stream, an end to end video solution designed to bring instant video to any device and network connection. Here’s how Stream works to optimize video upload, encoding and delivery.
Uploads
Using Cloudflare Stream starts with a call to the Stream API to /upload a video.
HTTP does not by default provide a reliable upload mechanism for large files, which can make it tricky to upload large media content like high quality video. If there’s any latency in the network connection, a timeout can cancel the entire upload and require the client to start over.
We use an open source upload protocol called Tus which allows for resumable uploads where the upload previously failed. Tus does this by splitting the download into manageable chunks and tracking completed chunks on the server.
Encodes
Video files are containers that hold the video file, the audio track, and some metadata. The video file is compressed by a codec. The codec is a compression algorithm for encoding video Continue reading
Geo Key Manager: How It Works
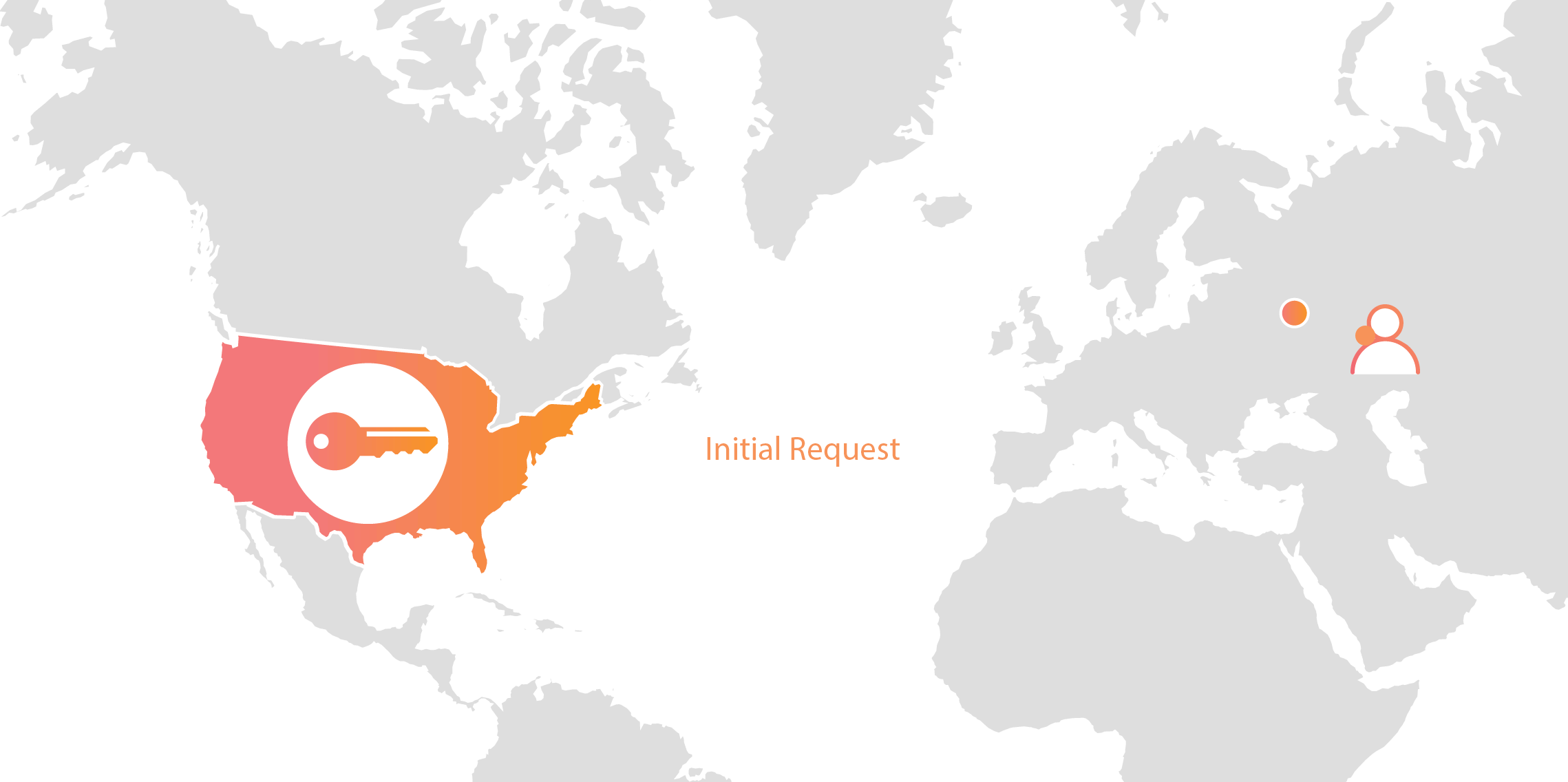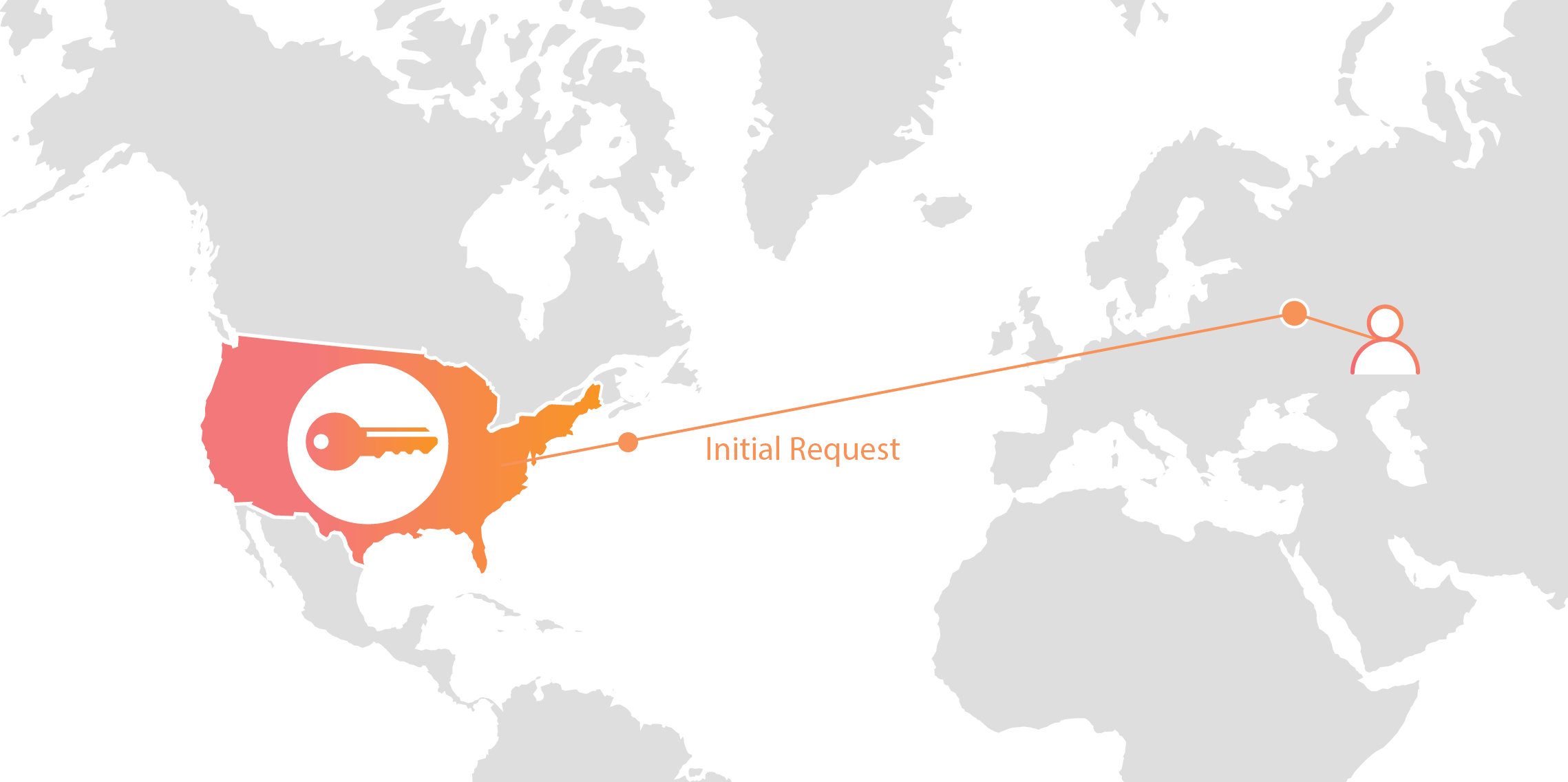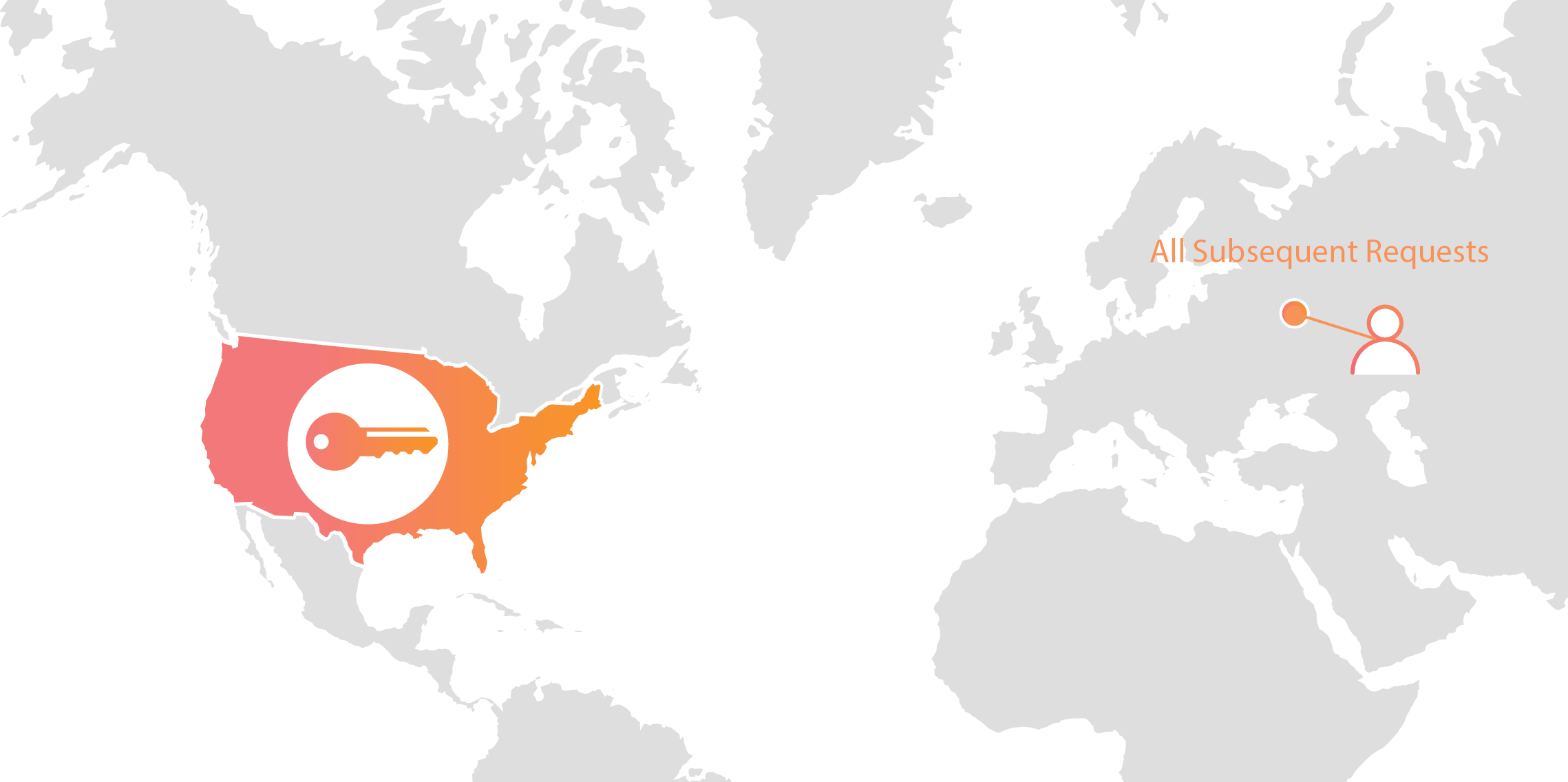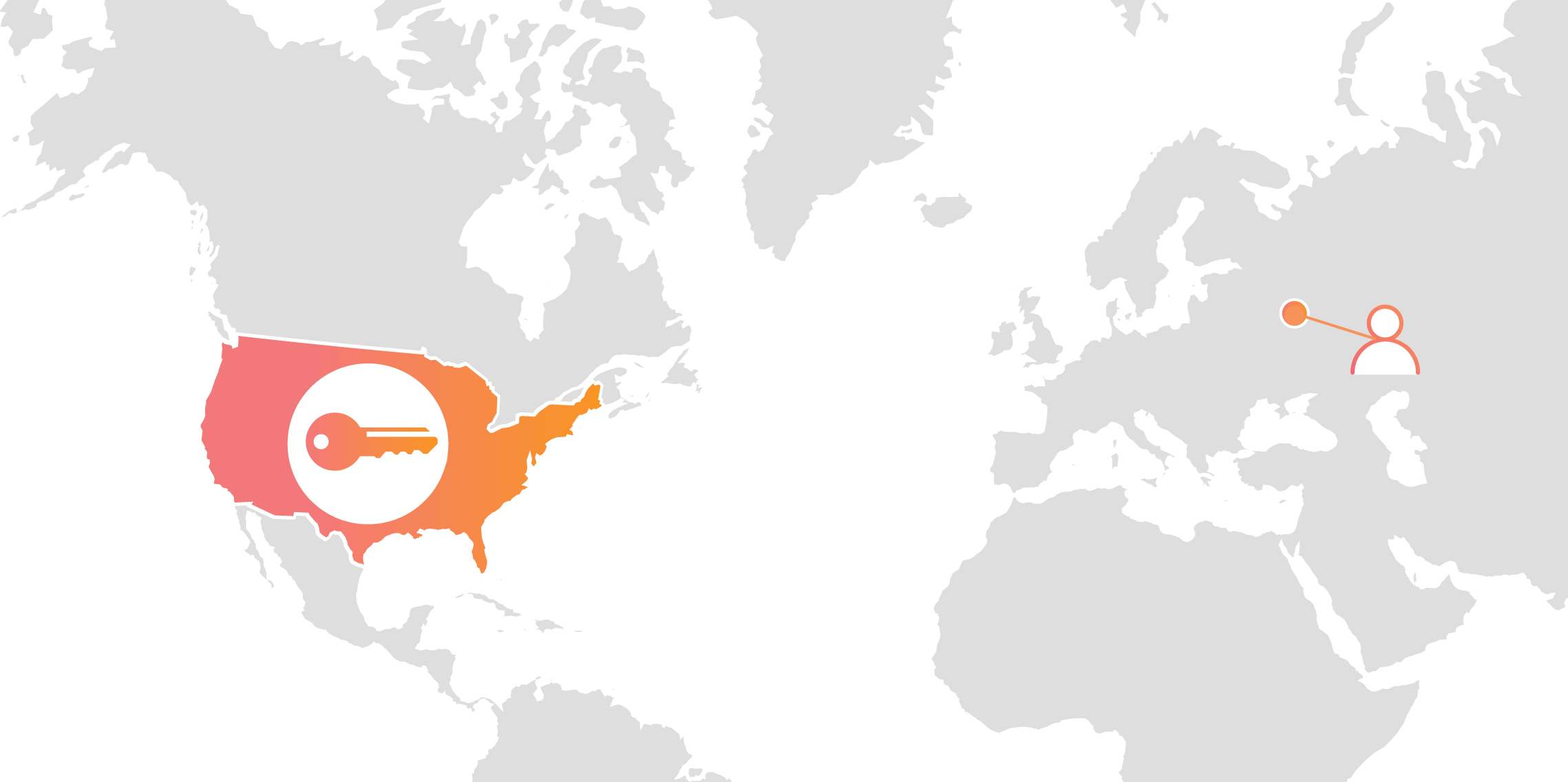
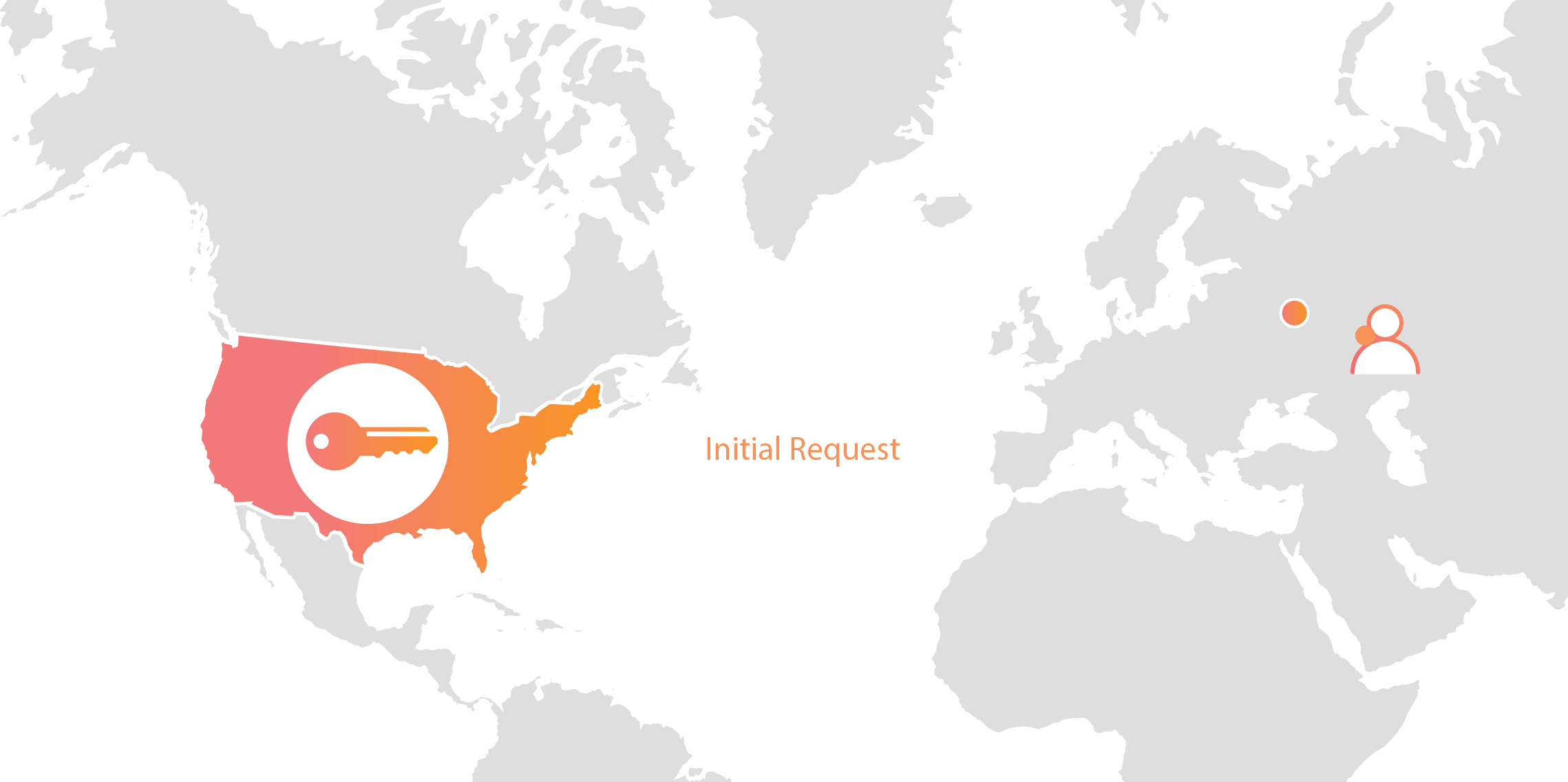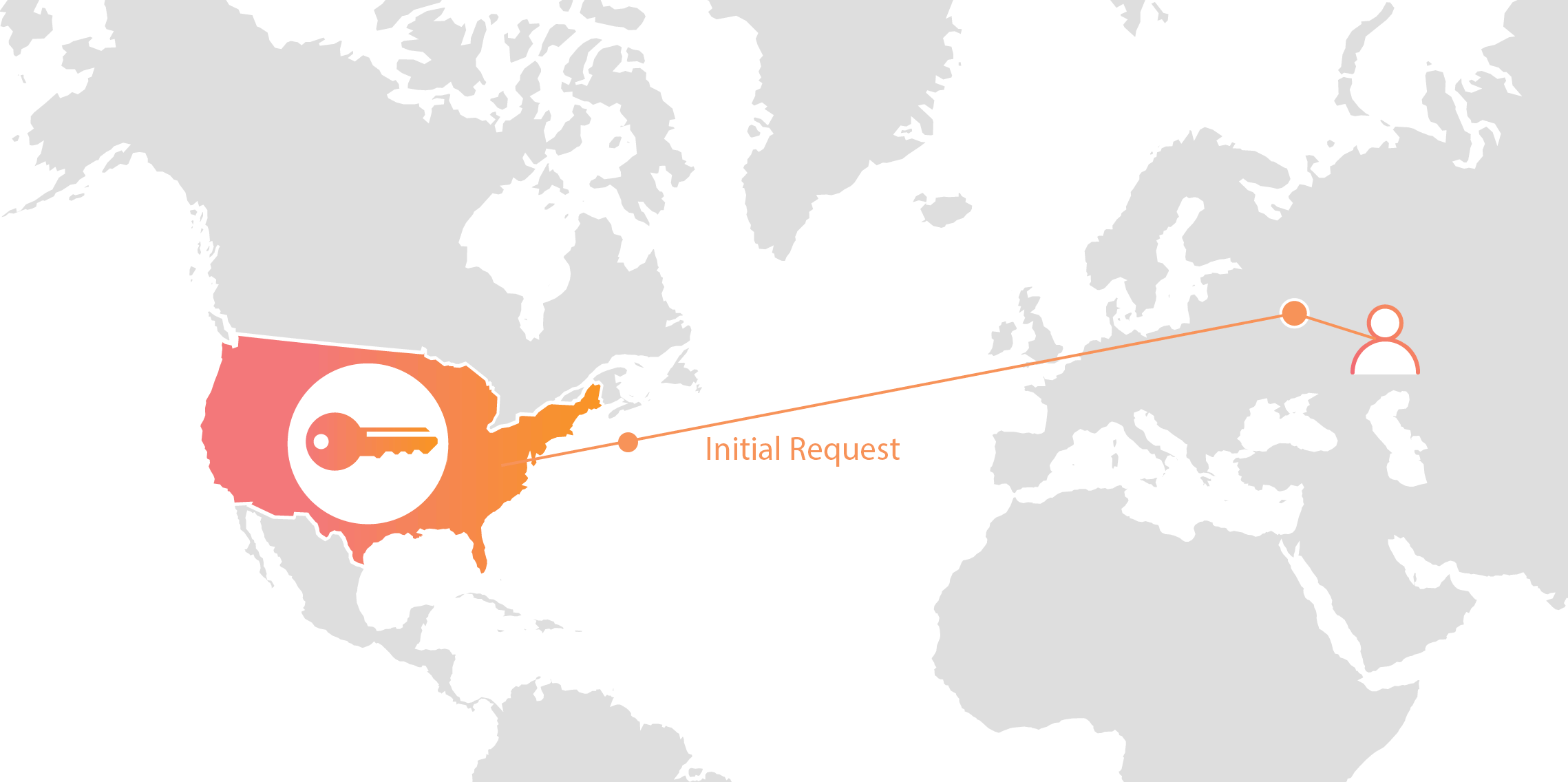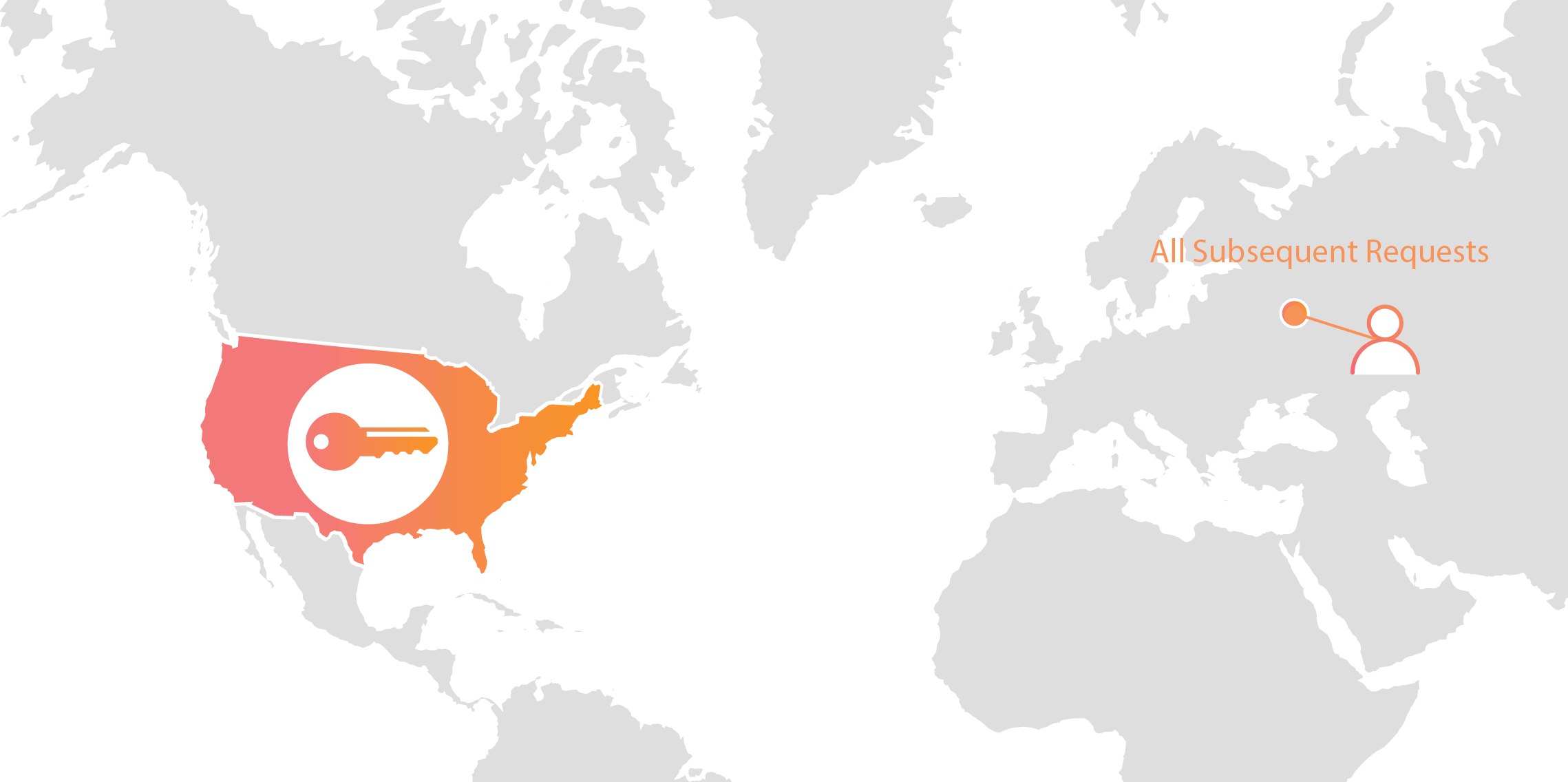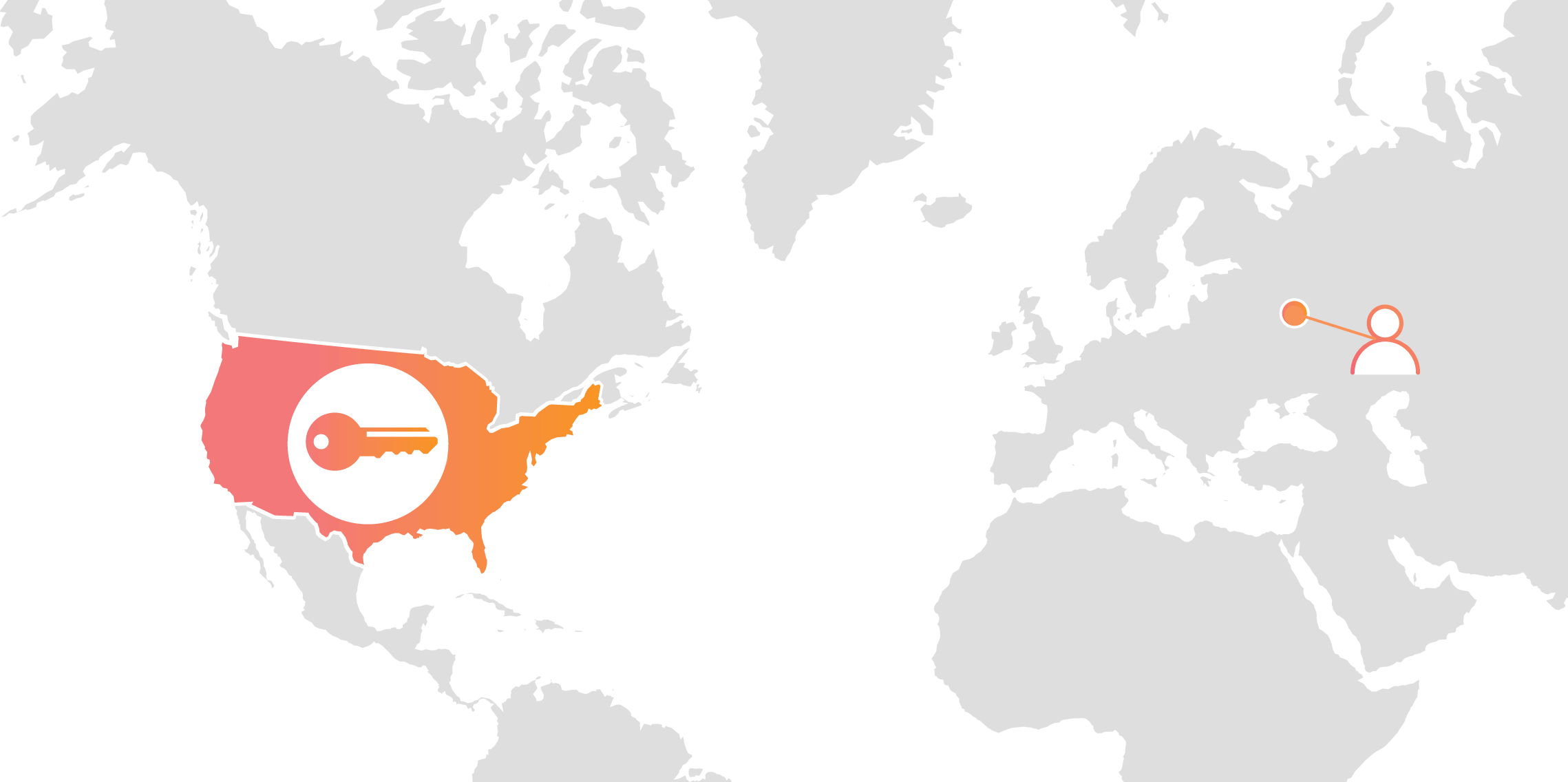
Today we announced Geo Key Manager, a feature that gives customers unprecedented control over where their private keys are stored when uploaded to Cloudflare. This feature builds on a previous Cloudflare innovation called Keyless SSL and a novel cryptographic access control mechanism based on both identity-based encryption and broadcast encryption. In this post we’ll explain the technical details of this feature, the first of its kind in the industry, and how Cloudflare leveraged its existing network and technologies to build it.
Keys in different area codes
Cloudflare launched Keyless SSL three years ago to wide acclaim. With Keyless SSL, customers are able to take advantage of the full benefits of Cloudflare’s network while keeping their HTTPS private keys inside their own infrastructure. Keyless SSL has been popular with customers in industries with regulations around the control of access to private keys, such as the financial industry. Keyless SSL adoption has been slower outside these regulated industries, partly because it requires customers to run custom software (the key server) inside their infrastructure.
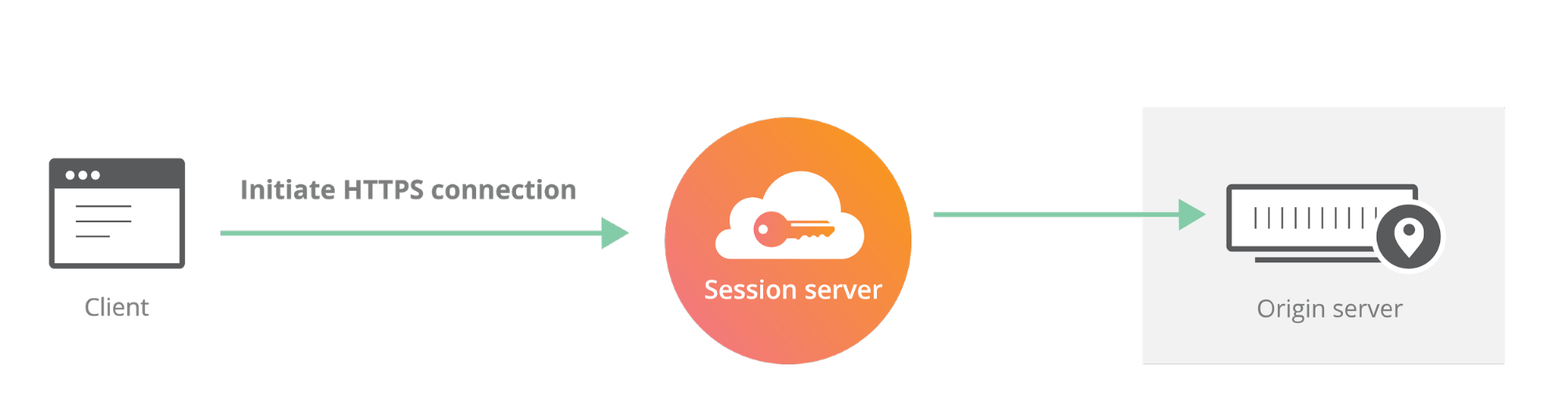
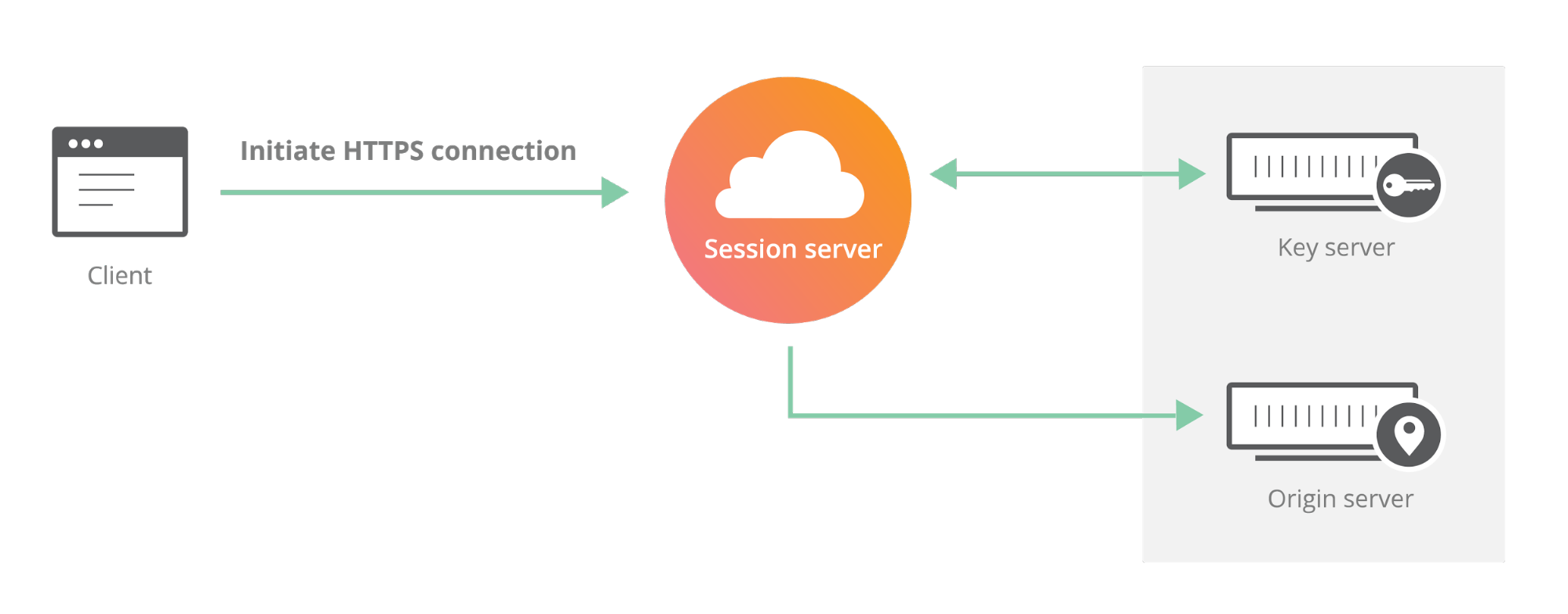
One of the motivating use cases for Keyless SSL was the expectation that customers may not trust a third party like Cloudflare with their Continue reading
Introducing the Cloudflare Geo Key Manager
Cloudflare’s customers recognize that they need to protect the confidentiality and integrity of communications with their web visitors. The widely accepted solution to this problem is to use the SSL/TLS protocol to establish an encrypted HTTPS session, over which secure requests can then be sent. Eavesdropping is protected against as only those who have access to the “private key” can legitimately identify themselves to browsers and decrypt encrypted requests.
Today, more than half of all traffic on the web uses HTTPS—but this was not always the case. In the early days of SSL, the protocol was viewed as slow as each encrypted request required two round trips between the user’s browser and web server. Companies like Cloudflare solved this problem by putting web servers close to end users and utilizing session resumption to eliminate those round trips for all but the very first request.
Expanding footprint meets geopolitical concerns
As Internet adoption grew around the world, with companies increasingly serving global and more remote audiences, providers like Cloudflare had to continue expanding their physical footprint to keep up with demand. As of the date this blog post was published, Cloudflare has data centers in over 55 countries, and we continue Continue reading
Unmetered Mitigation: DDoS Protection Without Limits
This is the week of Cloudflare's seventh birthday. It's become a tradition for us to announce a series of products each day of this week and bring major new benefits to our customers. We're beginning with one I'm especially proud of: Unmetered Mitigation.
 CC BY-SA 2.0 image by Vassilis
CC BY-SA 2.0 image by Vassilis
Cloudflare runs one of the largest networks in the world. One of our key services is DDoS mitigation and we deflect a new DDoS attack aimed at our customers every three minutes. We do this with over 15 terabits per second of DDoS mitigation capacity. That's more than the publicly announced capacity of every other DDoS mitigation service we're aware of combined. And we're continuing to invest in our network to expand capacity at an accelerating rate.
Surge Pricing
Virtually every Cloudflare competitor will send you a bigger bill if you are unlucky enough to get targeted by an attack. We've seen examples of small businesses that survive massive attacks to then be crippled by the bills other DDoS mitigation vendors sent them. From the beginning of Cloudflare's history, it never felt right that you should have to pay more if you came under an attack. That feels barely a Continue reading
No Scrubs: The Architecture That Made Unmetered Mitigation Possible
When building a DDoS mitigation service it’s incredibly tempting to think that the solution is scrubbing centers or scrubbing servers. I, too, thought that was a good idea in the beginning, but experience has shown that there are serious pitfalls to this approach.
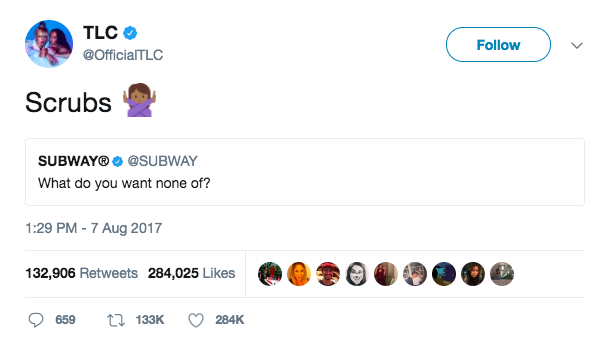
A scrubbing server is a dedicated machine that receives all network traffic destined for an IP address and attempts to filter good traffic from bad. Ideally, the scrubbing server will only forward non-DDoS packets to the Internet application being attacked. A scrubbing center is a dedicated location filled with scrubbing servers.
Three Problems With Scrubbers
The three most pressing problems with scrubbing are: bandwidth, cost, knowledge.
The bandwidth problem is easy to see. As DDoS attacks have scaled to >1Tbps having that much network capacity available is problematic. Provisioning and maintaining multiple-Tbps of bandwidth for DDoS mitigation is expensive and complicated. And it needs to be located in the right place on the Internet to receive and absorb an attack. If it’s not then attack traffic will need to be received at one location, scrubbed, and then clean traffic forwarded to the real server: that can introduce enormous delays with a limited number of locations.
Meet Gatebot – a bot that allows us to sleep
In the past, we’ve spoken about how Cloudflare is architected to sustain the largest DDoS attacks. During traffic surges we spread the traffic across a very large number of edge servers. This architecture allows us to avoid having a single choke point because the traffic gets distributed externally across multiple datacenters and internally across multiple servers. We do that by employing Anycast and ECMP.

We don't use separate scrubbing boxes or specialized hardware - every one of our edge servers can perform advanced traffic filtering if the need arises. This allows us to scale up our DDoS capacity as we grow. Each of the new servers we add to our datacenters increases our maximum theoretical DDoS “scrubbing” power. It also scales down nicely - in smaller datacenters we don't have to overinvest in expensive dedicated hardware.
During normal operations our attitude to attacks is rather pragmatic. Since the inbound traffic is distributed across hundreds of servers we can survive periodic spikes and small attacks without doing anything. Vanilla Linux is remarkably resilient against unexpected network events. This is especially true since kernel 4.4 when the performance of SYN cookies was greatly improved.
But at some point, malicious traffic volume Continue reading
The History of Email

This was adapted from a post which originally appeared on the Eager blog. Eager has now become the new Cloudflare Apps.
QWERTYUIOP
— Text of the first email ever sent, 1971
The ARPANET (a precursor to the Internet) was created “to help maintain U.S. technological superiority and guard against unforeseen technological advances by potential adversaries,” in other words, to avert the next Sputnik. Its purpose was to allow scientists to share the products of their work and to make it more likely that the work of any one team could potentially be somewhat usable by others. One thing which was not considered particularly valuable was allowing these scientists to communicate using this network. People were already perfectly capable of communicating by phone, letter, and in-person meeting. The purpose of a computer was to do massive computation, to augment our memories and empower our minds.
Surely we didn’t need a computer, this behemoth of technology and innovation, just to talk to each other.

The history of computing moves from massive data processing mainframes, to time sharing where many people share one computer, to the diverse collection of personal computing devices Continue reading
A New API Binding: cloudflare-php
Back in May last year, one of my colleagues blogged about the introduction of our Python binding for the Cloudflare API and drew reference to our other bindings in Go and Node. Today we are complimenting this range by introducing a new official binding, this time in PHP.
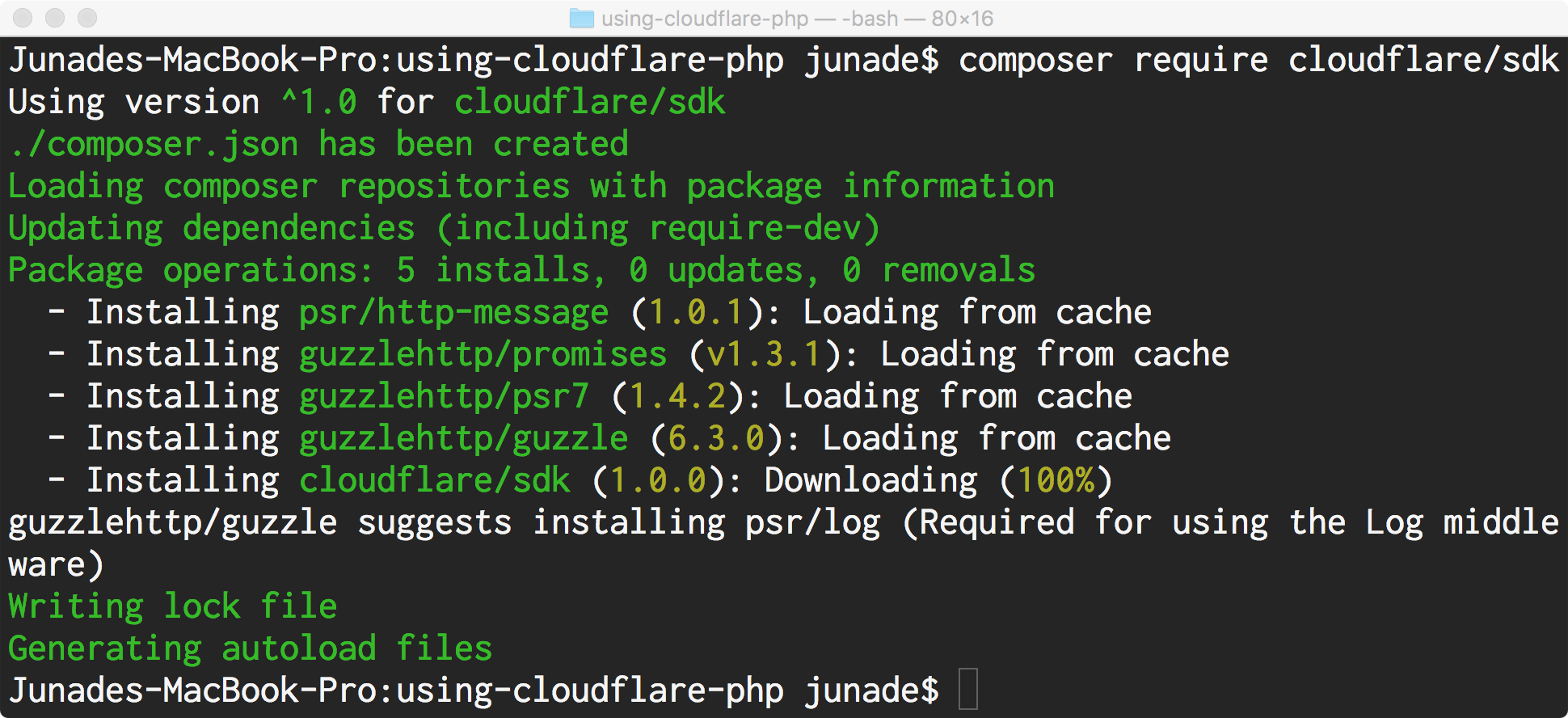
This binding is available via Packagist as cloudflare/sdk, you can install it using Composer simply by running composer require cloudflare/sdk. We have documented various use-cases in our "Cloudflare PHP API Binding" KB article to help you get started.
Alternatively should you wish to help contribute, or just give us a star on GitHub, feel free to browse to the cloudflare-php source code.
PHP is a controversial language, and there is no doubt there are elements of bad design within the language (as is the case with many other languages). However, love it or hate it, PHP is a language of high adoption; as of September 2017 W3Techs report that PHP is used by 82.8% of all the websites whose server-side programming language is known. In creating this binding the question clearly wasn't on the merits of PHP, but whether we wanted to help drive improvements to the developer experience for Continue reading
Project Jengo Strikes Its First Targets (and Looks for More)
 Jango Fett by Brickset (Flickr)
Jango Fett by Brickset (Flickr)
When Blackbird Tech, a notorious patent troll, sued us earlier this year for patent infringement, we discovered quickly that the folks at Blackbird were engaged in what appeared to be the broad and unsubstantiated assertion of patents -- filing about 115 lawsuits in less than 3 years, and have not yet won a single one of those cases on the merits in court. Cloudflare felt an appropriate response would be to review all of Blackbird Tech’s patents, not just the one it asserted against Cloudflare, to determine if they are invalid or should be limited in scope. We enlisted your help in this endeavor by placing a $50,000 bounty on prior art that proves the Blackbird Tech patents are invalid or overbroad, an effort we dubbed Project Jengo.
Since its inception, Project Jengo has doubled in size and provided us with a good amount of high quality prior art submissions. We have received more than 230 submissions so far, and have only just begun to scratch the surface. We have already come across a number of standouts that appear to be strong contenders for invalidating many of the Blackbird Tech patents. This means it is Continue reading
#FuerzaMexico: A way to help Mexico Earthquake victims

 Photo Credit: United Nations Photo (Flickr)
Photo Credit: United Nations Photo (Flickr)
On September 19, 1985 Mexico City was hit with the most damaging earthquake in its history. Yesterday -exactly 32 years later- Mexico’s capital and neighbouring areas were hit again by a large earthquake that caused significant damage. While the scale of the destruction is still being assessed, countless people passed away and the lives of many have been disrupted. Today, many heroes are on the streets focusing on recovery and relief.
We at Cloudflare want to make it easy for people to help out those affected in central Mexico. The Mexico Earthquake app will allow visitors to your site to donate to one of the charities helping those impacted.
The Mexico Earthquake App takes two clicks to install and requires no code change. The charities listed are two well respected organizations that are on the ground helping people now.
If you wanted to add your own custom list of charities for disaster relief or other causes, feel free to fork the source of this app and make your own.
#FuerzaMéxico: Una manera de apoyar a los damnificados del SismoMX
El 19 de septiembre de 1985 la Ciudad de México fue afectada por Continue reading
Cloudflare and Google Offer App Developers $100,000 in Cloud Platform Credits

When Cloudflare started, our company needed two things: an initial group of users, and the finances to fund our development. We know most developers face the same issues. The Cloudflare Apps Platform solves the first problem by allowing third parties to develop applications that can be delivered across Cloudflare's edge network to any of the six million sites powered by Cloudflare. The Cloudflare Developer Fund alleviates the second by giving developers the financial support they need to fund their company. Today, we are excited to announce another initiative that will make it possible for developers to make their app dreams a reality.
Cloudflare and Google Cloud are working together to offer developers the resources needed to quickly launch and scale Cloudflare Apps. This partnership will give any Cloudflare Apps developer the chance to access a wide range of benefits including $3k - $100k of Google Cloud Platform (GCP) for one year at no cost. Some startups will also be eligible for 24/7 technical support, and access to GCP’s technical solutions team. This supports a core belief of the Cloudflare Apps initiative: we want developers to focus on building great Apps, not worry about paying for infrastructure. Hundreds of startups have Continue reading
Truth Lives in the Open: Lessons from Wikipedia
Victoria Coleman, CTO, Wikimedia Foundation
Moderator: Michelle Zatlyn, Co-Founder & COO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MZ: What is the Wikimedia Foundation?
VC: We pride ourselves in aiming to make available information broadly
not-for-profit
We’re the 5th most visited site on the planet.
We are the guardians of the project. There are 12 projects that we support, Wikipedia is the most prominent but there are others that will be just as influential in the next 5 years: e.g. Wikidata.
299 languages
Let’s also talk about the things that we don’t do: we don’t do editing. We edit as community members but not as members of the foundation.
We don’t monetize our users, content, or presence. We are completely funded by donations, with an average donation of $15.
MZ: If your mission is to help bring free education to all, getting to everyone can be hard. So how do you get access to people in hard-to-reach areas?
VC: It’s definitely a challenge. We built this movement primarily in NA and EU, but our vision goes beyond that. We started doing some critically refined and focused research in Brazil, Mexico, Nigeria.
Trying to understand what global communities need in other Continue reading
Will Data Destroy Democracy?
Lawrence Lessig, Roy L. Furman Professor of Law and Leadership, Harvard Law School and Darren Bolding, CTO, Cambridge Analytica
Moderator: Matthew Prince, Co-Founder & CEO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MP: If there’s one person responsible for the Trump presidency, it seems there is a compelling argument that that might be you.
DB: I very much disagree with that.
MP: How does Cambridge Analytica work, and how did the Trump campaign use it to win the presidency?
DB: we take that data and match it up with lists of voters, and combine that data science to come up with ideas about you who might want to sell a product to, or in teh case of politics, this is this person's’ propensity to vote, this is the candidate they are likely most interested in. WE also do all the digital advertising. By combining data with digital advertising, we have lots of power.
MP: so you don’t want to take credit for having won the election; but the campaign's use of data and targeting was an important factor in the election.
DB: Yes, and what Cambridge did was basically a great turnaround story.
MP: larry you ran a presidential Continue reading
As Seen on TV
Chris Cantwell, Co-Creator and Show Runner, Halt & Catch Fire
Moderator: John Graham-Cumming, CTO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
CC: first off, we have very low ratings! The story came from my father who worked in computers in the early 80s in dallas; later in california. The dynamic between those characters was influenced by my dad.
This was largely a story about reverse engineering. The underdog story was interesting: not Bill Gates, not Silicon Valley, but a different story about the computer world.
JGC: and you managed to do 4 seasons
CC: In four seasons we go from ‘83 to ‘94; we cover everything from small networks to building of internet backbone, rise in search and www
JGC: I watched it before I came; it gave me some bad memories because there were AOL disks
CC: We have an incredible prop team. Some comes from RI computer museum; i have to ask our prop master, he might have manufactured them from images online.
JGC: This is a show about tech but also about money; these people are trying to build companies. The same people trying again and again. Is that a metaphor for recycling something?
CC: Yes, i Continue reading
Private Companies, Public Squares
Daphne Keller, Director, Stanford Center for Internet & Society, and Lee Rowland, Senior Staff Attorney, ACLU Speech, Privacy & Technology Project
Moderator: Matthew Prince, Co-Founder & CEO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MP: Technology and law seem like they are colliding more and more. Tech companies are being asked to regulate content. For a largely non-lawyer audience, give us some foundations about basic rules when you have content on your network?
LR: Communications 2.0 makes the 1st amendment almost quaint. The vast majority of speech that we exchange happens online. When it is hosted by private companies, the 1st amendment doesn’t constrain it. So this is a space governed by norms and individual choices of people like Matthew. In the wake of Cloudflare's decision to take down the Daily Stormer, Matthew penned a piece saying it’s scary that we have this power, and I exercised it. We have a completely unaccountable private medium of communication.
MP: There are shields for companies for this; What is intermediary liability and why is this a position at Google/Stanford?
DK: No one knows what it means; it’s a set of laws that tell platforms when they have to take down Continue reading
Betting on Blockchain
Juan Benet, Founder, Protocol Labs, and Jill Carlson, GM, Tezos Foundation
Moderator: Jen Taylor, Head of Product, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
JT: Tell us about what BlockChain is
JC: Going back to 2008, advent of blockchain came with bitcoin white paper.
The word Blockchain wasn’t mentioned at that point, but that was the advent of this tech.
What it solved was niche problem called double spend problem. Creation of digital cash.
What you see in a bank account isn’t digital cash. The problem in cryptography was how to create digital cash that doesn't rely on 3rd party intermediary. This is what Bitcoin created.
JB: Blockchain packs in lots of stuff: useful as brand. Like internet/web in early 90s, the meaning is fuzzy.
Properties that all of these apps have in common:
Academic definition: A blockchain is an indelible chain of blocks; once you insert information into one of them it remains.
Marketing definition: many applications have been developed over last few years, all have to do with public verifiability. Reliance on cryptographic methods to achieve goals on clearing payments and the ability to check and verify.
Across the board, removing 3rd parties from equation. Establishing publicly verifiable Continue reading
The New Breed of Patent Trolls
Lee Cheng, President & Co-CLO, Symmetry IP LLC, and Vera Ranieri, Staff Attorney, Electronic Frontier Foundation
Moderator: Doug Kramer, General Counsel, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
DK: Patent--IP issues and challenges are accelerating important supreme court cases. there’s also a flurry of legislative activity about patents. Good idea to talk about this topic: where is this going? How to push world in virtuous direction?
DK: current state of affairs. Vera: at the core is the patent itself, which is issued by and often adjudged by the patent office… is this where the problem lies?
VR: I like to blame everyone. How does someone get a patent in the first place? Someone comes up with an invention, patent attorney, documents it with opaque language, and files. The examiner then interprets the patent and searches for prior art, and says “I think this is what the patent owner is trying to claim.”
In the software space, it’s especially difficult. A lot of where inventing happens in software is right here, in businesses. People have a problem and find a solution by developing software. They don’t patent and publish.
Patent office tends to focus on patents.
DK: Talk about the Continue reading
If I Knew Then What I Know Now: Tales from the Early Internet
Paul Mockapetris, Inventor, DNS, and David Conrad, CTO, ICANN
Moderator: Matthew Prince, Co-Founder & CEO, Cloudflare
 Photo by Cloudflare Staff
Photo by Cloudflare Staff
MP: You guys wrote all this stuff; why is the internet so broken?
PM: People complain about security flaws, but there is no security in original design of dns. I think of it that we haven’t had the right investment in rebuilding the infrastructure.
Original stuff was only good for 10 years, but we’ve been using it for 30.
DC: The fact that we were able to get Packard from one machine to another in the early days was astonishing in itself.
MP: So what are you worried about in terms of Internet infrastructure that we aren’t even thinking about?
PM: i’m worried about the fact that a lot of places like the ITF are very incremental in their thinking, and that people aren’t willing to take the next big jump. E.g. hesitancy to adopt blockchain
Being able to experiment and try new stuff is important.
The idea that you can't change anything because it will affect the security and stability of the internet. we need to weigh benefits and risks or we will eventually die of Continue reading