African Peering and Interconnection Forum 2019 Fellows Announced

The 10th African Peering and Interconnection Forum (AfPIF-10) has selected twenty fellows to participate in the meeting next month.
The fellows are drawn from various fields such as interconnection, content, infrastructure, and policy. They represent Kenya, Lesotho, Somalia, Nigeria, Gabon, Burkina Faso, Mozambique, Tanzania, Madagascar, Democratic Republic of Congo (DR Congo), Egypt, Uganda, South Africa, Republic of the Congo (Congo), Ethiopian Cameroon, Benin, and Gambia.
Among the chosen fellows are six women sponsored by the Women in Tech partners. The women are drawn from Kenya, South Africa, Gambia, and Congo.
Representing DR Congo in this year’s AfPIF forum is Eric Nsilu Moanda. Eric works as a Senior Core Data Network Architect for Vodacom DR Congo. He has held the position at the Vodafone Group subsidiary for 12 years now, designing all IP Integration Solutions for the company.
“I look forward to learning how to produce attractive local content in Africa, for Africans, obtaining a fresh technical and marketing perspective, and gaining awareness in the evolution of continental interconnection projects,” Eric said.
In the past, Eric has peered on integrating Vodacom to KINIX (Kinshasa Exchange point) and he also worked on the Internet update link for the CDN of Kinix via Continue reading
Hackathon at Africa Internet Summit 2019: Network Programmability, Network Time, IPv6, IPWAVE, and Measurement

The Internet Society and AFRINIC collaborated to organize the 3rd Hackathon@AIS in Kampala, Uganda, which took place alongside the 2019 Africa Internet Summit. The event attracted more than one hundred participants who took part in five different tracks at the event. The event has grown from three tracks and 39 participants in 2017 and three tracks with 75 participants in 2018, to five tracks with 100 participants this year. Cisco DevNet has been helping organize the event since the first edition, and this year, they sponsored t-shirts for the Hackathon.
Objectives
The goals of the Hackathon@AIS and other open standards promotion activities in the African region are to identify, encourage, and expose engineers from Africa to open Internet Standards development, so that they can contribute to the work at organizations such as the Internet Engineering Task Force (IETF).
Format
The event ran for two days, organized as follows:
- Day 1, June 19th, Morning
- Opening session covering the goals of the meeting and the overall structure
- Registration formalities of participants – using information gathered during the registration process earlier in the year, participants were added into corresponding tracks with each track having its own meeting room and facilitators
- Room and lab Continue reading
The Week in Internet News: Community Broadband Offers Fastest Speeds in U.S.

Super fast: ISPs run by local communities or run through a partnership with a local community offer some of the fastest broadband in the U.S., a story at Vice.com says. Six of the 10 fastest ISPs in the country are either operated by local communities or are partnerships between the public and private sectors, according to a PCMag review.
Conflicting laws: Australia’s recently-passed encryption law, which mandates law enforcement access to encrypted communications, may conflict with the EU’s GDPR and the U.S. CLOUD Act, according to a story at ZDNet. Australian law enforcement agencies may have trouble requiring U.S. and EU companies to decrypt data, the Law Council of Australia has said.
Tweeting is back: The government of Chad has restored access to social media after a 16-month shutdown, QZ.com reports. That’s a lot of missed likes. The government had restricted access to electronic communications for “security reasons” and in “a context of terrorist threats.”
It steals your face: Mobile phone apps that allow you to edit pictures of your face may introduce security vulnerabilities, Forbes notes. One app may upload faces to a database without users’ permission, and another app Continue reading
RightsCon 2019: Human Rights in the Digital Age

Since its creation in 2011, RightsCon has gathered people from different sectors to discuss human rights in the digital age. It started as an event with a few hundred experts, but has become a major conference, with nearly 3000 participants in 2019. The 2019 program consisted of 17 tracks focusing on major issues, which totalized more than 450 sessions held in a period of four days.
As the conference started to attract a wider group of people, it adopted a series of measures to increase its diversity. The recent host countries, including Tunisia and Costa Rica, reflect the worldwide nature of the event, which now gathers individuals from all over the globe.
RightsCon has also gathered a considerable number of young people. They’ve had the opportunity to connect not only through regular conference activities, but during a summit on Day Zero. The summit aimed to engage youth and also brief them on the discussions taking place during the rest of RightsCon.
The sessions at RightsCon were designed with different formats, which was reflected in the physical structure of the meeting rooms. They were organized not just in an audience format, but also roundtables, allowing for people to feel equal footing Continue reading
Accessible, Clear, and Appropriate: An Open Letter to Amazon on Privacy Policies

With great power comes great responsibility.
Online marketplaces, such as Amazon, are becoming increasingly common. But can consumers count on these marketplaces to help safeguard their privacy? On Monday, coinciding with Amazon Prime Day, the Internet Society partnered with Mozilla and other organizations to publish An Open Letter to Amazon about Privacy.
We call for Amazon to require vendors of connected devices to have “a privacy policy that is easily accessible, written in language that is easily understood, and appropriate for the person using the device or service.”
This is one of the five minimum guidelines we called for in a joint statement with Mozilla and Consumers International during the 2018 holiday buying season: “Minimum Standards for Tackling IoT Security.” The other guidelines cover strong passwords, software upgradability, ability to manage reported vulnerabilities, and encryption of data. However, these five guidelines are just baseline recommendations. A full set of principles addressing security, privacy, and lifecycle issues is outlined in our IoT Trust Framework.
We urge everyone involved in the production and sales of connected products to step up and help protect their customers by ensuring that trust by design – making privacy and security the default – Continue reading
The Week in Internet News: Amazon, Microsoft Look to Expand Internet Access

More access, please: Two large tech companies have announced plans to expand Internet access. First, Microsoft and Ohio-based telecom firm Watch Communications have announced an agreement to extend broadband service to underserved areas in Ohio, Indiana, and Illinois, the Associated Press reports, via the Jacksonville Journal Courier. The project is part of Microsoft’s Airband Initiative, an effort to expand service across the U.S.
Look to the sky: Secondly, Amazon has asked the U.S. Federal Communications Commission for permission to launch more than 3,200 satellites, with plans to launch a global broadband network, Smart Cities Dive says. The Amazon plan would target underserved areas across the globe as well as aircraft, ships, and submarines.
That’s a long time without service: More than 350 Internet shutdowns during the last three years have caused the equivalent of 15 years of lost access, The Telegraph reports. About two-third of those shutdowns were in India, and protests or political instability were the reasons for the government actions, according to a report from Access Now.
Warning shot: Two companies, British Airways and Marriott, are facing nine-figure fines (in U.S. dollars) under the European Union’s General Data Protection Regulation for past data breaches Continue reading
The Internet of Things: Connecting the Dots to Become a Smart Consumer

According to a recent survey conducted by Consumers International and the Internet Society, 63% of consumers think the way Internet-connected devices collect data is “creepy.” The Trust Opportunity: Exploring Consumer Attitudes to the Internet of Things, which polled people in the US, Canada, Japan, Australia, France, and the UK, also found that 73% of consumers think people using connected devices should worry about eavesdropping. And yet, new connected devices are being introduced practically every day, and sales show no sign of slowing down.
The word “smart” is used to describe almost all of these devices. But is that right?
The marketing around the Internet of Things (IoT) has become almost non-stop. Smart-this will make your life better, happier, more efficient. If only you had smart-that, you would reap the benefits of the marvelous technological age in which we live. But this often leaves out key information consumers need to make real smart choices.
It’s really about connectivity. For instance, that smart oven is a computer that happens to get hot in the middle. These IoT devices are able to perform smart functions because they are connected to the Internet. And while the marketing focuses on features and functionality, Continue reading
Internet Society’s Online Trust Alliance 2018 Cyber Incidents & Breach Trends Report

On Tuesday July 9, 2019 the Internet Society’s Online Trust Alliance (OTA) released its 11th Cyber Incident & Breach Trends report, which provides an overview of cyber incidents – and offers steps organizations can take to prevent and mitigate the potential damage. This year’s report found a shifting landscape of cyber incidents. As the growth of some attack types levels off, others increase.
Adding it all up, OTA estimates that there were more than 2 million cyber incidents in 2018, and it is likely that even this number significantly underestimates the actual problem. OTA estimates an overall financial impact of at least $45 billion worldwide. The lead categories of attacks are cryptojacking (1.3 million) and ransomware (500,000), followed by breaches (60,000), supply chain (at least 60,000 infected websites), and Business Email Compromise (20,000).
There are many organizations that track data breaches overall. For example, Risk Based Security Reported the highest number at 6,515 breaches and 5 billion exposed records, both down from 2017. These estimates vary depending on their methodologies – see our full report for all of the breach estimates and our methodology.
One well-established attack type, ransomware, saw a decline in 2018. However, the total dollar Continue reading
The Week in Internet News: Balloon-based Internet Service Passes a Big Test

The sky’s the limit: An Internet connectivity balloon, operated by Google sister company Loon, has spent 223 days in the air and circled the globe in an effort to demonstrate the feasibility of balloon mesh networks, CNET reports. The P-496 spent 140 days testing flight algorithms off South America.
Bad for business: A recent law that forces Australian communications firms to give the government access to encrypted messages has hurt business there, the government says. The public perception about the downsides of the law has “had a material impact on the Australian market and the ability for Australian companies to compete globally,” Computerworld Australia reports.
Weak security: D-Link, a maker of routers, IP cameras and other Internet-connected devices, would be required to stand up a new comprehensive security program in a proposed cybersecurity settlement with the U.S. Federal Trade Commission, GovInfoSecurity says. In early 2017, the FTC alleged that D-Link “failed to take reasonable software testing and remediation measures to protect their routers and IP cameras against well-known and easily preventable software security flaws.” The company allegedly left default usernames and passwords on devices and stored login credentials insecurely, and it left a private code-signing key on a Continue reading
Myanmar’s March Towards a Digital Future

Earlier this month, in collaboration with the Asia-Pacific Telecommunity (APT) and the Government of the Republic of the Union of Myanmar, we delivered a training program on Internet Governance for 32 government officials in Myanmar’s capital city, Naypyidaw.
The program ran over three days covering various topics such as Internet policy principles and regulatory frameworks, Internet infrastructure and standards, Internet for development, and cybersecurity.
What impressed me was the participants’ interest in asking questions and their active participation in discussions – it was obvious they were all very eager to learn and explore ways they could apply the learnings in their roles in the various departments they were from. We also got to discuss and see what promise digital technology holds for the country.
I have had the opportunity to visit Myanmar several times, including well before the democratic reforms began. In the few years since those reforms brought Myanmar to the world stage, the country has gone through tremendous transformation. I distinctly remember the difficulties in getting access to the Internet and the lack of mobile phones during my earlier visits.
Today, it’s a very different story. There are multiple service providers, and multiple cable landing stations that provide Continue reading
In Patagonia: A New Community Network in the Village of El Cuy

Patagonia, a region in Argentina made up of deserts, pampas, and grasslands, is known for its large areas of uninhabited territory. In the north sits the village of El Cuy, with just 400 residents. Far from the large urban centers, the people of El Cuy have adapted to the difficulties of accessing different services and technologies. The Internet is no exception, thanks to a new community network.
In several ways, the community network model represents the Internet model of networking come to life. Community networks are built and implemented by people, through collaboration – all stages of the process include the community working together. In the case of the El Cuy community network, support was also provided by the CABASE and the ENACOM.
For Christian O’Flaherty, the Internet Society’s senior development manager for Latin America and the Caribbean, Internet access has become a positive catalyst for community development. “The operation of this pilot program has motivated the residents to organize themselves into a cooperative. This step will allow inhabitants from El Cuy to have access to various fundings offered by actors such as ENACOM to increase the capacity of the Internet connection.”
Abel Martínez, a resident of El Cuy Continue reading
Becoming Broadband Ready Means Community Innovation and Collaboration

There are countless communities across North America that are hungry to see better broadband access for their residents. It’s clear to local leaders that high-quality Internet access is the bedrock of a healthy and successful community – providing job opportunities, bolstering education, transforming health care, and democratizing access to information. What isn’t always so clear is how to make it happen.
That’s why Next Century Cities teamed up with the Internet Society and Neighborly to create the Becoming Broadband Ready toolkit. This comprehensive toolkit provides local leaders with a roadmap to encourage broadband investment in their community.
While every community will choose to tackle connectivity a little differently – a small island community and a large urban center will likely have unique considerations and approaches – there are many common threads that run through successful broadband projects. Becoming Broadband Ready compiles these threads into an easy-to-use and impactful resource for any community, providing resources specific to:
- Establish Leadership
- Build a Community Movement
- Identify Goals
- Evaluate the Current Circumstance
- Establish Policies and Procedures to Support Investment
- Prioritize Digital Inclusion
- Identify Legislative and Regulatory Barriers
- Explore Connectivity Options
- Explore Financing Options
- Be a Clear Collaborator
- Measure Success
Next Century Cities identified the Continue reading
Internet Society Asia-Pacific Policy Survey 2019 Now Open: Consolidation in the Internet Economy

The Internet Society recently embarked on a year-long effort to explore the trends of consolidation in the Internet economy, and I write to sincerely invite you to share your views with us in the Regional Policy Survey 2019, an annual exercise of the Asia-Pacific Bureau of the Internet Society.
Your input is very important to us. It will help us understand the issue from your perspectives and produce a report to be released later this year. Ultimately, your input will help us come up with technical and policy recommendations for policymakers with the aim of preserving the Internet’s properties that give us the critical abilities to connect, speak, innovate, share, choose, and trust.
Please take 5-10 minutes to complete the survey, which covers all Internet users in Asia-Pacific. To show our appreciation, we will be offering 2 tablet computers in a lucky draw, and the winners will be notified by email after the survey closes on July 31.
Read about the previous installments of the survey.
Thank you again for your time and input.
The post Internet Society Asia-Pacific Policy Survey 2019 Now Open: Consolidation in the Internet Economy appeared first on Internet Society.
Transparency, Fairness, and Respect: The Policy Brief on Responsible Data Handling

It’s been a little over a year since the European Union’s General Data Protection Regulation (GDPR) was implemented, but almost immediately, people noticed its impact. First, there was the flurry of emails seeking users’ consent to the collection and use of their data. Since then, there’s also been an increase in the number of sites that invite the user to consent to tracking by clicking “Yes to everything,” or to reject them by going through a laborious process of clicking “No” for each individual category. (Though some non-EU sites simply broadcast “if we think you’re visiting from the EU, we can’t let you access our content.”) There was also the headline-grabbing €50 million fine imposed on Google by the French supervisory authority.
In its summary of the year, the EU Data Protection Board (EDPB) reported an increase in the number of complaints received under GDPR, compared to the previous year, and a “perceived rise in awareness about data protection rights among individuals.” Users are more informed and want more control over the collection and use of their personal data.
They’re probably irritated by the current crop of consent panels, and either ignore, bypass, or click through them Continue reading
The Week in Internet News: Small Routing Error Has Big Consequences

Bad route: A small routing error led to Internet outages in the Northeastern United States on June 24, Inc.com reports. Small network services provider DQE Communications shared inaccurate routing information with Verizon, which then passed it along to the wider network. Internet services were flaky for about two hours, with Verizon Fios phone and Internet services in Virginia, Massachusetts, New York, New Jersey, Pennsylvania, and other states affected, the Washington Post said. Server issues also affected Reddit, Twitch, and video gaming service Discord.
Attacking encryption? U.S. President Donald Trump’s National Security Council recently discussed ways to prohibit companies from offering customers unbreakable encryption, Politico reports. Officials debated whether to ask Congress to effectively outlaw end-to-end encryption, according to anonymous sources.
Embrace the dark side: Government entities looking to improve Internet speeds in their areas should consider dark fiber when it’s available, advises AmericanCityandCounty.com. Switching to dark fiber can offer both performance improvement and cost savings, but the transition can demand a major overhaul.
Service restored, for one guy: Sudan’s three-week Internet shutdown keeps going, except for one lawyer, who won a lawsuit against telecom operator Zain Sudan over the blackout ordered by the country’s military rulers, the Continue reading
Announcing an Executive Director for the Internet Society Foundation

Last year we established the Internet Society Foundation, with a plan to make clearer the Internet Society’s grant-making activities, and distinguish them from Internet Society programmes. We announced that we would develop the Foundation over the course of the following year.
Since then, we have introduced the Internet Society Foundation’s new website and opened up the process for applications from ISOC Chapters and Special Interest Groups (SIGs) for the Beyond the Net Grants Programme, which is now housed within the Foundation. This now includes the full range of Beyond the Net Small, Medium, and Large Grants.
In parallel with moving the Beyond the Net Programme, we have been searching for a leader for the Foundation. I am pleased to announce our selection.
Sarah Armstrong starts in her new role as the Foundation’s Executive Director today, July 1. She brings a wealth of experience to us, having built a career in non-profit, humanitarian, and international development work over many years.
Please join me in extending a warm Internet Society welcome to Sarah. I am sure she will play a key role in ensuring that our financial support for others’ activities is focused and effective. I look forward to a Continue reading
Community Dispatch: New Hawaii Chapter Says the Internet Still a Force for Good

My first exposure to the Internet Society was back in 1995 when they held the 5th Annual INET International Networking Conference in Honolulu, Hawaii. It was a time when accessing the Internet was a new experience, at least for the public. Terms like hyperlinks, HTTP, FTP, Pine, and the World Wide Web were exciting and the innocence of connecting the world was full of potential.
Fast forward 25 years and the Internet is truly a worldwide resource. With the advent of smartphones, high-speed Internet, wireless technologies, and robust web protocols, accessing and communicating has become a rich experience. But within a quarter of a century, the innocence of the Internet has also tarnished. Not a day goes by without a story in the media about security breaches, privacy lost, horrible things broadcast over social media, online bullying, surveillance, hate speech, and the list goes on.
It is in this environment that we’re launching the Internet Society Hawaii Chapter. The mission of the Internet Society still rings true today: to bring the Internet of opportunity to everyone everywhere, an Internet that is open, globally connected, secure, and trustworthy. These principles apply whether you live in an urban center or rural community. Continue reading
Asia-Pacific Chapters Advocacy Meeting: Local Actions, Global Goals

Earlier this month, 19 representatives from 14 local Chapters in Asia-Pacific gathered in Kuala Lumpur, Malaysia, for a two-day workshop to boost their capability in implementing the Internet Society 2019 Action Plan collaboratively and in a coordinated manner, and to maximize impact across the vast and fast-developing region.
Chapter leaders from Hong Kong, India, Japan, Malaysia, Pakistan, the Philippines, Taiwan, and the Pacific Islands, among other places, spent a weekend together. They learned from each other and planned the collective implementation of the Action Plan that has four focus areas: connecting the world, improving technical security, building trust, and shaping the future of the Internet.
Run by members across the world who support the Internet Society’s mission, Chapters are central to our work. They give us unique local perspectives on emerging Internet issues. The Regional Chapters Workshop, which is held yearly, is an important event that lets us strategize with Chapters on a wave of impactful local actions to amplify our regional voice and promote the organization’s mission – the Internet is for Everyone.
To help the Chapters carry out their work, the workshop focused on training and leadership in the focus areas, including IoT security, routing Continue reading
Announcing news.internetsociety.org – a way to follow what is published across all Internet Society sites
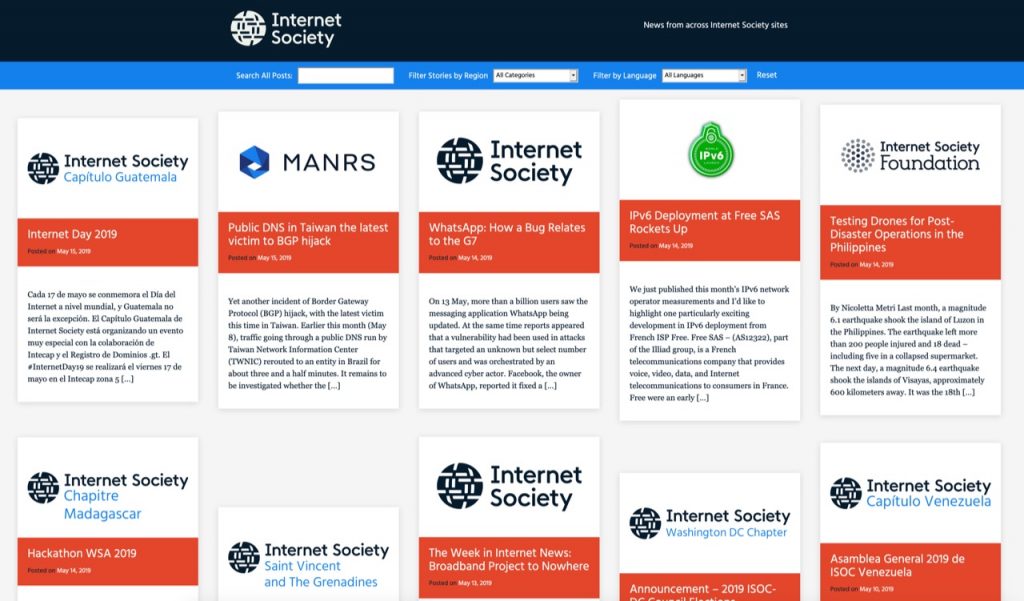
Today I’m pleased to announce a new site we have built that brings into one location links to all the content published across Internet Society websites:
This news site aggregates posts from our main website, from sites of our 130+ Chapters and Special Interest Groups (SIGs), and from certain other affiliated sites. On the site, you can:
- Search using keywords
- Filter the view based on the region
- Filter the view based on language
- Filter the view to see posts only from a specific source
For instance, you can see all the posts published by Chapters in Africa. Or you can see all the posts published in French, or Spanish, or Chinese… or Georgian.
Note that the filters can work together. By choosing “Africa” and “French” you will see only French posts from African Chapters. There’s a “Reset” link on the right side that will clear all the filters.
All the views also have unique URLs that you can share with people, or link to from other sites, email newsletters, etc. And of course the site has a master RSS feed that you can read in a RSS reader or other tool.
I find it quite Continue reading
The Internet Is Your Oyster: MANRS at International Telecoms Week

What do oysters, clams, and mussels have in common with network operators? Hint: it’s not just that they are both in Atlanta this week, either in exhibits in the Georgia Aquarium or for the 2019 International Telecoms Week.
It’s that both bivalves and network operators play an incredibly important role for their ecosystems: they filter the bad stuff out and leave things a lot cleaner.
As water quality is vital to life in the ocean, the global routing system is vital to the smooth functioning of the Internet. The routing system’s decentralized structure, made up of thousands of independent networks tied together through business decisions and trusted relationships, provides flexibility, scalability, and overall durability.
However, despite its strengths, thousands of routing incidents occur every year. Some of these can be pretty scary, with route hijacks sending government traffic through the networks of foreign adversaries; route leaks slowing parts of the global Internet to a crawl; or hackers using spoofed traffic to take down websites in distributed denial of service (DDoS) attacks.
Network operators can help mitigate these problems by using stronger filtering policies to block spoofed traffic coming from their networks (helping guard against DDoS attacks) and filter route announcements Continue reading