Famous Last Words: I’m Too Stupid for That
Some networking vendors realized that one way to gain mindshare is to make their network operating systems available as free-to-download containers or virtual machines. That’s the right way to go; I love their efforts and point out who went down that path whenever possible1 (as well as others like Cisco who try to make our lives miserable).
However, those virtual machines better work out of the box, or you’ll get frustrated engineers who will give up and never touch your warez again, or as someone said in a LinkedIn comment to my blog post describing how Junos vPTX consistently rejects its DHCP-assigned IP address: “If I had encountered an issue like this before seeing Ivan’s post, I would have definitely concluded that I am doing it wrong.”2
Famous Last Words: I’m Too Stupid for That
Some networking vendors realized that one way to gain mindshare is to make their network operating systems available as free-to-download containers or virtual machines. That’s the right way to go; I love their efforts and point out who went down that path whenever possible1 (as well as others like Cisco who try to make our lives miserable).
However, those virtual machines better work out of the box, or you’ll get frustrated engineers who will give up and never touch your warez again, or as someone said in a LinkedIn comment to my blog post describing how Junos vPTX consistently rejects its DHCP-assigned IP address: “If I had encountered an issue like this before seeing Ivan’s post, I would have definitely concluded that I am doing it wrong.”2
Worth Reading: Cisco vPC in VXLAN/EVPN Networks
Daniel Dib started writing a series of blog posts describing Cisco vPC in VXLAN/EVPN Networks. The first one covers the anycast gateway, the second one the vPC configuration.
Let’s hope he will keep them coming and link them together so it will be easy to find the whole series after stumbling on one of the posts ;)
Worth Reading: Cisco vPC in VXLAN/EVPN Networks
Daniel Dib started writing a series of blog posts describing Cisco vPC in VXLAN/EVPN Networks. The first one covers the anycast VTEP, the second one the vPC configuration.
Let’s hope he will keep them coming and link them together so it will be easy to find the whole series after stumbling on one of the posts ;)
Public Videos: Network Connectivity and Graph Theory

When I decided to sunset the ipSpace.net subscription, I asked Rachel Traylor whether I could make the content of her webinars public. She graciously agreed, and the first results are already here: you can download approximately half of the videos from the Network Connectivity and Graph Theory without a valid ipSpace.net account. Enjoy!
BGP Labs: EBGP Sessions over IPv6 LLA Interfaces
If you insist on building your network with EBGP as a better IGP, make sure your implementation supports running IPv4 and IPv6 address families over EBGP sessions established between IPv6 link-local addresses (the functionality lovingly called unnumbered EBGP sessions).
Want to practice that neat trick? Check out the EBGP Sessions over IPv6 LLA Interfaces lab exercise.
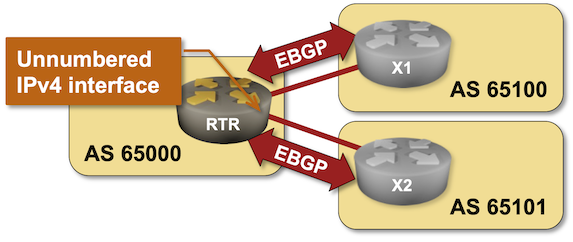
BGP Labs: EBGP Sessions over IPv6 LLA Interfaces
If you insist on building your network with EBGP as a better IGP, make sure your implementation supports running IPv4 and IPv6 address families over EBGP sessions established between IPv6 link-local addresses (the functionality lovingly called unnumbered EBGP sessions).
Want to practice that neat trick? Check out the EBGP Sessions over IPv6 LLA Interfaces lab exercise.

Repost: The Real LISP Mobility Use Case
Béla Várkonyi is working on an interesting challenge: building ground-to-airplane(s) networks providing multilink mobility. Due to its relative simplicity, he claims LISP works much better than BGP in that environment.
In some newer routers BGP would not be such a big bottleneck, but you need a lot of knob turning in BGP to get it right, while in LISP it is quite simple.
If you have many thousands concurrent airplanes with multi-link and max. 16 subnets with different routing policies on each, and the radio links are going up and down, then you have a large number of mobility events.
Repost: The Real LISP Mobility Use Case
Béla Várkonyi is working on an interesting challenge: building ground-to-airplane(s) networks providing multilink mobility. Due to its relative simplicity, he claims LISP works much better than BGP in that environment.
In some newer routers BGP would not be such a big bottleneck, but you need a lot of knob turning in BGP to get it right, while in LISP it is quite simple.
If you have many thousands concurrent airplanes with multi-link and max. 16 subnets with different routing policies on each, and the radio links are going up and down, then you have a large number of mobility events.
netlab: Global and Node VRFs
When designing the netlab VRF configuration module, I tried to make it as flexible as possible while using the minimum number of awkward nerd knobs. As is often the case1, the results could be hard to grasp, so let’s walk through the various scenarios of using global and node VRFs.
netlab allows you to define a VRF in the lab topology vrfs dictionary (global VRF) or in a node vrfs dictionary (node VRF). In most cases, you’d define a few global VRFs and move on.
netlab: Global and Node VRFs
When designing the netlab VRF configuration module, I tried to make it as flexible as possible while using the minimum number of awkward nerd knobs. As is often the case1, the results could be hard to grasp, so let’s walk through the various scenarios of using global and node VRFs.
netlab allows you to define a VRF in the lab topology vrfs dictionary (global VRF) or in a node vrfs dictionary (node VRF). In most cases, you’d define a few global VRFs and move on.
Worth Reading: Comparing GNS3, containerlab, and netlab
You probably know I hate posting links to walled gardens or sites that try really hard to make you sign up. Sometimes, I have to make an exception: Roman Pomazanov wrote a great (and humorous) article comparing how easy it is to set up simple labs with GNS3, containerlab, and netlab.
Worth Reading: Comparing GNS3, containerlab, and netlab
You probably know I hate posting links to walled gardens or sites that try really hard to make you sign up. Sometimes, I have to make an exception: Roman Pomazanov wrote a great (and humorous) article comparing how easy it is to set up simple labs with GNS3, containerlab, and netlab.
Repost: Think About the 99% of the Users
Daniel left a very relevant comment on my Data Center Fabric Designs: Size Matters blog post, describing how everyone rushes to sell the newest gizmos and technologies to the unsuspecting (and sometimes too-awed) users1:
Absolutely right. I’m working at an MSP, and we do a lot of project work for enterprises with between 500 and 2000 people. That means the IT department is not that big; it’s usually just a cost center for them.
Repost: Think About the 99% of the Users
Daniel left a very relevant comment on my Data Center Fabric Designs: Size Matters blog post, describing how everyone rushes to sell the newest gizmos and technologies to the unsuspecting (and sometimes too-awed) users1:
Absolutely right. I’m working at an MSP, and we do a lot of project work for enterprises with between 500 and 2000 people. That means the IT department is not that big; it’s usually just a cost center for them.
Stop the Network-Based Application Recognition Nonsense
One of my readers sent me an interesting update on the post-QUIC round of NBAR whack-a-mole (TL&DR: everything is better with Bluetooth AI):
So far, so good. However, whenever there’s a change, there’s an opportunity for marketing FUD, coming from the usual direction.
Stop the Network-Based Application Recognition Nonsense
One of my readers sent me an interesting update on the post-QUIC round of NBAR whack-a-mole (TL&DR: everything is better with Bluetooth AI):
So far, so good. However, whenever there’s a change, there’s an opportunity for marketing FUD, coming from the usual direction.
Presentation: Introduction to netlab
On April 22nd, I had an Intro to netlab presentation at the wonderful RIPE SEE meeting in Athens.
You can download the presentation or watch it on YouTube. Enjoy ;)
Presentation: Introduction to netlab
On April 22nd, I had an Intro to netlab presentation at the wonderful RIPE SEE meeting in Athens.
You can download the presentation or watch it on YouTube. Enjoy ;)
Repost: Campus-Wide Wireless Roaming with EVPN
As a response to my LISP vs EVPN: Mobility in Campus Networks blog post, Route Abel provided interesting real-life details of a large-scale campus wireless testing using EVPN and VXLAN tunnels to a central aggregation point (slightly edited):
I was arguing for VxLAN EVPN with some of my peers, but I had no direct hands-on knowledge of how it would actually perform and very limited ability to lab it on hardware. My client was considering deploying Campus VxLAN, and they have one of the largest campuses in North America.