Cloudflare One: One Year Later


Cloudflare One helps enterprises build modern enterprise networks, operate efficiently and securely, and throw out on-premise hardware. It’s been more than a year since we announced the product suite, and we wanted to check in on how things are going.
We’re celebrating Chief Information Officers this week. Regardless of the size of their organization, they’ve had a challenging year. Overnight, their teams became responsible for years of digital transformation to prepare their networks and users to support work-from-home and to adopt new technologies. They worked with partners across security, engineering, and people teams to keep their critical infrastructure running.
Today, we want to focus on the problems that CIOs have been able to solve with Cloudflare One in the last year. Customers are using Cloudflare One at a scale we couldn’t have imagined a year ago to solve interesting problems that we didn't know existed yet. We’ll walk through some specific use cases later in the post, but first, let’s recap why we built Cloudflare One, what problems it solves, and some of the new things we’re launching this week.
What is Cloudflare One?
Cloudflare One allows companies to purchase, provision, and manage connectivity, security, and analytics tools needed Continue reading
How to connect your offices to Cloudflare using SD-WAN
Many offices will soon be re-opening and, just as two years ago when the shift to remote work brought a paradigm change for IT and networking teams, the return to office will bring its own challenges. Two years ago, Chief Information Officers faced a surprise fire drill enabling a completely remote workforce nearly overnight. As companies start to experiment with hybrid working models, IT teams are facing new problems. They are not just re-opening existing branches and potentially activating new ones to enable greater distribution of a more flexible workforce, but also ensuring users have a consistent experience regardless of where they’re connecting. All of this occurs while maintaining visibility and security across an increasingly complex and hard to maintain corporate network.
Some companies have adopted SD-WAN technology to help solve these problems. SD-WAN, or software-defined wide-area networking, is a flexible way to interconnect branches and corporate headquarters together using software as an overlay to various hardware platforms. Deploying SD-WAN can make IT and network teams’ lives simpler by consolidating management tasks and abstracting away the complexity of router configuration. SD-WAN platforms often include a central “orchestrator” that holds information about connected locations.
SD-WAN as Management Overlay for your Corporate Continue reading
PII and Selective Logging controls for Cloudflare’s Zero Trust platform


At Cloudflare, we believe that you shouldn’t have to compromise privacy for security. Last year, we launched Cloudflare Gateway — a comprehensive, Secure Web Gateway with built-in Zero Trust browsing controls for your organization. Today, we’re excited to share the latest set of privacy features available to administrators to log and audit events based on your team’s needs.
Protecting your organization
Cloudflare Gateway helps organizations replace legacy firewalls while also implementing Zero Trust controls for their users. Gateway meets you wherever your users are and allows them to connect to the Internet or even your private network running on Cloudflare. This extends your security perimeter without having to purchase or maintain any additional boxes.
Organizations also benefit from improvements to user performance beyond just removing the backhaul of traffic to an office or data center. Cloudflare’s network delivers security filters closer to the user in over 250 cities around the world. Customers start their connection by using the world’s fastest DNS resolver. Once connected, Cloudflare intelligently routes their traffic through our network with layer 4 network and layer 7 HTTP filters.
To get started, administrators deploy Cloudflare’s client (WARP) on user devices, whether those devices are macOS, Windows, iOS, Android, Continue reading
Welcome to CIO Week and the future of corporate networks


The world of a Chief Information Officer has changed — today’s corporate networks look nothing like those of even five or ten years ago — and these changes have created gaps in visibility and security, introduced high costs and operational burdens, and made networks fragile and brittle.
We’re optimistic that CIOs have a brighter future to look forward to. The Internet has evolved from a research project into integral infrastructure companies depend on, and we believe a better Internet is the path forward to solving the most challenging problems CIOs face today. Cloudflare is helping build an Internet that’s faster, more secure, more reliable, more private, and programmable, and by doing so, we’re enabling organizations to build their next-generation networks on ours.
This week, we’ll demonstrate how Cloudflare One, our Zero Trust Network-as-a-Service, is helping CIOs transform their corporate networks. We’ll also introduce new functionality that expands the scope of Cloudflare’s platform to address existing and emerging needs for CIOs. But before we jump into the week, we wanted to spend some time on our vision for the corporate network of the future. We hope this explanation will clarify language and acronyms used by vendors and analysts who have realized Continue reading
The Grinch Bot is Stealing Christmas!

This week, a group of US lawmakers introduced the Stopping Grinch Bots Act — new legislation that could stop holiday hoarders on the Internet. This inspired us to put a spin on a Dr. Seuss classic:
Each person on the Internet liked Christmas a lot
But the Grinch Bot, built by the scalper did not!
The Grinch Bot hated Christmas! The whole Christmas season!
Now, please don’t ask why. No one quite knows the reason.

Cloudflare stops billions of bad bots every day. As you might have guessed, we see all types of attacks, but none is more painful than a Grinch Bot attack. Join us as we take a closer look at this notorious holiday villain...
25 days seconds of Christmas
What is the Grinch Bot? Technically speaking, it’s just a program running on a computer, making automated requests that reach different websites. We’ve come to refer to these requests as “bots” on the Internet. Bots move quickly, leveraging the efficiency of computers to carry out tasks at scale. The Grinch Bot is a very special type that satisfies two conditions:
- It only pursues online inventory, attempting to purchase items before humans can complete their orders.
- It only operates Continue reading
Get notified when your site is under attack
Our core application security features such as the WAF, firewall rules and rate limiting help keep millions of Internet properties safe. They all do so quietly without generating any notifications when attack traffic is blocked, as our focus has always been to stop malicious requests first and foremost.
Today, we are happy to announce a big step in that direction. Business and Enterprise customers can now set up proactive alerts whenever we observe a spike in firewall related events indicating a likely ongoing attack.
Alerts can be configured via email, PagerDuty or webhooks, allowing for flexible integrations across many systems.
You can find and set up the new alert types under the notifications tab in your Cloudflare account.
What Notifications are available?
Two new notification types have been added to the platform.
Security Events Alert
This notification can be set up on Business and Enterprise zones, and will alert on any spike of firewall related events across all products and services. You will receive the alert within two hours of the attack being mitigated.
Advanced Security Events Alert
This notification can be set up on Enterprise zones only. It allows you to filter on the exact security service you are Continue reading
Thanksgiving’s biggest online shopping day was Cyber Monday, but other days were close behind


November comes, the temperatures start to get colder for most of the planet's population (87% live in the Northern Hemisphere) and many are also starting to prepare for the festive season. That also brings significant changes in Internet traffic, most notably the online shopping kind of traffic.
So, what were the November days that e-commerce websites had the most traffic in the US and what about worldwide? Is humanity using more mobile Internet at this time? And what are the most popular days online — is Black Friday the winner?
We’ll dig into those questions using Cloudflare Radar. E-commerce is expanding and at an all-time high, especially after the pandemic accelerated the digital transformation process (e-commerce had a 32.4% increase in sales in the US in 2020 and is expected to grow this year).
Cyber Monday, a ‘last minute’ winner
Let’s start with e-commerce — we added a chart to Radar that shows trends for e-commerce by country. The worldwide trend is pretty evident: Cyber Monday, the day for supposedly last-minute discounts, was the clear winner.
Worldwide most popular days for e-commerce
#1. Cyber Monday, November 29.
#2. Monday, November 23.
#3. Black Friday, November 26 — November Continue reading
Attack Maps now available on Radar
Cloudflare Radar launched as part of last year’s Birthday Week. We described it as a “newspaper for the Internet”, that gives “any digital citizen the chance to see what’s happening online [which] is part of our pursuit to help build a better, more informed, Internet”.
Since then, we have made considerable strides, including adding dedicated pages to cover how key events such as the UEFA Euro 2020 Championship and the Tokyo Olympics shaped Internet usage in participating countries, and added a Radar section for interactive deep-dive reports on topics such as DDoS.
Today, Radar has four main sections:
- Main page with near real-time information about global Internet usage.
- Internet usage details by country (see, for example, Portugal).
- Domain insights, where searching for a domain returns traffic, registration and certificate information about it.
- Deep-dive reports on complex and often underreported topics.
Cloudflare’s global network spans more than 250 cities in over 100 countries. Because of this, we have the unique ability to see both macro and micro trends happening online, including insights on how traffic is flowing around the world or what type of attacks are prevalent in a certain country.
Radar Maps will make this information even richer Continue reading
How the US paused shopping (and browsing) for Thanksgiving

So, if you like to keep up with the tradition in the United States you and your family yesterday (November 25, 2021) celebrated Thanksgiving. So on a special day, with family gatherings for many and with a lot of cooking if you’re into the tradition (roast turkey, stuffing and pumpkin pie), it makes sense that different Internet patterns show up on Cloudflare Radar.
First, let’s look at shopping habits. After a busy Monday, Tuesday and Wednesday, online shopping paused for Thanksgiving Day and dipped at lunchtime. So in a very good week for e-Commerce, Thanksgiving was an exception, especially at the extended lunchtime.
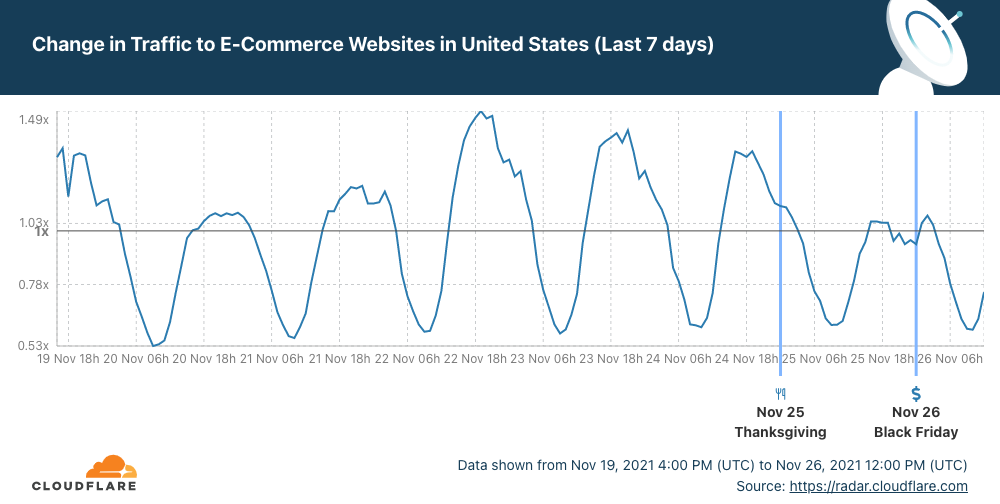
Now, let’s focus on Internet traffic at the time of the Thanksgiving Dinner. First, what time is that? Every family is different, but a 2018 survey of US consumers showed that for 42% early afternoon (between 13:00 and 15:00 is the preferred time to sit at the table and start to dig in). But 16:00 seems to be the “correct time” — The Atlantic explains why.
Cloudflare Radar shows that Internet traffic in the US increased this past seven days, compared with the previous period, and that makes sense given that it’s traditionally a good week for Continue reading
Heard in the halls of Web Summit 2021


Global in-person events were back in a big way at the start of November (1-4) in Lisbon, Portugal, with Web Summit 2021 gathering more than 42,000 attendees from 128 countries. I was there to discover Internet trends and meet interesting people. What I saw was the contagious excitement of people from all corners of the world coming together for what seemed like a type of normality in a time when the Internet “is almost as important as having water”, according to Sonia Jorge from the World Wide Web Foundation.
Here’s some of what I heard in the halls.
With a lot happening on a screen, the lockdowns throughout the pandemic showed us a glimpse of what the metaverse could be, just without VR or AR headsets. Think about the way many were able to use virtual tools to work all day, learn, collaborate, order food, supplies, and communicate with friends and family — all from their homes.
While many had this experience, many others were unable to, with some talks at the event focusing on the digital divide and how “Internet access Continue reading
Everything you ever wanted to know about UDP sockets but were afraid to ask, part 1
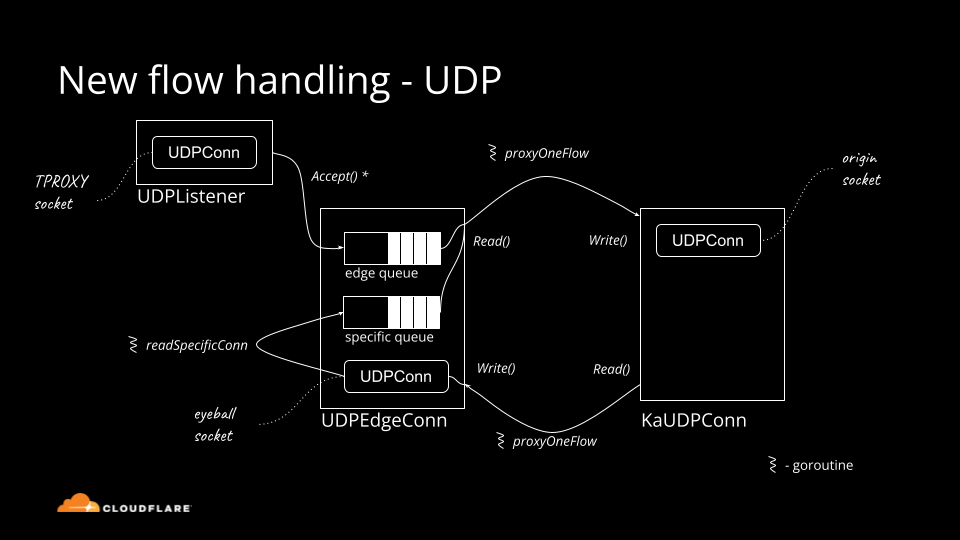
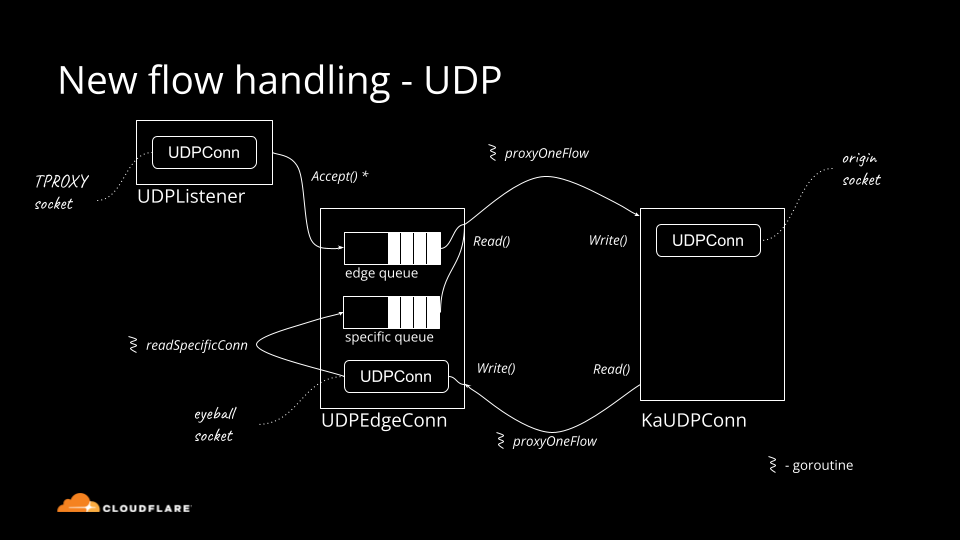
Historically Cloudflare's core competency was operating an HTTP reverse proxy. We've spent significant effort optimizing traditional HTTP/1.1 and HTTP/2 servers running on top of TCP. Recently though, we started operating big scale stateful UDP services.
Stateful UDP gains popularity for a number of reasons:
— QUIC is a new transport protocol based on UDP, it powers HTTP/3. We see the adoption accelerating.
— We operate WARP — our Wireguard protocol based tunneling service — which uses UDP under the hood.
— We have a lot of generic UDP traffic going through our Spectrum service.
Although UDP is simple in principle, there is a lot of domain knowledge needed to run things at scale. In this blog post we'll cover the basics: all you need to know about UDP servers to get started.
Connected vs unconnected
How do you "accept" connections on a UDP server? If you are using unconnected sockets, you generally don't.
But let's start with the basics. UDP sockets can be "connected" (or "established") or "unconnected". Connected sockets have a full 4-tuple associated {source ip, source port, destination ip, destination port}, unconnected Continue reading
Announcing Argo for Spectrum

Today we're excited to announce the general availability of Argo for Spectrum, a way to turbo-charge any TCP based application. With Argo for Spectrum, you can reduce latency, packet loss and improve connectivity for any TCP application, including common protocols like Minecraft, Remote Desktop Protocol and SFTP.
The Internet — more than just a browser
When people think of the Internet, many of us think about using a browser to view websites. Of course, it’s so much more! We often use other ways to connect to each other and to the resources we need for work. For example, you may interact with servers for work using SSH File Transfer Protocol (SFTP), git or Remote Desktop software. At home, you might play a video game on the Internet with friends.
To help people that protect these services against DDoS attacks, Spectrum launched in 2018 and extends Cloudflare’s DDoS protection to any TCP or UDP based protocol. Customers use it for a wide variety of use cases, including to protect video streaming (RTMP), gaming and internal IT systems. Spectrum also supports common VoIP protocols such as SIP and RTP, which have recently seen an increase in DDoS ransomware attacks. A lot of Continue reading
Burkina Faso Internet shutdown

A few days after Sudan restored access to the Internet, people living in Burkina Faso are facing an Internet shutdown. On Saturday, Cloudflare Radar shows that after 22:00 UTC (the same local time) Internet traffic went down significantly, something that has happened in the context of social tensions in the country that started on November 14, 2021, and after this Saturday’s shooting of protesters that tried to block a French military convoy.
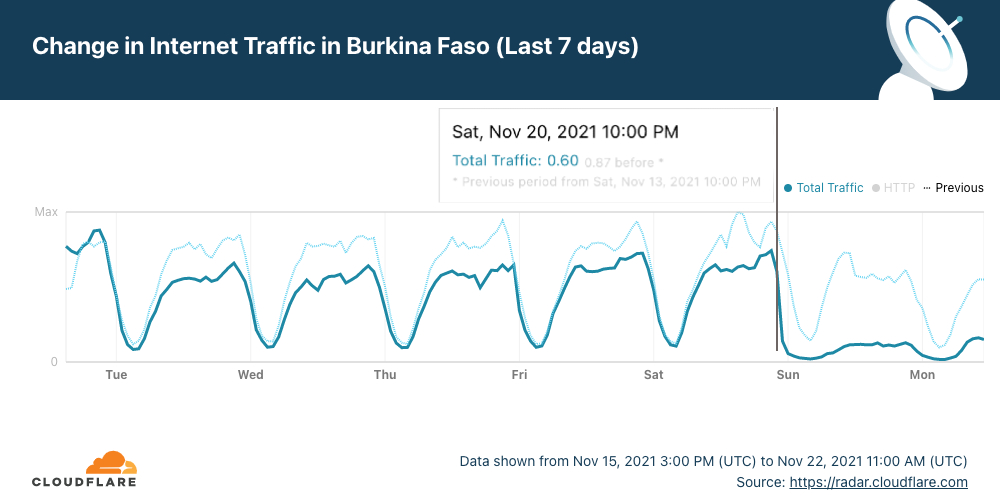
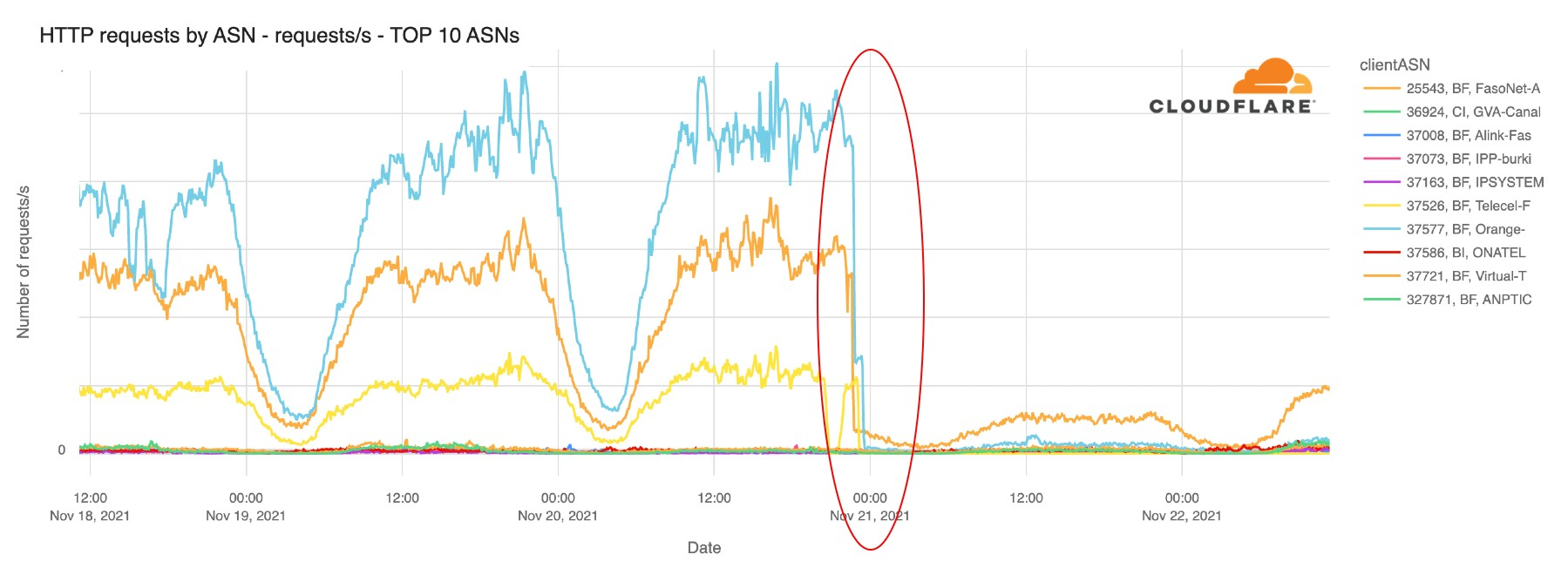
It is clear when we look at the last 30 days, that Sunday and today, Monday, November 22, are days almost without Internet traffic in Burkina Faso.
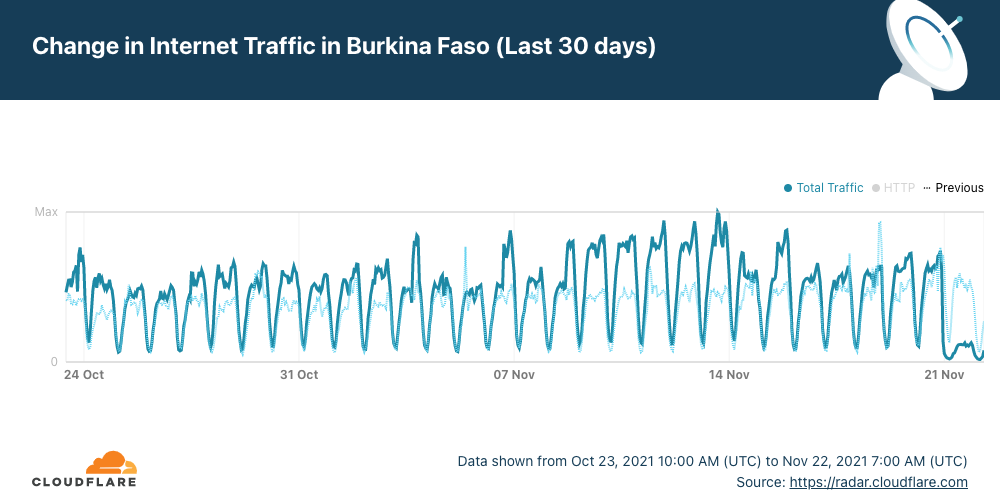
All the Internet Service Providers (ISP) of the country were significantly affected by what we could see in our data. That is evident when we look at HTTP traffic by ASN (Autonomous System Number). Orange, FasoNet and Telecel are the three most used ISPs in the country and this chart clearly shows how they were impacted.
Mobile traffic affected
Burkina Faso is a mobile-first country because mobile is the main way of accessing the Internet — in the last 30 days the mobile traffic percentage represented 77% of the total Internet traffic in the country.
We can also Continue reading
Sudan was cut off from the Internet for 25 days

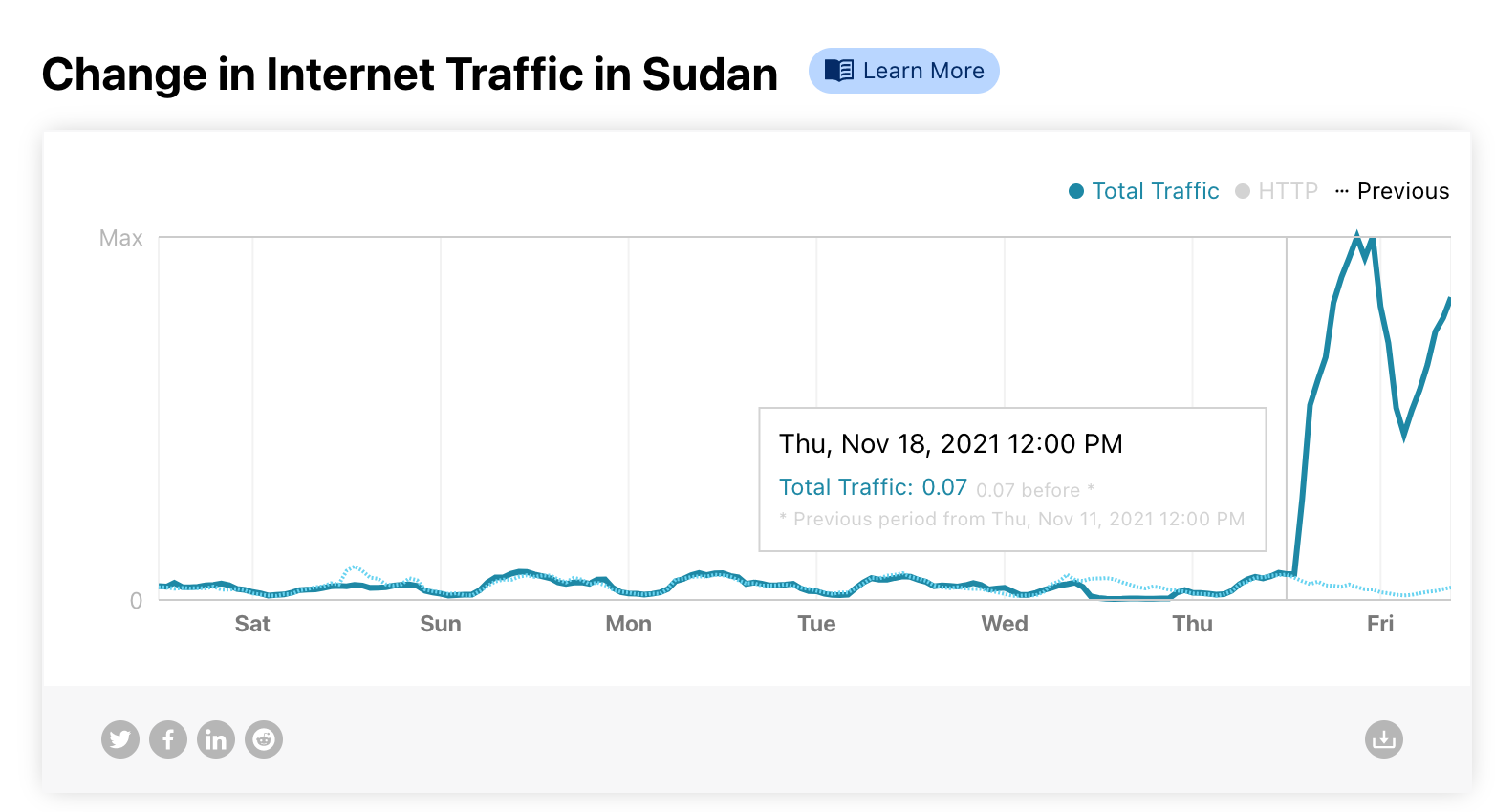
Internet traffic started to come back in Sudan (with limitations) on Thursday, November 18, 2021. This happened after 25 days of an almost complete shutdown that affected the whole country. It’s a simple line going up on a chart for us, but for a country that also meant that Internet access was (at least in part) back on with all of what comes with it for businesses, communities, families and society as a whole.
You can see that trend on Cloudflare Radar, in particular after 13:00 UTC (15:00 local time). After that Internet traffic went up like we haven’t seen at all in the previous three weeks.
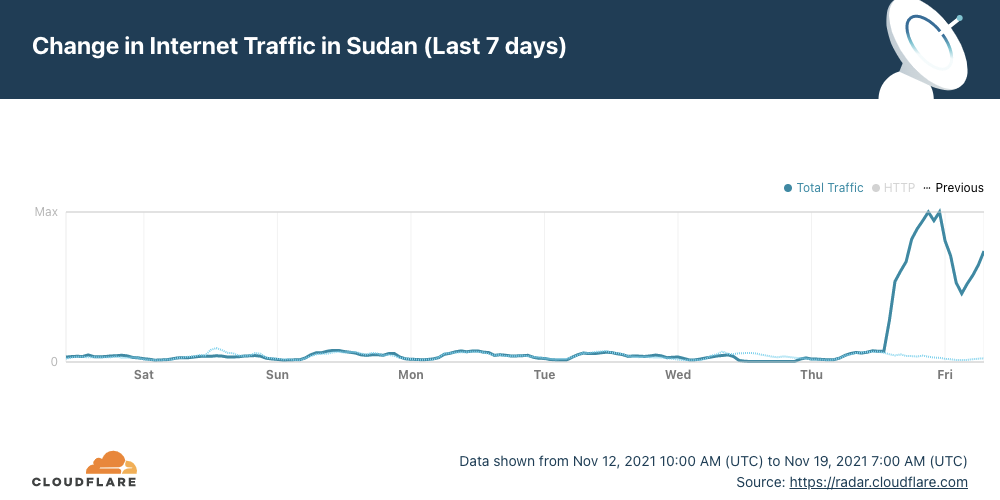
Internet access was mostly cut off on October 25, 2021, after a political turmoil in the country. A Sudanese court previously ordered the restoration of Internet access on November 9, but until last Thursday, November 18, there were no signs of services returning to normal. The biggest Internet access shutdown in recent history in the country was back in 2019 — for a full 36 days.
Looking back at the last 30 days Cloudflare Radar shows very distinctively a big difference from what was previously normal in the country.
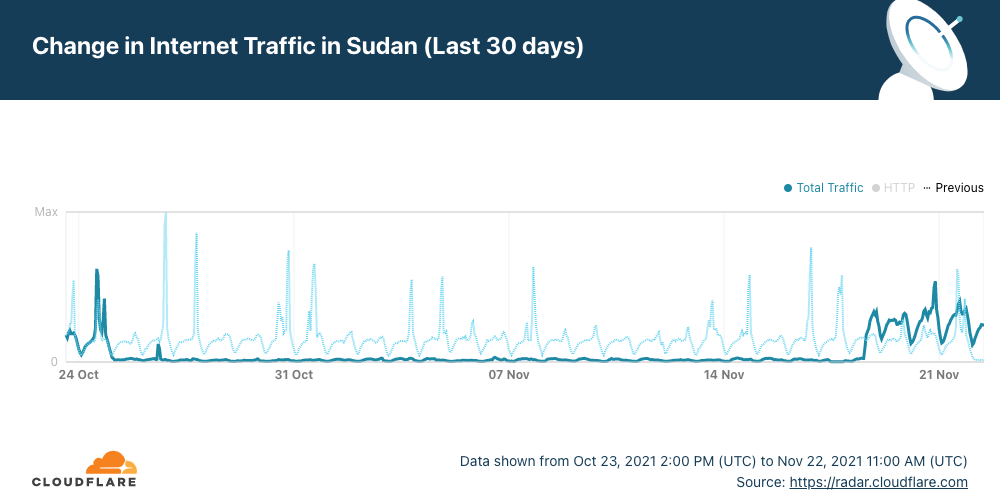
On Wednesday, Continue reading
Network Performance Update: Full Stack Week

This blog was published on November 20, 2021. As we continue to optimize our network we're publishing regular updates, which are available here.

A little over two months ago, we shared extensive benchmarking results of last mile networks all around the world. The results showed that on a range of tests (TCP connection time, time to first byte, time to last byte), and on a range of measurements (p95, mean), that Cloudflare was the fastest provider in 49% of networks around the world. Since then, we’ve worked to continuously improve performance until we’re the fastest everywhere. We set a goal to grow the number of networks where we’re the fastest by 10% every Innovation Week. We met that goal during Birthday Week (September 2021).
Today, we’re proud to report we blew the goal away for Full Stack Week (November 2021). Cloudflare measured our performance against the top 1,000 networks in the world (by number of IPv4 addresses advertised). Out of those, Cloudflare has become the fastest provider in 79 new networks, an increase of 14% of these 1,000 networks. Of course, we’re not done yet, but we wanted to share the latest results and explain how we did it.
However, Continue reading
Announcing native support for Stripe’s JavaScript SDK in Cloudflare Workers

This post is also available in 日本語, 简体中文.

Handling payments inside your apps is crucial to building a business online. For many developers, the leading choice for handling payments is Stripe. Since my first encounter with Stripe about seven years ago, the service has evolved far beyond simple payment processing. In the e-commerce example application I shared last year, Stripe managed a complete seller marketplace, using the Connect product. Stripe's product suite is great for developers looking to go beyond accepting payments.
Earlier versions of Stripe's SDK had core Node.js dependencies, like many popular JavaScript packages. In Stripe’s case, it interacted directly with core Node.js libraries like net/http, to handle HTTP interactions. For Cloudflare Workers, a V8-based runtime, this meant that the official Stripe JS library didn’t work; you had to fall back to using Stripe’s (very well-documented) REST API. By doing so, you’d lose the benefits of using Stripe’s native JS library — things like automatic type-checking in your editor, and the simplicity of function calls like stripe.customers.create(), instead of manually constructed HTTP requests, to interact with Stripe’s various pieces of functionality.
In April, we wrote that we were focused on Continue reading
New Stream Player customizations to boost your video experience

When we launched Stream, one of our goals was to provide the most performant video player. We focused on building a player that loads fast, works across different browsers and frameworks, and intelligently switches video quality levels depending on your end user’s connectivity.
We are expanding the Stream Player vision, so you can control the look and feel of the viewing experience. Today, we are announcing a series of new customization options to help you deliver the best video playback experience.
Add Your Own Color
One thing we kept hearing from customers is that they would like to be able to customize the Stream Player to better reflect their brand. Stream Player now supports setting a primary color to match your company’s color. Here is an example of us using the primaryColor property to set the primary color to the Cloudflare Orange.
To use the primaryColor property, simply add it to the iframe URL. In this example, the hex code is #F48120 and the uri-encoded value is %23F48120.
https://iframe.videodelivery.net/fcfa5c97795ba90251cbbae1880a0e18?primaryColor=%23F48120
If you are using the React or Angular wrapper, you can use the primaryColor prop to customize the player color.
Currently, setting the primary color property will change Continue reading
Launching a Startup on Cloudflare Workers

Closing out the Developer Spotlight series for this week is Tejas Mehta who shares how he built his startup, cClip.
cClip is a great tool that allows you to “copy/paste” and transfer files between any of your devices, regardless of what OS they run.
What is so interesting about cClip though is that it is a fully serverless application built on top of Workers and KV, but not exclusively. It uses Firebase for authentication, RevenueCat for a consolidated view over the Apple and Google Play store, and Stripe for all other billing related work.
This is a peek into the future of application development. This is a future where we will be “importing” other SaaS applications as easily as we currently import a package from a package manager. And not only unidirectional by calling APIs on that external application, but bi-directional communication through events with Webhooks.
Here is Tejas telling his story.
The origins of cClip
The abrupt transition to virtual schooling last year led to all my school communications and assignments transitioning online. With a MacBook laptop and an Android phone, submitting my precalculus homework meant I had to take a picture of each page, email each picture to Continue reading
An Open-Source CMS on the Cloudflare Stack: Introductory Post


The Cloudflare documentation is a great resource when learning concepts, reviewing API usage notes, or when you’re in need of a concise snippet to illustrate those APIs or concepts. But, as comprehensive as it is, new users to the Cloudflare Workers platform must bridge a large gap to go from the introductory example snippets to a real, production-ready application. While some of this may be specific to Workers (as with any platform), developers everywhere are figuring out how applications should be built in a serverless world. Building large serverless applications entails a learning curve journey, regardless of a developer’s experience level.
At Cloudflare, we’re intimately aware of this because we also had to go through the same transition. Our engineers are world-class and expertfully design and craft products that compliment the distributed paradigm… but experts aren’t born overnight! We have been there, and we want to help jumpstart and aid others’ understanding.
With this in mind, we decided to do something unique to the industry: we are developing an example feature-complete SaaS application that will be built entirely on the Cloudflare stack. It is and will continue to be completely free, open-sourced on GitHub, and developed in public. This Continue reading
Build your next video application on Cloudflare

Historically, building video applications has been very difficult. There's a lot of complicated tech behind recording, encoding, and playing videos. Luckily, Cloudflare Stream abstracts all the difficult parts away, so you can build custom video and streaming applications easily. Let's look at how we can combine Cloudflare Stream, Access, Pages, and Workers to create a high-performance video application with very little code.
Today, we’re going to build a video application inspired by Cloudflare TV. We’ll have user authentication and the ability for administrators to upload recorded videos or livestream new content. Think about being able to build your own YouTube or Twitch using Cloudflare services!
Fetching a list of videos
On the main page of our application, we want to display a list of all videos. The videos are uploaded and stored with Cloudflare Stream, but more on that later! This code could be changed to display only the "trending" videos or a selection of videos chosen for each user. For now, we'll use the search API and pass in an empty string to return all.
import { getSignedStreamId } from "../../src/cfStream"
export async function onRequestGet(context) {
const {
request,
env,
params,
} = context
const { id Continue reading