Day Two Cloud 010: The Role Of Egress Control In Cloud Security
Today's Day Two Cloud episode dives into egress control for cloud security. Guest David Redekop explains why outbound control is essential to protect cloud services, how to use DNS to restrict outbound connections, and the value of logging tools such as OSquery.
The post Day Two Cloud 010: The Role Of Egress Control In Cloud Security appeared first on Packet Pushers.
Docker Security Bug Latest to Hit the Container Space
 The latest flaw allows a witty attacker to target API endpoints behind the docker cp command that...
The latest flaw allows a witty attacker to target API endpoints behind the docker cp command that...
Huawei Revs Up Battle With US Government
 It’s unclear what impact, if any, the outcome of the legal challenge will have on Huawei's...
It’s unclear what impact, if any, the outcome of the legal challenge will have on Huawei's...
Marvell Doubles Down on 5G, Data Center Silicon, Sells WiFi Chip Business to NXP
![]() The acquisition includes Marvell’s WiFi and Bluetooth technology portfolios and related assets,...
The acquisition includes Marvell’s WiFi and Bluetooth technology portfolios and related assets,...
History of the Internet: An Asian Perspective
Fun fact from this episode of the History of Networking: because of export rules, students in South Korea had to rebuild the TCP/IP stack for the PDP11 and other hosts in order to bring the first IP link up in southeastern Asia. In this recording, Donald and I are joined by Kilnam Chon.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
Palo Alto Networks Launches Prisma Cloud Security as Twistlock Acquisition Rumors Swirl
 The vendor has reportedly reached deals to buy container security startup Twistlock for between...
The vendor has reportedly reached deals to buy container security startup Twistlock for between...
Subscription Licensing, The 5g Time Machine & The Trough Of Disillusionment
In this episode we take a look at the gradual shift to subscription based licensing, how 5g could potentially set back weather radar 30+ years, and a conversation about the hype cycle in networking.
Outro Music:
Danger Storm Kevin MacLeod (incompetech.com)
Licensed under Creative Commons: By Attribution 3.0 License
http://creativecommons.org/licenses/by/3.0/
The post Subscription Licensing, The 5g Time Machine & The Trough Of Disillusionment appeared first on Network Collective.
Finding Common Ground on U.S. Net Neutrality

After more than a decade of regulatory ping pong, net neutrality’s future in the United States is still unclear.
Since 2004, FCC rulemakings have been caught in a vicious cycle. They have been passed, fought in court, and returned to the FCC with minor (and sometimes major) revisions. In the last few years there have also been numerous attempts to pass legislation, cementing net neutrality once and for all, but nothing has succeeded in Congress.
Recognizing the importance of finding a sustainable solution, the Internet Society proposed a collaborative process to help experts find common ground on this complex policy issue. Starting in June 2018, we convened an ideologically diverse group of experts to create a baseline set of principles for an open Internet.
The Net Neutrality Experts’ Roundtable series included representatives from the technical community, edge providers, academia, Internet service providers, industry associations, and both left- and right-leaning civil society groups.
In a series of meetings over ten months, participants discussed how to create a sustainable solution for net neutrality that protect the interests of Internet users while fostering an environment that encourages investment and innovation.
Ultimately, the group was able to create a consensus-driven set of bipartisan principles for an open Continue reading
IPv6 Support in Microsoft Azure
TL&DR: MIA
Six years ago, when I was talking about overlay virtual networks at Interop, I loved to joke that we must be living on a weird planet where Microsoft has the best overlay virtual networking implementation… at least as far as IPv6 goes.
Even then, their data plane implementation which was fully dual-stack-aware on both tenant- and underlay level was way ahead of what System Center could do.
Read more ...Join Cloudflare & PicsArt at our meetup in Yerevan!

Cloudflare is partnering with PiscArt to create a meetup this month at PicsArt office in Yerevan. We would love to invite you to join us to learn about the newest in the Internet industry. You'll join Cloudflare's users, stakeholders from the tech community, and Engineers from both Cloudflare and PicsArt.
Tuesday, 4 June, 18:30-21:00
PicsArt office, Yerevan

Agenda:
- 18:30-19:00 Doors open, food and drinks
- 19:00 - 19:30 Areg Harutyunyan, Engineering Lead of Argo Tunnel at Cloudflare, "Cloudflare Overview / Cloudflare Security: How Argo Tunnel and Cloudflare Access enable effortless security for your team"
- 19:30-20:00 Gerasim Hovhannisyan, Director IT Infrastructure Operations at PicsArt, "Scaling to 10PB Content Delivery with Cloudflare's Global Network"
- 20:00-20:30 Olga Skobeleva, Solutions Engineer at Cloudflare, "Security: the Serverless Future"
- 20:30-21:00 Networking, food and drinks
View Event Details & Register Here »
We'll hope to meet you soon. Here are some photos from the meetup at PicsArt last year:




Create lab lessons for the NRE Labs Antidote network emulator
The Antidote network emulator, part of the Network Reliability Engineering project, offers a web interface that presents network emulation scenarios to users as documented lessons. Each lesson is presented in a window running Jupyter Notebooks and contains commands that the user can click on to run them on the virtual nodes in the network emulation scenario.

The NRE Labs developers intend for Antidote to be used as an educational tool. Its lesson-focused user interface supports students’ learning progress. This post is a tutorial showing how to create and test two simple, but different, Antidote lessons.
Lab documentation
At the time I wrote this post, the Antidote documentation does not provide enough practical information about how to create new Antidote labs. However, useful information is spread around in a few different locations, which I list below:
- Read the documentation about Lesson Endpoints
- The NRE Labs blog and videos on the NRE Labs Community Resources page provide some useful information about building labs for Antidote
- The Tips and FAQs Page that includes useful information about building lessons
- Read the post on the NRE Labs blog about how NRE Labs implements curriculum as code
- You can also reverse-engineer existing lab lessons
- Look Continue reading
Stopping SharePoint’s CVE-2019-0604
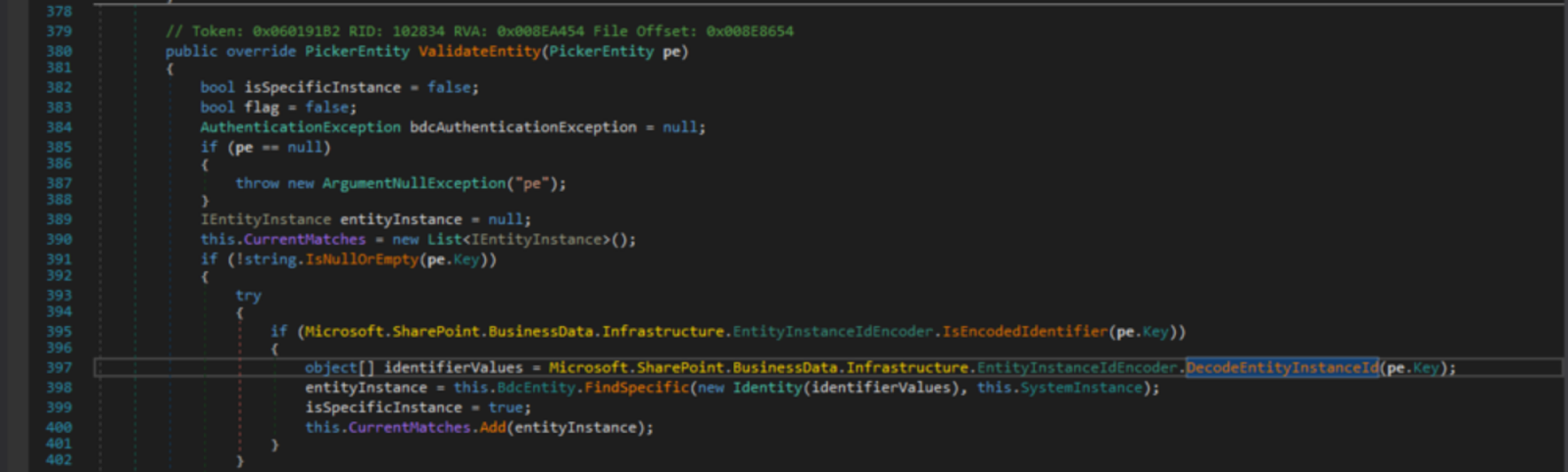
On Saturday, 11th May 2019, we got the news of a critical web vulnerability being actively exploited in the wild by advanced persistent threats (APTs), affecting Microsoft’s SharePoint server (versions 2010 through 2019).
This was CVE-2019-0604, a Remote Code Execution vulnerability in Microsoft SharePoint Servers which was not previously known to be exploitable via the web.
Several cyber security centres including the Canadian Centre for Cyber Security and Saudi Arabia’s National Center put out alerts for this threat, indicating it was being exploited to download and execute malicious code which would in turn take complete control of servers.
The affected software versions:
- Microsoft SharePoint Foundation 2010 Service Pack 2
- Microsoft SharePoint Foundation 2013 Service Pack 1
- Microsoft SharePoint Server 2010 Service Pack 2
- Microsoft SharePoint Server 2013 Service Pack 1
- Microsoft SharePoint Enterprise Server 2016
- Microsoft SharePoint Server 2019
Introduction
The vulnerability was initially given a critical CVSS v3 rating of 8.8 on the Zero Day Initiative advisory (however the advisory states authentication is required). This would imply only an insider threat, someone who has authorisation within SharePoint, such as an employee, on the local network could exploit the vulnerability.
We discovered that was not always Continue reading
Virtual Design Clinic 5 – Continues

Open, free and ready for you to join.
The post Virtual Design Clinic 5 – Continues appeared first on EtherealMind.
Wiwynn Launches Telco Edge Platform Based On OCP OpenEdge
 The server manufacturer also said it will contribute an open firmware development kit to the...
The server manufacturer also said it will contribute an open firmware development kit to the...



