Understanding the BGP Table Version – Part 2: Example
More on BGP Table Version – the most unknown and unexplained, BGP concept/value that I rarely ever troubleshoot without This is part 2 in the 3 part series of “Understanding the BGP Table Version”. If you haven’t already read part... Read More ›
The post Understanding the BGP Table Version – Part 2: Example appeared first on Networking with FISH.
Understanding BGP Table Version – Part 1: Intro to BGP Table Version
Diving into the BGP Table First a Look at the Local BGP Table Before we begin… let’s take a look at the BGP table. One would assume (rightly so) that anything called the “BGP table version” probably is tied somehow... Read More ›
The post Understanding BGP Table Version – Part 1: Intro to BGP Table Version appeared first on Networking with FISH.
Clearing Up Some Misinformation RE: eBGP Multihop and TTL
Myth: You have to set ttl to 2 because it is decremented on the way to the loopback.
**This blog is a formatting cleanup and update to a previous blog I posted in 2013 on NetworkWorld.
Years and years ago I was trying to learn more about BGP and I was reading some book with a chapter on the topic. Back then I pretty much believed that if it made it into a book it must be true and my knowledge had to be in error.  So to say I was confused back then would be an understatement.
So to say I was confused back then would be an understatement.
Why? Well ya see… they basically said that the reason one must set the TTL to 2 for eBGP peers that are directly connected, but peering with their loopbacks, was cause “the TTL gets decremented on the way to the loopback”
When I try to help someone deprogram this brain washing, I find pictures help. So for those who’d like to get deprogrammed and learn the truth… Let’s go play in the lab!!!
In the picture above we have 3 Routers in 3 different BGP ASes. We all probably know that if we peer R1 and R2 Continue reading
Pop Up Tech Talks: Denise Fishburne
Earlier today I saw a tweet that @PopUpTechTalks had uploaded their interview of me up to their YouTube Channel. I was super stoked!  Just had to share it with y’all!
Just had to share it with y’all!
SolidFire’s Amy Lewis speaks with Cisco’s Denise Fishburne aka Fish about embracing your inner network detective at Cisco Live 2015. Filmed June, 2015 in San Diego.
Click on the pic below to see watch the interview.
“Understanding IPv6” – 7 Part IPv6 Network Computing Series
Newer to IPv6? Know it some but just want to go a little bit deeper? I realized I never put up here on my web site my 7 part … labor of love…. IPv6 blog series I did over on Network Computing. 
Understanding IPv6: The Journey Begins
Why is IPv6 so difficult to understand? Fish explains how she began unraveling this complex topic.
Understanding IPv6: Link-Local ‘Magic’
Fish performs a little IPv6 sleight of hand in the second post in her series on IPv6.
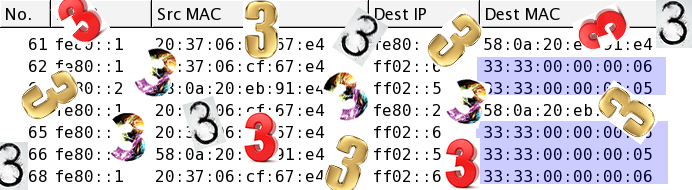
Understanding IPv6: A Sniffer Full Of 3s
Fish explores Wireshark sniffer traces in order to understand the difference between IPv4 and IPv6 addressing.
Understanding IPv6: What Is Solicited-Node Multicast?
Fish lays down the basics of solicited-node multicast, which provides the functionality for Neighbor Discovery in IPv6 addressing.
Understanding IPv6: Prepping For Solicited-Node Multicast
Before jumping into solicited-node multicast, a review of link-local scope multicast addresses is helpful.
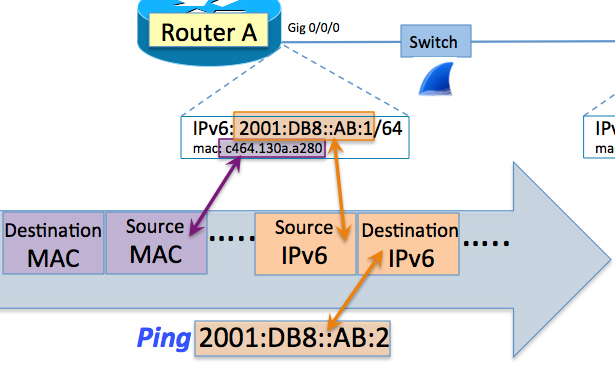
Understanding IPv6: The Ping Before Solicited-Node Multicast
Fish gets ready to walk through solicited-node multicast, analyzing an ICMP ping echo request in IPv4 and showing how it differs from IPv6.
Understanding IPv6: Solicited-Node Multicast In Action
In the Continue reading
IWAN: Why EIGRP or BGP Over the DMVPN Tunnel?
IWAN (Intelligent Wide Area Network) and Why EIGRP or BGP over the DMVPN Tunnel.
In this YouTube “playing in the lab” IWAN fun we are going to drill down between 2 sites – Branch 3 and the Hub site. Branch 3 will be in “hybrid” mode (1 MPLS link and 1 Internet Link) – in the past using the MPLS link as a primary and the internet link as backup only. Now, however, taking advantage of IWAN’s Intelligent Path Control.
We will design the implementation such that should we need to fall back from Intelligent Path Control to normal routing… we fallback to what is (for many customers’) today’s norm in this situation – MPLS as the Primary and Internet as the backup. For this to happen….there will only be 1 entry in the RIB (via the MPLS) How, then you ask, would you ever send any traffic at all out of the Internet link (tunnel 20) if that path is not in the routing table? 
PfRv3 can read the EIGRP topo table and the BGP table…. we can still do intelligent decision making at the WAN edge and only send out the Internet path Continue reading
Fun in the Lab: Troubleshooting DMVPN Per-Tunnel QoS
In Playing in the Lab: DMVPN and Per-Tunnel QoS we looked at DMVPN per-tunnel QoS. We looked at how to configure it…. how the vendor private extensions in RFC2332 are used in the NHRP registration request… and how to see,... Read More ›
The post Fun in the Lab: Troubleshooting DMVPN Per-Tunnel QoS appeared first on Networking with FISH.
Glass Half Empty or Half Full?
Look at that middle glass in the picture to the left. Do you view that middle glass as 1/2 empty or 1/2 full?
Intelligent Bandwidth Decisions at the WAN Edge
Business Critical Applications and Intelligent Decision Making at the WAN Edge….. these are the things I’ve been focusing on in the past few blogs. To me, PfRv3 and DMVPN are the dynamic duo of Cisco’s IWAN that help you learn about and avoid impairments (delay, loss, jitter) along the path that business critical traffic takes.
Let’s take this even further though. How else can IWAN’s Intelligent Path Control help us apply the mentality of the 7Ps (“Prior proper preparation prevents piss poor performance”) to our network and to business critical traffic?
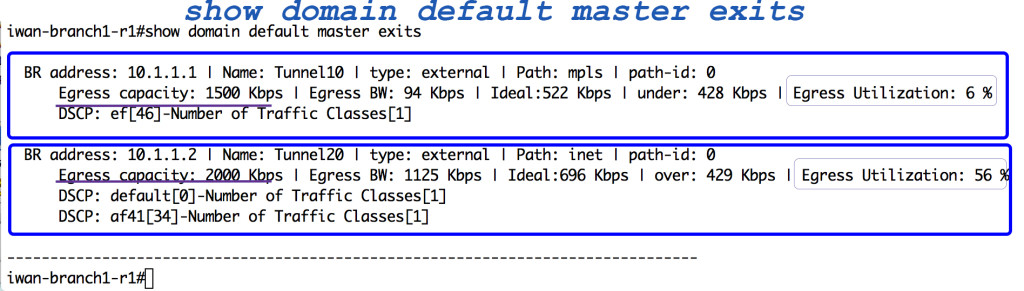
Knowledge… information gathering… awareness. These are the first steps. Once you have the knowledge you can make intelligent decisions based on that knowledge at the WAN edge.
What knowledge?  How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
How about the bandwidth of your WAN links? Wouldn’t it be nice to have facts, such as what their current bandwidth utilization is, be a part of the Intelligent decision making at the WAN edge?
We can do that for you now. We can use what your current egress utilization is on your WAN links in the intelligent decision making process that PfRv3 does for you at Continue reading
Business Critical Apps & the DMVPN Underlay of IWAN’s Intelligent Path Control
Let’s assume we have a Branch with 1 Router and 2 WAN connections. We decide to use Intelligent Path Control with PfRv3 and design our policy such that the business critical traffic goes over one of the WAN clouds (MPLS, for example) and will use the other WAN cloud (Internet, for example) should a certain level of impairment (delay, loss, jitter) occur on the primary path.
But that business critical traffic is well….. critical to your business. So that probably isn’t really good enough. Let’s take this a couple steps further to make sure your business critical traffic is treated as such.
With Intelligent Path Control with PfRv3 what will actually happen is that while the business critical traffic is going over the primary channel, a backup channel will be created over the other WAN cloud. On top of that, PfRv3 will be checking the health of the path the backup channel is taking. Actually… let me be even more specific. PfRv3 will be checking the health of the exact path that business critical traffic would take if it were to be sent over the fallback WAN cloud.
“How is this accomplished?
Regardless of hashing algorithms Continue reading
Which Path in the WAN are those Business Critical Applications Taking?
“Learning about and avoiding impairments (delay, loss, jitter) along the path that business critical traffic takes.” That is what I wrote in my previous blog “IWAN’s Intelligent Path Control & Using Your Backup Link.” But how is that possible to do?
Thinking some type of probe? From where to where? Thinking the WAN edge links? But how do you know the path you send your probes over is the path that your business critical traffic is taking?
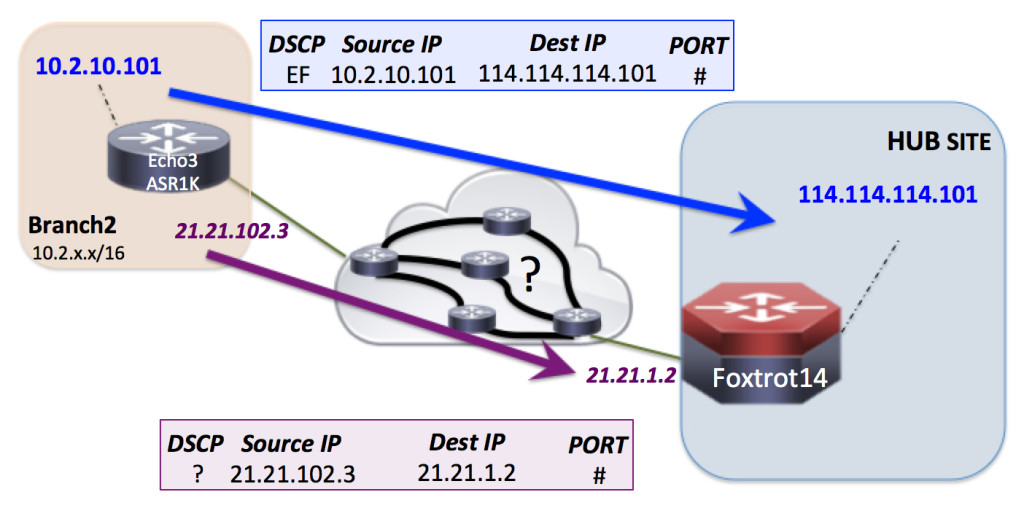
Let’s talk about what I mean by this by looking at an example.
In the above picture we have 2 sites with 1 host per site, and 1 WAN connection between the two.
- Branch2 w/ host 10.2.10.101
- Hub Site w/ host 114.114.114.101
- WAN connection w/ 21.21.102.3 on the Branch2 side and 21.21.1.2 on the Hub Site side.
Let’s say you check the health of the path between Branch2 and the Hub Site with some type of probe/IP SLA. You will be doing it from the 2 WAN IP addresses 21.21.102.3 and 21.21.1.2. Right? Continue reading
IWAN’s “Intelligent Path Control” & Using Your Backup Link
The blog I was going to post today was a blog about how PfRv3 (IWAN’s “Intelligent Path Control”) utilizes the GRE tunnel of the DMVPN underlay in order to make intelligent decisions about where to send business critical traffic based on knowledge of the health of the path that business critical traffic would take. …… But then I started realizing that while I have dug into a lot of DMVPN stuff recently on “Networking With Fish”…. I have not even really touched “Intelligent Path Control”. So……. let’s take a giant step backward.
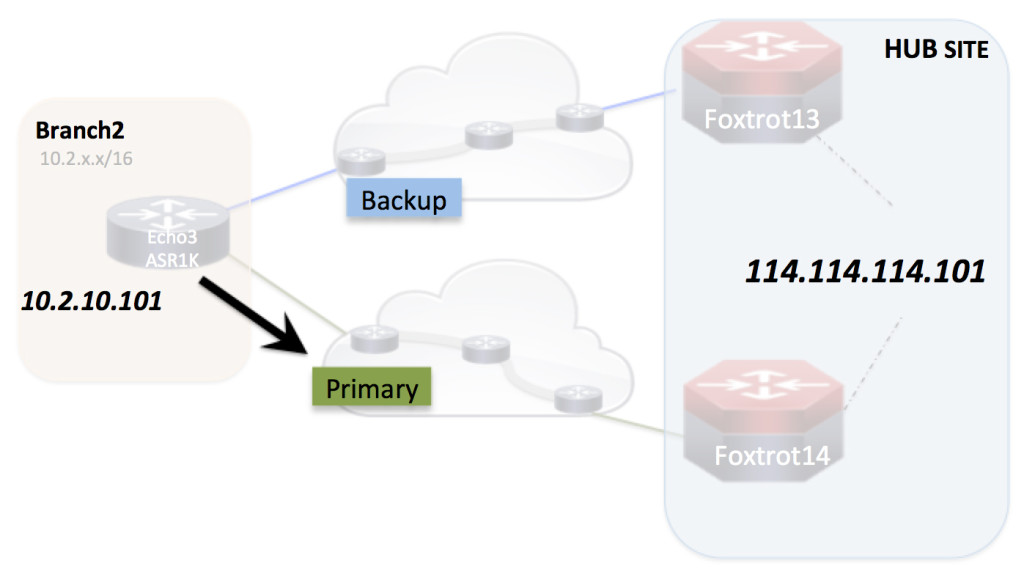
“Intelligent Path Control” at the WAN – what can it do for you and why do you want it? In this blog I’m not going to try to be the definitive all encompassing guide of what all “Intelligent Path Control” is…. just enough to get us a little on the same page before we start “playing in the lab together” with it in future blogs.
The picture above is of a typical 1 router branch location with 2 WAN connections. One WAN connection is the primary and the other one sits there, unused, as just a backup … doing nothing Continue reading
Playing in the Lab: LiveAction Administrative Fun
I’m newer to LiveAction but what I have seen thus far I have definitely liked. But admittedly with GUIs I sometimes still feel like a “CLI girl living in a GUI world”.
During the past week I was noticing that when I was in my Live Action client view… looking at the “dashboard” I would suddenly find myself back at the main LiveAction client view. I asked a co-worker name Robert if he had ever seen that before. He had not. So I showed it to him. He noticed something I had not. There seemed to be a “trigger event” that was associated with the changing screens.
…. Hope you have fun with the video and playing in the lab with me. 
Click on the diagram below to go play. 
Approx time: 16 Minutes
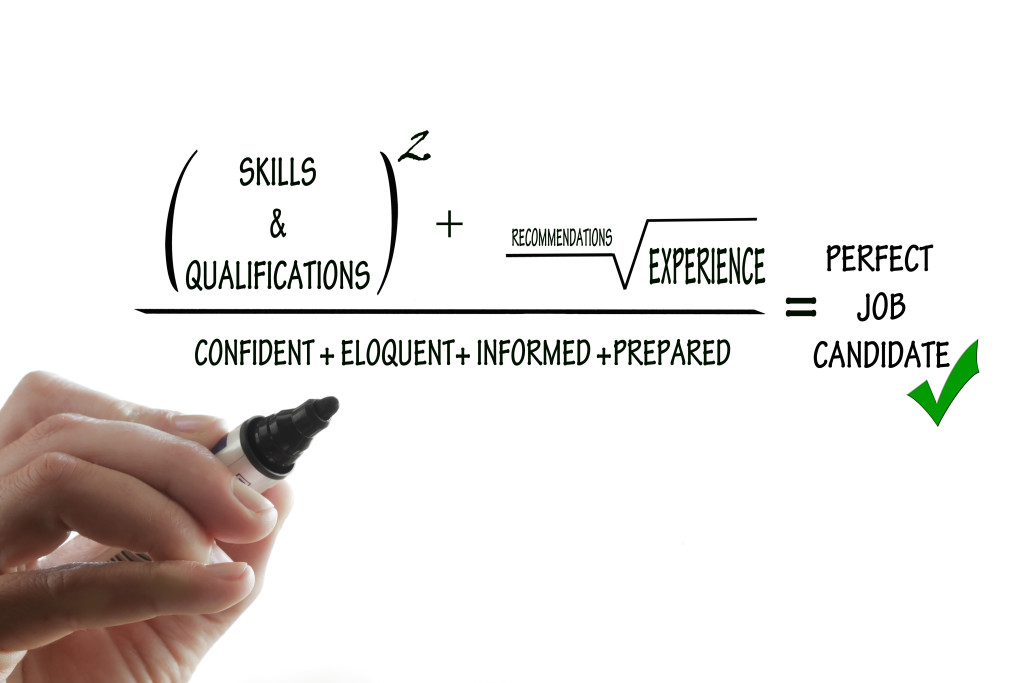
Interviewing for the “Ideal Candidate”: Looking for “Nerdvana” – New Packet Pushers Blog
I was going through a stock photo website the other day and came across a “formula” that was supposed to equal the “perfect job candidate”. I chuckled a little out loud. The person sitting next to me looked over at what was on my laptop screen. Paused. Then asked me what I look for when I’m interviewing someone. What is my “perfect job candidate?”
…. For the rest please go to Packet Pushers
http://packetpushers.net/interviewing-for-the-ideal-candidate-looking-for-nerdvana/
1 Year Anniversary for Networking With Fish
It seems like just yesterday I was at CiscoLive in San Francisco asking people I had met on twitter about their experiences blogging as well as hosting a web page. Today? Last week marked the 1 year anniversary of “Networking With Fish”.
I want to say thank you.
Those of you who know me, know that I’m not much on the idea of one person’s success being solely on them. That can be a philosophical debate for some other day. But suffice it to say I had nothing to do with the IQ or EQ I was born with. Also while I was studying for my certifications…. I was reading documents and books that other people wrote.
So too with success of Networking With Fish.
So please indulge me for one moment on this 1 year Anniversary to say “thank you” to all those who were instrumental in the success of this web site. Your mug is in the mail. 
Russ White – Much starts with Russ. My CiscoLive career started because he asked me to be a speaker for CiscoLive 2006. My becoming a CiscoLive Session Group Manager is because he Continue reading
YouTube: A Little IWAN Fun in the Lab
In this YouTube “playing in the lab” IWAN fun we are going to have 2 phones (one in Branch 1 and one in Branch 3) doing a voice/video call. We will use LiveAction to see that the video call between the 2 branches is actually going directly spoke-to-spoke despite the fact that they are on an mGRE tunnel with a DMVPN hub in the Hub Site. We will confirm what LiveAction is seeing via command line on Branch1 Router 1 and see the NHRP shortcuts that this router has to go directly to the Router 3’s direct IP address that it uses to connect to the MPLS cloud.
We will then ask what might happen if a brownout impairment were to occur on the Branch1_Router1 link with the MPLS PE. For example – 2% loss. We will look at a little of the PfRv3 configs up on the domain master controller as well as Branch1_Router1’s master policy that it received from the domain master controller. Then we will cause impairment (2% loss) to the MPLS link… during which I have a video recording of the phone call… where … pretty much… the move over from the primary Continue reading
IPv6: Yet Another Post Trying to Urge You to Start TODAY
“Okay, who wants to learn IPv6 and be the IPv6 person for CPOC?” This was the question asked by our manager to our team back in 2002 when we heard “IPv6 is COMING – GET READY NOW!” My hand went up almost without me even realizing it. No other hands went up. Not one. So, by default, it was me. I was pumped with excitement! After the meeting I immediately went online and ordered about 8 IPv6 books. (For those of you who know me… this will not be a shock) 
Then what happened? Was 2003 the “year that CPOC got SLAMMED with IPv6 requests”? Uh…. no. Was 2004? ….. No. Don’t get me wrong. People came in with IPv6 in the test plan. But typically IPv6 was on the list of things to test more as a “checklist” test just to make sure the boxes could do IPv6.
In ~2006 I started believing that this “IPv4 exhaustion scare” wasn’t “real”. NAT would take care of everything. If it was “really” that much of a big deal …… people would be doing something serious about it. Continue reading
Playing in the Lab: DMVPN and Per-Tunnel QoS
There is this really cool thing about DMVPN that I came across a while back: DMVPN Per-Tunnel QoS. Apparently it isn’t just me (as a lab rat) that thinks this is cool. Every time I show this to people I... Read More ›
The post Playing in the Lab: DMVPN and Per-Tunnel QoS appeared first on Networking with FISH.
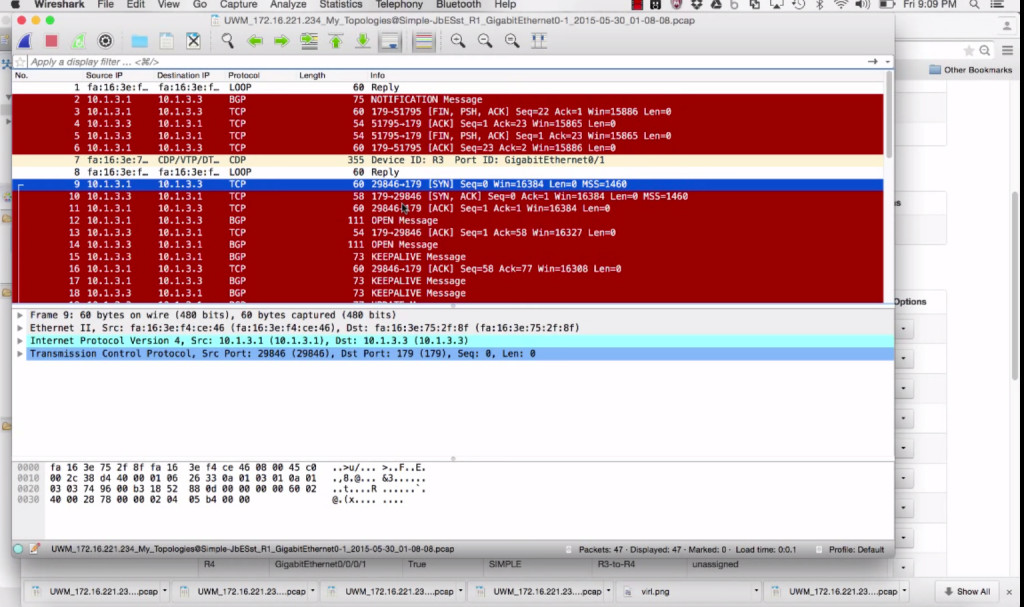
YouTube: Packet Capturing with VIRL
Tried VIRL when it first came out. “Why?”, you ask, when you know I work in a Cisco Customer Proof of Concept lab with lots of “real” networking hardware? Answer is because it would be nice to be able to toss together networks to play with… without having to reserve gear, load line cards that are on shelves into empty chassis, cable, code, config… etc etc.
But there was, for me, a major item missing from VIRL when it first came out — the ability to packet capture easily. For what I wanted VIRL for, that was a showstopper for me. So, back into the lab for my “playing” and teaching.
Now?  Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.
Very very happy to pass on to you that VIRL supports packet capturing now!!! Tossed together a quick ~12minute youtube.
Fun in the Lab: Sniffer Tracing a DMVPN Tunnel Startup
I have seen that for many people new to DMVPN… it seems quite overwhelming and scary. I will admit it was that way for me also. I think really cause of all those nhrp commands. Funny thing about those nhrp is that these items... Read More ›
The post Fun in the Lab: Sniffer Tracing a DMVPN Tunnel Startup appeared first on Networking with FISH.