Worth Reading: AI Is Still a Delusion
Here’s another AI rant to spice your summer: AI Is Still a Delusion, including an excellent example of how the latest LLMs flunk simple logical reasoning. I particularly liked this one-line summary:
The real danger today is not that computers are smarter than us but that we think computers are smarter than us and consequently trust them to make decisions they should not be trusted to make.
It might be worth remembering that quote when an AI-powered management appliance messes up your network because of a false positive ;)
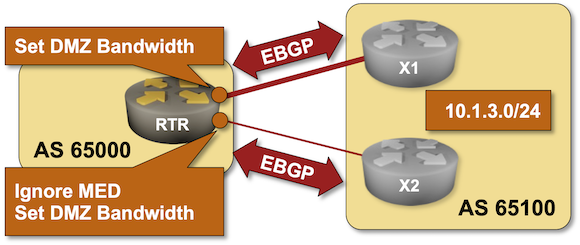
EBGP Load Balancing with BGP Link Bandwidth
The first BGP load balancing lab exercise described the basics of EBGP equal-cost load balancing. Now for the fun part: what if you want to spread traffic across multiple links in an unequal ratio? There’s a nerd knob for that: the BGP Link Bandwidth extended community that you can test-drive in this lab exercise.
Worth Reading: GitHub Copilot Workspace Review
In Matt Duggan’s blog post, you’ll find a scathing review of another attempt to throw AI spaghetti at the wall to see if they stick: the GitHub Copilot Workspace.
He also succinctly summarized everything I ever wanted to say about the idea of using AI tools to generate networking configurations:
Having a tool that makes stuff that looks right but ends up broken is worse than not having the tool at all.
Worth Reading: Why Do We Have Native VLANs?
Daniel Dib went on another deep dive: Why Do We Have Native VLANs? What I loved most was that he went through the whole 802.1 standard (quite an undertaking) and explained the reasoning that VLAN-aware switches behave the way they do.
You should also read the follow-up post: what happens if a VLAN-unaware switch receives an 802.1Q-tagged frame?
Again: What Exactly Is MPLS?
Brad Casemore published an interesting analysis explaining why Cisco should accept being a mature company with mature products (yeah, you have to subscribe to view it). I always loved reading his articles, but unfortunately, this time, he briefly ventured into the “I don’t think this word means what you think it means” territory:
MPLS worked – and it still works – but it provided optimal value in an earlier time when the center of gravity was not the cloud. The cloud challenged the efficacy of MPLS, and it wasn’t long before SD-WAN, cloud connects, and interconnects […] represented an implacable threat to a status quo that had once seemed unassailable.
The second part of the paragraph is (almost) true, but it had nothing to do with MPLS.
Worth Reading: Terminal Line Editing
In another wonderful deep dive, Julia Evans explains why you can’t edit the command line in some Linux utilities like the ancient sh.
You’ll also figure out:
- Why does CTRL-A jump to the beginning of the line?
- How can you enable command line editing in ancient utilities?
Have fun!
BGP Labs: a Year Later
Last summer, I started a long-term project to revive the BGP labs I created in the mid-1990s. I completed the original lab exercises (BGP sessions, IBGP, local preference, MED, communities) in late 2023 but then kept going. This is how far I got in a year:
- Twenty-six deploy BGP exercises, including advanced settings like AS path manipulations, MD5 passwords and BFD, and new technologies like TCP/AO and interface EBGP sessions.
- Fifteen BGP routing policies exercises, covering the basic mechanisms as well as dirty tricks like route disaggregation
- Four load balancing exercises, from EBGP ECMP to BGP Link Bandwidth and BGP Additional Paths.
- Five challenges for everyone who got bored doing the simple stuff ;)
That completes the BGP technologies I wanted to cover. I’ll keep adding the challenge labs and advanced scenarios. Here are some ideas; if you have others, please leave a comment.
blog.ipspace.net Is On Cloudflare Pages
Long story short: Years after migrating my blog to Hugo, I found the willpower to deal with the “interesting” way Cloudflare Pages deal with static HTML files, changed the Hugo URL scheme, and spent two days fixing broken links.
Apart from having the satisfaction of ticking off a long-outstanding project, the blog pages should load faster, and I won’t have to deal with GitLab hiccups anymore.
If you notice anything being broken, please let me know. Thank you!
MUST READ: ChatGPT Is Bullshit
Bogdan Golab sent me a link to an (open access) article in Ethics and Information Technology arguing why ChatGPT is bullshit. Straight from the introduction:
Because these programs cannot themselves be concerned with truth, and because they are designed to produce text that looks truth-apt without any actual concern for truth, it seems appropriate to call their outputs bullshit.
Have fun!
MUST READ: ChatGPT Is Bullshit
Bogdan Golab sent me a link to an (open access) article in Ethics and Information Technology arguing why ChatGPT is bullshit. Straight from the introduction:
Because these programs cannot themselves be concerned with truth, and because they are designed to produce text that looks truth-apt without any actual concern for truth, it seems appropriate to call their outputs bullshit.
Have fun!
Master New Platforms and Technologies with netlab
One of my readers sent me this remark (probably while trying to work on the EBGP Sessions over the IPv6 LLA Interfaces lab):
I did attempt some of your labs, like IPv6 link-local-only BGP with FRR hosts, but FRR seemed not to play ball, or I was just doing it wrong.
As he was already using netlab, I could send him a cheat code:
Master New Platforms and Technologies with netlab
One of my readers sent me this remark (probably while trying to work on the EBGP Sessions over the IPv6 LLA Interfaces lab):
I did attempt some of your labs, like IPv6 link-local-only BGP with FRR hosts, but FRR seemed not to play ball, or I was just doing it wrong.
As he was already using netlab, I could send him a cheat code:
Running Arista cEOS in GitHub Codespaces
Yesterday, I explained how you can run netlab examples in GitHub codespaces and mentioned that they work best with vendors who understand the value of frictionless downloads. But what if you’d like to use a device from one of the good guys who provide the container images but require a registration?
It turns out the solution is trivial:
Running Arista cEOS in GitHub Codespaces
Yesterday, I explained how you can run netlab examples in GitHub codespaces and mentioned that they work best with vendors who understand the value of frictionless downloads. But what if you’d like to use a device from one of the good guys who provide the container images but require a registration?
It turns out the solution is trivial:
Netlab Examples in GitHub Codespaces
A few days ago, someone asked me about the IPv4 next-hop details of running interface EBGP sessions. I pointed him to a blog post explaining them, adding, “And of course, you can test that in netlab.” A few minutes later, it hit me: instead of asking him to set up netlab locally, I could enable him to do that in a minute with GitHub codespaces.
Setting that up was easy: copy the .devcontainer directory from the BGP labs repository into the netlab examples repository and commit the change. After a short yak-shaving exercise (writing README files and rearranging a few folders), I successfully started the codespace and was ready for this blog post. There was just one gotcha…
Netlab Examples in GitHub Codespaces
A few days ago, someone asked me about the IPv4 next-hop details of running interface EBGP sessions. I pointed him to a blog post explaining them, adding, “And of course, you can test that in netlab.” A few minutes later, it hit me: instead of asking him to set up netlab locally, I could enable him to do that in a minute with GitHub codespaces.
Setting that up was easy: copy the .devcontainer directory from the BGP labs repository into the netlab examples repository and commit the change. After a short yak-shaving exercise (writing README files and rearranging a few folders), I successfully started the codespace and was ready for this blog post. There was just one gotcha…
Worth Reading: The Evolution of Network Security
Sharada Yeluri published an interesting overview of the evolution of network security, from packet filtering firewalls to GenAI and Quantum Computing (yeah, she works for a networking vendor ;). Definitely worth reading if you’re looking for an intro-level overview.
Worth Reading: The Evolution of Network Security
Sharada Yeluri published an interesting overview of the evolution of network security, from packet filtering firewalls to GenAI and Quantum Computing (yeah, she works for a networking vendor ;). Definitely worth reading if you’re looking for an intro-level overview.
Worth Reading: Don’t Use Excel as a Source of Truth
Some people insist on using Excel as the ultimate source of user-supplied data (including network automation source of truth).
If you agree with me that that’s not necessarily the best idea out there, you might enjoy this rant by Nikhil Suresh.
Worth Reading: Don’t Use Excel as a Source of Truth
Some people insist on using Excel as the ultimate source of user-supplied data (including network automation source of truth).
If you agree with me that that’s not necessarily the best idea out there, you might enjoy this rant by Nikhil Suresh.
