Asset Inventories
How do you know what you need to apply your PCI DSS controls to? Simple, you check your asset inventory. You do have one, right? You know, PCI DSS requirement 2.4? Oh. You haven’t got one, have you.
Never fear, creating one is relatively simple providing you know your scope. Creating the asset inventory is really just a case of listing all the components that are in-scope for you. What should you include though?
Well, all system components so that’s things like network devices, firewalls, servers, desktops, laptops, wireless access points (important enough they get their own requirement, 11.1.1) and POI machines. You should also include at least key software that is used within your environment (think operating systems, payment applications, server software etc.)

You also need to include enough information to satisfy PCI DSS so for each item that is:
- Enough information to uniquely identify the component (host…
View original post 263 more words
PenTest Edition: Cracking WEP, WPS, WPA, and WPA2 Wi-Fi Networks with the “Fern Wi-Fi Cracker” Tool
Here’s a fun assessment you can perform on your home network. I’m running Kali Linux 2018.1 in a virtual machine using VMware Workstation Player. My wireless network adapter is an Alfa AWUS036NHA with a 9dBi omni-directional antenna. Penetration testers may use the Fern Wi-Fi cracker as a security auditing tool to test the security of an organization’s wireless network.
Disclaimer:
The information provided on the cybersecurityman is for educational purposes only. I am in no way responsible for any misuse of the information provided. All the information here is meant to provide the reader with the knowledge to defend against hackers and prevent the attacks discussed here. At no time should any reader attempt to use this information for illegal purposes.
The “Fern Wi-Fi Cracker” tool, from hereon abbreviated as “FWC,” is a security auditing and attack software program provided in the Kali Linux distribution. FWC has the ability to…
View original post 1,225 more words
Streamline the PCI Assessment Process with a Playbook
Why Create a PCI Assessment Playbook
Having gone through the Payment Card Industry Data Security Standard (PCI DSS) yearly assessment process several times, I can confirm it is a fairly intensive assessment that will require a large effort from a lot people!
Each assessment the Assessors will request evidence, review documentation, ask for sample system configurations, be onsite to interview and observe personnel, and present observations or findings that must be remediated. These various assessment activities and last-minute remediation efforts can be very disruptive to all involved, and usually result in “fire drill” activities that require personnel to be pulled away from their daily tasks to react to the assessment requests.
Since the PCI assessment is very similar from year to year, and with some well thought out planning it is possible to streamline the assessment process. Just like in football, having a well thought out strategy in the form of a playbook can assist everyone that needs to know their part, or what needs to be done when. With this cylinder process in place and in the form of a PCI Assessment Playbook that everyone can follow, it can greatly reduce the stress historically associated with the assessment and attaining Continue reading
The Great Multi-Factor Authentication Debate — PCI Guru
The Council brings back the Assessor Session to this year’s Community Meeting and it takes only one question to get passions flowing. The question was to get a clarification of a comment made by Ralph Poore, Director, Emerging Standards at the Council, about multi-factor authentication (MFA). First a little background to get everyone up to […]
via The Great Multi-Factor Authentication Debate — PCI Guru
The Importance of System Hardening
Most operating systems are not very secure out of the box and favor convenience and ease of use over security. IT Security professionals may not agree with a vendor’s user friendly approach to their OS, but that does not mean they have to accept it. There are steps that can be taken to harden a system and eliminate as many security risks as possible
System Hardening Examples
The most basic hardening procedure is to change the vendor default user name and password. You would be surprised how many vendor default access codes can found with a simple Google search!
System hardening can include configuration settings to remove unnecessary services, applying firewall rules, enforcing password complexity, setting failed login thresholds, and system idle time outs.
System hardening can also include installing an anti-virus program, forwarding logs to a centralized log management solution, and applying vendor released system patches.
Basically system hardening is a way to lock down the Operating System before the system goes into production. The hardening guides can not only detail the steps to follow to secure a system, but can complement any system deployment guides. Along with the list of procedures to follow to improve system security the hardening Continue reading
Installation Guide for Kali Linux
Originally posted on MakeThingsEasy:
Introducing Kali Linux
The creators of BackTrack have released a new, advanced penetration testing Linux distribution named Kali Linux. BackTrack 5 was the last major version of the BackTrack distribution. The creators of BackTrack decided that to move forward with the challenges of cyber security and modern testing a new foundation was needed. Kali Linux was born and released March 13th 2013. Kali Linux is based on Debian and an FHS-Compliant file system.
Kali has many advantages over the BackTrack. It comes with many more updated tools. The tools and streamlined with Debian repositories and synchronized four times a day. That means users have the latest package updates and security fixes. The new compliant file systems translate into running most tools from anywhere on the system. Kali has also made customization, unattended installation, and flexible desktop environments and strong feature in Kali Linux.
View original 858 more words
IT Security Skills Anyone Can and Should Learn
I’ve been teaching IT security awareness for several years and I try to get those in attendance of the classes to learn some basic IT security skills. These basic skills build on each other and there is some cross over, but ultimately this blended set of security skills can help anyone stay safe online. As with any sport you always start by learning the fundamentals, and while no one skill can get you into the game or keep you safe online, they can definitely make you ready for either.
Physical Security
With free Wi-Fi available in coffee shops and many fast food restaurants I constantly see people leaving their devices unattended and this lapse can allow someone to walk off with the device unnoticed. Think about your device and the amount of data it may contain. The device may have your whole world stored on it! If someone takes your laptop, tablet, or phone it is so much more than having the device stolen, but the data it contains. Besides this Wi-Fi example other scenarios to pay attention to your device is when going through airport security or leaving the device in plain site while stored in the car. Continue reading
Complete Detailed Guide on Installing Kali linux in Vmware
Great set of instructions for installing Kali Linux in VMware Player.
Originally posted on Cyber Warrior+:
First we need to download Kali from http://kali.org/downloads/. If you have a 64-bit capable computer (like me), then you probably will want the 64-bit version of Kali for performance reasons. Expand the drop down menu’s to find the version you need. Select the 64-bit version ONLY if you have a 64-bit computer.


View original 968 more words
What’s in a Name?
 Most home users select their wireless network name without much thought to the actual name except to make it easy for them to see and connect to. So many people never think that the networks name also known as the Service Set Identifier or SSID could be a security risk. Okay, a security risk may be a reach, but let’s just say some SSIDs are more secure than others, and I will list some dos and don’ts when selecting an SSID.
Most home users select their wireless network name without much thought to the actual name except to make it easy for them to see and connect to. So many people never think that the networks name also known as the Service Set Identifier or SSID could be a security risk. Okay, a security risk may be a reach, but let’s just say some SSIDs are more secure than others, and I will list some dos and don’ts when selecting an SSID.
Before the list lets discuss what makes the SSID important. Hackers need to gather several pieces of information including the SSID to crack a networks WPA/WPA2 password. Hackers have pre-configured tables with this information including common or default SSID names and if you’re using one of these common names you have made their job easier and your network more of a target.
- Do change the SSID from the factory set default wireless network name.
- Don’t select a name in top 1000 most common SSIDs. Now this list is very long and at first glance you will notice a lot of factory given default names (dlink, Linksys, 2wire, Netgear, etc…), so as mentioned above change the default name.
- Don’t use your Continue reading
The To DS and From DS Fields
Currently I’m studying for the Certified Wireless Analysis Professional (CWAP) exam and I’m rereading the study guide and I found the chapters that examined the different fields and elements present in the MAC header most interesting. I had a rough idea, but during my studies learned a great deal more about the unique fields and elements dedicated to wireless that keep the network functioning and help packets get delivered. Two fields of particular interest are the To Distribution System (To DS) and From Distribution System (From DS) and how these fields determine if the frame is leaving or entering the wireless environment.
Distribution System
Just a quick definition of the distribution system and basically the DS is the infrastructure that connects multiple access points together to form an Extended Service Set (ESS). The DS is typically an 802.3 Ethernet wired network, but it doesn’t have to be, and the DS can even be a wireless back haul.
MAC Header & Frame Control Field
Lets now look at the MAC header which can contain four address fields. The number of address fields is a major difference between Ethernet frames, which only use two address fields, and wireless frames that could Continue reading
Wireshark 802.11 Display Filters
Wireshark 802.11 frame type and subtype display filters to quickly sort packet captures.
Control Frames
Data Frames
Association Request
Association Response
Reassociation Request
Reassociation Response
Probe Request
Probe Response
Beacon
ATIM
Disassociation
Authentication
Deauthentication
Action Frames
Block ACK Request
Block ACK
Power Save Poll
Request to Send
Clear to Send
ACK
CFP End
CFP End ACK
Data + CF ACK
Data + CF Poll
Data + CF ACK + CF Poll
Null Data
Null Data + CF ACK
Null Data + CF Poll
Null Data + CF ACK + CF Poll
QoS Data
QoS Data + CF ACK
QoS Data + CF Poll
QoS Data + CF ACK + CF Poll
Null QoS Data
Null QoS Data + CF Poll
Null QoS Data + CF ACK + CF Poll
wlan.fc.type==1
wlan.fc.type==2
wlan.fc.type_subtype==0
wlan.fc.type_subtype==1
wlan.fc.type_subtype==2
wlan.fc.type_subtype==3
wlan.fc.type_subtype==4
wlan.fc.type_subtype==5
wlan.fc.type_subtype==8
wlan.fc.type_subtype==9
wlan.fc.type_subtype==10
wlan.fc.type_subtype==11
wlan.fc.type_subtype==12
wlan.fc.type_subtype==13
wlan.fc.type_subtype==24
wlan.fc.type_subtype==25
wlan.fc.type_subtype==26
wlan.fc.type_subtype==27
wlan.fc.type_subtype==28
wlan.fc.type_subtype==29
wlan.fc.type_subtype==30
wlan.fc.type_subtype==31
wlan.fc.type_subtype==33
wlan.fc.type_subtype==34
wlan.fc.type_subtype==35
wlan.fc.type_subtype==36
wlan.fc.type_subtype==37
wlan.fc.type_subtype==38
wlan.fc.type_subtype==39
wlan.fc.type_subtype==40
wlan.fc.type_subtype==41
wlan.fc.type_subtype==42
wlan.fc.type_subtype==43
wlan.fc.type_subtype==44
wlan.fc.type_subtype==46
wlan.fc.type_subtype==47
CWNA CWSP CWAP Study Resources
General Resources
![]() Quick overview of 802 legacy, 802.11a, 802.11b, 802.11g, 802.11n, and the 802.11ac draft standard.
Quick overview of 802 legacy, 802.11a, 802.11b, 802.11g, 802.11n, and the 802.11ac draft standard.
Free Wi-Fi Learning Resources from CWNP
The CWNP Question of the Day (QOTD)
CWNP Study Guide CD-ROM Downloads
Packetlife WLAN cheat sheet
CWNA
Certified Wireless Network Administrator (CWNA) Overview of the Certificfation
CWNA Certified Wireless Network Official Study Guide: Exam PW0-105 (CWNP Official Study Guides)
Here is the link to download the updated PW0-105 CWNA exam objectives
Wi-Fi Back to Basics – 2.4 GHz Channel Planning
Wikipedia page on WLAN Channels
Introduction to Wi-Fi Wireless Antennas
Wi-Fi CERTIFIED™ for WMM®-Power Save
Aerohive’s Medium Contention & Mac Sublayer WiFi 101 video (28:00)
Radio Frequency Measurements (1:13)
Memorize 802.11 MCS values and Data rates for CWNA or CWDP (YouTube Video)
CWSP
CWSP Certified Wireless Security Professional Official Study Guide: Exam PW0-204 (CWSP Official Study Guides)
Here is the link to download the updated PW0-204 CWSP exam objectives
EAP Types (Excel file for my own reference)
Marcus Burton, Director of Product Development at CWNP, Continue reading
Cyber Spring Cleaning! Don’t Forget Your Wireless Router!
 As the weather warms up articles to remind us about cleaning up our devices, online accounts, making backups, and changing passwords are sure to show up, but don’t forget to add your wireless router to this list. Over time the wireless environment may have changed and the number of devices connecting to the network has increased and you have noticed a decrease in the performance. I have listed some items to check to either improve the performance or security of your wireless network.
As the weather warms up articles to remind us about cleaning up our devices, online accounts, making backups, and changing passwords are sure to show up, but don’t forget to add your wireless router to this list. Over time the wireless environment may have changed and the number of devices connecting to the network has increased and you have noticed a decrease in the performance. I have listed some items to check to either improve the performance or security of your wireless network.
Upgrade the Router
Electronics age fast and if you’re still running an 802.11g router it is time to upgrade. Look for an 802.11n protocol wireless router or get the latest and greatest 802.11ac router and be ready for the next wave of wireless devices. Either way you’ll notice a performance boost and the router won’t create a bottleneck in the network.
Check for the Latest Firmware
While not as often as Windows or Apple software updates a routers software called firmware does get the occasional update. Firmware could add functionality, patch bugs, or add security features. When you log into the routers management interface look for the firmware section to verify the current version and download Continue reading
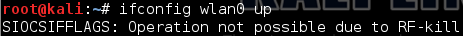
How to Fix the SIOCSIFFLAGS Error in Kali Linux
I recently rebuilt my laptop and reloaded the applications I use for pentesting including Virtualbox and Kali Linux. If you need help setting up Kali Linux in Virtualbox here is a great link that walks through the setup process.
Once I had Kali up and running in my virtual environment I plugged in my ALFA wireless adapter and made sure the USB device was running in the virtual environment.
I ran iwconfig to verify the wireless interface.
So far so good and I ran ifconfig to verify the interface was up, but the only interface returned was the loopback.
After discovering the wireless interface was not up and I ran ifconfig wlan0 up to bring it up and got the SIOCSIFFLAGS error.
I wrote about this error a while back when I was running Backtrack 5 and I first started using the Fern WiFi Cracker. I decided to expand on that post plus I was asked about creating a script to run all the commands at one time instead of typing them individually. The script should be run every time Kali is booted, but after your adapter is plugged in and recognized.
First open a text editor and type in the Continue reading
Changing Your MAC Address Using Macchanger
Macchanger is a free utility used to change the MAC address of the network adapter. Macchanger can randomly assign a MAC address or assign a specific MAC address of your choosing.
Usage
There are several instances changing the MAC address is necessary, but I use the utility while pentesting a wireless network with MAC filtering enabled and have to assign an approved MAC address to the wireless adapter.
Install
The Macchanger utility is included with Kali Linux, but to install the application, update it, or verify your using the most up to date version run the following command. In the screen shot that follows the install command confirms that the newest version is already installed.
#apt-get install macchanger
Help
Help with Macchanger can be accessed by running the following two commands.
#macchanger --help #man macchanger
Assign a Random MAC Address
I’m using an Alfa USB wireless adapter and I will run the following commands to verify the adapters interface and the permanent MAC address.
#ifconfig #ifconfig wlan1
Macchanger can also be used to verify the manufacture burned in MAC address by running the following command.
#macchanger--show wlan1
Change the MAC address using one of the following commands.
#macchanger -r Continue reading
How to install Kali Linux in Virtualbox : Step-By-Step guide.
Great step by step instructions on how to install Kali Linux in VirtualBox. Plenty of screen shots for those visual people and it really helps tell how the configuration and install should work.
Originally posted on kanishkas how to?:
Oracle Virtualbox is an open source virtualization software that can be downloaded from here. It runs on Windows, Linux, Macintosh, and Solaris hosts and supports a large number of guest operating systems . Now we are going to see how to install Kali Linux in Virtualbox. I am using the latest release of Virtualbox for this howto. After downloading and installing virtualbox, open it. Click on New as shown below.
The “Create virtual machine” window opens. Type the name of the virtual machine. select type as Linux and version as Linux 2.6 or Debian. Click on Next.
Then select the RAM for your virtual machine. I put it to 512MB. Make choice according to the memory available in your system. Make sure it is above or same as recommended memory. Click Next.
The size of the hard disk is automatically assigned. We can change it later. I suggest you…
View original 635 more words