Feedback: Ansible for Networking Engineers
One of ipSpace.net subscribers sent me the following feedback on Ansible for Networking Engineers webinar:
The “Ansible for Network Engineers” webinar is of the highest caliber. I’ve taken Ansible courses with your CCIE peers, and though they are good, I objectively feel, that I get more of a total comprehensive understanding with network automation here at ipSpace. Also, I enjoy your professional care-free tone, and how you pepper humor into the subject matter.
I’ve setup a virtual lab with Ubuntu 18.04 LTS server, and am using both Aruba and Cisco switches/routers. Ansible has lots of nuances that will take me time to fully get a grip-on– but, that’s why I subscribe with the network pros like ipSpace.
Worth Reading: Switching the Technology Stack
Did you ever wonder why a company would replace a working technology with an overhyped pile of half-baked code? Why we at $FAMOUS_COMPANY Switched to $HYPED_TECHNOLOGY by Saagar Jha is a hilarious take on the subject.
Want more? How about migrating your Exadata database to AWS?
Worth Reading: Switching the Technology Stack
Did you ever wonder why a company would replace a working technology with an overhyped pile of half-baked code? Why we at $FAMOUS_COMPANY Switched to $HYPED_TECHNOLOGY by Saagar Jha is a hilarious take on the subject.
Want more? How about migrating your Exadata database to AWS?
Video: Functions-as-a-Service Demo
Serverless computing (marketing term for code running on servers managed by other people) is one of the must-have terms if you’re playing a Buzzword Bingo, but what does it really mean and how does the whole thing work?
Matthias Luft and Florian Barth illustrated the concept during the Introduction to Cloud Computing webinar with a short demo in which they build a simple AWS Lambda function.
Video: Functions-as-a-Service Demo
Serverless computing (marketing term for code running on servers managed by other people) is one of the must-have terms if you’re playing a Buzzword Bingo, but what does it really mean and how does the whole thing work?
Matthias Luft and Florian Barth illustrated the concept during the Introduction to Cloud Computing webinar with a short demo in which they build a simple AWS Lambda function. For a more network-centric view, read the Can We Ping a Lambda Function blog post by Noel Boulene.
Should We Use LISP?
LISP started as yet-another ocean-boiling project focused initially on solving the “we use locators as identifiers” mess (not quite), and providing scalable IPv6 connectivity over IPv4-only transport networks by adding another layer of indirection and thus yet again proving RFC 1925 rule 6a. At least those are the diagrams I remember from the early “look at this wonderful tool” presentations explaining for example how Facebook is using LISP to deploy IPv6 (more details in this presentation).
Somehow that use case failed to gain traction and so the pivots1 started explaining how one can use LISP to solve IP mobility or IP multihoming or live VM migration, or to implement IP version of conversational learning in Cisco SD-Access. After a few years of those pivots, I started dismissing LISP with a short “cache-based forwarding never worked well” counterargument.
Should We Use LISP?
LISP started as yet-another ocean-boiling project focused initially on solving the “we use locators as identifiers” mess (not quite), and providing scalable IPv6 connectivity over IPv4-only transport networks by adding another layer of indirection and thus yet again proving RFC 1925 rule 6a. At least those are the diagrams I remember from the early “look at this wonderful tool” presentations explaining for example how Facebook is using LISP to deploy IPv6 (more details in this presentation).
Somehow that use case failed to gain traction and so the pivots1 started explaining how one can use LISP to solve IP mobility or IP multihoming or live VM migration, or to implement IP version of conversational learning in Cisco SD-Access. After a few years of those pivots, I started dismissing LISP with a short “cache-based forwarding never worked well” counterargument.
Segment Routing vs LDP in Hub-and-Spoke Networks
I got an interesting question that nicely illustrates why Segment Routing (the MPLS variant) is so much better than LDP. Imagine a redundant hub-and-spoke network with hundreds of spokes. Let’s settle on 500 spokes – IS-IS supposedly has no problem dealing with a link-state topology of that size.
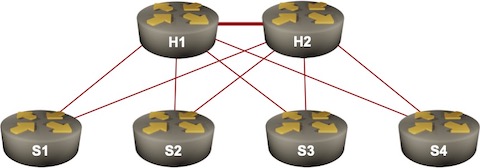
Let’s further assume that all routers advertise only their loopbacks1 and that we’re using unnumbered hub-to-spoke links to minimize the routing table size. The global routing table thus contains ~500 entries. MPLS forwarding tables (LFIB) contain approximately as many entries as each router assigns a label to every prefix in the routing table2. What about the LDP table (LIB – Label Information Base)?
Segment Routing vs LDP in Hub-and-Spoke Networks
I got an interesting question that nicely illustrates why Segment Routing (the MPLS variant) is so much better than LDP. Imagine a redundant hub-and-spoke network with hundreds of spokes. Let’s settle on 500 spokes – IS-IS supposedly has no problem dealing with a link-state topology of that size.

Let’s further assume that all routers advertise only their loopbacks1 and that we’re using unnumbered hub-to-spoke links to minimize the routing table size. The global routing table thus contains ~500 entries. MPLS forwarding tables (LFIB) contain approximately as many entries as each router assigns a label to every prefix in the routing table2. What about the LDP table (LIB – Label Information Base)?
Flow-Based Packet Forwarding
In the Cache-Based Packet Forwarding blog post I described what happens when someone tries to bypass the complexities of IP routing table lookup with a forwarding cache.
Now imagine you want to implement full-featured fast packet forwarding including ingress- and egress ACL, NAT, QoS… but find the required hardware (TCAM) too expensive. Wouldn’t it be nice if we could send the first packet of every flow to a CPU to figure out what to do with it, and download the results into a high-speed flow cache where they could be used to switch the subsequent packets of the same flow. Welcome to flow-based packet forwarding.
Flow-Based Packet Forwarding
In the Cache-Based Packet Forwarding blog post I described what happens when someone tries to bypass the complexities of IP routing table lookup with a forwarding cache.
Now imagine you want to implement full-featured fast packet forwarding including ingress- and egress ACL, NAT, QoS… but find the required hardware (TCAM) too expensive. Wouldn’t it be nice if we could send the first packet of every flow to a CPU to figure out what to do with it, and download the results into a high-speed flow cache where they could be used to switch the subsequent packets of the same flow. Welcome to flow-based packet forwarding.
netsim-tools Release 1.1.3
netsim-tools release 1.1.3 brings a number of goodies, including:
- OSPFv3 support on a few platforms (we’re still looking for contributors to implement OSPFv3 on other platforms)
- EIGRP implementation of common routing protocol features (router ID, passive and external interfaces)
- Configurable address family support for IS-IS, OSPF and EIGRP
- Support for /31 IPv4 P2P links
- Configurable MTU for VyOS and RouterOS
If you’re building your own libvirt boxes, you might also appreciate:
netsim-tools Release 1.1.3
netsim-tools release 1.1.3 brings a number of goodies, including:
- OSPFv3 support on a few platforms (we’re still looking for contributors to implement OSPFv3 on other platforms)
- EIGRP implementation of common routing protocol features (router ID, passive and external interfaces)
- Configurable address family support for IS-IS, OSPF and EIGRP
- Support for /31 IPv4 P2P links
- Configurable MTU for VyOS and RouterOS
Worth Reading: Misconceptions about Route Origin Validation
Use the email sent by Randy Bush to RIPE routing WG mailing list every time a security researcher claims a technology with no built-in security mechanism is insecure (slightly reworded to make it more generic).
Lately, I am getting flak about $SomeTechnology not providing protection from this or that malicious attack. Indeed it does not.
Worth Reading: Misconceptions about Route Origin Validation
Use the email sent by Randy Bush to RIPE routing WG mailing list every time a security researcher claims a technology with no built-in security mechanism is insecure (slightly reworded to make it more generic).
Lately, I am getting flak about $SomeTechnology not providing protection from this or that malicious attack. Indeed it does not.
Worth Reading: AI Makes Animists of Us All
Erik Hoel published a wonderful article describing how he’s fighting the algorithm that is deciding whether to approve a charge on his credit card.
My credit card now has a kami. Such new technological kamis are, just like the ancient ones, fickle; sometimes blessing us, sometimes hindering us, and all we as unwilling animists can do is a modern ritual to the inarticulate fey creatures that control our inboxes and our mortgages and our insurance rates.
There are networking vendors unleashing similar “spirits” on our networks. Welcome to the brave new world ;)
Worth Reading: AI Makes Animists of Us All
Erik Hoel published a wonderful article describing how he’s fighting the algorithm that is deciding whether to approve a charge on his credit card.
My credit card now has a kami. Such new technological kamis are, just like the ancient ones, fickle; sometimes blessing us, sometimes hindering us, and all we as unwilling animists can do is a modern ritual to the inarticulate fey creatures that control our inboxes and our mortgages and our insurance rates.
There are networking vendors unleashing similar “spirits” on our networks. Welcome to the brave new world ;)
Video: Comparing TCP/IP and CLNP
If you were building networks in early 1990s you probably remember at least a half-dozen different network protocols. Only one of them survived (IPv6 came later), with another one (CLNP) providing an interesting view into a totally different parallel universe that evolved using a different set of fundamental principles.
After introducing the network-layer addressing, I compared the two and pointed out where one or the other was clearly better.
You might think that it makes no sense to talk about protocols that were rarely used in old days, and that are almost non-existent today, but as always those who cannot remember the past are doomed to repeat it, this time reinventing CLNP principles in IPv6-based layer-3-only data center fabrics.
Video: Comparing TCP/IP and CLNP
If you were building networks in early 1990s you probably remember at least a half-dozen different network protocols. Only one of them survived (IPv6 came later), with another one (CLNP) providing an interesting view into a totally different parallel universe that evolved using a different set of fundamental principles.
After introducing the network-layer addressing, I compared the two and pointed out where one or the other was clearly better.
You might think that it makes no sense to talk about protocols that were rarely used in old days, and that are almost non-existent today, but as always those who cannot remember the past are doomed to repeat it, this time reinventing CLNP principles in IPv6-based layer-3-only data center fabrics.
Data Plane Quirks in Virtual Network Devices
Have you noticed an interesting twist in the ICMP Redirects saga: operating systems of some network devices might install redirect entries and use them for control plane traffic – an interesting implementation side effect of the architecture of most modern network devices.
A large majority of network devices run on some variant of Linux or *BSD operating system, the only true exception being ancient operating systems like Cisco IOS1. The network daemons populate various routing protocol tables and compute the best routes that somehow get merged into a single routing table that might still be just a data structure in some user-mode process.