Why I Enthusiastically Switched from Cacti to Zabbix for System Monitoring
Cacti is a “complete network graphing solution” according to their website. It has also been a thorn in my side for a long time.
See what I did there? Thorn… because it’s a cactus… never mind.
When Cacti is in a steady state–when I could get it to a steady state–it was good. Not great, because there was a lot of effort to get it into what I consider “steady state”, but good. The rest of the time… thorny.
There are five major things that have driven me up the wall. In no particular order:
Round Robin Database (RRD) sucks
The concept behind RRD is cool: a fixed-size, circular database (oldest data overwritten by the newest data) makes good sense for the type of data that a network graphing solution collects. In practice, using RRD means:
- Another software dependency that needs to be updated, patched, and integrated in the Cacti ecosystem
- Manually managing all of the RRD files that are generated for all of the data sources you’re collecting. RRD stores its data in individual files on the file system, you see, and the more data sources you collect with Cacti, the more RRD files you have Continue reading
Why I Enthusiastically Switched from Cacti to Zabbix for System Monitoring
Cacti is a “complete network graphing solution” according to their website. It has also been a thorn in my side for a long time.
See what I did there? Thorn… because it's a cactus… never mind.
When Cacti is in a steady state-when I could get it to a steady state-it was good. Not great, because there was a lot of effort to get it into what I consider “steady state”, but good. The rest of the time… thorny.
There are five major things that have driven me up the wall. In no particular order:
How I Relearned the Consequences of Improper Monitoring
I had just lost the RAID array that hosts my ESXi data store. I didn’t yet know that’s what had happened, but with some investigation, some embarrassment, and a bit of swearing, I would find out that an oversight on my part three years ago would lead to this happening.
I first realized there was trouble when every VM on the host became unresponsive. Most notably, the Plex Media Server fell off the network which caused the episode of Modern Family that we were watching to immediately freeze. What was odd to me is that while the VMs were unreachable, the ESXi host itself was fine. I could ping it, ssh to it and load it up with the vSphere client. The first wave of panic hit me when I found messages like this in the host’s event log:

This was quickly confirmed from the ssh shell by looking for the data store and finding that a) the symlink for the volume (RAID1) pointed to a non-existent directory and b) the reported size of the volume was a paltry 450MB compared to the 930GB I expected.

Since I knew from prior experience Continue reading
How I Relearned the Consequences of Improper Monitoring
I had just lost the RAID array that hosts my ESXi data store. I didn't yet know that's what had happened, but with some investigation, some embarrassment, and a bit of swearing, I would find out that an oversight on my part three years ago would lead to this happening.
Big Changes in 2017
This past June when I was in North Carolina at Cisco’s CPOC lab, I learned that there was a chance–albeit a slim one, but a chance nonetheless–that a position would be opening up on the CPOC team in the fall. By that point I had been to CPOC three times and knew many of the engineers who worked there. I spoke to them to get their feedback, met with the newly-hired manager of the team, and just generally did all the things I thought I should be doing to take advantage of my time being face to face with these folks.
Then I flew home, subscribed to the “new jobs at Cisco mailing list” and waited.
And then, one day, it was posted: CPOC Technical Projects Systems Engineer. I immediately sent a message to my wife who responded as only she knows how:

Five short interviews later I was offered the job!
This brings me to change #1: As of this month (January), I am no longer a Systems Engineer with Cisco Systems Canada. I am now a Systems Engineer on the CPOC team reporting to a manager in the US.
Beyond the basic level of Continue reading
Big Changes in 2017
This past June when I was in North Carolina at Cisco's CPOC lab, I learned that there was a chance-albeit a slim one, but a chance nonetheless-that a position would be opening up on the CPOC team in the fall. By that point I had been to CPOC three times and knew many of the engineers who worked there. I spoke to them to get their feedback, met with the newly-hired manager of the team, and just generally did all the things I thought I should be doing to take advantage of my time being face to face with these folks.My Personal Look Back on 2016
I haven’t ever written a “year in review” type of post before. Sure, I do a post to summarize how the blog has done over the year but I’ve never done a personal look back. Last night–New Years Eve–I was thinking about everything that I was involved in during 2016 and I realized “I should write this down! I was involved in or a participant of some amazing things last year!”
So here we go. In an effort to show a more personal side and not just my geeky side, here is my personal 2016 year in review.
Got Married
In February, my then-girlfriend and I got married! I know everyone says their wedding was the best, but ours totally was! Trust me!  In all honesty, it was one of the funnest days of my life. Full credit to my wife for planning what was essentially an awesome party with our families and closest friends. Oh, and the venue and staff were absolutely amazing as well which sealed the deal as the greatest wedding ever
In all honesty, it was one of the funnest days of my life. Full credit to my wife for planning what was essentially an awesome party with our families and closest friends. Oh, and the venue and staff were absolutely amazing as well which sealed the deal as the greatest wedding ever  .
.
Launched a Second Blog

For a while now I’ve been in the habit of snapping photos of wireless access points Continue reading
My Personal Look Back on 2016
I haven't ever written a “year in review” type of post before. Sure, I do a post to summarize how the blog has done over the year but I've never done a personal look back. Last night-New Years Eve-I was thinking about everything that I was involved in during 2016 and I realized “I should write this down! I was involved in or a participant of some amazing things last year!”
So here we go. In an effort to show a more personal side and not just my geeky side, here is my personal 2016 year in review.
2016 End of Year Blog Statistics
Happy New Year! I just realized the other day that this blog turned 5 years old in 2016. It’s been a lot of fun and has paid me back for my time in terms of building my brand and being a means to explore and learn new topics. I have plans to put more focus on my writing in 2017 and reduce the friction between starting with a blank page and hitting that “Publish” button.
Anyways! Here’s a look back at 2016 on packetmischief.ca.

Hmm. Basically flat growth in terms of views and visitors. I feel like this is to be expected based on how much writing and promotion I did throughout the year. I can improve these numbers for 2017.
Just like last year, the new vs returning visitor numbers are basically unchanged.

The 5 most popular posts in 2016 are:

Quick links:
- 4 Types of Port Channels and When They’re Used
- Resetting Admin Password on a Cisco ISE Appliance
- What the Fex is a FEX Anyways
- Five Functional Facts about FabricPath
- Airplay, VLANs, and an Open Source Solution
And the top 5 posts in 2016 that Continue reading
2016 End of Year Blog Statistics
Happy New Year! I just realized the other day that this blog turned 5 years old in 2016. It's been a lot of fun and has paid me back for my time in terms of building my brand and being a means to explore and learn new topics. I have plans to put more focus on my writing in 2017 and reduce the friction between starting with a blank page and hitting that “Publish” button.
Anyways! Here's a look back at 2016 on packetmischief.ca.
OpenBSD on the Sixth Generation Intel NUC

I recently decided it would be fun to upgrade the hardware on my main OpenBSD machine at home (because, you know, geek). These Intel NUC machines are pretty interesting. They are pretty powerful, support a decent amount of RAM, certain models support internal storage, and they are very low power and low noise. Perfect for a machine that is a shell/email/development box.
The model I chose is the NUC6i3SYH.
- Core i3 processor (because my machine is not at all CPU bound)
- Very low power consumption (15W)
- Supports a 2.5″ SSD
OpenBSD 6.0 boots with the GENERIC kernel; no tuning or tweaking required. Full dmesg is at the end of this post. Hightlights of the hardware include:
- Wired network: Intel I219-V using the
em(4)driver - Wireless network: Intel Dual Band Wireless AC 8260 using the
iwm(4)driver (no support for 802.11ac in OpenBSD at the time of this writing so it’s 802.11n only) - Dual-core CPU with hyperthreading (be sure to boot GENERIC.MP)
The kernel recognizes the Intel SpeedStep capabilities of the CPU and will adjust the CPU’s clock speed as needed (further keeping the power consumption of the machine at a very Continue reading
OpenBSD on the Sixth Generation Intel NUC

Sixth Generation Intel NUC
I recently decided it would be fun to upgrade the hardware on my main OpenBSD machine at home (because, you know, geek). These Intel NUC machines are pretty interesting. They are pretty powerful, support a decent amount of RAM, certain models support internal storage, and they are very low power and low noise. Perfect for a machine that is a shell/email/development box.
L3 vPC Support on Nexus 5k
So… I’m a little embarrased to admit this but I only very recently found out that there are significant differences in how Virtual Port Channels (vPC) behave on the Nexus 5k vs the Nexus 7k when it comes to forming routing adjacencies over the vPC.

I’ve read the vPC Best Practice whitepaper and have often referred
others to it and also referred back to it myself from time to time. What I failed to realize is that I should’ve been taking the title of this paper more literally: it is 100% specific to the Nexus 7k. The behaviors the paper describes, particularly around the data plane loop prevention protections for packets crossing the vPC peer-link, are specific to the n7k and are not necessarily repeated on the n5k.
To that end, there are some topologies for Layer 3 peering over a vPC which are not supported on the n7k but are supported on the n5k. For example, peering a third-party Layer 3 device to the SVIs on the two n5ks in the vPC is supported.

The third-party device has an IP address on its port-channel interface and forms an Layer 3 adjacency/neighborship with Continue reading
L3 vPC Support on Nexus 5k
So… I'm a little embarrased to admit this but I only very recently found out that there are significant differences in how Virtual Port Channels (vPC) behave on the Nexus 5k vs the Nexus 7k when it comes to forming routing adjacencies over the vPC.
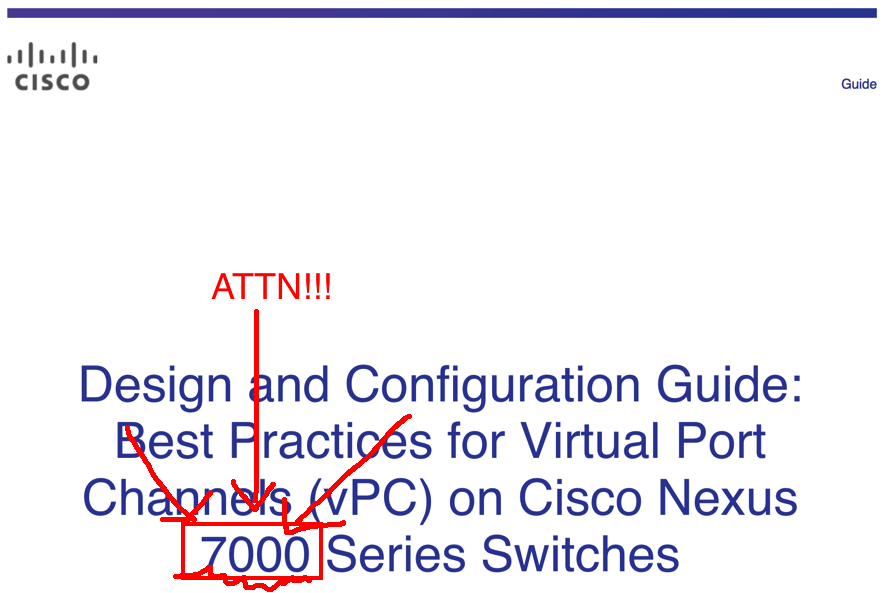
Take the title literally!
I've read the vPC Best Practice whitepaper and have often referred
others to it and also referred back to it myself from time to time. What I failed to realize is that I should've been taking the title of this paper more literally: it is 100% specific to the Nexus 7k. The behaviors the paper describes, particularly around the data plane loop prevention protections for packets crossing the vPC peer-link, are specific to the n7k and are not necessarily repeated on the n5k.
So Your Username and Password Where in a Data Dump. Now What?
Whether it’s Dropbox, LinkedIn, MySpace, PlayStation, or whatever the latest breach happens to be, it’s almost inevitable that you will be caught up in one of these breaches and have your username, password and possibly other information exposed in a data dump. Here’s how to respond when that happens.
How Does This Happen?
A data dump is what often happens after a website has been breached and information about that site’s users/customers is stolen. All that stolen data is often “dumped” on the Internet for all to see. Once the data is dumped, it’s at that point that all this information becomes public and along with it, your information.
Sometimes, as in the case of the Ashely Madison dump, that information can be personally damaging. Other times the information is limited to usernames and passwords.
This article is going to focus on how to respond if your username and password are part of a data dump.
Step 1 – Reset Your Password
This is obvious, but go and change your password. Do it right now, before something comes along and distracts you. Even if you’re a security concious person and you’re using Two-Factor Authentication Continue reading
So Your Username and Password Where in a Data Dump. Now What?
Whether it's Dropbox, LinkedIn, MySpace, PlayStation, or whatever the latest breach happens to be, it's almost inevitable that you will be caught up in one of these breaches and have your username, password and possibly other information exposed in a data dump. Here's how to respond when that happens.
SSH Agent on OS X
There’s a lot of information on the intertoobs about getting ssh-agent “working” in OS X and even more articles about when and how the stock behavior of ssh-agent changed (mostly with respect to how ssh-agent interacted with the Keychain).
This article doesn’t cover or care about any of that.
This article is concerned with:
- Enabling ssh-agent in such a way that I can “ssh-add” in one terminal window and that same agent (and the loaded keys) is available in all of my other terminal windows.
- Enabling use of ssh-agent from MacPorts and/or Homebrew and not the older ssh-agent that OS X ships with in /usr/bin.
- To avoid having to put my keys in the Keychain (just a matter of preference).
Compatibility
Beware, reader. There’s an awful lot of outdated, inaccurate information out there on how to modify ssh-agent behavior on OS X. Guess what? OS X changes from version to version! Many articles out there cater to older versions of the OS and are either no longer applicable (due to changes in OS X behavior) or plain don’t work (due to functional changes in the software).
The steps below have been tested with OS X El Capitan (10.11).
What’s Continue reading
SSH Agent on OS X
There's a lot of information on the intertoobs about getting ssh-agent “working” in OS X and even more articles about when and how the stock behavior of ssh-agent changed (mostly with respect to how ssh-agent interacted with the Keychain).
This article doesn't cover or care about any of that.
This article is concerned with:
- Enabling ssh-agent in such a way that I can “ssh-add” in one terminal window and that same agent (and the loaded keys) is available in all of my other terminal windows.
- Enabling use of ssh-agent from MacPorts and/or Homebrew and not the older ssh-agent that OS X ships with in /usr/bin.
- To avoid having to put my keys in the Keychain (just a matter of preference).
Cisco DevNet Scavenger Hunt at GSX 17
At Cisco’s GSX conference at the start of FY17, the DevNet team made a programming scavenger hunt by posting daily challenges that required using things like containers, Cisco Shipped, Python, and RESTful APIs in Cisco software in order to solve puzzles. In order to submit an answer, the team created an API that contestants had to use (in effect creating another challenge that contestants had to solve).
This post contains the artifacts I created while solving some of the challenges.
Tools Used
- Postman
- Browser (for reading docs and such)
- Python 2.7 (for Challenge 2)
Challenge 2: UCS Manager API
Your customer has been asked by their Help Desk Manager to make it easier on his first line engineers when requests come in related to UCS Server problems. Today, they have to train engineers on UCS Manager to get details like blade status, firmware levels, and uptime. He is asking how they could embed those details in their help desk system. Create some sample code leveraging the Python SDK for UCS Manager.
- There is a Service Profile with a dn of
org-root/ls-gsx-minihack1. Find itsint_id.
Answer
Challenge 5: ACI REST API
Congratulations! Your customer has selected ACI Continue reading
Cisco DevNet Scavenger Hunt at GSX 17
At Cisco's GSX conference at the start of FY17, the DevNet team made a programming scavenger hunt by posting daily challenges that required using things like containers, Cisco Shipped, Python, and RESTful APIs in Cisco software in order to solve puzzles. In order to submit an answer, the team created an API that contestants had to use (in effect creating another challenge that contestants had to solve).
This post contains the artifacts I created while solving some of the challenges.