Upcoming Cloudflare events: Berlin May 5-7, Austin & Portland May 11

Attending JS Conf EU, CSS Conf, or OSCON in the next couple of weeks? Live in Berlin or Austin or Portland? Come over and join Cloudflare devs in the area at our upcoming events.
 JS Conf EU 2016. Photo by Holger Blank.
JS Conf EU 2016. Photo by Holger Blank.
In Berlin? Attending JS Conf EU or CSS Conf EU?
If you’re at JS Conf EU (May 6-7) or CSS Conf EU (May 5):
- Be sure to make it to John Fawcett’s session, “Invisible Code: Building JavaScript Libraries For Non-Technical People.”
- Made a Cloudflare App? Drop by the Cloudflare Hacker Lounge to show me and I have a special gift for you.
- Started working on a Cloudflare App and have questions? Drop by the Cloudflare Hacker Lounge and get them answered.
Just happen to be in Berlin? Tweet @qiqing and @IcyApril to come hang out with us in person.
 Cloudflare Apps Preview. Visualize your app here.
Cloudflare Apps Preview. Visualize your app here.
In Austin? Attending OSCON?
Join the core developers of Cloudflare Apps for the inaugural Cloudflare meetup in Austin. It will feature an introduction by Zack Bloom (tech lead) to the new Cloudflare Apps including details of how apps get created, moderated, installed, and served to millions of users Continue reading
Introducing Cloudflare Orbit: A Private Network for IoT Devices

In October, we wrote about a 1.75M rps DDoS attack we mitigated on our network, launched by 52,467 unique IP’s, mostly hacked CCTV cameras.
We continued to see more IoT devices in DDoS attacks, and so we started to put together a security solution to protect the devices from becoming part of the botnet in the first place. Today we’re announcing it: Cloudflare Orbit.
PC-era security doesn’t work in IoT-era computing
As we talked to IoT companies, over and over again we heard the same thing. In the consumer electronics space, IoT manufacturers were telling us that they were shipping patches to their devices, but their end users didn’t always download and install them. (Reserve your judgment, how many times have you pressed ignore when your phone asked you to update its operating system?) In the industrial control, medical and automotive spaces, where devices are used in life-critical functions, we heard a different story. Even if someone wanted to apply a patch, it just wasn’t that easy. For example, even if the manager of a nuclear power plant wants to update software on their thermostats, shutting down operations long enough to do that means the update has to Continue reading
AES-CBC is going the way of the dodo
A little over a year ago, Nick Sullivan talked about the beginning of the end for AES-CBC cipher suites, following a plethora of attacks on this cipher mode.
Today we can safely confirm that this prediction is coming true, as for the first time ever the share of AES-CBC cipher suites on Cloudflare’s edge network dropped below that of ChaCha20-Poly1305 suites, and is fast approaching the 10% mark.
Over the course of the last six months, AES-CBC shed more than 33% of its “market” share, dropping from 20% to just 13.4%.
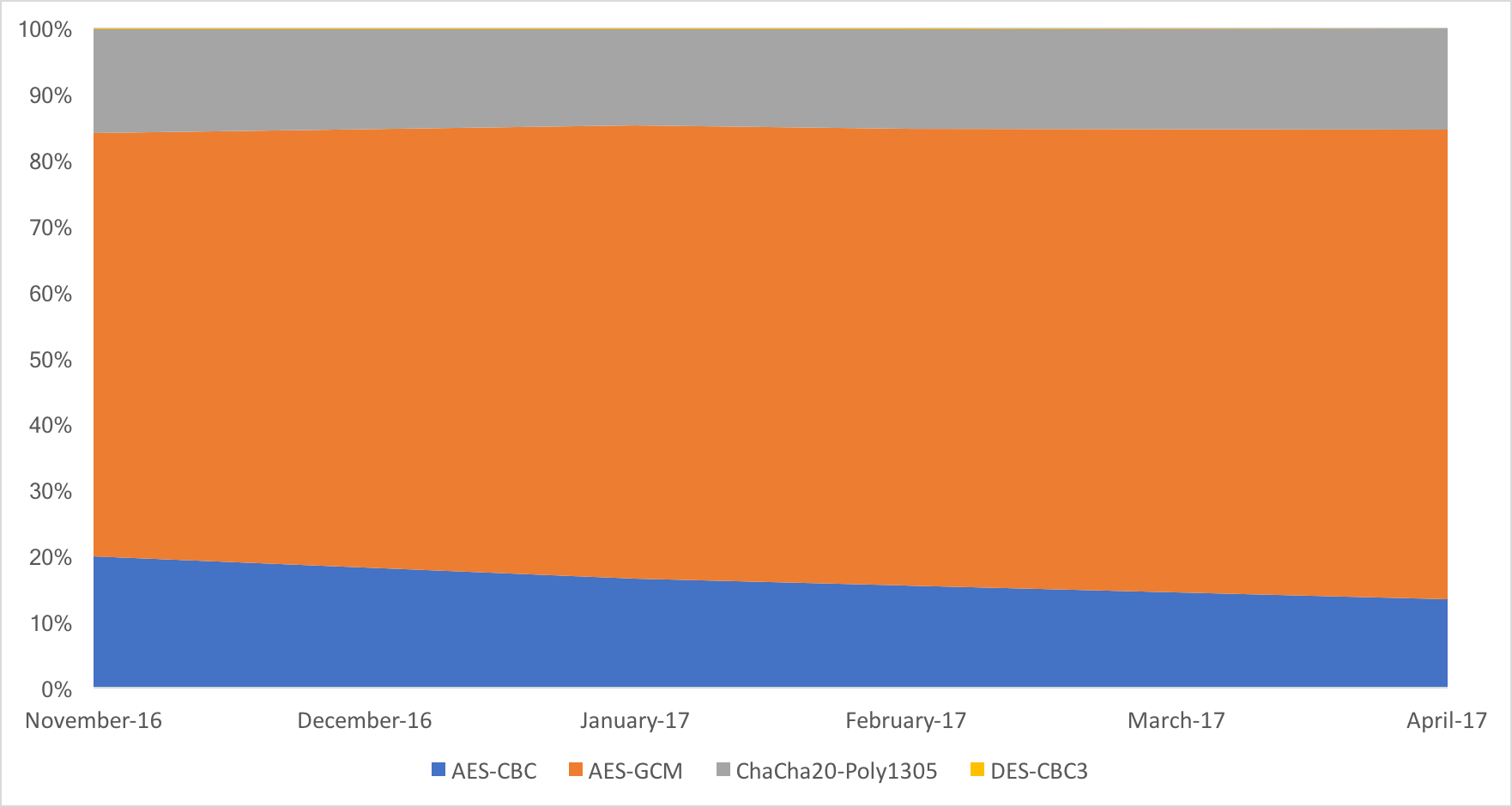
All of that share, went to AES-GCM, that currently encrypts over 71.2% of all connections. ChaCha20-Poly1305 is stable, with 15.3% of all connections opting for that cipher. Surprisingly 3DES is still around, with 0.1% of the connections.
The internal AES-CBC cipher suite breakdown as follows:
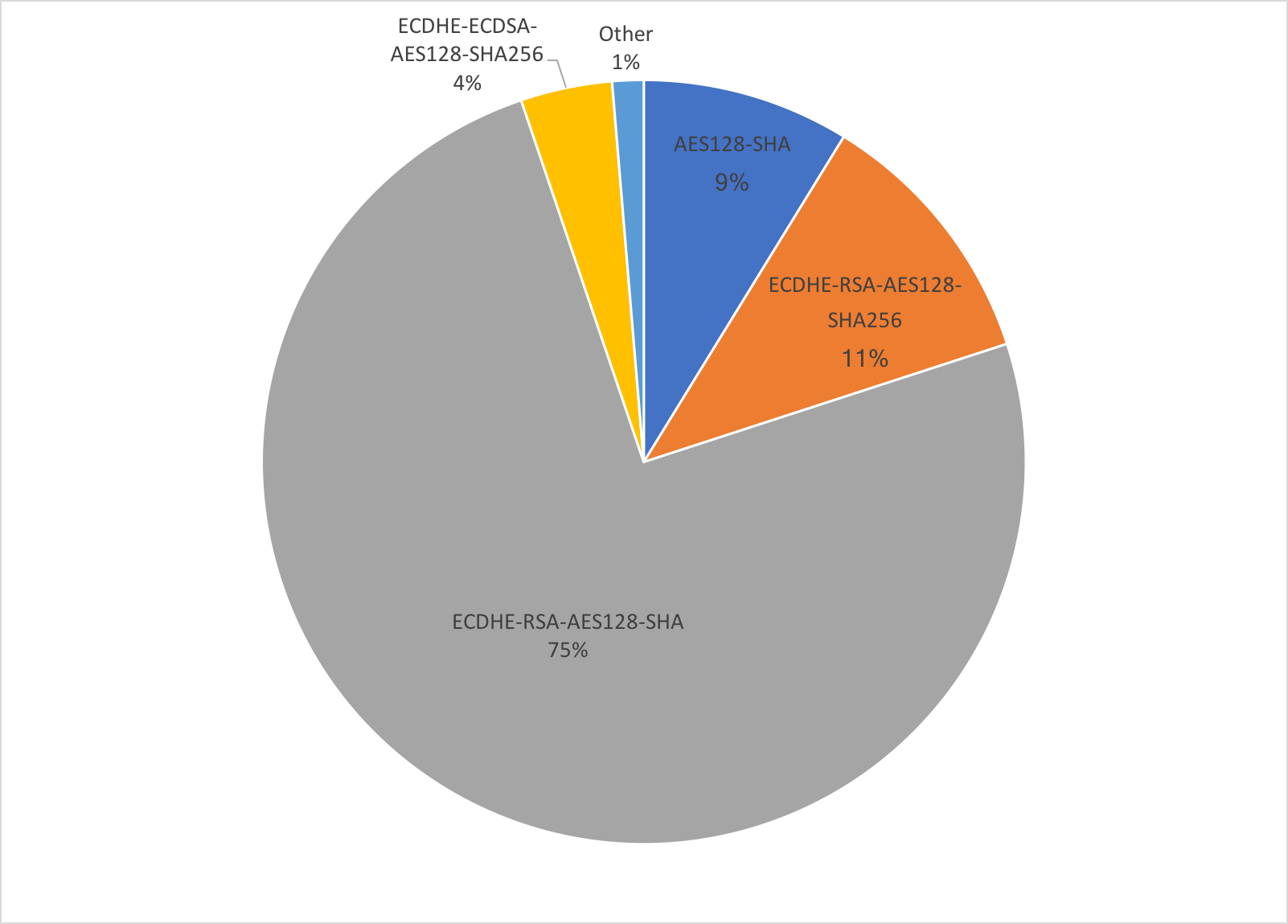
The majority of AES-CBC connections use ECDHE-RSA or RSA key exchange, and not ECDHE-ECDSA, which implies that we mostly deal with older clients.
RSA is also dying
In other good new, the use of ECDSA surpassed that of RSA at the beginning of the year. Currently more than 60% of all connections use Continue reading
Introducing SSL for SaaS
If you’re running a SaaS company, you know how important it is that your application is performant, highly available, and hardened against attack. Your customers—and your revenue stream—depend on it. Putting your app behind a solution such as Cloudflare is an obvious move for your own infrastructure, but how do you securely (and easily) extend these benefits to your customers?
If your customers interact with your app on your domain and don’t care about branding under their custom or “vanity” domain (or aren’t paying you for the ability to do so), the solution is straightforward: onboard your domain to Cloudflare and serve the app at either https://app.yourcompany.ltd or https://yourcustomer.yourcompany.ltd. But if your customers want to host your application, portal, content management solution, etc. on their own domain for improved SEO and discoverability, e.g., https://app.yourcustomer.site the solution is not so easy.
Easily extend the benefits of Cloudflare to your customers, one hostname at a time

Until today, your best bet was to ask them to CNAME over to your infrastructure, have them generate a private key and CSR, send the latter to a CA for signing, and then securely provide you with the Continue reading
Budapest (Hungary): Cloudflare Data Center #111
Hot on the heels of several recent data center additions in Yerevan, Quito, Rome, Kansas City, Belgrade, Curacao, Djibouti and Munich, we are delighted to announce our newest deployment in Budapest, making six million websites even faster and safer across Hungary.
Until today, Hungarian visitors to these Internet properties were principally served out of our Frankfurt data center 1,000 km away, or from Vienna. We are happy to further reduce their latency to over 8 million Internet users.

CC BY 2.0 image by Moyann Brenn
Beautiful Budapest
Budapest is one of the most beautiful cities in the world, with must-see sites such as Halászbástya (Fisherman's Bastion), Az Országház (House of the Nation - The Hungarian Parliament), and the Széchenyi Chain Bridge by the Danube. We love this aerial video with breathtaking views of the city created by Milan Heal (Drone Travel Guides).
We have new facilities in the works across five continents. Watch out for even more additions to our growing network.
-The Cloudflare Team
The Cloudflare network today

Ecommerce websites on Cloudflare: best practices

Cloudflare provides numerous benefits to ecommerce sites, including advanced DDOS protection and an industry-leading Web Application Firewall (WAF) that helps secure your transactions and protect customers’ private data.
A key Cloudflare feature is caching, which allows content to be served closer to the end user from our global network of data centers. Doing so improves the user's shopping experience and contributes to increasing the proportion of people completing a purchase (conversion rate).
For example:
- Walmart found improving page load time by 1 second increased their conversion rate by 2%
- Research for Amazon showed every 0.1 second of delay costs 1% of sales
- The Barack Obama campaign website saw an 80% page load time boost resulted in a 14% increase in donations
What is caching?
Cloudflare operates over 110 data centers around the world. When a website implements Cloudflare, visitor requests for the site will proxy through the nearest Cloudflare data center instead of connecting directly to the webserver hosting the site (origin). This means Cloudflare can store content such as images, JavaScript, CSS and HTML on our servers, speeding up access to those resources for end-users.
Most ecommerce websites rely on a backend database containing product descriptions and metadata Continue reading
Understanding Our Cache and the Web Cache Deception Attack
About a month ago, security researcher Omer Gil published the details of an attack that he calls the Web Cache Deception attack. It works against sites that sit behind a reverse proxy (like Cloudflare) and are misconfigured in a particular way. Unfortunately, the definition of "misconfigured" for the purposes of this attack changes depending on how the cache works. In this post, we're going to explain the attack and then describe the algorithm that our cache uses to decide whether or not to cache a given piece of content so that customers can be sure that they are secure against this attack.
The Attack
First, we'll explain the basics of the Web Cache Deception attack. For those who want a more in-depth explanation, Omer's original post is a great resource.

Imagine that you run the social media website example.com, and that each of your users has a newsfeed at example.com/newsfeed. When a user navigates to their newsfeed, the HTTP request generated by their browser might look something like this:
GET /newsfeed HTTP/1.1
Host: example.com
...
If you use Cloudflare, you don't want us to cache this request because if Continue reading
Cloudflare Rate Limiting – Insight, Control, and Mitigation against Layer 7 DDoS Attacks
Today, Cloudflare is extending its Rate Limiting service by allowing any of our customers to sign up. Our Enterprise customers have enjoyed the benefits of Cloudflare’s Rate Limiting offering for the past several months. As part of our mission to build a better internet, we believe that everyone should have the ability to sign up for the service to protect their websites and APIs.
 CC-BY 2.0 image by Benjamin Child
CC-BY 2.0 image by Benjamin Child
Rate Limiting is one more feature in our arsenal of tools that help to protect our customers against denial-of-service attacks, brute-force password attempts, and other types of abusive behavior targeting the application layer. Application layer attacks are usually a barrage of HTTP/S requests which may look like they originate from real users, but are typically generated by machines (or bots). As a result, application layer attacks are often harder to detect and can more easily bring down a site, application, or API. Rate Limiting complements our existing DDoS protection services by providing control and insight into Layer 7 DDoS attacks.
Rate Limiting is now available to all customers across all plans as an optional paid feature. The first 10,000 qualifying requests are free, which allows customers to start using Continue reading
Data Transfers Post-Brexit: Smoothing the Transition
The average internet user consumes vast amounts of data on a daily basis but rarely – unless an avid follower of Max Schrems - thinks about how the data flows or the mechanisms and legal arrangements in place to make it all happen. If companies like Cloudflare are doing their job well behind the scenes, you really shouldn’t have to – it just works, and so you can busy yourself emailing, communicating, transacting and sharing information.
Users benefit enormously from the free movement of data, and it is a highly regarded feature of living and doing business within the European Union. With the appropriate legal protections in place, scientific and societal benefits also flow along with the data, and the quality of our lives is improved immensely.
And the internet is an increasingly busy place:

Let it flow, let it flow...
The European Commission reported in a communication earlier this year that the European Data Economy – i.e the marketplace where digital data is exchanged as products or services derived from raw data – was estimated at EUR 272 billion in 2015, and that the value is expected to increase to EUR Continue reading
Munich: Cloudflare’s fifth data center in Germany
Oktoberfest has come early this year! We just turned up our latest data center in Munich: our 110th data center globally, and our fifth in Germany, joining Frankfurt, Düsseldorf, Berlin and Hamburg. Just over a mile away from the historic Hofbräuhaus, our newest deployment helps make six million websites faster across Bavaria, while providing additional redundancy and capacity to withstand attacks.
Oktoberfest kommt früh in diesem Jahr! Wir haben gerade unser 110. Rechenzentrum in München angeschaltet. Wir haben somit fünf Rechenzentren in Deutschland (Frankfurt, Düsseldorf, Berlin, Hamburg und München). Nur ca. 2 Kilometer entfernt vom historischen Hofbräuhaus, wird unser neustes Rechenzentrum sechs Millionen Webseiten im Raum Bayern schneller machen, und zugleich größere Kapazitäten gegen DDoS Attacken bereitstellen.
As TripAdvisor put it: Germany’s third largest city reflects the character of a city and a post card village at the same time.
Wie TripAdvisor es ausdrückt: Deutschlands drittgrößte Stadt spiegelt zugleich den Charakter einer Stadt und eines Dorfes wider.

CC BY-NC-ND 2.0 image by Werner Nieke
Continued Expansion
We have several additional locations being added to our fast expanding network that spans 55 countries. If you have a new city in mind, let us know, Continue reading
Changing Internet Standards to Build A Secure Internet
We’ve been working with registrars and registries in the IETF on making DNSSEC easier for domain owners, and over the next two weeks we’ll be starting out by enabling DNSSEC automatically for .dk domains.
DNSSEC: A Primer
Before we get into the details of how we've improved the DNSSEC experience, we should explain why DNSSEC is important and the function it plays in keeping the web safe.
DNSSEC’s role is to verify the integrity of DNS answers. When DNS was written in the early 1980’s, it was only a few researchers and academics on the internet. They all knew and trusted each other, and couldn’t imagine a world in which someone malicious would try to operate online. As a result, DNS relies on trust to operate. When a client asks for the address of a hostname like www.cloudflare.com, without DNSSEC it will trust basically any server that returns the response, even if it wasn’t the same server it originally asked. With DNSSEC, every DNS answer is signed so clients can verify answers haven’t been manipulated over transit.
The Trouble With DNSSEC
If DNSSEC is so important, why do so few domains support it? First, for a domain to Continue reading
How we made our DNS stack 3x faster
Cloudflare is now well into its 6th year and providing authoritative DNS has been a core part of infrastructure from the start. We’ve since grown to be the largest and one of the fastest managed DNS services on the Internet, hosting DNS for nearly 100,000 of the Alexa top 1M sites and over 6 million other web properties – or DNS zones.
 CC-BY 2.0 image by Steve Jurvetson
CC-BY 2.0 image by Steve Jurvetson
Today Cloudflare’s DNS service answers around 1 million queries per second – not including attack traffic – via a global anycast network. Naturally as a growing startup, the technology we used to handle tens or hundreds of thousands of zones a few years ago became outdated over time, and couldn't keep up with the millions we have today. Last year we decided to replace two core elements of our DNS infrastructure: the part of our DNS server that answers authoritative queries and the data pipeline which takes changes made by our customers to DNS records and distributes them to our edge machines across the globe.
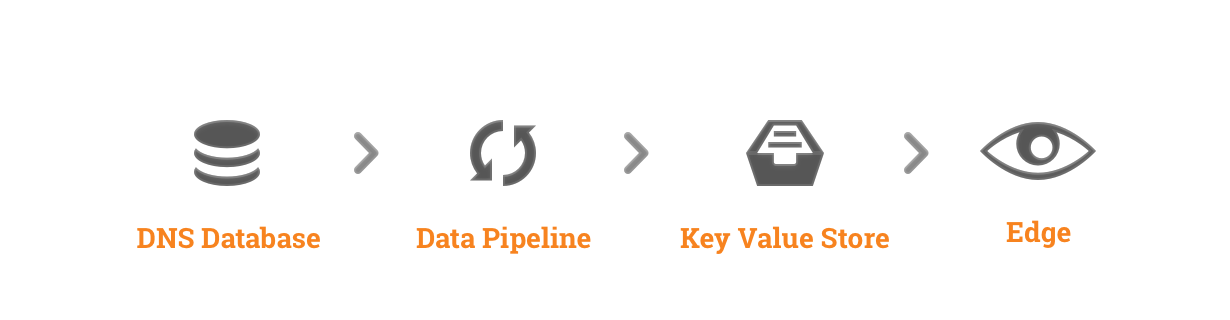
The rough architecture of the system can be seen above. We store customer DNS records and other origin server information in a central database, convert the Continue reading
Curaçao and Djibouti – two new Cloudflare datacenters located where undersea cables meet

Cloudflare has just turned up two new datacenters (numbers 108 and 109). Both are around halfway between the Tropic of Cancer and the Equator. They are located continents-apart, yet share something very-much in common as both of these new data centers are deployed and associated with where undersea cables reach land. Undersea cables have been and still are a growing part of the interconnected world that the Internet represents.
Curaçao, part of the Netherland Antilles in the Caribbean
 CC-BY 2.0 image by Nelo Hotsuma
CC-BY 2.0 image by Nelo Hotsuma
Curaçao is located in the Southern Caribbean Sea (just north of Venezuela) and has a strong Dutch heritage. Along with Aruba and Bonaire, Curaçao is part of the Lesser Antilles (they are called the ABC islands).
More importantly, Willemstad - the capital of Curaçao is where the Amsterdam Internet Exchange operates AMS-IX Caribbean. Why AMS-IX? Because of that Dutch relationship!
It’s AMS-IX’s goal (along with its local partners) to promote Curaçao as an interconnection location for the Caribbean. Cloudflare is there with all its services ready for that day!
Djibouti on the horn of Africa
Djibouti is a country of around 850,000 people with ~60% of the population living in the nation's capital, also Continue reading
Zdravo, Beograde! Cloudflare network spans 30 European cities
 CC-BY 2.0 image by De kleine rode kater
CC-BY 2.0 image by De kleine rode kater
Since Cloudflare began with our very first data center in Chicago, we are especially excited that our expansion takes us to its sister city. Where the Sava meets the Danube, Belgrade (Serbia) is home to Cloudflare’s 107th data center.
Пошто је Клаудфлер почео са првим дата центом у Чикагу посебно смо узбуђени што нас је наше ширење одвело у побратимљен град. Тамо где се Сава улива у Дунав, Београд, у Србији је дом Клаудфлеровог 107. дата центра.
Pošto je Cloudflare počeo sa prvim data centrom u Čikagu posebno smo uzbuđeni što nas je naše širenje odvelo u pobratimljen grad. Tamo gde se Sava uliva u Dunav, Beograd, u Srbiji je dom Cloudflare-ovog 107. data centra.
As a member of the Serbian Open Exchange, the leading internet exchange point in the country, we are excited to help make 6 million websites even faster for nearly 6 million Internet users. Belgrade is seeing growth in employment across the technology industry, ranging from the Microsoft Development Center to Serbian gaming company Nordeus to startups such as TeleSkin and Content Insights.
Као члан Serbian Open Exchage-а, водећег internet exchange-a у Србији, драго нам Continue reading
Kansas City: Cloudflare’s 106th Data Center Now Live
 CC-BY 2.0 image by Vincent Parsons
CC-BY 2.0 image by Vincent Parsons
Kansas City, Missouri. Home to the Kansas City Royals, Swope Park, over 100 barbeque restaurants, and now, Cloudflare's 106th data center. We are excited to help make 6 million websites even faster in the Midwest, as our newest deployment joins existing United States facilities in Ashburn, Atlanta, Boston, Chicago, Dallas, Denver, Las Vegas, Los Angeles, Miami,
Minneapolis, Nashville, Newark, Omaha, Philadelphia, Phoenix, San Jose, Seattle, St. Louis, and Tampa.
BBQ!
 CC-BY 2.0 image by Shelby Bell
CC-BY 2.0 image by Shelby Bell
Anthony Bourdain said it best with regards to Joe's KC BBQ in his "13 Places to Eat Before You Die" (alongside Michelin 3-star restaurants like French Laundry and Le Bernardin):
"People may disagree on who has the best BBQ. Here, the brisket (particularly the burnt ends), pulled pork, and ribs are all of a quality that meet the high standards even of Kansas City natives. It's the best BBQ in Kansas City, which makes it the best BBQ in the world."
Visit Kansas City to find the world’s largest shuttlecocks outside the Nelson Atkins Art Museum, as Continue reading
Cloudflare Apps: Develop Features for Everyone


CC-BY 2.5 image by Hans Braxmeier
Cloudflare’s mission is to help build a faster and more secure Internet for everyone, but sometimes sites often lack the accessibility features critical to allowing all Internet users to enjoy their content and perspective. Cloudflare Apps, which power the add-ons featured here, can allow developers to enhance any website. Get notified for the developer preview >>
The team at Cloudflare is excited to announce the release of two performance-enhancing features that makes the Internet more usable for two underrepresented demographics on the Internet: cats and Australians.
Feline Mode
The modern internet is full of content which challenges our perspectives. Often though, we are not interested in being challenged, we are interested in cats. To use the internet, to be a member of this incredible cultural fabric, is to find the most feline part of yourself. A love of sleeping, of curling up on a soft pile of destroyed clothing, a love of distracting and bothering others. Often though, websites just fail to recognize this critical part of our identity.
Australia Mode
We believe access to the internet is a basic human right. It’s not enough to just be able to access it Continue reading
Our Response to the Senate Vote on FCC Privacy Rules
Today, the U.S. Senate voted narrowly to undo certain regulations governing broadband providers, put in place during the Obama administration, that would have required Internet Service Providers (ISPs) to obtain approval from their customers before sharing information such as web-browsing histories, app usage, and aspects of their financial and health information, with third parties. Now, ISPs may sell targeted advertising or share personal information and browsing history with third party marketers, without first getting explicit consent from web users.
Cloudflare is disappointed with the Senate’s actions, as we feel strongly that consumer privacy rights need to be at the forefront of discussions around how personal information is treated. The new regulations would have steered the U.S. closer to the privacy standards enjoyed by citizens in many other developed countries, rather than away from such rights.
Defaulting to an “opt-in” rather than “opt-out” standard would provide consumers with greater controls over how, when, and with whom their personal information is used and shared. We believe that individuals should have the last say on what is done with their personal information, rather than corporations.
Regardless of whether Washington ultimately decides to approve rolling back these regulations, Cloudflare will continue to Continue reading
Buongiorno, Roma! Cloudflare Data Center CV
 CC-BY 2.0 image by Ilaria Giacomi
CC-BY 2.0 image by Ilaria Giacomi
We’re excited to announce Cloudflare’s 105th data center in Rome. Visitors in Italy (and especially around the region of Lazio) to over 6 million Internet properties now benefit from reduced latency and increased security. As our global network grows in breadth and capacity, we are able to stop attacks (typically, outside of Italy!), while serving legitimate traffic from our nearest in-country data center. Rome serves as a point of redundancy to our existing data center in Milan, and expands Cloudflare’s Europe network to 29 cities, with at least five more cities already in the works.
Siamo orgogliosi di annunciare il 105esimo data center di Cloudflare a Roma. Utenti in tutta Italia (e specialmente nel Lazio e regioni limitrofe) insieme ad oltre 6 milioni di proprietà in rete beneficeranno di latenze ridotte e maggior sicurezza. Con la crescita della nostra rete sia in copertura che capacità, abbiamo la possibilità di fermare attacchi (tipicamente originati fuori del territorio Italiano!) e di servire traffico legittimo dal data center più vicino. Roma offre maggiore ridondanza nella rete in coppia con il data center di Milano ed espande la rete Europea di Cloudflare a 29 Continue reading
¡Hola, Ecuador! Quito Data Center expands Cloudflare network to 104 cities across 52 countries
Located only 15 miles from the Equator, we are excited to announce Cloudflare’s newest data center in the World Heritage City of Quito, Ecuador. This deployment is made possible in partnership with the NAP.EC Internet exchange run by AEPROVI (Asociación de empresas proveedoras de servicios de internet). Our newest data center expands Cloudflare’s growing Latin America network to six cities, joining Buenos Aires (Argentina), Lima (Peru), Medellin (Colombia), Sao Paulo (Brazil) and Valparaiso (Chile). Quito is our 104th deployment globally, with over a dozen additional cities in the works right now.
Ubicado a sólo 15 millas del ecuador, estamos contentos de anunciar el nuevo centro de datos de Cloudflare en la ciudad de Quito, Ecuador. Este se realizó en asociación con el intercambio neutral de Internet de NAP.EC administrado por AEPROVI (Asociación de empresas proveedoras de servicios de internet). Este despliegue amplía la red latinoamericana de Cloudflare a seis ciudades: Buenos Aires (Argentina), Lima (Perú), Medellín (Colombia), Sao Paulo (Brasil) y Valparaíso (Chile). Quito es nuestro 104 despliegue global, con más de una docena de ciudades en desarrollo de expansión en este momento.
Open interconnection

Cloudflare participates at over 150 Internet exchanges Continue reading
Yerevan, Armenia: Cloudflare Data Center #103
In the coming days, Cloudflare will be announcing a series of new data centers across five continents. We begin with Yerevan, the capital and largest city of Armenia, the mountainous country in the South Caucasus. This deployment is our 37th data center in Asia, and 103rd data center globally.
History
Yerevan, one of the oldest continuously inhabited cities in the world, has a rich history going back all the way to 782 BC. Famous for its cognac, lavash flatbread, and beautiful medieval churches, Armenia is also home to more chess grandmasters per capita than most countries!
6 Million Websites Faster
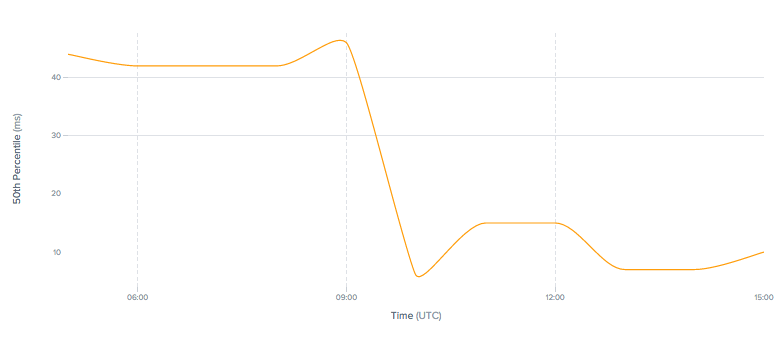 Latency (ms) decreases 6x for UCOM Internet user in Yerevan to Cloudflare. Source: Cedexis
Latency (ms) decreases 6x for UCOM Internet user in Yerevan to Cloudflare. Source: Cedexis
The newest Cloudflare deployment will make 6 million Internet properties faster and more secure, as we serve traffic to Yerevan and adjoining countries.
If the Cloudflare datacenter closest to the Equator (to date) was Singapore, the next deployment brings us even closer. Which one do you think it is?
The Cloudflare network today

- The Cloudflare Team




