The Week in Internet News: U.S. Census Seeks Help with Fake News from Tech Giants

Fake news fears: The U.S. Census Bureau is seeking help from Google, Facebook, and Twitter to fight off fake news during its 2020 population count, Reuters reports. Some groups appear to be targeting the census as a way to redirect congressional representation and federal funding.
Broadband for all: The Vermont House has voted for a bill to add funding for broadband deployment, including community broadband projects, Vermont Public Radio reports. About 17,000 Vermont residents don’t have broadband available, and many others have slow Internet service.
Copyright rules divide: New copyright rules in the European Union may lead to a different Internet experience there, The Verge says. With the EU’s Copyright Directive, there’s now a European Internet that feels different that the U.S. Internet and the authoritarian Internet in some countries, the story says. Among other things, the new rules allow publishers to charge platforms like Google News for displaying snippets of stories.
Encryption rising: The use of encryption by large companies has hit an all-time high, Dark Reading notes. About 45 percent of enterprises have encryption plans in place.
Fake news fighters: Facebook has launched a fake-news fighting effort in India as the country heads toward elections, Time. Continue reading
IoT Security, Privacy Vital from the Outset

For any new technology to be trusted, it must be secure. That is why privacy and security are essential to the development of new technologies from the outset. They must not be an afterthought.
This is especially so for the Internet of Things (IoT) and the plethora of devices that are now available. These devices are gradually being integrated into daily life as we enjoy the benefits they bring. In a number of cases, we are also increasing our dependence on them, such as fitness monitors and home automation.
But poorly-secured IoT devices and services can serve as entry points for cyber attacks, compromising sensitive data and potentially threatening the safety of individual users, as well others.
Attacks on infrastructure and other users, fueled by networks of poorly-secured IoT devices, can affect the delivery of essential services such as healthcare and basic utilities, put the security and privacy of others at risk, and threaten the resilience of the Internet globally.
As concerns mount about the need for regulating the ecosystem and policymakers around the world consider ways to secure it throughout its product lifecycles, it is important to consider the risks this fast-growing technology poses, as well as what steps Continue reading
Working Together the Internet Way to Build Success in North America

One of the most common lines you’ll hear in the virtual halls of the Internet Society is that the Internet’s success is due to its open, distributed, and global nature.
Think about it. A network of voluntarily-connected networks changed the course of history in a matter of decades because people agreed to work and innovate together. It’s a deeply profound source of inspiration about the power of humankind.
It practically begs the question: can we replicate even a portion of its success by embodying the “the Internet way” of working in North America?
The answer is yes.
As part of this, one thing is strikingly clear. Chapters and partners are the lifeblood of the organization. They are critical to working more closely with communities at the front lines of our work.
The Internet’s own globally-operable infrastructure proves the infinite potential of what can happen when people work together. In the same way, we will come together as a diverse community to help define future priorities.
We’ve already seen successes in the North American region that show how closer collaboration with Chapters and partners can help us reach new levels of success.
Enhancing IoT Security
Canada is changing how countries around Continue reading
What Is the Internet Model of Networking?

Fundamentally, the Internet model is that independent networks connect to one another and, all together, provide the global Internet.
The independent networks may be enterprises with business services and employees connected to them, they may be cloud service providers or residential Internet service providers. They are independent in the way that they choose their business models, build and manage their networks, and compete with their neighbors; they offer, however, global connectivity by adhering (voluntarily) to a set of open Internet standards that enable interoperability. To connect on the Internet is inherently to do so voluntarily via open protocols. A different architecture might use different choices, but these are the ones the Internet uses.
All these independent networks interoperate and form an Internet by participating in a global routing system, subject only to technical standards and agreements with neighbors (the technical terms here are peering and transit). The magic of the Internet is that in order to communicate between a mobile phone connected to a broadband provider in the Netherlands and a server in a data center in Kenya, the two networks at either end of the connection do not need a relationship with each other. The magic of the Continue reading
Nominations Open! Jonathan B. Postel Service Award 2019
We are pleased to announce that nominations for the 2019 Jonathan B. Postel Service Award are now open. Do you know someone who should be a recipient?
This annual award is presented to an individual or organization that has made outstanding contributions in service to the data communications community and places particular emphasis on those who have supported and enabled others.
Nominations are encouraged for individuals or teams of individuals from across the data communications industry around the world who are dedicated to the efforts of advancing the Internet for the benefit of everybody.
Past Postel award winners include Steven G. Huter for “his leadership and personal contributions at the Network Startup Resource Center that enabled countless others to develop the Internet in more than 120 countries,” kc claffy for her pioneering work on Internet measurement, Mahabir Pun for his key role in bringing the Internet to rural Nepal with the founding of the Nepal Wireless Networking Project, and Bob Braden and Joyce K. Reynolds for their stewardship of the RFC (Request for Comments) series.
The signature crystal globe and a USD 20,000 prize will be presented at the IETF 105 in Montreal, Canada (20-26 July 2019) to the chosen Continue reading
The Week in Internet News: Russia Moves Toward Test of Internet Disconnect

A separate Internet: The MIT Technology Review looks at the implications of Russia’s test to cut itself off from the rest of the Internet, scheduled for early April. The shutdown is a test of an Internet sovereignty law being considered in Russia, but it’s unclear how the country will actually accomplish the disconnect.
Clamping down: Egypt is cracking down on fake news with new rules that critics say are meant to curb dissent and restrict information the government believe is a threat to national security, The Hill reports. The country’s Supreme Media Regulatory Council can now block websites and some social media accounts with more than 5,000 followers for what it believes is “fake news” and can fine operators up to US$14,400 without getting a court order. Meanwhile, Russian President Vladimir Putin has signed two bills that critics say amount to censorship, Ars Technica says. One bill allows stiff fines for disseminating what the government determines is fake news, and the second allows fines and jail time for insulting government officials, including Putin.
Encrypting the IoT: The U.S. National Institute of Standards and Technology is looking at encryption methods to protect the Internet of Things and other computing devices against future encryption-cracking technologies, Continue reading
Internet Resilience Discussions at IETF 104

Let’s look at what’s happening in the Internet Engineering Task Force (IETF) and the upcoming IETF 104 meeting in the area of Internet infrastructure resilience. As usual, my focus here is primarily on the routing and forwarding planes, and specifically routing security and unwanted traffic of Distributed Denial of Service Attacks (DDoS) attacks. There’s interesting and important work underway at the IETF that can help addressing problems in both areas.
This time there are a lot of new ideas, especially of an operational nature, that people bring to the IETF in the form of Internet Drafts that aim to improve the security and resilience of the Internet infrastructure. So I’d like to introduce some of them to you, but keep in mind that an Internet Draft (I-D) does not necessarily indicate IETF endorsement. It also does not constitute a standard and may even not result in any work at the IETF.
So let’s look at what’s happening in BGP land.
Can BGP Communities be harmful?
In the recent paper “BGP Communities: Even more Worms in the Routing Can“, the authors demonstrated that Border Gateway Protocol (BGP) communities can be exploited by remote parties to influence routing in Continue reading
Coming Togther for an All-Inclusive and Accessible Internet in South Asia

Last year, at the Internet Society Asia-Pacific and Middle-East Chapters Meeting, I was introduced to the series of easily-digestible and thought-provoking issue papers published by the Internet Society. Particularly, the one on digital accessibility had me shaking in disbelief. It stated that one in six people in the Asia-Pacific region lives with disability – that is a total of about 650 million people.

The Internet Society Pakistan Islamabad Chapter had always been active in promoting digital accessibility, but I realized that we need to do more, especially at the transnational level. Thus, the idea of organizing a regional forum on digital accessibility was born, and with support from the Internet Society Asia-Pacific Bureau, it became a reality.
The Regional Forum on Digital Accessibility was successfully held on 7 February in Islamabad. It brought together 120 participants, including Internet Society Chapter leaders from Afghanistan and Nepal, fellows from Sri Lanka, and speakers from India.
A major achievement emerging from the forum was the vow from Pakistan’s high-level government officials to include representation of persons with disabilities in the recently-established Prime Minister’s Task Force on Information Technology (IT) and Telecom that is developing a roadmap for Pakistan’s digital transformation. There was Continue reading
Célébration du 1er anniversaire du chapitre Guinéen de l’Internet Society

Le Chapitre Guinéen de l’Internet Society (ISOC Guinée) a célébré son 1er anniversaire le 9 février 2019 dans la salle de conférence de l’université de Simbaya (UniSim) sous le thème «A la découverte de l’Internet, Histoire et perspectives de l’Internet et de son écosystème en Guinée». Cet important événement a réuni 150 personnes pour marquer la présence de l’Internet Society en Guinée à travers le chapitre et mutualiser les efforts pour la promotion et le développement d’un Internet ouvert, globalement connecté, sécurisé et digne de confiance pour tous en Guinée. L’opportunité a aussi été donnée aux participants et membres du chapitre ISOC Guinée de découvrir le plan d’action 2019 de l’Internet Society et voir comment cela peut se décliner en projets et activités concrètes au niveau local.
La célébration de ce 1er anniversaire du chapitre ISOC Guinée a été soutenue financièrement par le programme de financement Beyond the Net de l’Internet Society et autres partenaires locaux du chapitre dont l’université de Simbaya (UniSim).
Au cours de cette célébration, il a décidé de rendre la date du 30 décembre de chaque année comme une date historique pour le chapitre afin de renforcer les relations d’amitié et de fraternité entre Continue reading
Join a Local IETF Viewing Hub in Africa

The Internet Engineering Task Force (IETF) is the premier Internet standards body, developing open standards through processes to make the Internet work better. It gathers a large, international community of network designers, operators, vendors, and researchers concerned with the evolution of the Internet architecture and the smooth operation of the Internet. Core Internet technologies such as DNS, routing and traffic encryption use protocols standardized at IETF.
The IETF holds three meetings yearly which are livestreamed and can be followed individually, or with others sharing similar interest at a common venue. The next IETF meeting will be held from 25-29 March 2019 in Prague. The usual audience for an IETF meeting is network engineers, system engineers, developers, and university students or lecturers in information technology fields.
The Internet Society Africa Regional Bureau is running an initiative to encourage remote participation in IETF meetings that aims to promote the work of the IETF. IETF Remote Hubs aim to raise awareness about the IETF and allow those who cannot travel to a meeting to participate in the meeting remotely. The meetings are streamed in English only.
Join one of the following IETF Remote Hubs in your area, raise your awareness about the IETF and engage in the various topics of Continue reading
Concluding the IETF Rough Guide, Long Live the IETF Blog

For many years we have produced a series of blog posts as a Rough Guide to each upcoming IETF meeting usually in the week prior to the meeting. The Rough Guides were intended to provide a snapshot of IETF activity of interest to the Internet Society because of programmatic activity that we were engaged in. They were also an opportunity to highlight the activities sponsored directly by the Internet Society that were happening adjacent to the upcoming IETF meeting.
Rough Guides were intended to help guide a non-specialist but technically minded audience to the hot topics and debates of interest at each upcoming IETF meeting with pointers to the agenda and remote participation possibilties. Originally intended to help spur meeting attendance by those interested in the key topics, they became a way to highlight important discussions taking place and ways to get involved in person or remotely.
As we are now less than a week away from the IETF 104 meeting in Prague it seemed like the right time to share an update regarding our plans for writing about IETF activity. We have decided to discontinue producing the Rough Guides. Instead, we will be helping to supply relevant, high-quality content Continue reading
The Week in Internet News: Four Visions of the Internet

Competing visions: The World Economic Forum’s blog looks at four competing visions of the Internet that it sees emerging. These include Silicon Valley’s open Internet, Beijing’s paternal Internet, Brussels’ bourgeois Internet, and Washington’s commercial Internet. Will one vision win out?
Searching for fakes: WhatsApp, the popular messaging app owned by Facebook, is testing reverse image search in its efforts to battle fake news, TheNextWeb reports. The chat app may use Google APIs to compare the targeted image with similar pictures as a way to filter out doctored images.
Working against itself: An Artificial Intelligence that can right fake news articles may also be useful for spotting them, the MIT Technology Review says. Recently, OpenAI withheld the release of its new language model on fears that it could be used to spread misinformation, but researchers say the tool may be useful for the opposite effect.
Privacy laundering: Lawfareblog.com take a hard look at Facebook’s recent announcement that it was moving to end-to-end encryption. The social media giant won’t fix its privacy problems with the move, however, the article says. “Facebook’s business model is the quintessential example of ‘surveillance capitalism,’ with user data serving as the main product that Facebook sells to Continue reading
Seeking Canadian Feedback: Draft Report on Securing the Internet of Things in Canada

Trying to remove cyber security risks from the growing world of connected things is not an easy task. That said, there’s no time like World Consumer Rights Day to give Canada a shout out for its global leadership to champion a safer digital future for all.
Recognizing the need to secure the Internet of Things (IoT), the Internet Society, in partnership with the Ministry of Innovation Science and Economic Development (ISED), the Canadian Internet Registration Authority (CIRA), Canadian Internet Policy and Public Interest Clinic (CIPPIC), and CANARIE, led a voluntary multistakeholder process to develop a broad-reaching policy to ingrain security at the core of innovation in Canada.
Over the past year, we led a series of meetings with business leaders, technical experts, government representatives, civil society, and academia to discuss challenges and recommend the best ways to address them. We gathered feedback through in-person and online attendance. Collectively, these efforts, combined with well-rounded research and documentation, formed the Canadian Multistakeholder Process for Enhancing IoT Security.
Rather than a top-down, government-imposed regulatory model, our multistakeholder approach helped us balance roles and contributions among the group. By working in a way that includes feedback from all participants, we are developing IoT security Continue reading
DNS Privacy Frequently Asked Questions (FAQ)
We previously posted about how the DNS does not inherently employ any mechanisms to provide confidentiality for DNS transactions, and mentioned some of the protocols that have been recently developed to improve user privacy.
To complement this, we are publishing our DNS Privacy Frequently Asked Questions (FAQ). This highlights and provides answers to the most important aspects of DNS privacy.
Please also check our DNS Privacy page for more information!
Further Information
- Introduction to DNS Privacy
- DNS Privacy
- DNS Privacy Frequently Asked Questions (FAQ)
- DNS Privacy Project
The post DNS Privacy Frequently Asked Questions (FAQ) appeared first on Internet Society.
Fact or Fiction? With IoT It’s Not Always Clear

Recently, owners of expensive smart shoes found themselves at loose ends. Unable to pair the shoes to their smart phone app, they couldn’t tighten their self-lacing sneakers. It sounds like science fiction, but this really happened.
From dental sensors that can monitor what a person eats to kitty litters that can track a cat’s every movement, it can be difficult to sort fact from fiction when it comes to the Internet of Things (IoT). Can you tell which is real and which is not?

Fact or Fiction? The voice came from inside the Arizona man’s home – his home security camera to be exact. “You’ve never met me. I’m just a hacker.” Fortunately, it was a friendly hacker, alerting the household to a vulnerability in their home security system.
Fact: The hacker had a solution: turn on two-factor authentication. When using IoT devices, consumers can take this simple step, plus a few others, to help protect their privacy and security.

Fact or Fiction? A couple returned home to find that their carpet had been worn through by their overzealous Internet-connected vacuum cleaner. A hacker had programmed it to clean one square foot of their carpet for several Continue reading
Introduction to DNS Privacy

Almost every time we use an Internet application, it starts with a DNS (Domain Name System) transaction to map a human-friendly domain name to a set of IP addresses that can be used to deliver packets over the Internet. DNS transactions can therefore be correlated to the applications we use, the websites we visit, and sometimes even the people we communicate with.
While the domain name information itself is public, the transactions performed by the hosts are not. Unfortunately, the DNS does not inherently employ any mechanisms to provide confidentiality for these transactions, and the corresponding information can therefore easily be logged by the operators of DNS resolvers and name servers, as well as be eavesdropped by others.
So we are publishing our Introduction to DNS Privacy to raise awareness of the privacy implications of the DNS, and the mechanisms that have been recently developed to improve user privacy.
Please also check our DNS Privacy page for more information!
Further Information
The post Introduction to DNS Privacy appeared first on Internet Society.
IXDO Project: An Internet Exchange Point in the Dominican Republic

For more than a decade, different organizations from civil society and the private sector have been involved in efforts to establish an Internet Exchange Point (IXP) in the Dominican Republic, with no success. Possible causes were either lack of interest at the time, the maturity level of the ICT sector, or even lack of financial support. The Internet Society Dominican Republic Chapter decided to discuss those outcomes with different stakeholders and promote an atmosphere to proceed when the moment was right.
Among efforts from the past, it is important to mention two of them, which made important advances: (1) the datacenter firm NAP del Caribe (NDC), invited interested local Internet Service Providers (ISP) to establish either an IXP or private peering; (2) the academic sector worked to establish a local research network, Red de Avanzada Dominicana de Estudio e Investigación (RADEI), which sought the support of the local regulator Instituto Dominicano de las Telecomunicaciones (INDOTEL).
In 2017, the Internet Society Chapter Dominican Republic (ISOC-DO) board, after considering past efforts and brainstorming on different approaches to succeed in the IXDO initiative, taking inspiration on the regional trends, and locating experts to support our goal, decided to design the annual Continue reading
IPv6 Security for IPv4 Engineers

It is often argued that IPv4 practices should be forgotten when deploying IPv6, as after all IPv6 is a different protocol! But we think years of IPv4 operational experience should be leveraged as much as possible.
So we are publishing IPv6 Security for IPv4 Engineers as a roadmap to IPv6 security that is specifically aimed at IPv4 engineers and operators.
Rather than describing IPv6 in an isolated manner, it aims to re-use as much of the existing IPv4 knowledge and experience as possible, by highlighting the security issues that affect both protocols in the same manner, and those that are new or different for the IPv6 protocol suite. Additionally, it discusses the security implications arising from the co-existence of the IPv6 and IPv4 protocols.
Be sure also to check our IPv6 Security page as well!
Further Information
The post IPv6 Security for IPv4 Engineers appeared first on Internet Society.
Making the Internet Better Together at APRICOT 2019

Asia Pacific Regional Internet Conference on Operational Technologies (APRICOT) 2019, said to be the largest technical conference in the region, drew hundreds of the world’s leading Internet engineers from over 50 countries to Daejeon, South Korea last week.
The Internet Society, a long-time partner of the event, contributed to the event by not only sponsoring over a dozen of fellows to travel there, but also made multiple high-profile appearances in various sessions, including the opening keynote speech.
The Internet Society’s President and CEO Andrew Sullivan delivered the keynote Up and Down the Stack Through a Nerd’s Eyes: Making the Internet Better the Internet Way with hundreds of people present, including Tae-Jeong Her, Mayor of Daejeon, and Dr Hee-yoon Choi, President of organiser the Korea Institute of Science and Technology Information (KISTI), a government research institute.
Now that so many people depend on the Internet, it is no surprise that businesspeople, policymakers, regulators, and politicians all want a say in the way the Internet evolves. But some of the proposals for the future of the Internet, Sullivan said, betray fundamental misunderstandings of the way the Internet works. The talk urged us all to continue to engage with the big questions Continue reading
Celebrating the 30th Anniversary of the World Wide Web
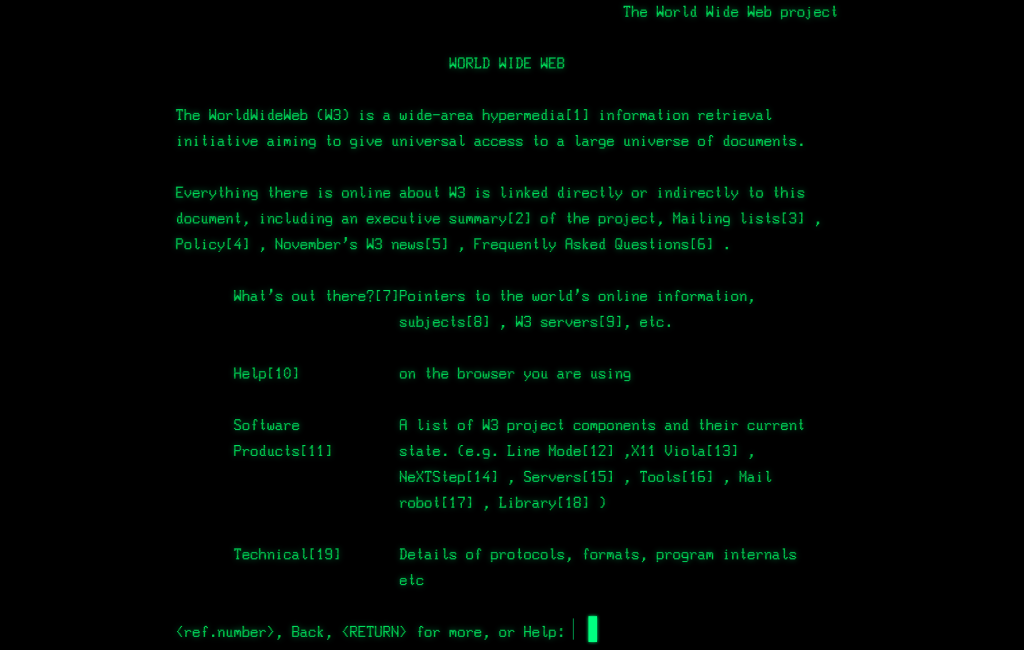
Back around 1991, I was traveling throughout the eastern USA teaching an “Introduction to the Internet” course I had written. The students were mainly from telecom, financial, and software companies wanting to know what this Internet thing was all about. I taught about IP addresses and DNS, using email, sending files with FTP, using archie and veronica to find info, engaging in USENET discussions, and using Gopher to explore “gopherspace”.
At the end of the course, one of the final sections was on “emerging technologies”. And there, nestled in with HyTelnet and WAIS, was one single page about this new service called the “World-Wide Web”.
And all the page really said was: telnet to info.cern.ch, login as “www”, and start pressing numbers to follow links on the screen.
That was it! (and you can still experience that site today)
We had no idea in those very early days that what we were witnessing was the birth of a service that would come to create so much of the communication across the Internet.
In only a few short years, of course, I was teaching new courses on “Weaving the Web: Creating HTML Documents” and Continue reading