Independent report shows: moving to Cloudflare can cut your carbon footprint

This post is also available in 简体中文, Français and Español.

In July 2021, Cloudflare described that although we did not start out with the goal to reduce the Internet's environmental impact, that has changed. Our mission is to help build a better Internet, and clearly a better Internet must be sustainable.
As we continue to hunt for efficiencies in every component of our network hardware, every piece of software we write, and every Internet protocol we support, we also want to understand in terms of Internet architecture how moving network security, performance, and reliability functions like those offered by Cloudflare from on-premise solutions to the cloud affects sustainability.
To that end, earlier this year we commissioned a study from the consulting firm Analysys Mason to evaluate the relative carbon efficiency of network functions like firewalls, WAF, SD-WAN, DDoS protection, content servers, and others that are provided through Cloudflare against similar on-premise solutions.
Although the full report will not be available until next year, we are pleased to share that according to initial findings:
Cloudflare Web Application Firewall (WAF) "generates up to around 90% less carbon than on-premises appliances at low-medium traffic demand."
Needless to say, we Continue reading
A more sustainable end-of-life for your legacy hardware appliances with Cloudflare and Iron Mountain


Today, as part of Cloudflare’s Impact Week, we’re excited to announce an opportunity for Cloudflare customers to make it easier to decommission and dispose of their used hardware appliances sustainably. We’re partnering with Iron Mountain to offer preferred pricing and discounts for Cloudflare customers that recycle or remarket legacy hardware through its service.
Replacing legacy hardware with Cloudflare’s network
Cloudflare’s products enable customers to replace legacy hardware appliances with our global network. Connecting to our network enables access to firewall (including WAF and Network Firewalls, Intrusion Detection Systems, etc), DDoS mitigation, VPN replacement, WAN optimization, and other networking and security functions that were traditionally delivered in physical hardware. These are served from our network and delivered as a service. This creates a myriad of benefits for customers including stronger security, better performance, lower operational overhead, and none of the headaches of traditional hardware like capacity planning, maintenance, or upgrade cycles. It’s also better for the Earth: our multi-tenant SaaS approach means more efficiency and a lower carbon footprint to deliver those functions.
But what happens with all that hardware you no longer need to maintain after switching to Cloudflare?
The life of a hardware box
The life of a hardware Continue reading
Historical emissions offsets (and Scope 3 sneak preview)


In July 2021, Cloudflare committed to removing or offsetting the historical emissions associated with powering our network by 2025. Earlier this year, after a comprehensive analysis of our records, we determined that our network has emitted approximately 31,284 metric tons (MTs) of carbon dioxide equivalent (CO2e) since our founding.
Today, we are excited to announce our first step toward offsetting our historical emissions by investing in 6,060 MTs’ worth of reforestation carbon offsets as part of the Pacajai Reduction of Emissions from Deforestation and forest Degradation (REDD+) Project in the State of Para, Brazil.
Generally, REDD+ projects attempt to create financial value for carbon stored in forests by using market approaches to compensate landowners for not clearing or degrading forests. From 2007 to 2016, approximately 13% of global carbon emissions from anthropogenic sources were the result of land use change, including deforestation and forest degradation. REDD+ projects are considered a low-cost policy mechanism to reduce emissions and promote co-benefits of reducing deforestation, including biodiversity conservation, sustainable management of forests, and conservation of existing carbon stocks. REDD projects were first recognized as part of the 11th Conference of the Parties (COP) of the United Nations Framework Convention on Climate Change in Continue reading
How we redesigned our offices to be more sustainable


At Cloudflare, we are working hard to ensure that we are making a positive impact on the surrounding environment, with the goal of building the most sustainable network. At the same time, we want to make sure that the positive changes that we are making are also something that our local Cloudflare team members can touch and feel, and know that in each of our actions we are having a positive impact on the environment around us. This is why we make sustainability one of the underlying goals of the design, construction, and operations of our global office spaces.
To make this type of pervasive change we have focused our efforts in three main areas: working with sustainable construction materials, efficient operations, and renewable energy purchasing (using clean sources like sunlight and wind). We believe that sustainable design goes far beyond just purchasing recycled and regenerative products. If you don’t operate your space with efficiency and renewables in mind, we haven’t fully accounted for all of our environmental impact.
Sustainability in office design & construction

Since 2020, we have been redefining how our teams work Continue reading
How we’re making Cloudflare’s infrastructure more sustainable


Whether you are building a global network or buying groceries, some rules of sustainable living remain the same: be thoughtful about what you get, make the most out of what you have, and try to upcycle your waste rather than throwing it away. These rules are central to Cloudflare — we take helping build a better Internet seriously, and we define this as not just having the most secure, reliable, and performant network — but also the most sustainable one.
With incredible growth of the Internet, and the increased usage of Cloudflare’s network, even linear improvements to sustainability in our hardware today will result in exponential gains in the future. We want to use this post to outline how we think about the sustainability impact of the hardware in our network, and what we’re doing to continually mitigate that impact.
Sustainability in the realm of servers
The total carbon footprint of a server is approximately 6 tons of Carbon Dioxide equivalent (CO2eq) when used in the US. There are four parts to the carbon footprint of any computing device:
- The embodied emissions: source materials and production
- Packing and shipping
- Use of the product
- End of life.
The emissions from the Continue reading
More bots, more trees


Once a year, we pull data from our Bot Fight Mode to determine the number of trees we can donate to our partners at One Tree Planted. It's part of the commitment we made in 2019 to deter malicious bots online by redirecting them to a challenge page that requires them to perform computationally intensive, but meaningless tasks. While we use these tasks to drive up the bill for bot operators, we account for the carbon cost by planting trees.
This year when we pulled the numbers, we saw something exciting. While the number of bot detections has gone significantly up, the time bots spend in the Bot Fight Mode challenge page has gone way down. We’ve observed that bot operators are giving up quickly, and moving on to other, unprotected targets. Bot Fight Mode is getting smarter at detecting bots and more efficient at deterring bot operators, and that’s a win for Cloudflare and the environment.
What’s changed?
We’ve seen two changes this year in the Bot Fight Mode results. First, the time attackers spend in Bot Fight Mode challenges has reduced by 166%. Many bot operators are disconnecting almost immediately now from Cloudflare challenge pages. We expect this Continue reading
How Cloudflare helps protect small businesses


Large-scale cyber attacks on enterprises and governments make the headlines, but the impacts of cyberattacks can be felt acutely by small businesses that struggle to keep the lights on during normal times. In this blog, we’ll share new research on how small businesses, including those using our free services, have leveraged Cloudflare services to make their businesses more secure and resistant to disruption, along with a real story about how Cloudflare makes a tangible impact for small business customers.
Research has indicated that 43% of cyber attacks target small businesses [Source: Institute for Security and Technology, Blueprint for Ransomware Defense, 2022]. Small businesses face many of the same cybersecurity challenges as larger organizations, but with fewer resources to plan, design, and manage their IT systems and security protections. Most small businesses say they don’t have the personnel to address IT security adequately or appropriately [Source: Ponemon Institute, 2018 State of Cybersecurity in Small & Medium Size Businesses].
Your local florist, fitness studio, café, or pet shop is likely using a wide variety of cloud-based SaaS apps to stay open for customers, including online accounting software, booking systems, point-of-sale credit card readers, inventory management systems, content management Continue reading
The Montgomery, Alabama Internet Exchange is making the Internet faster. We’re happy to be there.
Part of the magic of the Internet is in tens of thousands of networks connecting to each other all across the world in an effort to share information more efficiently. Cloudflare is a member of 279 Internet Exchanges (IX for short), but today we want to highlight one such dot on the global Internet map: the Montgomery, Alabama Internet Exchange, called MGMix. Thanks to the hard work of local leaders and the participation of dozens of networks (including Cloudflare), the Internet in Alabama works better today than it did before the IX launched.
Understanding IXs
Before we talk more about Alabama in particular, let's take a step back to understand the critical role that Internet Exchanges play in our global Internet. In a simple model of exchanging Internet traffic, one person is on their laptop and requests content on a website, uses a video conferencing application, or wants to securely connect to their workplace from home. The person, or “client” in technical terms, is generally using a traditional Internet Service Provider, who they pay to access everything on the Internet. On the other hand, whatever the user is trying to reach – the website, API endpoint, or security service – Continue reading
Cloudflare expands Project Pangea to connect and protect (even) more community networks


In July 2021, Cloudflare announced Project Pangea to help underserved community networks get access to the Internet for free. Today, as part of Impact Week, we’re excited to expand this program to support even more communities by relaxing the technical requirements to participate.
Previously, in order to be eligible for Project Pangea, participants would need to bring at least a /24 block of IP space for Cloudflare to advertise on their behalf (referred to as “Bring Your Own IP”). But everyone should have secure, fast, and reliable access to the Internet, without being gated by costly network resources like IPv4 space. Starting now, participants no longer need to bring a /24 in order to access Pangea services: Internet connectivity, DDoS protection, network firewalling, traffic acceleration, and more, are available for free for eligible networks.
How is Project Pangea helping community networks?
The Internet Society, or ISOC, describes community networks as “when people come together to build and maintain the necessary infrastructure for Internet connection.” Most often, community networks emerge from need, and in response to the lack or absence of available Internet connectivity.
Cloudflare’s global network, which spans more than 275 cities across the world, provides Continue reading
The US government is working on an “Internet for all” plan. We’re on board.
Recently, the United States Department of Commerce announced that all 50 states and every eligible territory had signed on to the “Internet for All'' initiative. Internet for All is the US government’s $65 billion initiative to close the Digital Divide once and for all through new broadband deployment and digital equity programs. Cloudflare is on a mission to help build a better Internet, and we support initiatives like this because we want more people using the Internet on high-throughput, low-latency, resilient and affordable Internet connections. It’s been written often since the start of the pandemic because it’s true: it isn’t acceptable that students need to go to a Taco Bell parking lot to do their homework, and a good Internet connection is increasingly important for doing adult jobs as well.
The Internet for All initiative is the result of $65 billion in broadband-related funding appropriated by the US Congress as part of the Infrastructure Investment and Jobs Act (IIJA). It’s been called a “once in a generation” funding opportunity, and compared with the Rural Electrification Act which brought power lines to rural America in the 1930s. The components of the broadband portion of the Infrastructure bill are:
- \$42. Continue reading
Project Safekeeping – protecting the world’s most vulnerable infrastructure with Zero Trust

This post is also available in 简体中文, 日本語, 한국어, Deutsch, Français and Español.

Under-resourced organizations that are vital to the basic functioning of our global communities face relentless cyber attacks, threatening basic needs for health, safety and security.
Cloudflare’s mission is to help make a better Internet. Starting December 13, 2022, we will help support these vulnerable infrastructure by providing our enterprise-level Zero Trust cybersecurity solution to them at no cost, with no time limit.
It is our pleasure to introduce our newest Impact initiative: Project Safekeeping.
Small targets, devastating impacts
Critical infrastructure is an obvious target for cyber attack: by its very definition, these are the organizations and systems that are crucial for the functioning of our society and economy. As such, these organizations cannot have prolonged interruptions in service, or risk having sensitive data exposed.
Our conversations over the past few months with government officials in Australia, Germany, Japan, Portugal, and the United Kingdom show that they are focused on the threat to critical infrastructure, but resource constraints mean that their attention is on protecting large organizations – immense financial institutions, hospital networks, oil pipelines, and airports. Yet, the small critical infrastructure organizations that Continue reading
Expanding Area 1 email security to the Athenian Project

This post is also available in 简体中文, Deutsch, Français and Español.

Election security encompasses a wide variety of measures, including the protection of voting machines, election office networks, voter registration databases, and other systems that manage the electoral process. At Cloudflare, we have reported on threats to state and local governments under the Athenian Project, how we prepare political campaigns and state parties under Cloudflare for Campaigns for election season, and our work with organizations that report on election results and voting rights groups under Project Galileo.
Since the 2022 US midterm elections, we have been thinking about how we help state and local governments deflect larger cyber threats that target the election community and have been analyzing the biggest problems they are facing. In October 2022, Jen Easterly, the director of the Cybersecurity and Infrastructure Security Agency, said, “The current election threat environment is more complex than it has ever been.” Amid threats, intimidation toward election workers, and cyber attacks against election infrastructure and operations, preparing for elections is no easy task.
At Cloudflare, our mission is to help build a better Internet. The Internet plays a key role in promoting democracy and ensuring Continue reading
Two months later: Internet use in Iran during the Mahsa Amini Protests


A series of protests began in Iran on September 16, following the death in custody of Mahsa Amini — a 22-year-old who had been arrested for violating Iran’s mandatory hijab law. The protests and civil unrest have continued to this day. But the impact hasn’t just been on the ground in Iran — the impact of the civil unrest can be seen in Internet usage inside the country, as well.
With the proliferation of smartphones and the ubiquity of the Internet that has resulted, it’s no longer simply the offline world impacting the Internet; what happens on the Internet is impacting the offline world, too. For that reason, it’s not surprising that in order to limit the spread of the protests — both news of it happening and the further organization of civil unrest — the Iranian government introduced limits on the Internet. This included banning certain social media and communications tools: most notably including Instagram and WhatsApp, which are estimated to be used by over 50% of the Iranian population.
But despite the threat that the protests pose, and the Internet’s enabling role in them, it has not been cut off altogether. In fact, from the perspective of Cloudflare, Continue reading
The latest on attacks, traffic patterns and cyber protection in Ukraine


On February 24, 2022, when Russia invaded Ukraine, Cloudflare jumped into action to provide services that could help prevent potentially destructive cyber attacks and keep the global Internet flowing. In the nearly 10 months since that day, we’ve posted about our actions, network traffic patterns, cyberattacks and network outages we’ve seen during the conflict.
During Impact Week, we want to provide an update on where things currently stand, the role of security companies like Cloudflare, and some of our takeaways from the conflict so far.
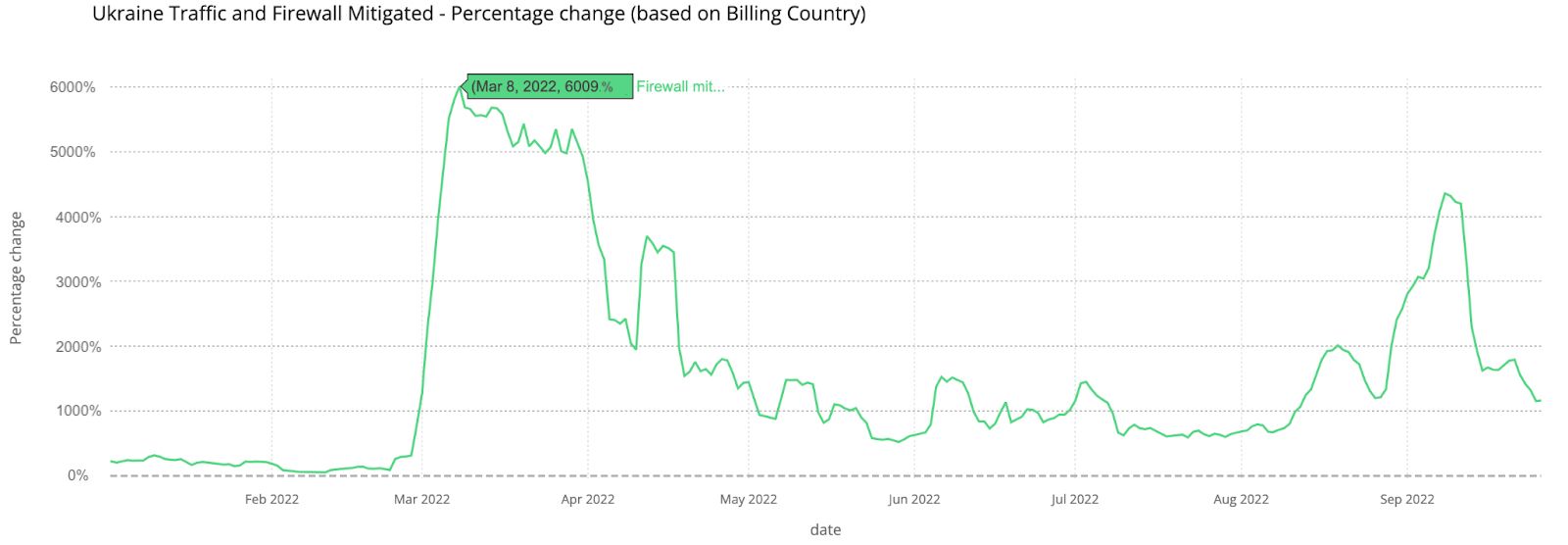
Cyberattacks on Ukrainian infrastructure and Cloudflare’s assistance
Since the time of the invasion, Ukrainian government and civilian infrastructure has come under a barrage of DDoS and other common cyberattacks. Although the public perception has been that cyberattacks have not played a significant role in the conflict, cyberspace has been an active battlefield. Ukrainian websites saw a significant spike in application layer firewall mitigated attacks in March 2022 and another spike in mid-September. Ukrainian sites have also seen a significant increase in the percentage of requests that were mitigated as attack traffic on a daily average, when compared with Q4 2021. Those spikes are shown below, using a seven-day rolling average:
The challenges of sanctioning the Internet


Following Russia’s invasion of Ukraine, governments around the world, including the US, UK, and EU announced sweeping sanctions targeting the Russian and Belarussian economies. These sanctions prohibit a specified level of economic activity in an effort to use economic influences to punish targeted countries. Almost overnight, we saw unprecedented restrictions put in place for multinational companies doing business in Russia or Belarus.
Separately, recent events in Iran led the US government to authorize additional Internet/communications activities, which were being used widely by average Iranians protesting against the government. This was done by expanding some existing licenses, or exceptions, to sanctions the US has imposed on Iran.
While the use of sanctions as a tool for responding to foreign relations crises is nothing new, the wide-ranging multilateral sanctions that have been imposed on Russia and the recent authorizations in Iran are significant and provide fresh examples of how sanctions can affect access to a free and open global Internet.
Balancing interests in sanctions policy
Cloudflare is committed to complying with all applicable sanctions, including US, UK, and EU sanctions, and we have put in place programs to ensure that compliance. At the same time, we recognize the important role we and Continue reading
How Cloudflare helps secure the inboxes of democracy

This post is also available in 简体中文, 日本語, Français, Español.

We at Cloudflare believe that every candidate, no matter their political affiliation, should be able to operate their campaign without having to worry about the risk of cyberattacks. Malicious attackers such as nation-state threat actors, those seeking monetary reward, or those with too much time on their hands often disagree with our mission and aim to wreak havoc on the democratic process.
Protecting Email Inboxes Is Key In Stopping Attacks
In the past years, malicious actors have used email as their primary threat vector when trying to disrupt election campaigns. A quick search online shows how active attackers still are in trying to compromise election official’s email inboxes.1 Over 90% of damages done to any organization are caused by a phishing attack, making protecting email inboxes a key focus. A well crafted phishing email paired, or an errant click could give an attacker the opportunity to see sensitive information, disseminate false information to voters, or steal campaign donations.
For the United States 2022 midterm elections, Cloudflare protected the inboxes of over 100 campaigns, election officials and public organizations supporting elections. These campaigns ranged from new officials Continue reading
Democratizing access to Zero Trust with Project Galileo

This post is also available in Deutsch, Français, Español, 简体中文.

Project Galileo was started in 2014 to protect free expression from cyber attacks. Many of the organizations in the world that champion new ideas are underfunded and lack the resources to properly secure themselves. This means they are exposed to Internet attacks aimed at thwarting and suppressing legitimate free speech.
In the last eight years, we have worked with 50 partners across civil society to onboard more than 2,000 organizations in 111 countries to provide our powerful cyber security products to those who work in sensitive yet critical areas of human rights and democracy building.
New security needs for a new threat environment
As Cloudflare has grown as a company, we have adapted and evolved Project Galileo especially amid global events such as COVID-19, social justice movements after the death of George Floyd, the war in Ukraine, and emerging threats to these groups intended to silence them. Early in the pandemic, as organizations had to quickly implement work-from-home solutions, new risks stemmed from this shift.
In our conversations with partners and participants, we noticed a theme. The digital divide in terms of cyber security products Continue reading
Cloudflare Zero Trust for Project Galileo and the Athenian Project

This post is also available in 日本語, Deutsch, Français, Español.

The organizations served by Projects Galileo and Athenian face the same security challenges as some of the world’s largest companies, but lack the budget to protect themselves. Sophisticated phishing campaigns attempt to compromise user credentials. Bad actors find ways to disrupt connectivity to critical resources. However, the tools to defend against these threats have historically only been available to the largest enterprises.
We’re excited to help fix that. Starting today, we are making the Cloudflare One Zero Trust suite available to teams that qualify for Project Galileo or Athenian at no cost. Cloudflare One includes the same Zero Trust security and connectivity solutions used by over 10,000 customers today to connect their users and safeguard their data.
Same problem, different missions
Athenian Project candidates work to safeguard elections in the United States. Project Galileo applicants launched their causes to support journalists, encourage artistic expression, or protect persecuted groups. They each set out to fix difficult and painful problems. None of the applications to our programs wrote their mission statement to deal with phishing attacks or internal data loss.
However, security problems plague these teams. Instead of being Continue reading
Welcome to Cloudflare’s Impact Week

In the early days of Cloudflare, we made it a policy that every new hire had to interview with either me or my co-founder Michelle. It’s still the case today, though we now have more than 3,000 employees, continue to hire great people as we find them, and, because there are only so many hours in the day, have had to enlist a few more senior executives to help with these final calls.
At first, these calls were about helping screen for new members of our small team. But, as our team grew, the purpose of these calls changed. Today, by the time I do the final call with someone we’ve made the decision to hire them, so it’s rarely about screening. Instead, the primary purpose is to make sure everyone joining has had a positive conversation with a senior member of our team, so if in the future they ever see something going wrong they’ll hopefully feel a bit more comfortable letting one of us know. I think because of that these calls are some of the most important work I do.
But, for me, there’s another purpose. I get to hear first-hand why people chose to apply. That’s Continue reading
Stop attacks before they are known: making the Cloudflare WAF smarter


Cloudflare’s WAF helps site owners keep their application safe from attackers. It does this by analyzing traffic with the Cloudflare Managed Rules: handwritten highly specialized rules that detect and stop malicious payloads. But they have a problem: if a rule is not written for a specific attack, it will not detect it.
Today, we are solving this problem by making our WAF smarter and announcing our WAF attack scoring system in general availability.
Customers on our Enterprise Core and Advanced Security bundles will have gradual access to this new feature. All remaining Enterprise customers will gain access over the coming months.
Our WAF attack scoring system, fully complementary to our Cloudflare Managed Rules, classifies all requests using a model trained on observed true positives across the Cloudflare network, allowing you to detect (and block) evasion, bypass and new attack techniques before they are publicly known.
The problem with signature based WAFs
Attackers trying to infiltrate web applications often use known or recently disclosed payloads. The Cloudflare WAF has been built to handle these attacks very well. The Cloudflare Managed Ruleset and the Cloudflare OWASP Managed Ruleset are in fact continuously updated and aimed at protecting web applications against known Continue reading