Sandboxing in Linux with zero lines of code
Modern Linux operating systems provide many tools to run code more securely. There are namespaces (the basic building blocks for containers), Linux Security Modules, Integrity Measurement Architecture etc.
In this post we will review Linux seccomp and learn how to sandbox any (even a proprietary) application without writing a single line of code.
Tux by Iwan Gabovitch, GPL
Sandbox, Simplified Pixabay License
Linux system calls
System calls (syscalls) is a well-defined interface between userspace applications and the operating system (OS) kernel. On modern operating systems most applications provide only application-specific logic as code. Applications do not, and most of the time cannot, directly access low-level hardware or networking, when they need to store data or send something over the wire. Instead they use system calls to ask the OS kernel to do specific hardware and networking tasks on their behalf:
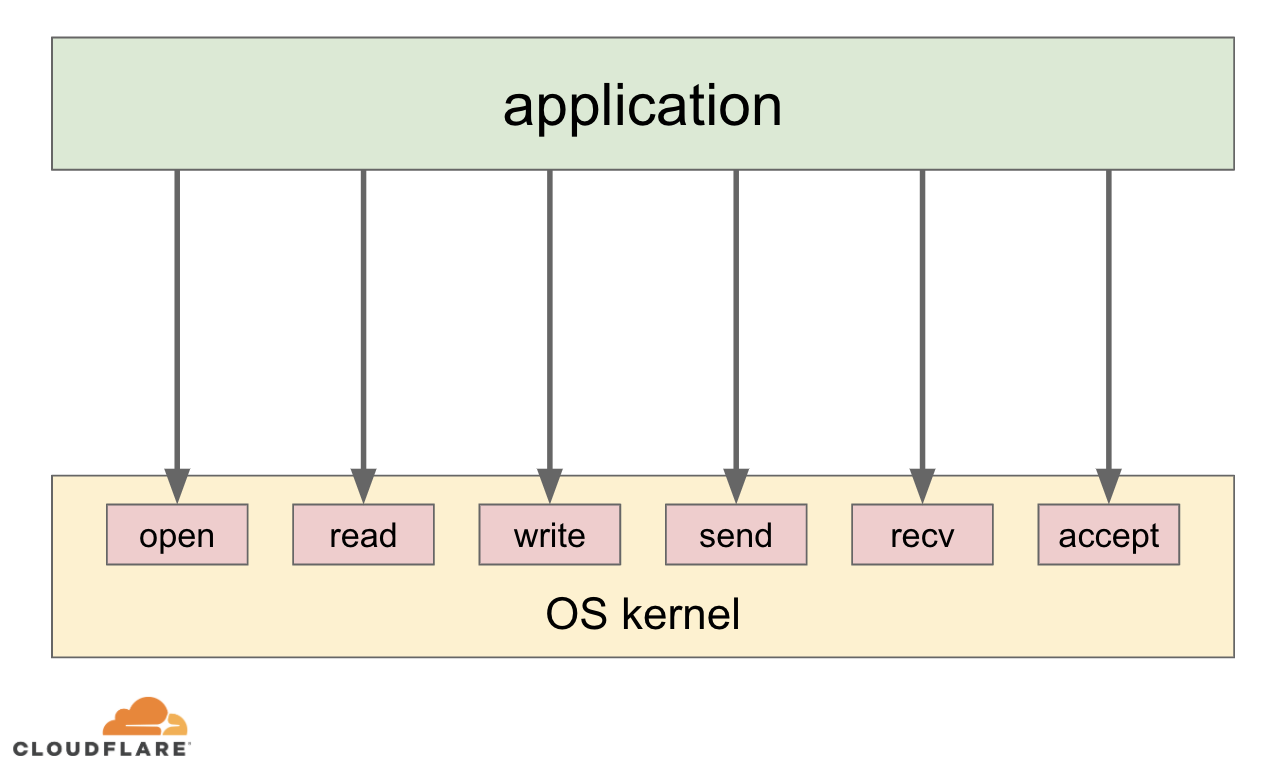
Apart from providing a generic high level way for applications to interact with the low level hardware, the system call architecture allows the OS kernel to manage available resources between applications as well as enforce policies, like application permissions, networking access control lists etc.
Linux seccomp
Linux seccomp is yet another syscall on Linux, but it is a bit Continue reading
CVE-2020-5902: Helping to protect against the F5 TMUI RCE vulnerability
Cloudflare has deployed a new managed rule protecting customers against a remote code execution vulnerability that has been found in F5 BIG-IP’s web-based Traffic Management User Interface (TMUI). Any customer who has access to the Cloudflare Web Application Firewall (WAF) is automatically protected by the new rule (100315) that has a default action of BLOCK.
Initial testing on our network has shown that attackers started probing and trying to exploit this vulnerability starting on July 3.
F5 has published detailed instructions on how to patch affected devices, how to detect if attempts have been made to exploit the vulnerability on a device and instructions on how to add a custom mitigation. If you have an F5 device, read their detailed mitigations before reading the rest of this blog post.
The most popular probe URL appears to be /tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp followed by /tmui/login.jsp/..;/tmui/util/getTabSet.jsp, /tmui/login.jsp/..;/tmui/system/user/authproperties.jsp and /tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp. All contain the critical pattern ..; which is at the heart of the vulnerability.
On July 3 we saw O(1k) probes ramping to O(1m) yesterday. This is because simple test patterns have been added to scanning tools and small test programs made available by Continue reading
Building Cloudflare TV from scratch


Cloudflare TV is inspired by television shows of the 90s that shared the newest, most exciting developments in computing and music videos. We had three basic requirements for Cloudflare TV:
- Guest participation should be as simple as joining a Zoom call
- There should be 24x7 programming. Something interesting should be playing all the time
- Everything should happen in the cloud and we should never have to ask anyone “to leave their computer on” to have the stream running 24 hours a day

We didn’t set out to build Cloudflare TV from scratch
Building a lot of the technology behind Cloudflare TV from scratch was not part of the plan, especially given our aggressive timeline. So why did we decide to pursue it? After evaluating multiple live streaming solutions, we reached the following conclusion:
- 24x7 linear streaming is not something that is a priority for most video streaming platforms. This makes sense: the rise of video-on-demand and event-based live streaming has come at the expense of linear streaming.
- Most broadcasting platforms have their own guest apps which must be downloaded and set up in advance. This introduces unnecessary friction compared to clicking a link in the calendar invite to join a Continue reading
Making the WAF 40% faster
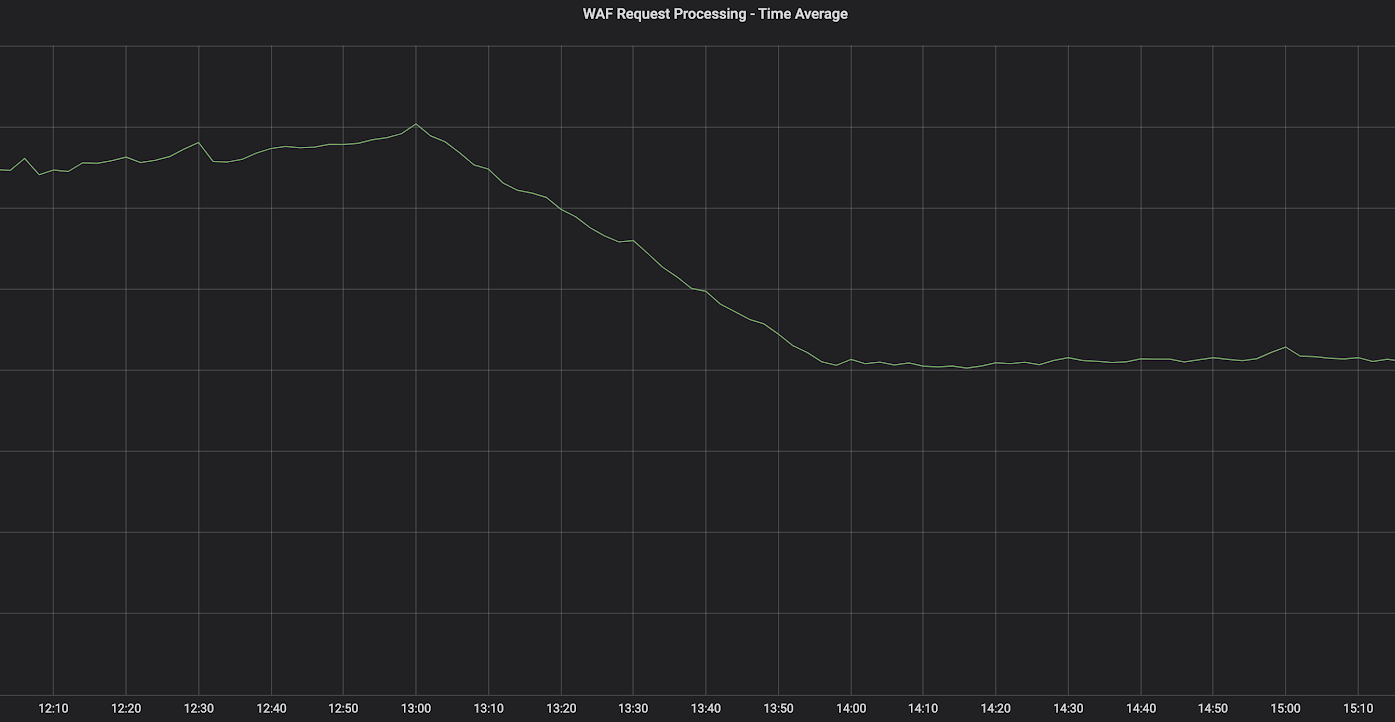
Cloudflare’s Web Application Firewall (WAF) protects against malicious attacks aiming to exploit vulnerabilities in web applications. It is continuously updated to provide comprehensive coverage against the most recent threats while ensuring a low false positive rate.
As with all Cloudflare security products, the WAF is designed to not sacrifice performance for security, but there is always room for improvement.
This blog post provides a brief overview of the latest performance improvements that were rolled out to our customers.
Transitioning from PCRE to RE2
Back in July of 2019, the WAF transitioned from using a regular expression engine based on PCRE to one inspired by RE2, which is based around using a deterministic finite automaton (DFA) instead of backtracking algorithms. This change came as a result of an outage where an update added a regular expression which backtracked enormously on certain HTTP requests, resulting in exponential execution time.
After the migration was finished, we saw no measurable difference in CPU consumption at the edge, but noticed execution time outliers in the 95th and 99th percentiles decreased, something we expected given RE2's guarantees of a linear time execution with the size of the input.
How to test HTTP/3 and QUIC with Firefox Nightly


HTTP/3 is the third major version of the Hypertext Transfer Protocol, which takes the bold step of moving away from TCP to the new transport protocol QUIC in order to provide performance and security improvements.
During Cloudflare's Birthday Week 2019, we were delighted to announce that we had enabled QUIC and HTTP/3 support on the Cloudflare edge network. This was joined by support from Google Chrome and Mozilla Firefox, two of the leading browser vendors and partners in our effort to make the web faster and more reliable for all. A big part of developing new standards is interoperability, which typically means different people analysing, implementing and testing a written specification in order to prove that it is precise, unambiguous, and actually implementable.
At the time of our announcement, Chrome Canary had experimental HTTP/3 support and we were eagerly awaiting a release of Firefox Nightly. Now that Firefox supports HTTP/3 we thought we'd share some instructions to help you enable and test it yourselves.
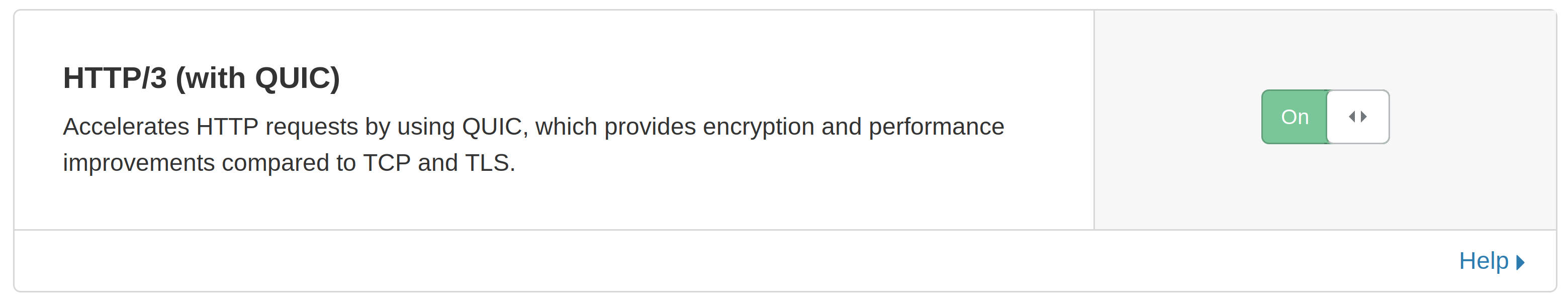
How do I enable HTTP/3 for my domain?
Simply go to the Cloudflare dashboard and flip the switch from the "Network" tab manually:
Using Firefox Nightly as an HTTP/3 client
Firefox Nightly has experimental support for Continue reading
Catching up with Workers KV


The Workers Distributed Data team has been hard at work since we gave you an update last November. Today, we’d like to share with you some of the stuff that has recently shipped in Workers KV: a new feature and an internal change that should significantly improve latency in some cases. Let’s dig in!
KV Metadata
Workers KV has a fairly straightforward interface: you can put keys and values into KV, and then fetch the value back out by key:
await contents.put(“index.html”, someHtmlContent);
await contents.put(“index.css”, someCssContent);
await contents.put(“index.js”, someJsContent);
// later
let index = await contents.get(“index.html”);
Pretty straightforward. But as you can see from this example, you may store different kinds of content in KV, even if the type is identical. All of the values are strings, but one is HTML, one is CSS, and one is JavaScript. If we were going to serve this content to users, we would have to construct a response. And when we do, we have to let the client know what the content type of that request is: text/html for HTML, text/css for CSS, and text/javascript for JavaScript. If we serve the incorrect content type to Continue reading
Introducing Regional Services
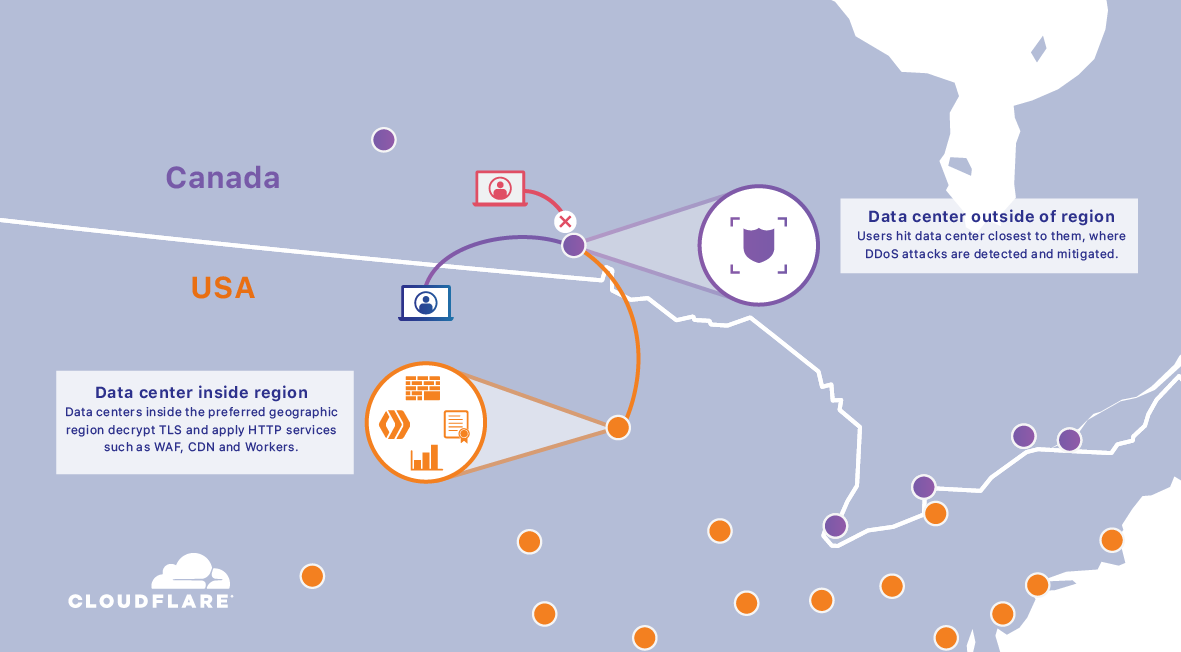
In a world where, increasingly, workloads shift to the cloud, it is often uncertain and unclear how data travels the Internet and in which countries data is processed. Today, Cloudflare is pleased to announce that we're giving our customers control. With Regional Services, we’re providing customers full control over exactly where their traffic is handled.
We operate a global network spanning more than 200 cities. Each data center runs servers with the exact same software stack. This has enabled Cloudflare to quickly and efficiently add capacity where needed. It also allows our engineers to ship features with ease: deploy once and it's available globally.
The same benefit applies to our customers: configure once and that change is applied everywhere in seconds, regardless of whether they’re changing security features, adding a DNS record or deploying a Cloudflare Worker containing code.
Having a homogenous network is great from a routing point of view: whenever a user performs an HTTP request, the closest datacenter is found due to Cloudflare's Anycast network. BGP looks at the hops that would need to be traversed to find the closest data center. This means that someone near the Canadian border (let's say North Dakota) could easily find Continue reading
Lessons from a 2020 intern assignment
This summer, Cloudflare announced that we were doubling the size of our Summer 2020 intern class. Like everyone else at Cloudflare, our interns would be working remotely, and due to COVID-19, many companies had significantly reduced their intern class size, or outright cancelled their programs entirely.
With our announcement came a huge influx of students interested in coming to Cloudflare. For applicants seeking engineering internships, we opted to create an exercise based on our serverless product Cloudflare Workers. I'm not a huge fan of timed coding exercises, which is a pretty traditional way that companies gauge candidate skill, so when I was asked to help contribute an example project that would be used instead, I was excited to jump on the project. In addition, it was a rare chance to have literally thousands of eager pairs of eyes on Workers, and on our documentation, a project that I've been working on daily since I started at Cloudflare over a year ago.
In this blog post, I will explain the details of the full-stack take home exercise that we sent out to our 2020 internship applicants. We asked participants to spend no more than an afternoon working on it, and Continue reading
Cloudflare and Rackspace Technology Expand Partnership with Managed Services


Last year, Cloudflare announced the planned expansion of our partner program to help managed and professional service partners efficiently engage with Cloudflare and join us in our mission to help build a better Internet. We’ve been hard at work growing and expanding our partnerships with some amazing global teams that help us support digital transformation and security needs around the world, and today we’d like to highlight one of our Elite global partners, Rackspace Technology.
Today, we are announcing the expansion of our worldwide reseller partnership with Rackspace Technology to include a series of managed services offerings for Cloudflare. As a result, with Cloudflare Security, Performance, and Reliability with Rackspace Managed Services, customers will not only have access to and the scalability of Cloudflare’s global network and integrated cloud platform of security, performance, and reliability solutions but also benefit from a team of certified, enabled Rackspace experts to configure, onboard, and deploy Cloudflare solutions. Because more than 1 billion unique IP addresses pass through Cloudflare's global network every day, Cloudflare, together with its solutions providers, can build real-world intelligence on the communications occurring over the Internet, and how well they perform. We’ve enjoyed enabling their teams to leverage this Continue reading
Why is there a “V” in SIGSEGV Segmentation Fault?


Another long night. I was working on my perfect, bug-free program in C, when the predictable thing happened:
$ clang skynet.c -o skynet
$ ./skynet.out
Segmentation fault (core dumped)
Oh, well... Maybe I'll be more lucky taking over the world another night. But then it struck me. My program received a SIGSEGV signal and crashed with "Segmentation Fault" message. Where does the "V" come from?
Did I read it wrong? Was there a "Segmentation Vault?"? Or did Linux authors make a mistake? Shouldn't the signal be named SIGSEGF?
I asked my colleagues and David Wragg quickly told me that the signal name stands for "Segmentation Violation". I guess that makes sense. Long long time ago, computers used to have memory segmentation. Each memory segment had defined length - called Segment Limit. Accessing data over this limit caused a processor fault. This error code got re-used by newer systems that used paging. I think the Intel manuals call this error "Invalid Page Fault". When it's triggered it gets reported to the userspace as a SIGSEGV signal. End of story.
Or is it?
Martin Levy pointed me to an ancient Version 6th UNIX documentation on "signal". This is Continue reading
Virtual Interning Offers Unique Challenges and Opportunities


I am in my third year at Northeastern University, pursuing an undergraduate degree in Marketing and Psychology. Five months ago I joined Cloudflare as an intern on the APAC Marketing team in the beautiful Singapore office. When searching for internships Cloudflare stood out as a place I could gain skills in marketing, learn from amazing mentors, and have space to take ownership in projects. As a young, but well-established company, Cloudflare provides the resources for their interns to work cross functionally and creatively and truly be a part of the exponential growth of the company.
My experience at Cloudflare
Earlier this week, I hopped on a virtual meeting with a few coworkers, thinking everything was set to record a webinar. As I shared my screen to explain how to navigate the platform I realised the set up was incorrect and we couldn’t start on time. Due to the virtual nature of the meeting, my coworkers didn’t see the panic on my face and had no idea what was going on. I corrected the issue and set up an additional trial run session, issuing apologies to both coworkers. They both took it in stride and expressed that it happens to the Continue reading
Introducing Cache Analytics
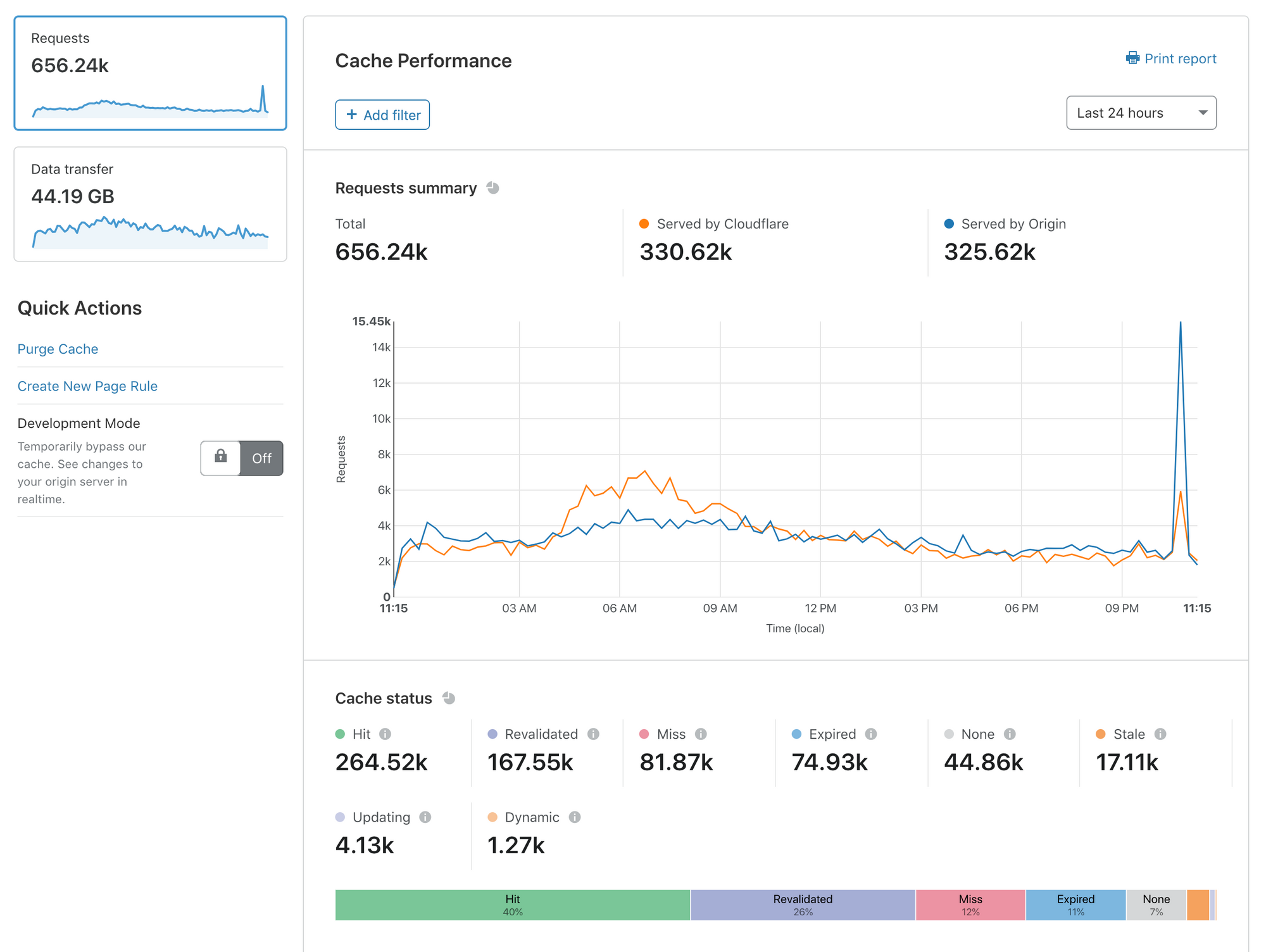
Today, I’m delighted to announce Cache Analytics: a new tool that gives deeper exploration capabilities into what Cloudflare’s caching and content delivery services are doing for your web presence.
Caching is the most effective way to improve the performance and economics of serving your website to the world. Unsurprisingly, customers consistently ask us how they can optimize their cache performance to get the most out of Cloudflare.
With Cache Analytics, it’s easier than ever to learn how to speed up your website, and reduce traffic sent to your origin. Some of my favorite capabilities include:
- See what resources are missing from cache, expired, or never eligible for cache in the first place
- Slice and dice your data as you see fit: filter by hostnames, or see a list of top URLs that miss cache
- Switch between views of requests and data Transfer to understand both performance and cost
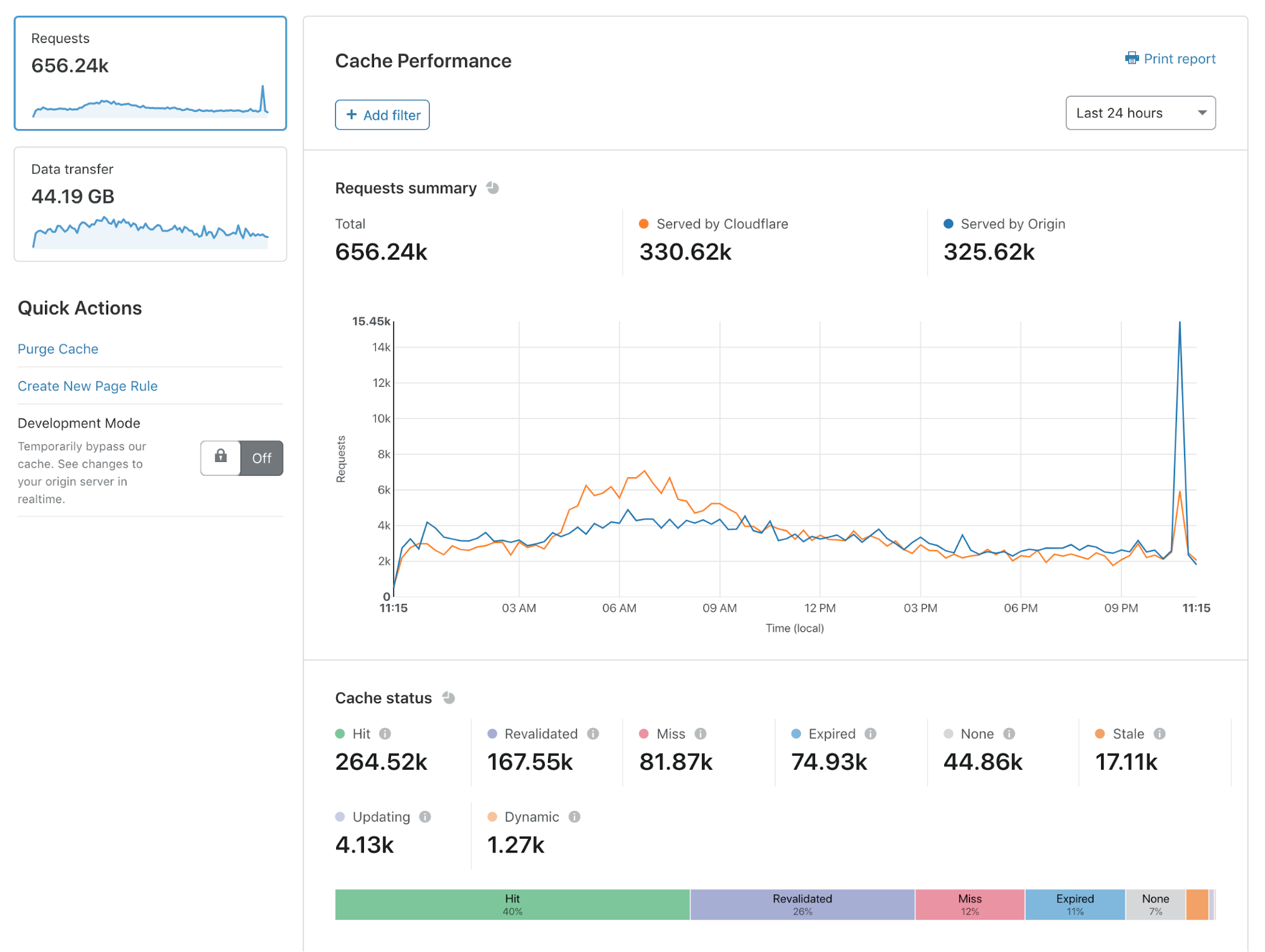
Cache Analytics is available today for all customers on our Pro, Business, and Enterprise plans.
In this blog post, I’ll explain why we built Cache Analytics and how you can get the most out of it.
Why do we need analytics focused on caching?
If you want Continue reading
Using data science and machine learning for improved customer support
In this blog post we’ll explore three tricks that can be used for data science that helped us solve real problems for our customer support group and our customers. Two for natural language processing in a customer support context and one for identifying attack Internet attack traffic.
Through these examples, we hope to demonstrate how invaluable data processing tricks, visualisations and tools can be before putting data into a machine learning algorithm. By refining data prior to processing, we are able to achieve dramatically improved results without needing to change the underlying machine learning strategies which are used.
Know the Limits (Language Classification)
When browsing a social media site, you may find the site prompts you to translate a post even though it is in your language.
We recently came across a similar problem at Cloudflare when we were looking into language classification for chat support messages. Using an off-the-shelf classification algorithm, users with short messages often had their chats classified incorrectly and our analysis found there’s a correlation between the length of a message and the accuracy of the classification (based on the browser Accept-Language header and the languages of the country where the request was submitted):
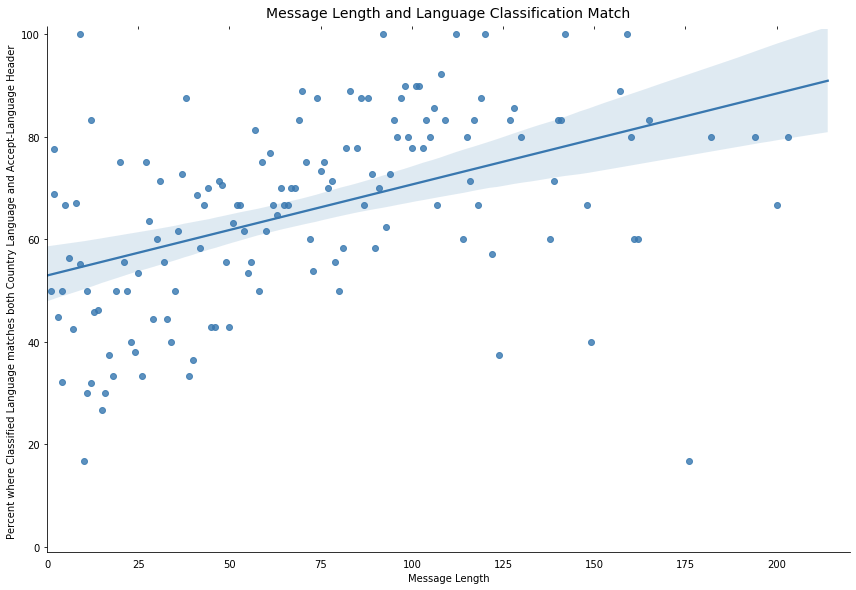
On a Continue reading
2020年第1四半期ネットワーク層DDoS攻撃の傾向


2020年第1四半期の締め括りにあたり、当社は、DDoS攻撃の傾向が、未曾有の世界的外出禁止令の中、変わったのかどうか、変わったのであればどのように変わったのかの把握に着手しました。それ以降、トラフィックレベルは多くの国で50%以上も増加していますが、DDoS攻撃も同様に増えているのでしょうか。
長期休暇の時期は、トラフィックの増加が見られます。この時期、世の中の人は、オンラインで買い物や食べ物を注文したり、オンラインゲームで遊んだり、その他オンラインでさまざまなことを楽しんでいるものです。使用量の増加は、種々多様なオンラインサービスを提供する企業にとって分刻みの収益増加につながります。
こうしたピーク時にダウンタイムやサービス低下が発生すると、あっという間にユーザーの解約や大規模な減収という事態になりかねません。ITICの見積もりでは、停止時の損失額は、1分あたり平均5,600ドルとなります。これは1時間あたり30万ドル以上の損失に相当します。したがって、長期休暇時期に攻撃者がDDoS攻撃の数を増やすことで、この機会を利用するのは驚くべきことではありません。
現在のコロナ禍は、同じような因果関係を持っています。多くの人が、家にいることを余儀なくされています。日々の仕事をこなすために、オンラインサービスへの依存度を高めている現状が、インターネットトラフィックとDDoS攻撃の急増を引き起こします。
小規模で短時間の攻撃の台頭
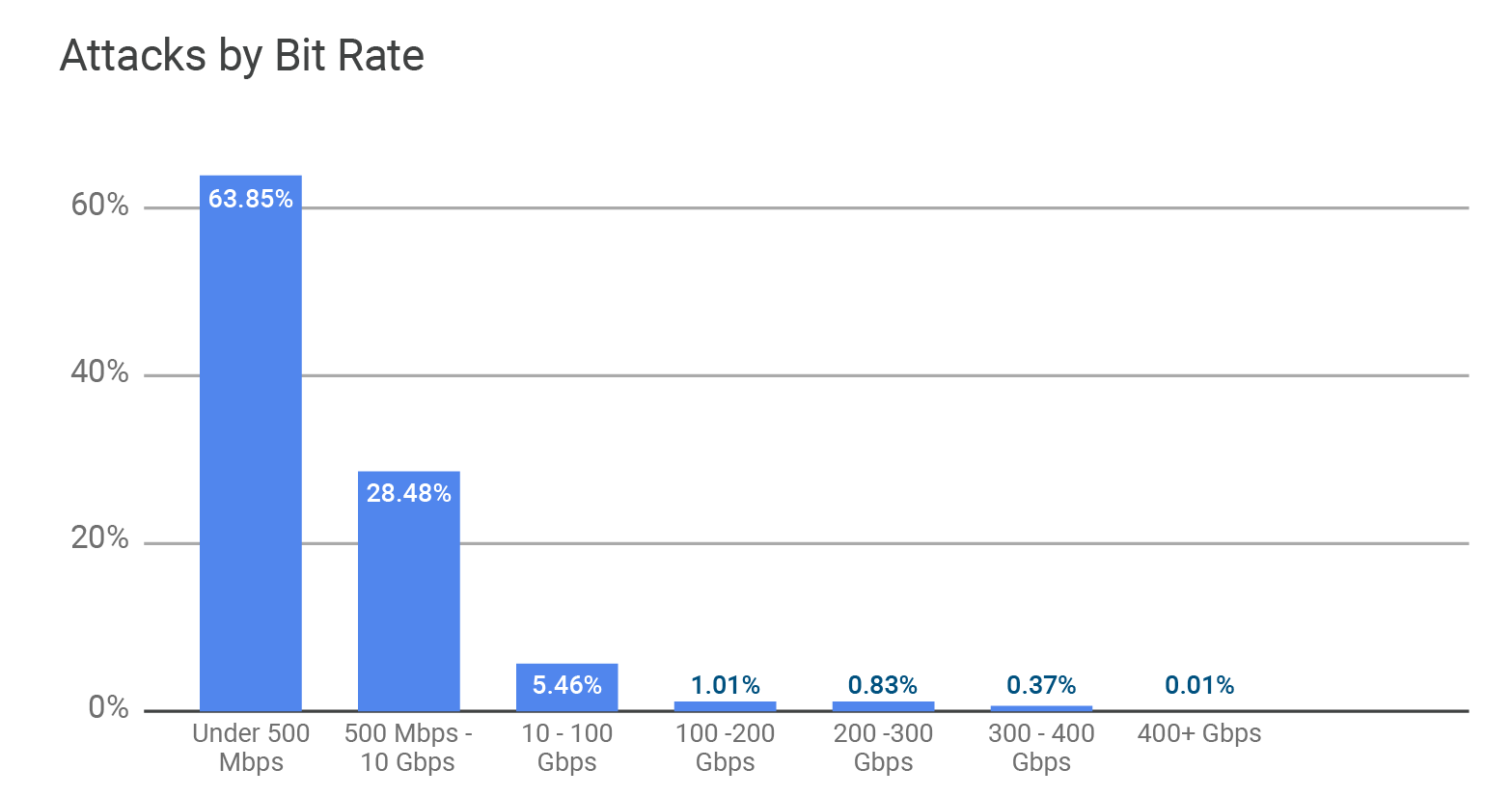
2020年の第1四半期に観測された攻撃のほとんどが、ビットレートで比較的小規模なものでした。次の図で示すように、10Gbps未満の攻撃が起きたのは、2020年第1四半期が92%、一方、2019年の第4四半期は、84%でした。
さらに深く掘り下げると、第1四半期の10Gbps未満の攻撃の分布には、前四半期と比較すると興味深い変化が見られます。前年第4四半期では、47%のネットワーク層DDoS攻撃の最大値は500Mbps以下であるのに対して、今年の第1四半期では、それが64%まで増加しています。
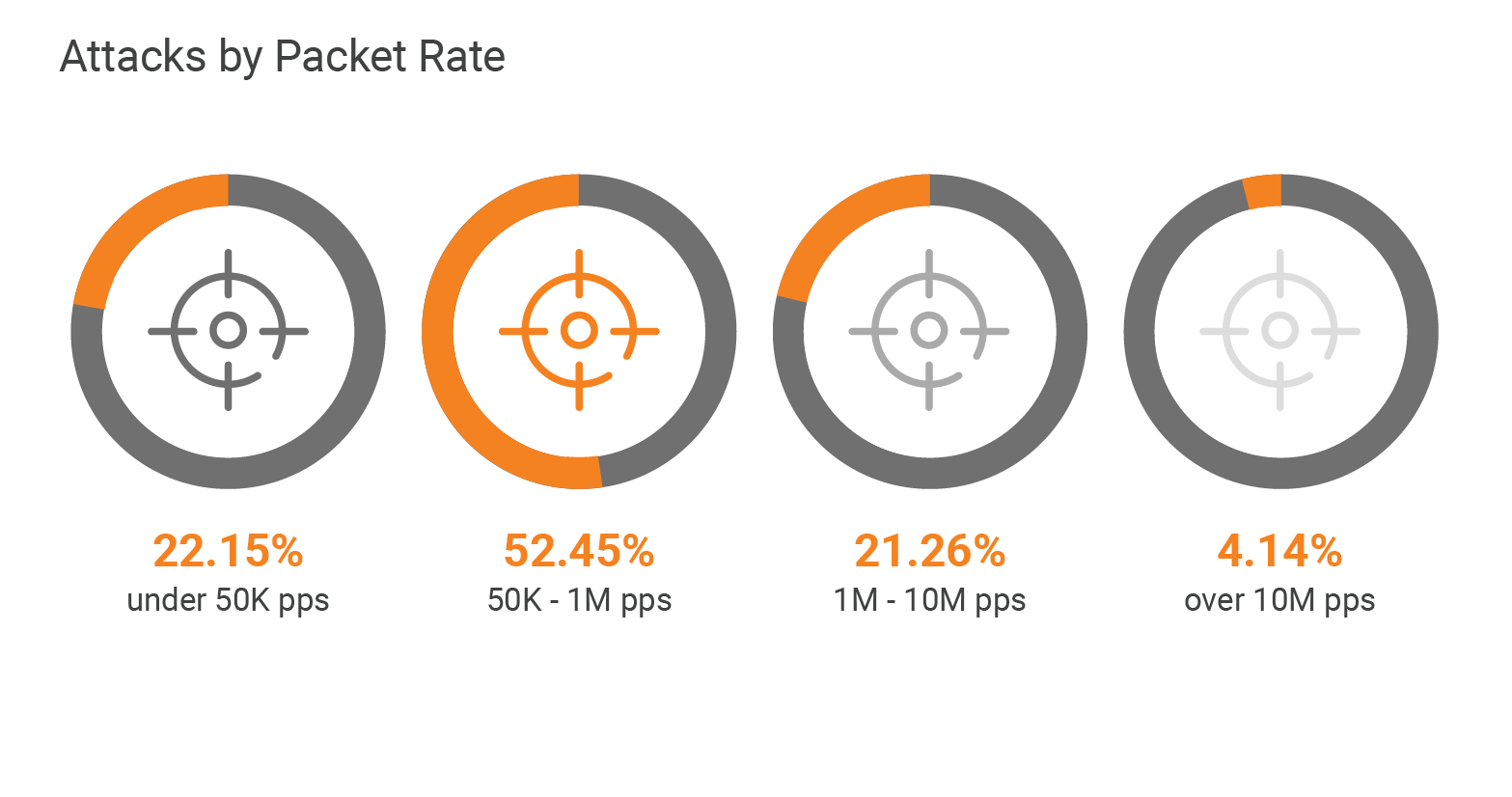
パケットレートの観点からは、攻撃の大部分で最大値は100万pps以下でした。ビットレートとともに、このレートは攻撃者が1秒あたり数ビットまたはパケットの高速フラッドを生成するために努力もリソースも集中させていないことを示しています。
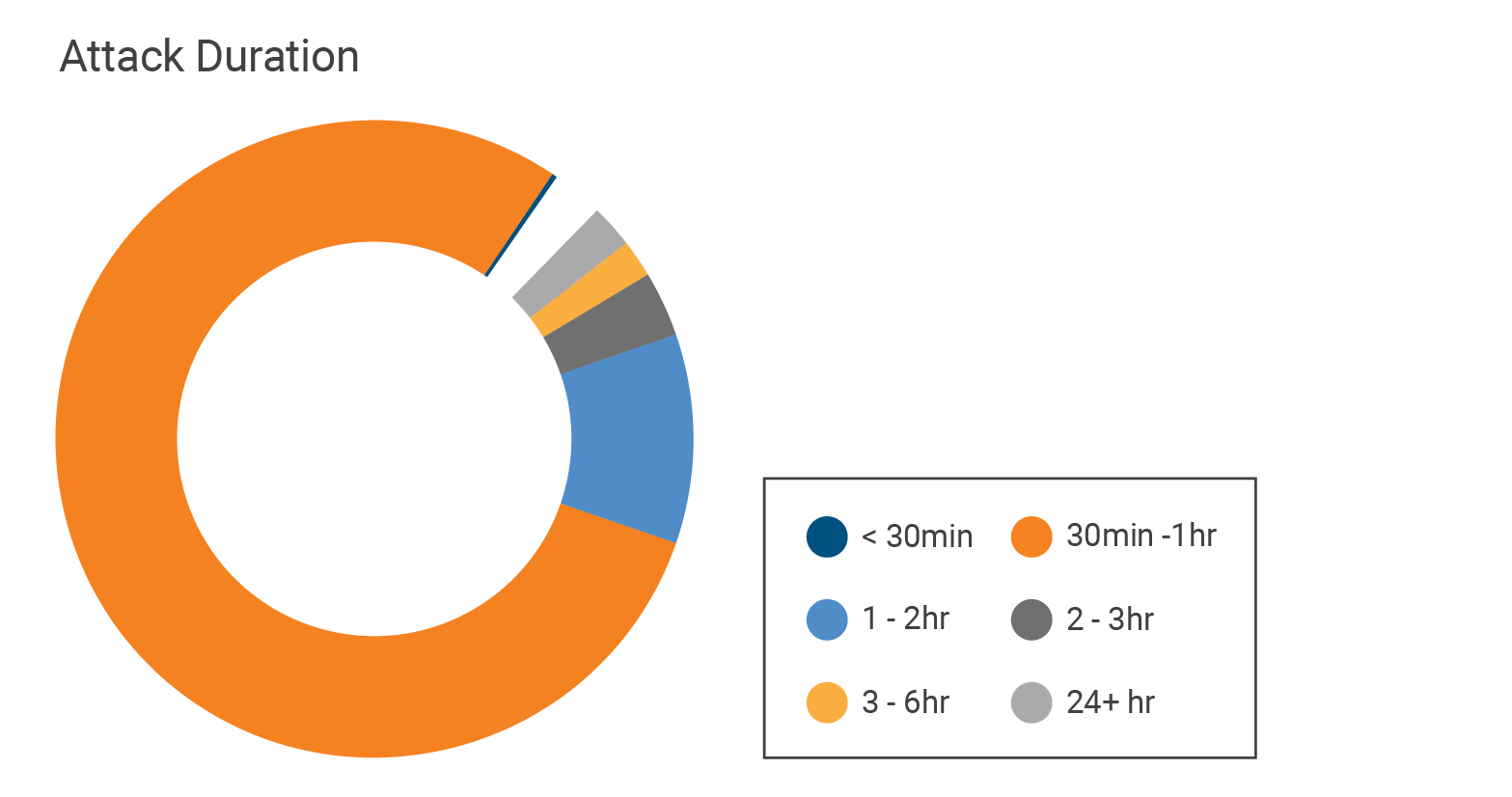
ところが、減少しているのはパケットとビットレートだけでなく、攻撃持続時間も減少しています。下の図を見ると、第1四半期に30~60分間続いたDDoS攻撃は79%で、第4四半期の60%から19%増加したことがわかります。
この3つの傾向は、次のように説明できます。
- DDoS攻撃を始めるのは安価で、技術的な知識はそれほど必要ではありません。DDoS-as-a-service(サービスとしてのDDoS攻撃)ツールは、専門知識を持たない悪者が費用対効果の高い方法で、帯域幅も多く使わずに迅速かつ簡単にDDoS攻撃を仕掛けることを可能にしました。Kaperskyによると、DDoS攻撃サービスは300秒間(5分間)の攻撃でわずか5ドルです。さらに、アマチュアの攻撃者でも簡単に無料ツールを使って、パケットのフラッドを引き起こすことができてしまいます。次のセクションで説明しますが、第1四半期の全DDoS攻撃のうち13.5%が一般に公開されているMiraiコードの変種を使って生成されていました。
- 10Gbps未満の攻撃は小さいように見えるかもしれませんが、未保護のインターネットプロパティに影響を与えるには十分な規模です。より小規模でより速い攻撃は、インターネットプロパティの可用性を妨害しない代わりに、攻撃者が企業から身代金を要求することのROIが高いということになるかもしれません。
大規模な攻撃は少数ながら依然として存在する
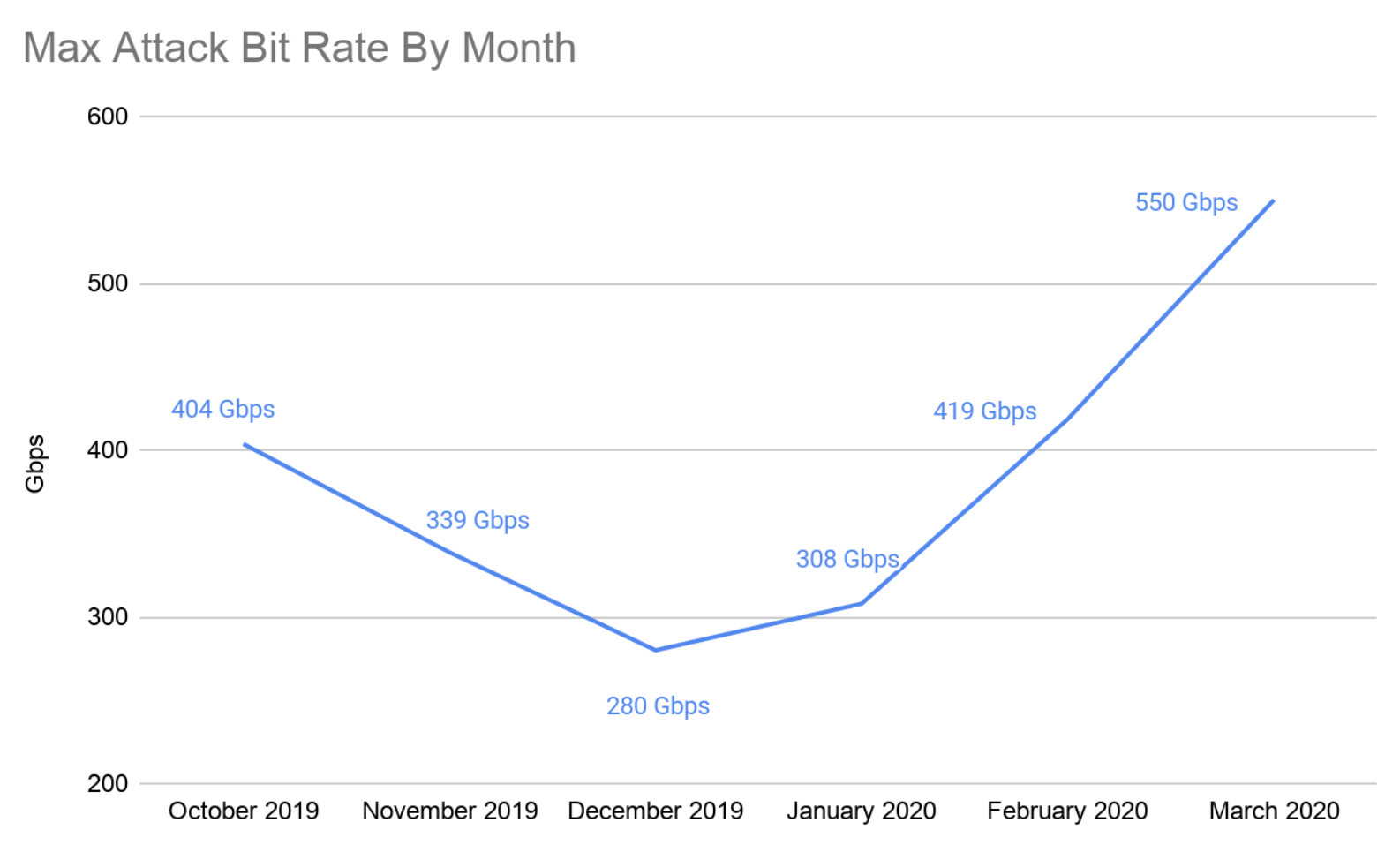
攻撃の大部分は10Gbps未満ですが、大規模な攻撃も依然として蔓延しています。以下のグラフでは、2019年第4四半期と2020年第1四半期にCloudflareが観測し、軽減したネットワーク層DDoS攻撃の最大ビットレートの傾向を示しています。今四半期に起きた最大の攻撃は3月に発生し、ピークは550Gbpsをわずかに上回りました。
失敗しても諦めず、再試行を繰り返す
しつこい攻撃者は、攻撃に失敗しても諦めないタイプです。何度も仕掛けてきます。ターゲットに向けて複数の攻撃を仕掛け、攻撃ベクトルを複数利用することもあります。2019年第4四半期の年末期間中に、攻撃者は単一のCloudflare IPに対して1日に523件ものDDoS攻撃をしつこく仕掛けてきました。攻撃下にあったCloudflare IPそれぞれが、毎日平均4.6ものDDoS攻撃の標的となりました。
各国で新型コロナウイルスによる都市封鎖が始まった第1四半期中、例年の月間平均と比べると、攻撃数に大幅な増加が見られました。このような増加を目の当たりにしたのは、2019年の第4四半期以来です。ただし、そこには興味深い違いがあり、現在の攻撃は年末時期より持続性が低かったように見えました。2020年第1四半期、各Cloudflare IPアドレスへの1日あたりの攻撃の持続率は2.2件まで低下しており、単一IPアドレスへの攻撃の最大数は311件でした。これは前期の年末時期に比べ40%の削減でした。
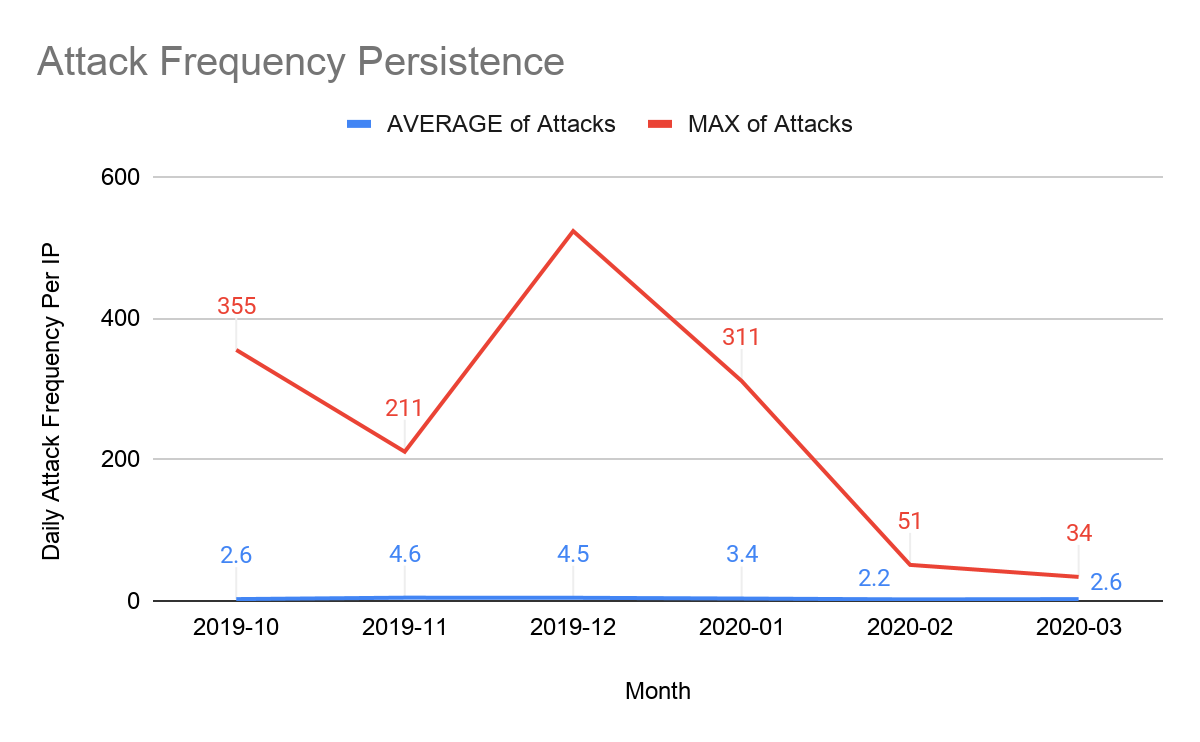
過去2四半期にわたり、1日あたりIPごとのDDoS攻撃で使われた攻撃ベクトルの平均数はほぼ一定して約1.4で、最大数は10でした。

この四半期では、第3/4層で34種類の攻撃ベクトルが見られました。ACK攻撃は第1四半期の最大数(50.1%)を占め、次はSYN攻撃の16.6%でした。第3位はMiraiで、それでも攻撃の大きな割合(15.4%)を占めています。SYN攻撃とACK DDoS攻撃(TCP)を合わせると、第1四半期の第3/4層への全攻撃ベクトルの66%となります。
攻撃ベクトルのトップ
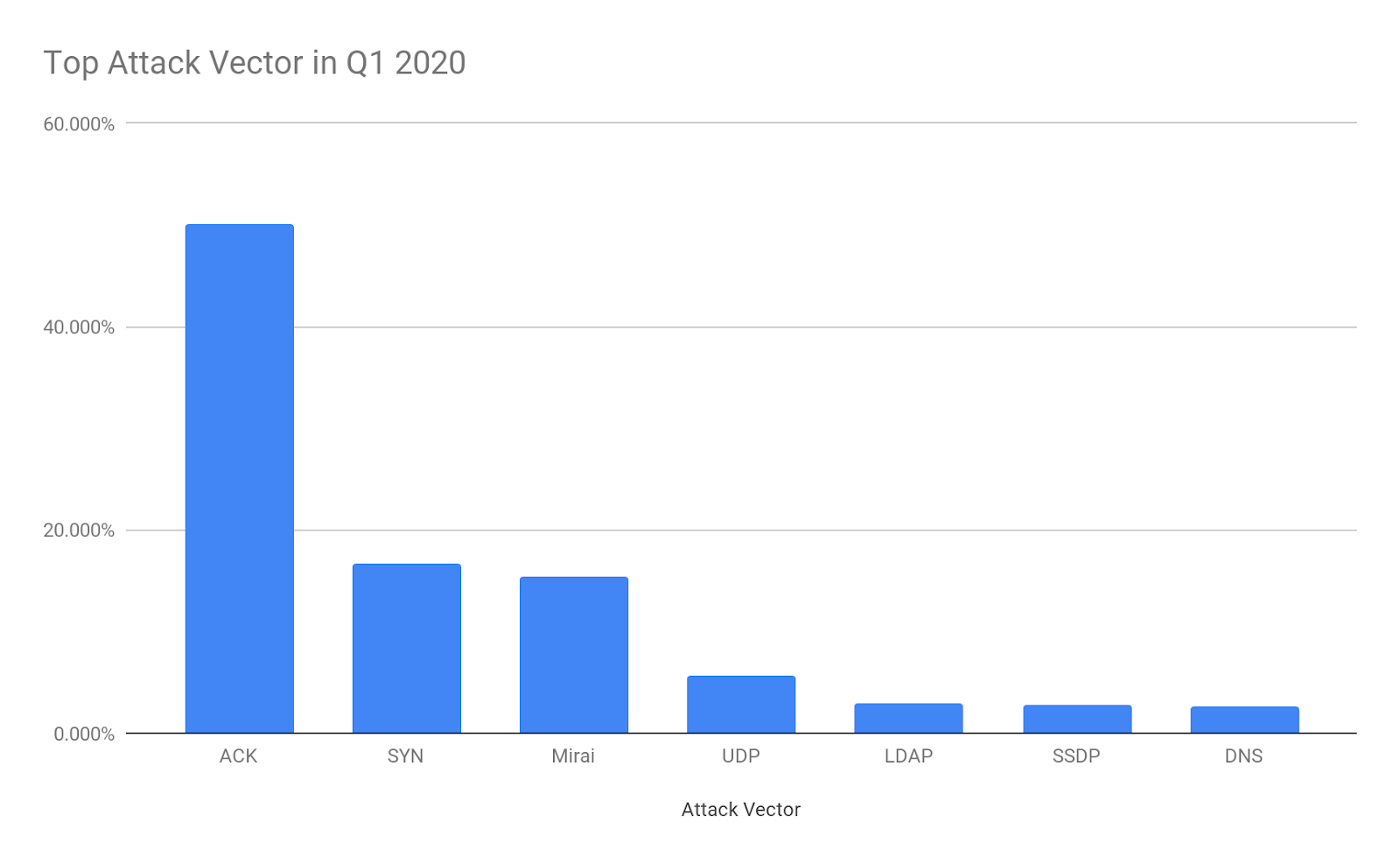
すべての攻撃ベクトル
| Attack Vector | Percent in Q1 |
|---|---|
| ACK | 50.121% |
| SYN | 16.636% |
| Mirai | 15.404% |
| UDP | 5.714% |
| LDAP | 2.898% |
| SSDP | 2.833% |
| DNS | 2.677% |
| Other | 0.876% |
| QUIC | 0.527% |
| NTP | 0.373% |
| RST | 0.353% |
| Memcached | 0.296% |
| ChargeGen | 0.236% |
| WS Discovery | 0.221% |
| ACK-PSH | 0.208% |
| SNMP | 0.159% |
| VSE | 0.081% |
| MSSQL | 0.079% |
| ICMP | 0.072% |
| Bittorrent | 0.056% |
| OpenVPN | 0.046% |
| Dahua | 0.032% |
| GRE | 0.022% |
| TFTP | 0.014% |
| LOIC | 0.014% |
| STUN | 0.011% |
| Lantronix | 0.009% |
| CoAP | 0.008% |
| Jenkins | 0.006% |
| VXWorks | 0.005% |
| Ubiquity | 0.005% |
| TeamSpeak | 0.004% |
| XMAS | 0.003% |
| SPSS | 0.001% |
残念なことに、危機的状況とは時に悪意の好機である
2020年3月のDDoS攻撃数は、1月と2月と比較して増加しました。以下に示されるように、この危機的時期を、攻撃者はDDoS攻撃を増やす絶好の機会であると考えました。

さらに、各国の政府当局が都市封鎖と一時待機の義務づけを始めたのに合わせて、攻撃者は3月下旬に大規模な攻撃を増加させに至りました。3月の後半(3月16~31日)には、前半(3月1~15日)に比べて検出された攻撃は55%も増加していました。さらに、300-400 Gbpsをピークとする攻撃の94%が3月中に発生したものでした。
規模に関わりなく、ソースにより近くでDDoS攻撃を阻止
DDoSの状況は常に変化しており、包括的で適応性の高いDDoS保護ソリューションを備えることが重要です。上記の攻撃への洞察の観点から、ここではCloudflareがお客様を保護するために、こうした変化に対して機先を制していく方法をご紹介しましょう。
- 攻撃の速度も持続時間も短縮を続け、今までのベンダーが提示してきたような、最大15分の軽減時間のSLAは、実用性がありません。Cloudflareは、多くの場合、ネットワーク層DDoS攻撃を10秒未満で軽減します。これはますます短くなる攻撃に対抗するために重要です。こちらで最新のDDoS攻撃検出と軽減システムについてお読みください。このシステムでは、DDoS攻撃の自動検出と軽減を迅速に、かつ大規模に行うことができます。
- 近年より多くのDDoS攻撃がローカライズされています。つまり、スクラビングセンターアプローチを採用する従来のDDoSソリューションは、グローバルなカバレッジに制限があると同時に、DDoSトラフィックをセンター経由で動かす必要があるためチョークポイントとなり、実用性が低いということになります。Cloudflare独自の分散型アーキテクチャは、世界200都市に広がり、完全なDDoS対策機能を提供して、データセンター全てを強化します。
- 大規模に分散された帯域幅消費型攻撃はまだ存在し、チャンスが増えたとき、高い処理能力を持った攻撃者に使われてしまいます。1Tbpsを超える攻撃が将来的に予想されるため、大規模なDDoS攻撃を軽減する能力は、今日のDDoSソリューションにとって大切です。Cloudflareは、最大規模のDDoS攻撃でさえも軽減することが可能となる35Tbpsを超える容量を持つ世界で最も相互接続しているネットワークの一つです。この大規模なネットワーク容量と世界的に分散されたアーキテクチャによって、Cloudflareはどのような規模でも、ソースに近いところで攻撃を軽減することができます。
CloudflareのDDoSソリューションの詳細は、こちらにお問い合わせいただくか、今すぐ始めましょう。
Health Check Analytics and how you can use it
At the end of last year, we introduced Standalone Health Checks - a service that lets you monitor the health of your origin servers and avoid the need to purchase additional third party services. The more that can be controlled from Cloudflare decreases maintenance cost, vendor management, and infrastructure complexity. This is important as it ensures you are able to scale your infrastructure seamlessly as your company grows. Today, we are introducing Standalone Health Check Analytics to help decrease your time to resolution for any potential issues. You can find Health Check Analytics in the sub-menu under the Traffic tab in your Cloudflare Dashboard.
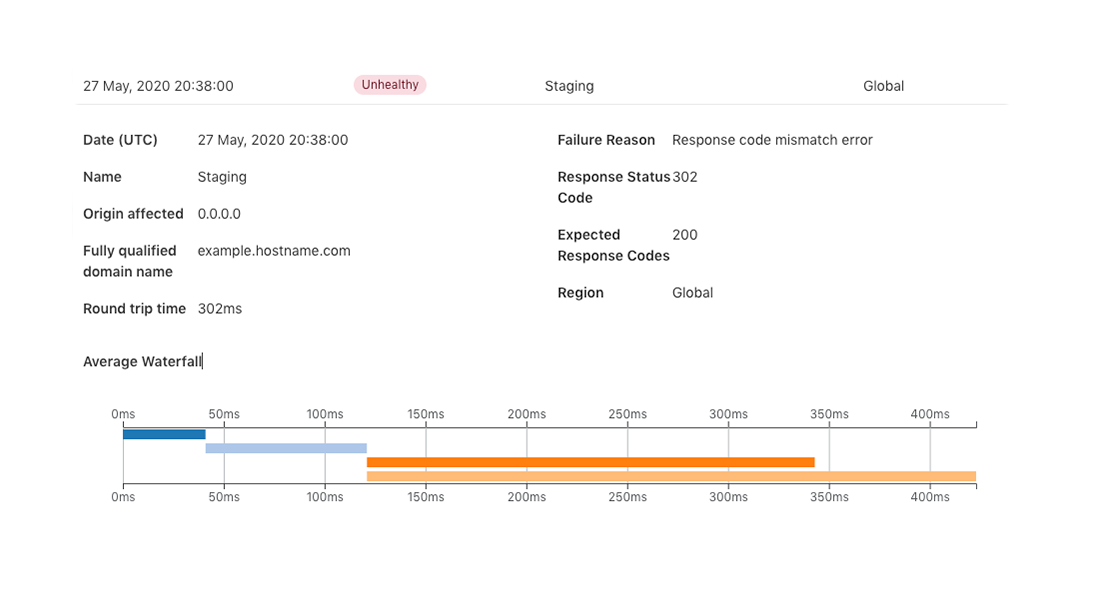
As a refresher, Standalone Health Checks is a service that monitors an IP address or hostname for your origin servers or application and notifies you in near real-time if there happens to be a problem. These Health Checks support fine-tuned configurations based on expected codes, interval, protocols, timeout and more. These configurations enable you to properly target your checks based on the unique setup of your infrastructure. An example of a Health Check can be seen below which is monitoring an origin server in a staging environment with a notification set via email.
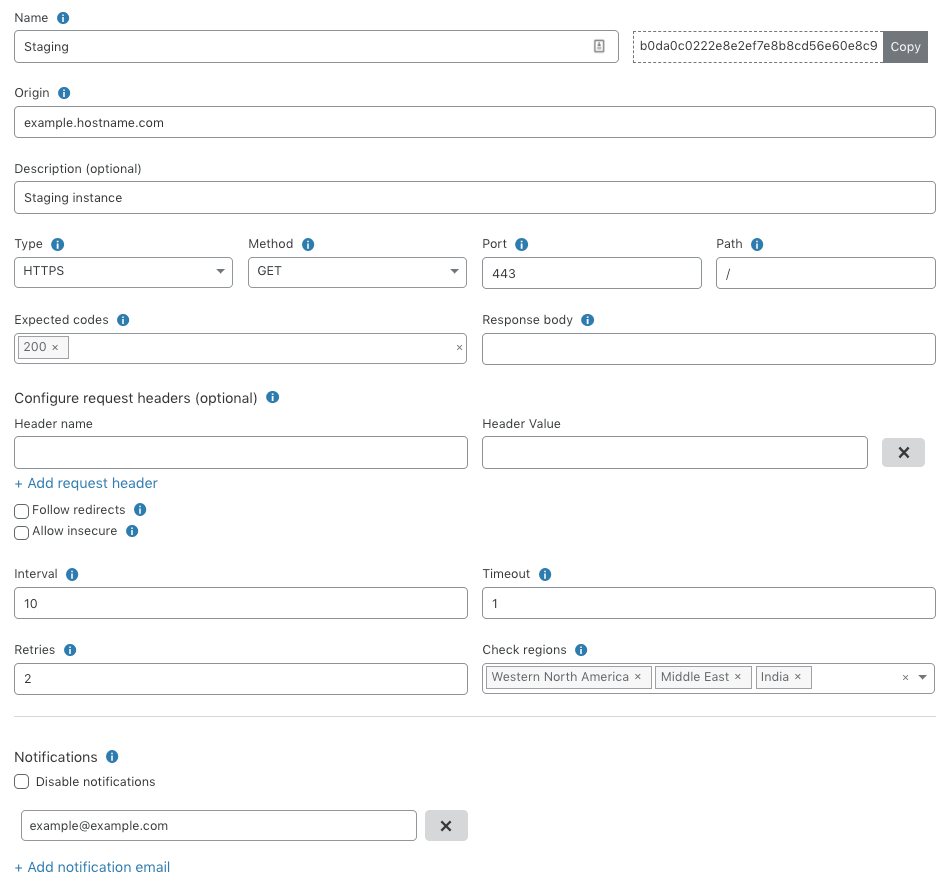
Once you set Continue reading
Project Galileo’s 6th year Anniversary: The Impact of COVID-19 on the most vulnerable groups on the Internet


Consistent with our mission to “help build a better Internet,” Cloudflare believes that one of the most important roles for the Internet is to empower marginalized voices that may not be heard, or bring together oppressed groups of people that may otherwise find themselves isolated and alone. Six years ago, Cloudflare started Project Galileo to provide free services to vulnerable nonprofits, journalism and independent media voices online who might otherwise be in danger of being silenced by cyberattacks. Much has changed in the past couple of months as the COVID-19 pandemic has transformed the world while the United States faces a wave of protests addressing racial violence and inequality. These events have put further strain on vulnerable groups working in these spaces, and we have seen many organizations step up to ensure that those who are most affected by these circumstances are protected. At Cloudflare, we believe that protecting these groups from attack is essential to helping build a better Internet.
We are excited to mark the 6th anniversary of the project this month, and it is a good time for us to reflect, talk to participants, and see how the Project has grown and changed over the course of Continue reading
High Availability Load Balancers with Maglev

Background

We run many backend services that power our customer dashboard, APIs, and features available at our edge. We own and operate physical infrastructure for our backend services. We need an effective way to route arbitrary TCP and UDP traffic between services and also from outside these data centers.
Previously, all traffic for these backend services would pass through several layers of stateful TCP proxies and NATs before reaching an available instance. This solution worked for several years, but as we grew it caused our service and operations teams many issues. Our service teams needed to deal with drops of availability, and our operations teams had much toil when needing to do maintenance on load balancer servers.
Goals
With the experience with our stateful TCP proxy and NAT solutions in mind, we had several goals for a replacement load balancing service, while remaining on our own infrastructure:
- Preserve source IPs through routing decisions to destination servers. This allows us to support servers that require client IP addresses as part of their operation, without workarounds such as X-Forwarded-For headers or the PROXY TCP extension.
- Support an architecture where backends are located across many racks and subnets. This prevents solutions that cannot Continue reading
7 Layers: IoT Part 2 — IoT Devices are Dangerously Insecure
This week is the second in a two-part series on the Internet of Things. We cover IoT security...
UtahFS: Encrypted File Storage
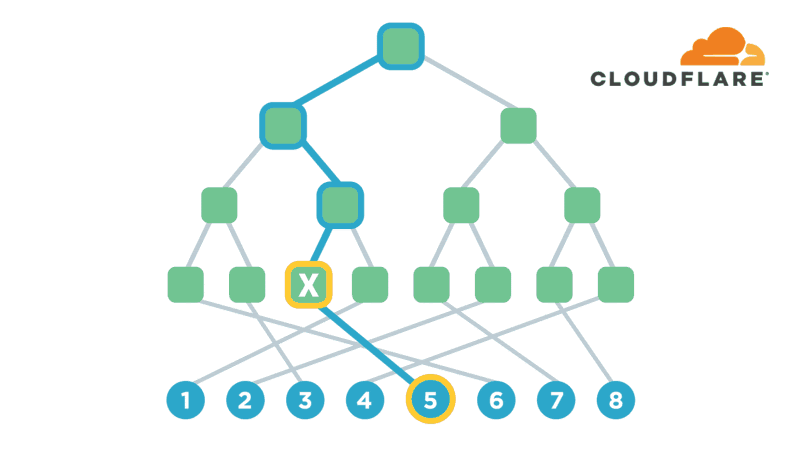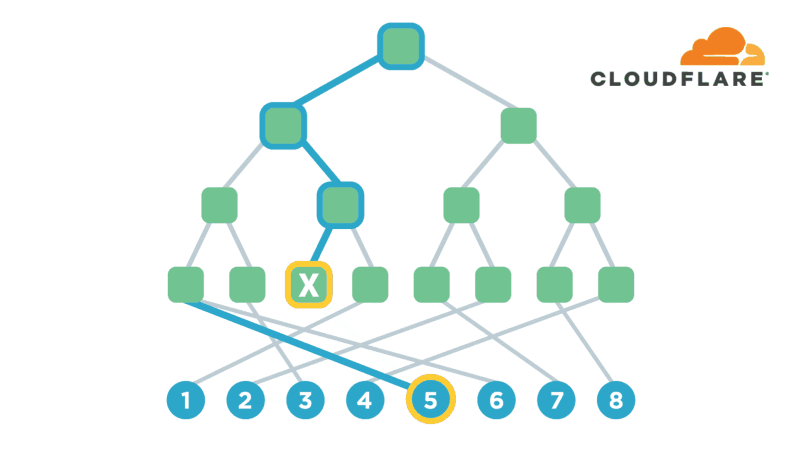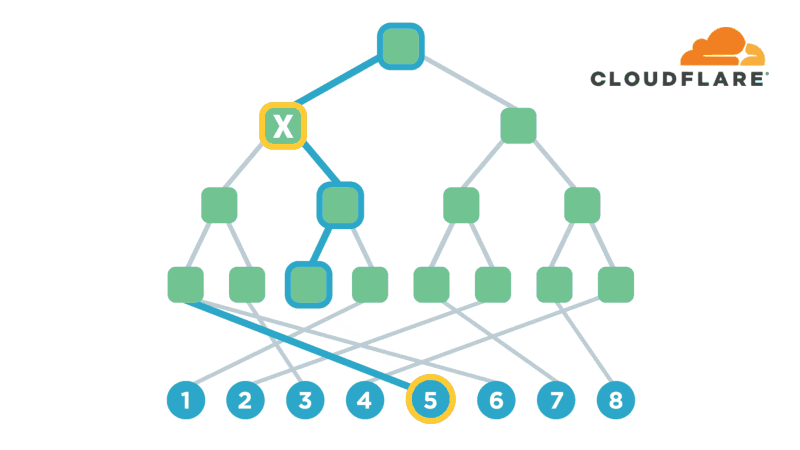
Encryption is one of the most powerful technologies that everyone uses on a daily basis without realizing it. Transport-layer encryption, which protects data as it’s sent across the Internet to its intended destination, is now ubiquitous because it’s a fundamental tool for creating a trustworthy Internet. Disk encryption, which protects data while it’s sitting idly on your phone or laptop’s hard drive, is also becoming ubiquitous because it prevents anybody who steals your device from also being able to see what’s on your desktop or read your email.
The next improvement on this technology that’s starting to gain popularity is end-to-end encryption, which refers to a system where only the end-users are able to access their data -- not any intermediate service providers. Some of the most popular examples of this type of encryption are chat apps like WhatsApp and Signal. End-to-end encryption significantly reduces the likelihood of a user’s data being maliciously stolen from, or otherwise mishandled by a service provider. This is because even if the service provider loses the data, nobody will have the keys to decrypt it!
Several months ago, I realized that I had a lot of sensitive files on my computer (my diary, if Continue reading
Ladies and Gentlemen… Cloudflare TV!


I'm excited to announce the upcoming launch of Cloudflare TV. A 24x7 live television broadcast, streamed globally via the Cloudflare network. You can tune in to the pre-broadcast station and check out the upcoming schedule at: cloudflare.tv
I'm kicking off the first live broadcast starting at 12:00pm Pacific (1900 UTC) on Monday, June 8 with a conversation with Chris Young (add to calendar). Chris was most recently the CEO of McAfee and has had a career defining the cyber security industry, from his own startup Cyveillance in the 1990s, to leadership positions at AOL, RSA, VMWare, Cisco, and Intel. I hope you'll tune in and then stay tuned for all the content our team has in store.
Which leaves the question: why on earth is Cloudflare launching a 24x7 television station?
The Uniting Power of Television and Tech Conferences
I was born in the 70's, am a child of the 80's, and got started in my career in the 90's. In the background, throughout much of it, was linear television we watched together. Over the last few months I've learned that Michelle Zatlyn, my co-founder and Cloudflare's COO, and I shared a love of Children's Television Network's Continue reading