Microservices Gone Wild – Tech Dive Part 1

I’ve heard a lot of noise about microservices in the last couple of years, perhaps most notably when I attended ONUG in Spring 2015 and Adrian Cockcroft from Battery Ventures (previously from Netflix) was pushing the idea of building applications using container-based microservices very convincingly. In this short series of posts, I’ll look at what microservices are, why you might want them (particularly in containers) and — because it would be no fun if this was all just theory — I’ll run through a demonstration where I take a simple monolithic application and successfully break it out into containerized microservices. I’ll share the code I use because I just know you’ll enjoy playing along at home.
Monolithic Applications
In order to consider the benefits of microservices it’s important first to get some context by looking at what is arguably the polar opposite, the monolithic application. I should preface this by saying that defining what constitutes a monolithic application can be a rather nuanced task, depending on the perspective from which one looks. For my purposes though, a monolithic application is typically one where the entire application is delivered in a single release. Even if the application is logically deployed across Continue reading
Response: CAM Table Basics

This post is a response to Greg Ferro’s recent Basics
posts on (Content Addressable Memory) CAM tables. As this is a response post, you can assume that I don’t agree entirely with all of his definitions. Alternatively, perhaps I am totally wrong and I need to go back and relearn how CAM works. Either way, Greg loves a good spar, so maybe together with our readers we can determine the truth in an understandable format for the betterment of everybody who isn’t a hardcore digital electronics engineer.
Greg’s Posts
Before continuing, I’d recommend should go reading these posts as context, since they are the basis for this post:
Basics: What is Content Addressable Memory (CAM) ?
Basics: What is Binary CAM (BCAM) ?
Basics: What is Ternary Content Address Memory (TCAM) ?
I’ll now address my concerns post by post below.
What is CAM
A CAM cell in the chip actually consists of two SRAM cells. SRAM requires requires extensive silicon gates to implement that require a lot of power per gate for fast switching. In a chip, power consumption generates heat and leads to limits on thermal dissipation by the limited footprint of a chip. This is a key factor on the Continue reading
Pica8 Scales Up to 100G Ethernet
Pica8, early pioneer of disaggregated networking and SDN, today announced a new version of their switch operating system, PicOS v2.7.1. Normally I wouldn’t note a networking OS update, but probably the biggest single update for this release is the new support for 100GigabitEthernet switches, with support for both Broadcom and Cavium / XPliant ASICs.
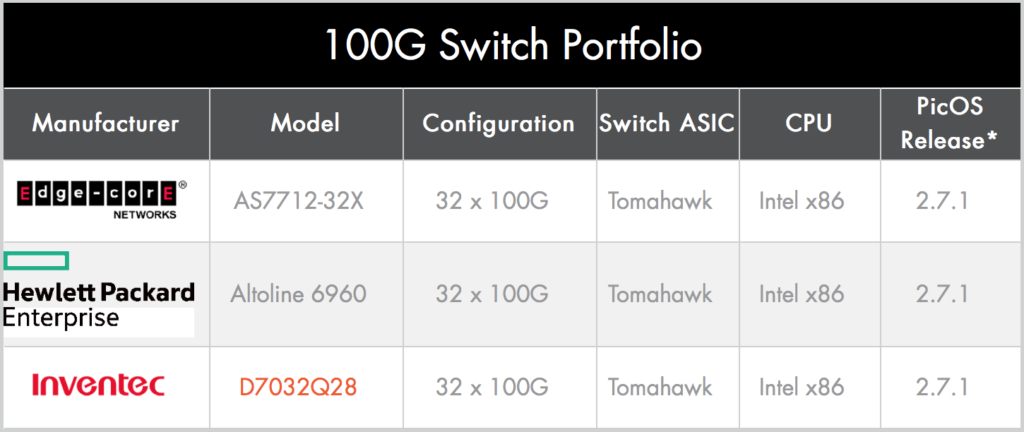
Currently the Hardware Compatibility List for 100G only features Broadcom-based switches but that will undoubtedly change as relative newcomer Cavium / XPliant continues to challenge Broadcom for speed, features and flexibility. I’m also curious to know whether in the future we’ll see hardware on that list using the Barefoot Tofino™ ASIC as well.
In addition to expanding the supported hardware offerings from HP Enterprise, the HCL now also features the first Dell platform to be certified. Dell and HPE are positioning themselves quite effectively as the branded whitebox solution of choice and their devices are supported by a number of software vendors now.
But why do we care about 100G Ethernet, PicOS and more advanced ASICs?

That’s right; because we always want more than we currently have. And, I suppose, because we keep on scaling our networks with more, faster servers. Sure, we’ll Continue reading
Cumulus, Dell, Red Hat Demo Linux as Full Stack SDDC

Cumulus Networks announced today that in conjunction with Dell and Red Hat, it has created a 300+ node OpenStack pod using standard open source DevOps tools to manage the deployment from top to bottom (i.e. from the spine switch down to the compute node). I thought that was interesting enough to justify a quick post.
All Linux, All The Time
I visited with Cumulus Linux as part of Networking Field Day 9 and learned two very important things:
- Cumulus co-founder, CEO (at the time), and now CTO, JR Rivers makes a mean cup of espresso;
- The culture at Cumulus is all about standards. It was expressed repeatedly that Cumulus want to ensure that their linux is absolutely standard, so the file system hierarchy should be the standard, configuration files should be where they normally are, and so forth. A system that doesn’t follow those guidelines becomes a special snowflake that can’t be supported by regular tools and, as you’ll see, this attitude has paid dividends in this solution.
The idea of this software stack demo is to take linux-based switches (Dell brite-box
Cumulus-certified hardware running the Cumulus Linux OS) and connect in linux-based compute resources (Dell PowerEdge servers running Continue reading
Late Breaking: Cisco Switches to Arista
The legal feud between Cisco and Arista may finally be over, though perhaps not in the way any of us had expected.


The news starting to filter out of San Jose this morning is that Cisco has agreed to drop its lawsuit in return for the immediate acquisition of Arista Networks’ assets, intellectual property and employees. After the ITC’s initial determination last month that Arista had infringed on three out of five patents listed in the suit, it is understood that this solution was urgently brokered to protect the company’s employees from the potential fallout should the ITC’s next ruling be less than favorable.
Sources close to Cisco CEO Chuck Robbins are saying that Cisco plans to rebrand Arista’s impressive 7500 switch hardware as the new flagship Cisco Nexus 8000 series. With its reassuringly familiar command line interface, Arista’s EOS should be a seamless addition to Cisco’s impressive existing portfolio of network operating systems (i.e. IOS, Native IOS, IOS-XR, IOS-XRv, IOS-XE and NXOS) and customers will likely be lining up to deploy the impressive new Nexus 8000 series hardware without having to suffer through the pains of the usual new product learning curve.
In some ways the timing of Continue reading
IOS For iOS – New Cisco App Brings Network Control To iPhone
This morning Cisco announced the release of a groundbreaking new product offering complete control of a Cisco-based enterprise network using Apple’s iPhone™ platform. IOS For iOS
, or IFi®
(pronounced eye-Fie, kind of like WiFi but without the W) will be available in the App Store in July 2016. Cisco have described the app as bringing Cellphone Defined Networking
(CDN) to busy network engineers and administrators.

What Is IOS For iOS?
The basic idea is to offer real time telemetry and full remote automation of the network so that engineers can make critical changes anywhere and anytime, reducing Mean Time To Restore (MTTR) and increasing employee satisfaction. The system requires at least one companion server
to be located in a data center to perform management and automation functions on the user’s behalf. The other component of course is the app itself, which connects to the companion server as needed.
My main initial criticisms of the app are that it requires a massive 23GB (you read that correctly!) of storage on your iPhone, and–due to the screen estate needs and the CPU required for the app to run at a reasonable speed–it is only recommended for use on the iPhone Continue reading
Skyport Systems and The Zero Trust DC
Skyport Systems offers a trusted computing platform to securely host virtual machines. Big deal? Well, maybe more than it seems at first glance.

I was sitting in some Juniper training last week being told about their Zero Trust security capabilities (referred to in VMWare NSX terminology as micro-segmentation
), and as I listened I started thinking about zero trust
in the wider context of who can be relied upon when it comes to software, and even the hardware on which it runs.
Software Issues
Let’s face it, the events of the the last few years have brought to light for Americans that far from a need to fear what other nation states might be willing to do to get access to our data, the real threat may lie within. Juniper was in the news at the end of last year after the announcement that ScreenOS contained unauthorized
code suspected of being planted there by the NSA. And then in January 2016, Juniper announced that ScreenOS would be dropping the NSA-developed Dual_EC_DRBG random number generator which perhaps coincidentally has a known weakness in it, a vulnerability that was made even worse by an implementation change in ScreenOS to use a larger Continue reading
Prophylactic Network Security

This week’s comedy gold was listening to a conversation emanating from a nearby inhabitant of our corporate cube accomodations, where one of my colleagues, Bob, was explaining to another coworker, George, the reasoning behind the decision to deploy firewalls to a particular new location.
Roughly summarized, the argument was this:
George, deploying a firewall is like having sex.
(No; I confess I had not anticipated ever typing that particular sentence, and I hope I never have to type it again.)
When you want to have sex, you decide whether you want a baby, and thus you choose whether or not to use contraception. If you don’t use contraception, while there’s no guarantee that a baby will arrive, there’s a real good chance that it will, so don’t be surprised if it does. Contraception isn’t perfect, but it at least reduces the likelihood of having a baby.
I confess I was laughing hard as I listened to the explanation because it’s an inspired analogy. However, buried somewhere in my subconscious was an Australian voice saying something like All these security products are a waste of money. It’s cheaper to save the money you would have spent, deal with a breach Continue reading
California Nurds by Katy Sperry

California Nurds
I know a place
Where the tech is truly awesome
Smart network folks; all clustered
inside CA’s borders
Cablin’ guys and gals
Running fibers to the servers.
We’re all hard core geeks, we are
certified nerf herders.
You may think you are sad,
But nothing comes close
To the silicon coast
Santa Clara’s just mad, you can’t
help your nerd lust
Oooooh Oh Oooooh
California nurds;
we are incredible!
Armed with Flukes,
we’re testing non stop.
Wi Fi smarts
so hot
we’ll melt your antenna
Oooooh Oh Oooooh
California nurds,
we like telemetry;
But we don’t
like SNMP.
West Coast time is lame
so we use UTC
Oooooh Oh Oooooh
We love unicorns, shooting
rainbows from their rear ends.
We’re Software Defined, running
everything in Python.
–John Herbert, with sincere apologies to Katy Perry
If you liked this post, please do click through to the source at California Nurds by Katy Sperry and give me a share/like. Thank you!
The Future is Bright! The Future is PoE?

There’s no avoiding the fact that the much-hyped Internet of Things
(IoT) is coming. Devices are popping up all over the place offering some form of wireless connectivity so that they can control (or be controlled) remotely, and if you want to run a Smart Building
, having control over all the elements of the environment could be a huge benefit. To that end, Cisco is playing with the idea that maybe we can offer power (via PoE), networking (Ethernet) and maybe even save a little money, by using Cat6 Ethernet cabling to connect those devices.
Current State of IoT
Not everything needs to be hard-wired, for sure. Some devices can be battery powered and may need to be placed in places where any wiring would be undesirable or impossible. Other devices though, may require more than battery power to operate, and that means running power to their location. If the device needs to send or receive a reasonable amount of data, it may also need to run 802.11 wireless, or have a wired connection; the common 802.15.4 Low-Rate Wireless Personal Area Network (LR-WPAN) solution utilized by many connected
devices may not provide enough bandwidth to be usable, and in Continue reading
Golang is GO GO GO!
You will have to be a programmer if you’re going to be a network engineer in the future,
they say. I don’t agree, but it surely helps you do your job. But what language should you learn? Perl? (no) Python? (maybe) Ruby? (perhaps) Every time I say something about learning Python, a little voice on Twitter says Or Go!
. Go? Go. And so, sucker that I am, I gave it a go (pun intended). TLDR: I think you should, too.
The Go Programming Language
The name Go feels like it should be a terrible word to search for on the Internet because it’s so short, but searches actually work remarkably well if you use Google Search. Compare the results of a search for “go if then else” from Bing and Google below; I’ll let you guess which is which:
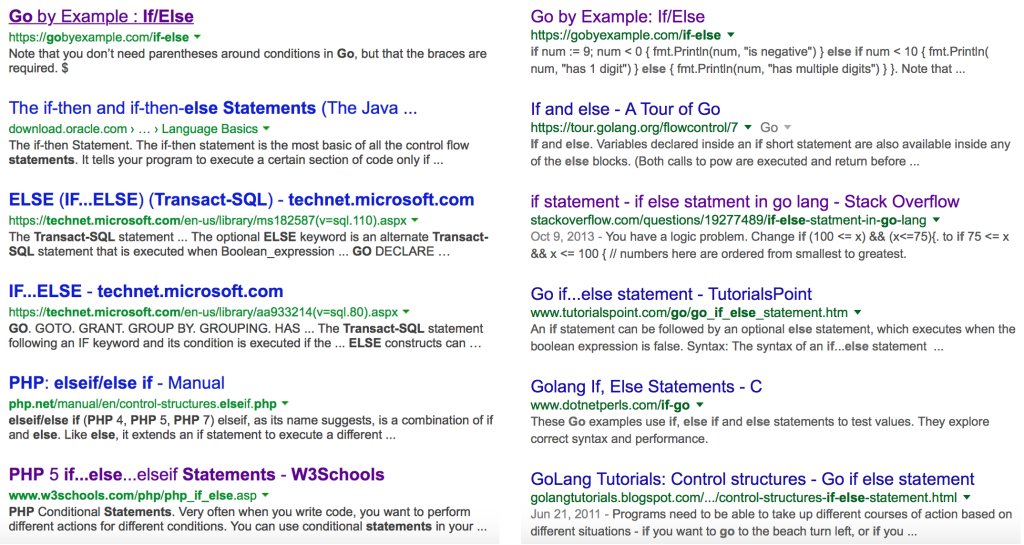
Maybe Google has learned from my search history. So, what’s important to know? Go is:
- Open source. The source code is readily available and can sometimes be helpful to figure out what’s going on.
- Free, obviously
- Pretty fast
- Multi-platform (Linux, OS X, Windows for starters)
- A compiled language
- Strongly typed
- Capable of Continue reading
Silver Peak Unity EdgeConnect SD WAN – Is It Any Good?

Ok, so Silver Peak offers yet another SD-WAN solution, you say? Well yes, but is it really possible to have too many options when it comes to broadband and hybrid WANs? I say no; the more choice we have, the more likely we can find the right solution for each situation and the more each vendor is encouraged to feature match with the others. With that in mind, let’s take a look at what Silver Peak offers and perhaps see how it is differentiated from the other solutions on the market.
What Is SD WAN?
Last year I wrote a brief definition of SD WAN as I see it, and for convenience I will reproduce that here as a reference point:
SD WAN is a solution that uses real time WAN link performance monitoring and data packet inspection to autonomously manage the distribution of network traffic across multiple, likely heterogenous, WAN links with the aim of improving and optimizing WAN performance in alignment with the business requirements.
My definition is intentionally vague about how such lofty goals should be accomplished, and that’s inevitably where the special sauce of each solution comes in.
Silver Peak WAN Optimization
Silver Peak sees two Continue reading
99 Problems and Configuration and Telemetry Ain’t Two

Isn’t SNMP just great? I love monitoring my network using an unreliable transport mechanism and an impenetrable and inconsistent data structure. Configuring my devices using automation is equally fun, where NETCONF has been subverted into something so ridiculously vendor-specific (and again, inconsistent), that each new device type (even from a single vendor) can mean starting again from scratch. Is there any hope for change? OpenConfig says yes.
Monitoring The Network
Love it or hate it (hate it), SNMP remains the de facto standard for alerting and monitoring. I think we cling on to SNMP as an industry because we’re scared that any replacement will end up being just as clunky, and we’d simple be putting expensive lipstick on a particularly ugly pig. If we want to get rid of SNMP, whatever comes next will need to bring significant benefits.
Configuring the Network
If you’re dedicated to making changes manually, it’s likely you don’t care much about the mechanisms currently available to automate configuration changes. However, I can assure you that writing scripts to make changes to network device configurations is a frustrating activity, especially in a multi-vendor environment. I should add that I consider automating CLI commands and screen-scraping the Continue reading
Riverbed Unleashes A Hungry “Project Tiger”

“The future of the WAN is NOT . . . a router.”
These bold words were spoken by Riverbed’s Josh Dobies in a presentation to the delegates at Networking Field Day 10 this August, as a lead in to the first public announcement of “Project Tiger.”
Anatomy of a Tiger
Riverbed explained that the SteelHead appliances perform WAN optimization in sites with highly contended bandwidth. The SteelFusion appliances offer both “hyperconverged infrastructure” and WAN optimization. For sites that have plenty of bandwidth, however, there’s no Riverbed product you can put there and that–for Riverbed at least–is a problem. Riverbed’s proposed solution? Ironically, it’s an appliance that can act as a WAN router, but with some rather unusual features.
Key Technical Takeaways
The headline features of Project Tiger as I see it, are:
- New SteelOS™ modular operating system (replacing RiOS)
- Containerization technology, used for the SteelOS modules
- Service-Chaining capability
- Riverbed SD-WAN features
- Zero Touch Provisioning (ZTP), with policy and configuration managed centrally in SteelCentral™
- BGP and OSPF to exchange routes with adjacent MPLS CE routers, for example.
Surprisingly absent from that list, however, is WAN Optimization. Despite being Riverbed’s core competency, this is not a feature of the Project Tiger appliance. Because Continue reading
PlantUML – Making Complicated Diagrams Simpler
A colleague at work recently told me that I should check out PlantUML. His advice is usually good, and this is no exception.
PlantUML uses a relatively simple text language to describe the desired diagram, then makes generation of the image as simple as processing the UML file. It’s easy to try online at http://plantuml.com/ where there is a text editor with real time image updates as you add more content.
Sequence Diagrams
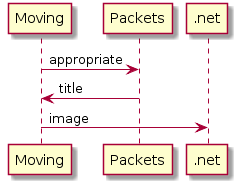
Sequence diagrams are probably the simplest to build, and are absurdly fast to create. Here’s a simple example of a TCP exchange:
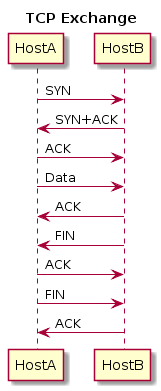 To create this, I used the following PlantUML:
To create this, I used the following PlantUML:
@startuml
title : TCP Exchange
HostA -> HostB : SYN
HostB -> HostA : SYN+ACK
HostA -> HostB : ACK
HostA -> HostB : Data
HostB -> HostA : ACK
HostB -> HostA : FIN
HostA -> HostB : ACK
HostA -> HostB : FIN
HostB -> HostA : ACK
@enduml
You’re not limited to two endpoints, of course:
Use Case Diagrams
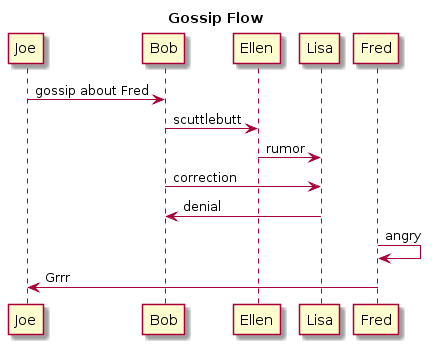
Here’s a simple use case with Fred and Joe again:
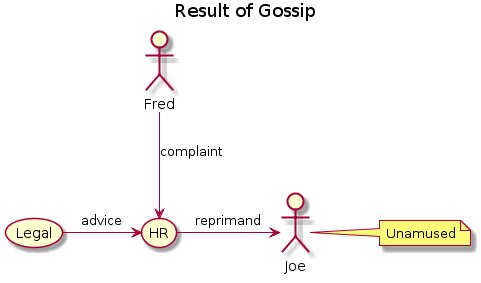 The PlantUML to generate this was:
The PlantUML to generate this was:
@startuml
title : Result of Gossip
Fred --> (HR) : complaint
(Legal) -> (HR) : advice
(HR) -> Continue readingSpeaking Geek at Solarwinds’ Thwack Community
Thwack!
For the new few months in addition to posting here, I’ll be making some blog posts over on Solarwinds‘ Thwack Community in their “Geek Speak” blogs, on the general topic of network management. I won’t be reposting the content here, but I’ll be sharing the links each time I post, and I hope you can find a moment to read them, rate the post if you are that way inclined, and maybe even comment! I know have some very smart readers, and Thwack has some smart users too, so the conversation should be great!
Solarwinds Thwack is a light-hearted community providing specific product support and templates for Solarwinds products, but also offering more general support on networking-related issues through blogs, community forums and product forums. It’s kind of a fun place to dig around, and the users are usually not short of an opinion on most topics. Signing up for an account is easy and free, and then you can post comments and join in the discussion!
Here’s the intro to the first post in the series, called “Do You Monitor Your Network Interfaces? at Geek Speak”
Hope to see you over there!
Disclosures
I am participating in the Solarwinds Continue reading
Operational Annoyances: Validating SSL VIPs

In the last two posts I described tools to validate the required intermediate SSL certificate chain for a given server certificate, and to validate that the private key and server certificate are a match. Once the SSL configuration is deployed though, how do we check that everything is working correctly and the new certificate is in place?
Checking deployed SSL Certificates and Intermediates
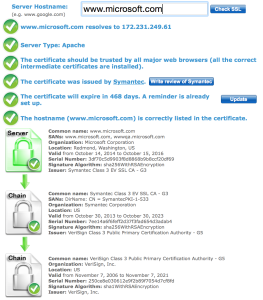
The simple answer is “use one of the tools already out there on the Internet.” That’s a fair answer, and I have been known to use some of these. A quick Google search shows a validator on SSLShopper:
There’s also a similar tool on DigiCert:
These are great tools and I strongly encourage using them to check your sites. However, there’s one situation where they can’t help you, and that’s when your site is only accessible internally. How do I do certificate validation for private sites?
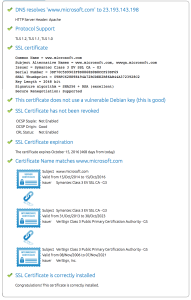
OpenSSL To The Rescue. Again
Yet again, OpenSSL is my tool of choice because not only can it open an SSL connection to a VIP, but it can also show the certificates it is sent. You may be thinking “Why not just use a web browser?” Again, Continue reading
Multi-datacenter Firewall Policy Automation
Back in that world where I reinvent the commercially available wheel, I’ve been wondering for a while about how to automate the creation of firewall policies in a multi-datacenter environment. This week I started tinkering with possible ways to achieve this, and knocked up some proof of concept code in my favorite untrendy, archaic language, Perl. Don’t say it.
The key issue is that given a firewall request (source IP, destination IP, port) it’s necessary to identify the firewalls and zones to which those rules apply, in order that rules can be automatically built in the right place(s). An additional twist I’ve seen is firewalls that have multiple routing instances, each of which maintains its own set of zones, effectively isolated from each other, even though they’re all on the same firewall.
Graphing Firewalls
I spent a while thinking about ways to model the firewall architecture, and kept on getting caught up on the firewalls with multiple routing instances. Because of the routing isolation, they behave like two separate firewalls, which makes it a little tricky to figure out the correct paths. I also wanted a solution that might also tell me which specific firewall zones were involved in the path; Continue reading
A Look Back at ONUG NYC 2015

I had a great time at the Open Networking Users Group meeting in NYC last month. Shortly afterward, I took a moment to think back on what I’d seen there, and that post was published on Gestalit.com. I won’t reproduce it here, so please take a moment to read my post at the source (gestaltit.com) and let me know what you think (here or there; either is fine). Topics covered include:
- Containerized microservices
- Software Defined WAN
- Cross-functional teams
- Adoption rates of new technologies
ONUG covered some cool stuff; I hope you enjoy the post.
Disclosure
My post at GestaltIT is a sponsored post as part of the ONUG Spring 2015 Tech Talk Series, part of the larger Tech Talks series.
If you liked this post, please do click through to the source at A Look Back at ONUG NYC 2015 and give me a share/like. Thank you!
Juniper EX4550. EX1113. EX063. What?

I came across some weird behavior (I think) in Junos recently. Nothing major, but an annoyance nonetheless.
Juniper EX4550
Let’s check out some statistics on this beautiful looking EX4550 stack, shall we?
john@EX4550> show pfe statistics bridge
Slot 0
PFE: 0
----------------------------------------
---- Ingress Counters ----
-- Set0 --
Received: 654383803
VLAN Filtered: 0
Security Filtered: 0
Other Discards: 324
-- Set1 --
Received: 654383797
VLAN Filtered: 0
Security Filtered: 0
Other Discards: 324
[...]
Oh dear look, 324 “Other” discards on my EX4550. I sure hope they aren’t incrementing. Let’s issue the command again and check if the 324 figure has increased?
{master:0}
john@EX4550> show pfe statistics bridge
Slot 0
PFE: 0
----------------------------------------
---- Ingress Counters ----
-- Set0 --
Received: 913272
VLAN Filtered: 0
Security Filtered: 0
Other Discards: 0
-- Set1 --
Received: 913267
VLAN Filtered: 0
Security Filtered: 0
Other Discards: 0
[...]
No it hasn’t. In fact it has mysteriously reset itself along with all the other PFE statistics. That is, well, suboptimal to say the least.

It’s probably a known bug, though it’s not important enough for me to go look it up. Maybe it’s even intentional (though for the life of Continue reading