Meeting Four of the Canadian Multistakeholder Process: Enhancing IoT Security
The Canadian Multistakeholder Process: Enhancing IoT Security meeting takes place in Ottawa today, November 20th, from 1PM-5PM EST.
This is the fourth session in a year-long series. The meetings have been convened to develop recommendations for a set of norms/policy to secure the Internet of Things in Canada and are a joint initiative of The Internet Society; Innovation, Science and Economic Development; the Canadian Internet Registration Authority; CANARIE; and CIPPIC.
Today’s session will build on the progress of the working groups, which were established during the second meeting: Consumer Education & Awareness, Labeling, and Network Resiliency. (Read the third multistakeholder meeting report.)
Register for the event or watch the livestream!
The post Meeting Four of the Canadian Multistakeholder Process: Enhancing IoT Security appeared first on Internet Society.
The Week in Internet News: The Bottom Line of IoT Security

The cost of IoT breaches: Companies struggling with Internet of things security are seeing a monetary impact, says WeLiveSecurity.com. About a quarter of companies struggling with IoT security have reported losses of at least US $34 million in the last two years, according to a recent survey.
International cyber deal: French President Emmanuel Macron called on other nations to join his country in an international pact against malicious activity online, reports ITworldCanada.com. Nations signing the Paris Call for Trust and Security in Cyberspace would agree to “condemn malicious cyber activities in peacetime, notably the ones threatening or resulting in significant, indiscriminate or systemic harm to individuals and critical infrastructure and welcome calls for their improved protection.” The pact, advanced at the Internet Governance Forum in Paris, was signed by 51 other countries, 224 companies, and 92 non-profits and advocacy groups. But the U.S., Russia, and China declined, ZDNet notes.
Booted from social media: In a three-week period, Chinese censors have deleted nearly 10,000 social media accounts operated by the country’s residents, reports the South China Morning Post via Yahoo News. Accounts shut down include those of a talk show celebrity and an entertainment blogger. The Continue reading
El Buen Fin: Tips to Shop Smart

Last week I had the opportunity to participate in the first edition of the International Internet and Entrepreneurship Forum (FIIE), in Monterrey, Mexico. The event was convened by NIC Mexico and other organizations of the Internet community of Latin America and the Caribbean as part of the activities of INCmty, an entrepreneurial festival with several years of tradition. The intersection between both topics is a fertile ground for reflection, especially in relation to the security of Internet of Things (IoT) devices.
IoT for Innovation and Entrepreneurship
The Internet has been known as a technology for facilitating innovation and entrepreneurship. The pace of technological development, together with the evolution of the Internet, has given rise to new solutions that seek to make life easier. Such is the case of the various devices connected to the Internet, which form the Internet of Things ecosystem.
Therefore, one of the issues addressed during the Forum was the role of IoT devices in the entrepreneurial ecosystem in the LAC region. There I took the opportunity to share the Internet Society’s vision of IoT security: we want people to benefit from the use of these devices in a trustworthy environment. The issue is particularly Continue reading
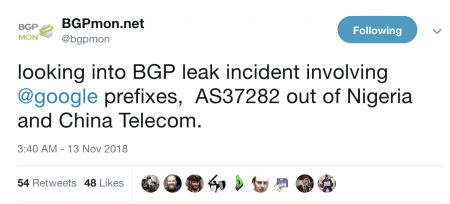
Route Leak Causes Major Google Outage

Google recently faced a major outage in many parts of the world thanks to a BGP leak. This incident that was caused by a Nigerian ISP – Mainone – occurred on 12 November 2018 between 21.10 and 22.35 UTC, and was identified in tweets from the BGP monitoring service BGPMon, as well as the network monitoring provider Thousand Eyes.
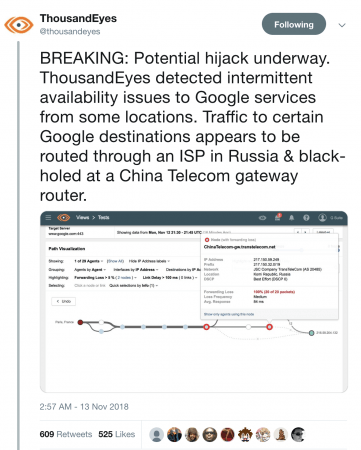
Google also announced the problem through their status page:
We’ve received a report of an issue with Google Cloud Networking as of Monday, 2018-11-12 14:16 US/Pacific. We have reports of Google Cloud IP addresses being erroneously advertised by internet service providers other than Google. We will provide more information by Monday, 2018-11-12 15:00 US/Pacific.
In order to understand this issue, MainOne Inc (AS37282) is peering at IXPN (Internet Exchange Point of Nigeria) in Lagos where Google (AS151169) and China Telecom (AS4809) are also members.
Google (AS15169) advertise their prefixes (more than 500) through the IXPN Route Server, where PCH (Packet Clearing House) collects a daily snapshot of BGP announcements of IXPN. Unfortunately, 212 prefixes (aggregates of those 500+ announcements) from Google were leaked, which was recorded by BGPMon and RIPEstat.
Looking at the RIPE stats it is evident Continue reading
In Azacualpa, Honduras: “Smart Communities” Help Preserve Collective Memory

Access to the Internet can change people’s lives for the better. This is particularly true when communities take ownership of that access and take full advantage of it to improve their quality of life. This has been the case in the community of Azacualpa, a village in Intibucá in Honduras.
In Azacualpa, the members of the community took on the task of developing and implementing the project “Smart Communities” in order to reduce the digital divide – and preserve their collective memory. The project, which is part of the Internet Society’s Beyond the Net program, finds its origin in “Radio Azacualpa – The Voice of Women,” a community radio station that started in 2017.
By 2018, Smart Communities expanded its reach by impacting the nearly 400 families that inhabit the Azacualpa Valley. To achieve its objectives, the team divided the tasks into three main groups: administrative aspects, project governance, and technical aspects. The three working groups were accompanied by the Honduras Chapter of the Internet Society and the organization Sustainable Development Network Honduras (RDS-HN).
The participation of the community was fundamental. In addition to promoting a consultation with the community, the project facilitators promoted training in communications so that community Continue reading
Inspecting Gadgets: Don’t Forget the Asterisk When Buying Smart Devices

As we approach the holiday buying season, excitement is building for all the new IoT gadgets – “smart” everything for the home, fitness/health trackers and a plethora of connected children’s toys. But this excitement should come with a giant asterisk:
* Are these products safe?
We’ve all seen the horror stories – hacked baby monitors, vulnerable door locks, robot vacuums turned into roving surveillance devices and connected toys pulled from shelves.
Clearly these gadgets need further inspection. This week the Internet Society has joined with Consumers International and Mozilla to advocate for a set of five minimum security and privacy standards IoT manufacturers should follow to improve the safety of their products. Mozilla has incorporated these into their evaluation of 70 products in the latest version of Privacy Not Included, their holiday IoT buyer’s guide. More detailed explanations of the guide and evaluation criteria are also available.
These minimum guidelines are great start to improve IoT security and privacy. They are a subset of our IoT Trust Framework, which comprehensively addresses key security, privacy and lifecycle principles that should be incorporated into IoT offerings. Manufacturers can use this list of principles to practice “trust by design,” resellers can Continue reading
U.S. R&E Community Embraces Routing Security

The Internet Society participated in a Routing Security Workshop that was held during the Internet2 Technology Exchange 2018 on 15 October 2018 in Orlando, United States. The research and education networking community has been one of the key targets of the MANRS initiative that is promoting adoption of best practices to reduce threats to the global routing system, and this community workshop followed on from a previous engagement we had with Internet2 and a number of other R&E networks in the US earlier in the year.
Internet2 interconnects R&E institutes across the United States in conjunction with regional and state networks, so we see them as a key partner in raising awareness of the routing security issues, as well as encouraging the adoption of the four MANRS principles. Indeed, one of the aims of MANRS is for network operator communities to take ownership of this process by generating awareness and disseminating best practices, along with making recommendations for improvement. So this workshop was a fantastic step in this direction.
Another positive step was Internet2 formally becoming a MANRS participant shortly before the workshop, follow in the footsteps of ESnet, CAAREN, KanREN, George Washington University, Indiana University, and DePaul University. WiscNet Continue reading
We Won’t Save the Internet by Breaking It

On the anniversary of the armistice ending the First World War, more than 40 countries stood together for security online by signing the Paris Call for Trust and Security in Cyberspace. The call, which sets out a list of challenges the world needs to tackle, seems to be promising on paper. From hacking to harming the public core – all of this needs to be addressed. And it needs to be addressed urgently.
Others signed the call too. The Internet Society signed because we believe it is a continuation of calls we have made before. It maintains that solutions to Internet issues must be developed together with other Internet stakeholders – each performing its role, and all working collaboratively.
This approach is what allows the Internet to thrive and is key to the ultimate success of this call. Open, decentralized, and distributed. It’s not the traditional multilateral way of doing things, but it is the Internet way – the only one that can work.
There are real and pressing Internet security concerns. It’s critical that signatories to the call do not imagine they can address the concerns alone. The Internet depends, as a technical fact, on cooperative voluntary action, so Continue reading
IoT Offers Opportunity, But We Must Also Advocate for Privacy

Our world is evolving exceedingly fast these days. Within the last few years in what has been coined the fourth industrial revolution we have witnessed evolutionary developments. One of those fascinating advancements concerns the everyday things and devices now connected to the Internet, also known as the Internet of Things (IoT). However, while every invention brings brand new exciting opportunities, it also entails disadvantages and may result in possible adverse consequences, if the disadvantages are not taken notice of.
Certainly IoT first and foremost provides an opportunity for a more comfortable and organized life. People may enjoy the chance to not preoccupy themselves with, for instance, managing their morning routines that may include waking up at a specific time, preparing the breakfast, and so on. Nowadays when your alarm clock can be connected to the thermostat and the latter has the information about the heavy snowfall of the night, the alarm can automatically readjust itself to wake you up an hour earlier than planned so that you manage to get to work on time.
Other examples may include smart scheduling programs or fitness tracking watches. As a runner, I personally am at ease realizing that I do not have to Continue reading
The Week in Internet News: China Wants Fairer Internet, More Control

China wants fairness: Chinese President Xi Jinping called for international cooperation to make the Internet more “fair and equitable,” while also asserting the Chinese government’s authority to shape it, Reuters reports. Xi has pushed for his country’s “cyber sovereignty” while promoting “core socialist values” online. Chinese officials also promoted the idea that each country should choose its own Internet “governance model,” The Star says.
Drones for broadband: A U.K. company has begun using drones to build fiber broadband networks in remote areas, reports Computer Weekly. Openreach is using drones to lay fiber in remote areas of the Scottish Highlands, where river gorges have previously presented a challenge.
Encrypted chat busted: Dutch police have found a way to infiltrate IronChat, an encrypted chat service running on proprietary hardware, Gizmodo says. The police were able to read 258,000 messages on the service, which costs about US$1,700 for a six-month subscription. News reports suggest the encryption wasn’t as strong as the vendor may have claimed.
Saving the Web: World Wide Web creator Tim Berners-Lee has been pushing a new Contract for the Web, in hopes of defining the responsibilities that governments, companies and citizens each have on the Web. Shortlist.com examines Continue reading
Global Cybersecurity and the Internet Conundrum

Today marks the 100th anniversary of the armistice that ended the first World War. The 1918 ceasefire re-introduced a fragile peace that had collapsed when the world failed to defend common rules and international cooperation. International security and stability are as important now as they were a century ago.
That’s why French President Emmanuel Macron and leaders from around the world are about to gather in Paris for the first Paris Peace Forum. The forum will attempt to pave a way forward for a world that is shifting and changing faster than most of us can keep up with. That change and shift, and the speed of it is enabled by the Internet.
That is why the Internet Society is participating in the Forum.
I will be in Paris to speak on a panel about creating peace in cyberspace. Cybersecurity concerns across the world are real and justified and need to be addressed. We believe that the collaborative approach that helped to drive the growth of the Internet and allows it to thrive is essential for establishing cybersecurity.
The essence of a collaborative approach is that it allows stakeholders to create a shared vision for security.
The Shared Vision
At the Continue reading
Making the Case for Community Networks at Africa IGF

Who supplies your Internet? If you live in urban Africa, you probably get Internet access through your mobile phone or through fibre at the office or home. When you travel to rural or underserved areas, there is probably limited or no Internet because mobile network operators and Internet Service Providers (ISPs) have yet to reach these areas. But what if people in rural and underserved areas could build their own networks to provide the telecommunications services that they need?
This notion has been tried successfully in several African countries. In Kenya, Tunapanda Institute has built TunapandaNET a wireless network connecting schools and youth centres in Kibera, Kenya’s largest slum. Bosco is a solar-powered wireless network that connects community ICT centres in Gulu, Northern Uganda. PamojaNet operates a wireless network to the community in Idjwi Island on lake Kivu, Eastern DRC, close to the border with Rwanda. Others such as Machaworks in rural Zambia and Zenzeleni Networks in Eastern Cape of South Africa provide similar services. These networks have been built by local communities to provide access to both offline content and Internet access where possible to the communities that they serve.
During a session at the 2018 Africa Internet Governance Continue reading
IETF 103, Day 4: Trusted Systems, IoT & IPv6

This week is IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Thursday actually represents the last day of the meeting this time, although there’s still several sessions to draw attention to.
SUIT is meeting first thing at 09.00 UTC+9. This is considering how the firmware of IoT devices can securely updated, and the architecture and information models for this will be discussed. There are three other drafts relating to manifest formats that are the meta-data describing the firmware images.
NOTE: If you are unable to attend IETF 103 in person, there are multiple ways to participate remotely.
DMM is the first of the afternoon sessions at 13.50 UTC+7, and there are several IPv6-related drafts under consideration. Proxy Mobile IPv6 extensions for Distributed Mobility Management proposes a solution whereby mobility sessions are anchored at the last IP hop router, whilst Segment Routing IPv6 for Mobile User Plane defines segment routing behaviour and applicability to the mobile user plane behaviour and defines the functions for that. There’s also three updated drafts on 5G implementations which may interest some.
To round off the week, there’s a choice Continue reading
IETF 103, Day 3: DNS Privacy, TLS & IoT

This week is IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Wednesday is a relatively light day in this respect, although there’s some pretty important matters being discussed today.
DPRIVE kicks off the day at 09.00 UTC+9, and will mostly be discussing user perspectives with respect to the recently introduced implementations of DNS-over-TLS and DNS-over-HTTPS, as well as the issues of DNS privacy between resolvers and authoritative servers. There’s also a new draft up for discussion on DNS-over-TLS for insecure delegations that describe an alternative authentication mechanism without need for DNSSEC support.
NOTE: If you are unable to attend IETF 103 in person, there are multiple ways to participate remotely.
TLS holds its second session of the week immediately after lunch at 12.20 UTC+7. This will carry-on where it left off on Monday, although will be discussing a DANE Record and DNSSEC Authentication Chain Extension for TLS. The intention is to allow TLS clients to perform DANE authentication of a TLS server without needing to perform additional DNS record lookups.
Then at 13.50 UTC+7, Homenet will be focusing on Homenet Naming Continue reading
Internet Hall of Fame Nominations Open 1 January
Do you know someone who has played a major role in the development and advancement of the Internet? On 1 January 2019, the Internet Hall of Fame will open nominations for its 2019 class of inductees.
The Internet Hall of Fame was launched in 2012 by the Internet Society. With more than 100 inductees, the Internet Hall of Fame celebrates Internet pioneers and innovators from around the world who have helped change the way we live and work today. Their trailblazing accomplishments are as broad and diverse as the Internet itself; expanding the Internet’s benefits into new regions and communities, and creating new technologies and standards that were foundational to the Internet’s development and expansion.
The Internet Hall of Fame recognizes:
- Individuals who were instrumental in the design and development of the Internet with exceptional achievements that impacted the Internet’s global advancement and evolution; or
- Individuals who made outstanding technological, commercial, or other advances and helped to expand the Internet’s positive impact on the lives of others; or
- Individuals who made major contributions to the growth, connectivity, and use of the Internet, either on a global scale or within a specific region that resulted in global impact.
If you know Continue reading
IETF 103, Day 2: IPv6, NTP, Routing Security & IoT

This week is IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. And following on from the previous day, Tuesday also features a packed agenda.
LPWAN will be discussing whether to move to a Working Group Last Call on the Static Context Header Compression (SCHC) framework for IPv6 and UDP, that provides both header compression and fragmentation functionalities. Three other drafts describe similar schemes for SigFox,LoRaWAN and IEEE 802.15.4 type networks.
NOTE: If you are unable to attend IETF 103 in person, there are multiple ways to participate remotely.
Then at 11.20 UTC+7, IPWAVE will be focusing on updates to the specification for transmitting IPv6 Packets over IEEE 802.11 Networks in Vehicular communications, and the use cases for IP-based vehicular networks. There have also been a couple of updates to DNS Name Autoconfiguration for Internet of Things Devices and IPv6 Neighbor Discovery for Prefix and Service Discovery in Vehicular Networks, so these may also be discussed.
6MAN will be meeting at 13.50 UTC+7 and has nine drafts up for discussion. The couple of working group Continue reading
The Youth Internet Governance Forum India: Our Experience

On 12 October, the Internet Society’s India Delhi Chapter (ISOC-Delhi) hosted the Youth Internet Governance Forum (YIGF) in New Delhi, India. Adarsh Umesh and Praneet Kaur share their thoughts on the event.
Hello everyone! A special “Hi!” from our side to the youth because this blog is specially dedicated to the youth of India.
 We’re very much inspired to write this blog due to the wonderful experience with the India Youth Internet Governance Forum (YIGF 2018). It was amazing to be a part of the multistakeholder advisory group and the event overall was a grand success. This would not have been possible without the consistent support from inSIG, ICANN, APNIC and the Internet Society.
We’re very much inspired to write this blog due to the wonderful experience with the India Youth Internet Governance Forum (YIGF 2018). It was amazing to be a part of the multistakeholder advisory group and the event overall was a grand success. This would not have been possible without the consistent support from inSIG, ICANN, APNIC and the Internet Society.
The YIGF 2018 was organized as day 0 event on the 12th October 2018, a day before the India School on Internet Governance 2018 (inSIG-2018) at Indira Gandhi Delhi Technical University for Women (IGDTUW). The event was well-designed and planned with a lot of technical exposure as well as fun. It extended support to youth from all over the country to attend the event. We provided fellowships to 15 delegates from different parts across India. The fellowship covered both travel and accommodation expenses for five Continue reading
The Week in Internet News: Companies Fear AI Will Destroy Business Models

AI against businesses: More than 40 percent of U.K. companies believe Artificial Intelligence will destroy their business models within five years, according to a Microsoft survey featured on CNBC.com. Still, more than half of businesses in the U.K. have no AI strategy. And while 45 percent workers are concerned their job could be replaced by AI, 51 percent are not learning skills to prepare for the changes.
Government AI board: Meanwhile, Public Knowledge, a digital rights advocacy group, has called on the U.S. government to create a new federal authority to develop AI expertise, as a way to effectively regulate and govern the technology, reports IP-watch.org. “The rapid and pervasive rise of artificial intelligence risks exploiting the most marginalized and vulnerable in our society,” the group argues.
Math against fake news: Professors from the U.K. and Switzerland have released a mathematical definition of fake news, in the hope that it will give lawmakers ideas on how to combat it, Phys.org says. The researchers have also introduced a model for fake news that can be used to study the phenomenon.
Vietnam against fake news: A new cybersecurity law in Vietnam is intended to combat Continue reading
IETF 103, Day 1: IPv6, TLS, DNS Privacy & Other Crypto

The Working Group sessions start tomorrow at IETF 103 in Bangkok, Thailand, and we’re bringing you daily blog posts highlighting the topics of interest to us in the ISOC Internet Technology Team. Only four days have been scheduled for the working groups this time around, which means there’s a lot of pack into each day; with Monday being no exception.
V6OPS is a key group and will be meeting on Monday morning starting at 09.00 UTC+7. It’s published four RFCs since its last meeting, including Happy Eyeballs v2, and this time will kick-off with a presentation on the CERNET2 network which is an IPv6-only research and education in China.
There’s also four drafts to be discussed, including three new ones. IPv6-Ready DNS/DNSSSEC Infrastructure recommends how DNS64 should be deployed as it modifies DNS records which in some circumstances can break DNSSEC. IPv6 Address Assignment to End-Sites obsoletes RFC 6177 with best current operational practice from RIPE-690 that makes recommendations on IPv6 prefix assignments, and reiterates that assignment policy and guidelines belong to the RIR community. Pros and Cons of IPv6 Transition Technologies for IPv4aaS discusses different use case scenarios for the five most prominent IPv4-as-a-service (IPv4aaS) transitional technologies, Continue reading
pkSIG 2018: A Fellow’s Perspective

The Pakistan School on Internet Governance 2018 (pkSIG) took place at the Regent Plaza Hotel in Karachi from 3-6 September 2018. It offered a four day intensive learning course, covering the political, legal, economic, socio-cultural, and technological dimensions of Internet Governance within the context of the Pakistani national imperatives. The program included theoretical sessions, role play, and participant engagement activities.
One of the objectives of the seminar was to develop a shared understanding of youth participation in Internet Governance by building expertise through the alumni of the school. A fellowship opportunity was offered to young applicants from the Sindh and Baluchistan provinces who presented a strong motivation to continue to work locally on IG issues after the pkSIG.
The involvement of students and young professionals, like the ICT engineer Sohaib Bukhari, is a successful example of meaningful participation in the shaping of the Internet. They are the generation that has been using the Internet since they were children, they are the ones who will be using it for the next 50 years. Sohaib was thrilled to have an open dialogue with the key stakeholders, while gaining access to comprehensive and structured knowledge on various aspects of the Internet Governance.
So, Continue reading