Black Friday Blowout: Hot Tech Picks for 2019
‘Tis the season… for the best shopping deals! What’s on tech pros’ must-have technology list for 2019?
How to Avoid Being the Network Turkey
In honor of the Thanksgiving holiday, we’ve put together a few handy tips on how to avoid becoming the network turkey. While many may enjoy it at the family dinner table, nobody wants to be the turkey at work, causing disruptions for their coworkers and organization.
Edge Computing Security Dos and Don’ts
Edge computing offers multiple benefits in an IoT environment, but one thing you don't want to be on the edge about is edge computing security.
Security Concerns Forcing Organizations to Rethink Cloud Strategies
Securing today’s increasingly complex multi-cloud environments requires much more than simply having a security platform available on a particular infrastructure.
6 Tech Trends for the Enterprise in 2019
Look for new technologies to emerge - and for emerging technologies to become the norm - in the new year.
Why We Need Self-Healing SD-WANs
Organizations need to build the necessary intelligence into their SD-WAN to anticipate problems and take corrective action. Only then will SD-WANs continue to work when outages come.
The Security Missing From 5G
For all of the excitement about the coming 5G mobile networks, there are a few words of caution from security experts.
Why SDN and IBN Demand Better Network Visibility
Automation has many positives, but also decreases NetOps’ understanding of the network. To overcome this, NetOps need tools designed to better understand, manage, and troubleshoot their infrastructure and applications.
5 Tips to Harden Network Security in a Connected Enterprise
As security efforts evolve from the fixed edge to the elastic edge, organizations need to combine traditional and new best practices to keep their networks safe from today’s evolving cyber threats.
Vulnerabilities in our Infrastructure: 5 Ways to Mitigate the Risk
By teaming up to address key technical and organizational issues, information and operational security teams can improve the resiliency and safety of their infrastructure systems.
Performance Testing: WinPcap versus Npcap
In this video, Tony Fortunato tests WinPcap versus Npcap. See which performs better.
Workflow UX Design Part 2: Building a Positive User Experience
Iterative feedback between users and developers, as well as good documentation, will help ensure workflow automation is successful.
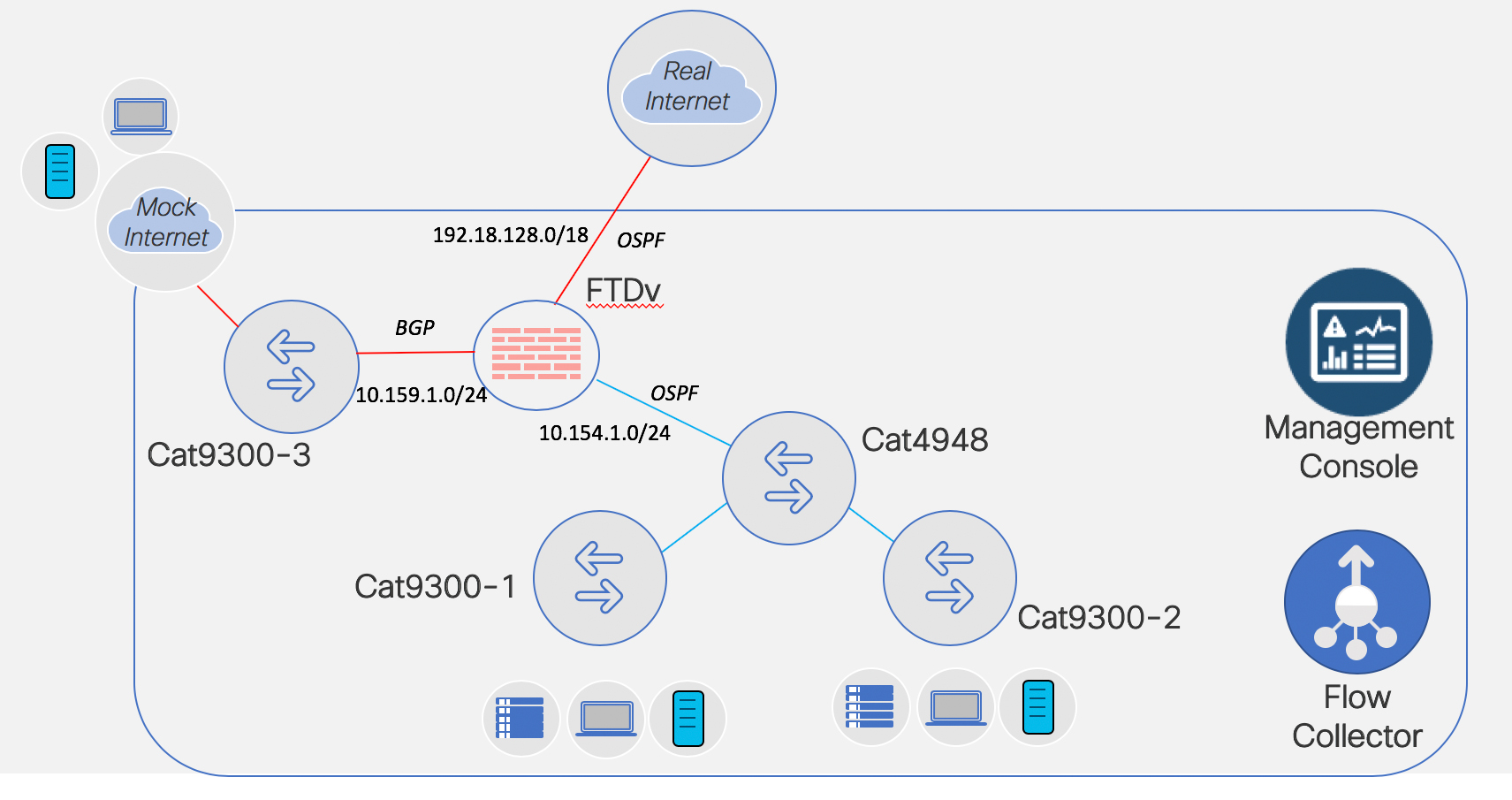
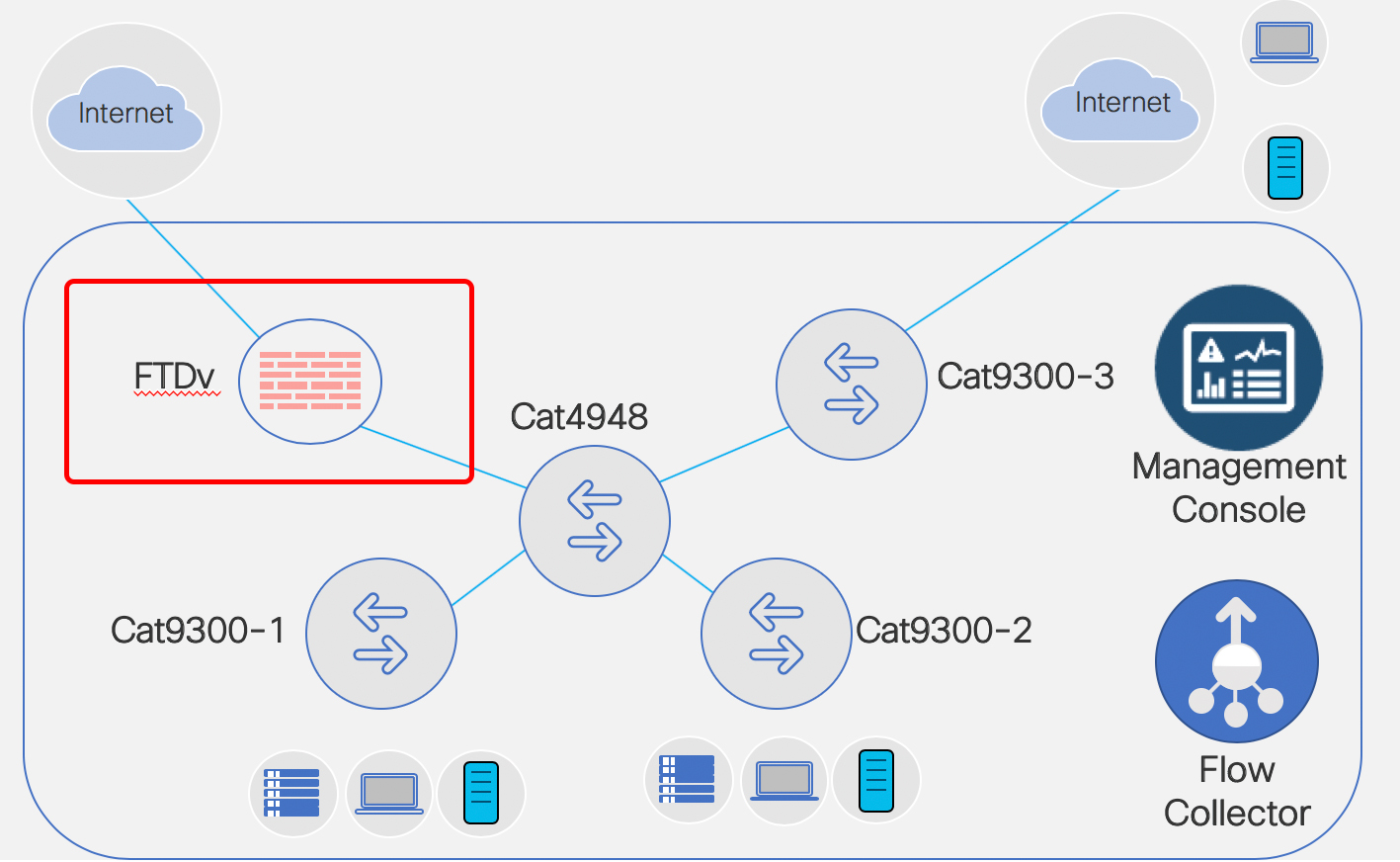
Setting Up Addressing and Routing: FTDv Fun
In my previous blog (Fun in the Lab: FTDv & FMC – Install and Deploy) we deployed a FMC VM and a FTDv VM and ended the blog with the FTDv successfully added to the FMC.
Now? Now let’s add IP addressing for the FTDv and also set up routing protocol neighbor relationships. I learned what I am about to show you from my co-worker and friend, Keith Brister. So don’t thank me, thank Keith. 
I tossed together a ~29 minute YouTube. Obviously you can watch the entire thing. Or… here you go for the big sections.
- Overview – Start to 2:17 minutes
- Physical/Logical Mapping Overview – 2:18 to 9:25
- vSwitches, vmNICs and More in VMware – 9:26 to 16:20
- FTDv Configuring IP Adresses via FMC – 16:21 to 23:18
- FTDv Configuring IP Routing via FMC – 23:19 to 29:29
Done and Done. Easy Peasy!
Infrastructure Vendors Making Strides in 2019
IT infrastructure vendors are embracing software and service-based options, and developing a host of innovative technologies. Our list highlights the ones to watch.
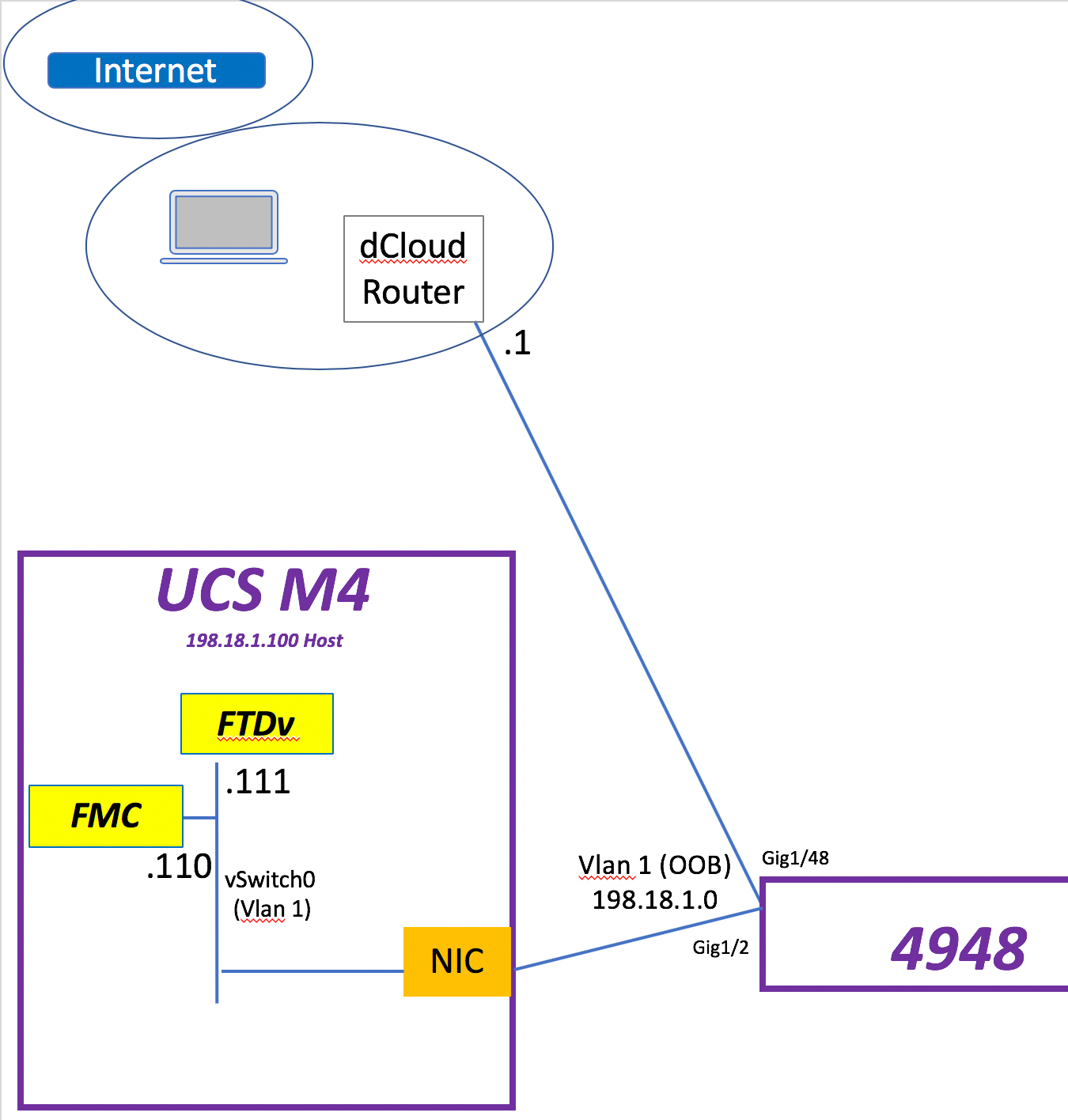
Fun in the Lab: FTDv & FMC – Install and Deploy
This is my Stealthwatch playground…. errrr… I mean … ahem… “work environment” for a Technical Solution Workshop I am working on for Stealthwatch.
Going to set up FTDv and FMC today. A co-worker and friend, Scott Barasch, helped me get jump started… so figure I’ll pass on what I just learned to you. 
What this blog will cover is
- DEPLOY
- Deploying the OVF for FTDv
- Deploying the OVF for FMC
- VMware settings
- Tweak for FTDv
- Tweak for FMC
- Prepping to Power On
- Snapshot Both Before Power On
- Power Both On
- Setup via Console
- FMC – console in and setup IP address
- FTDv – console in and step thru the prompts
- Test IP Connectivity
- Ping FMC and FTDv from the PC
- Notice Can’t ping FTDv
- Fix
- Ping
- Browse into FMC
- Change password
- Setup DNS
- Setup NTP
- Accept EULA
- Apply
- LICENSING
- License FMC
- FMC/FTDv: Make the Connection
- FTDv – Point FTDv to FMC
- FMC – bring the FTDv into the fold.

So let’s begin. What I have to host my FMC & FTDv VMs is a UCS M4 with a NIC connected to a Cat4948 in vlan 1. That NIC is tied to vSwitch0 in the UCS. Continue reading
Wireless Technology Transforms the Retail Experience of the Future
Retailers face serious challenges and opportunities as consumer shopping behavior and expectations evolve. The lessons learned in addressing the challenges have applications in many enterprise settings.
A Tale of Two DCs for Supply Chains: Distribution and Data Centers
Supply chains need IT systems that are highly available, and in an era in which most organizations rely on distributed data centers and cloud services, that’s become a far more complex task.
Getting DevOps Wrong: Top 5 Mistakes Organizations Make
Time spent working on DevOps projects has opened a window into some common mistakes that organizations make when trying to deliver a true DevOps initiative.
Is a Cloud-native Strategy Right for You?
A cloud-native approach offers an agile environment enabling organizations to meet ever-increasing customer demands and expectations. This allows companies to grow a product, service, or idea and deploy all these things as quickly as business plans change.
Halloween Horrors: Real-Life Scary Stories from the Data Center and Beyond
The end of October means it’s time to start carving pumpkins and picking the perfect Halloween costume. This is also a good time to scare yourself silly with horror stories from your data center.