Learn More about IXPs at the Middle East Network Operators Group

Internet Exchange Points are now considered to be an integral part of the Internet infrastructure worldwide. In very simple terms they are layer 2 switches that are used to route traffic that can be kept local instead of sending that traffic to the nearest major Internet node (usually located in Europe) and back. None of the countries of the Middle East contain enough globally-connected major Internet infrastructure so basically, all Internet traffic generated and terminated in the same country has to be routed through Europe. With well-implemented Internet Exchange Points, local Internet traffic stays local. Examples of local Internet traffic are financial transactions with your bank through online banking, requesting copies of your birth record from an e-government service, or any interaction with locally-hosted content.
Internet Exchange Points have three main benefits: lower latency, better cost efficiency, and control-of-traffic-sovereignty.
In the day and age of instant gratification and communications through social media and videos, latency, or the time it takes to fetch a web page, needs to be minimal and under 10ms as per industry standard (every 100km causes 1ms delay). In order to optimize the user experience, content providers have built their own global networks and spread their servers Continue reading
Introducing Cf-Terraforming
Ever since we implemented support for configuring Cloudflare via Terraform, we’ve been steadily expanding the set of features and services you can manage via this popular open-source tool.
If you're unfamiliar with how Terraform works with Cloudflare, check out our developer docs.
We are Terraform users ourselves, and we believe in the stability and reproducibility that can be achieved by defining your infrastructure as code.
What is Terraform?
Terraform is an open-source tool that allows you to describe your infrastructure and cloud services (think virtual machines, servers, databases, network configurations, Cloudflare API resources, and more) as human-readable configurations.
Once you’ve done this, you can run the Terraform command-line tool and it will figure out the difference between your desired state and your current state, and make the API calls in the background necessary to reconcile the two.
Unlike other solutions, Terraform does not require you to run software on your hosts, and instead of spending time manually configuring machines, creating DNS records, and specifying Page Rules, you can simply run:
terraform apply
and the state described in your configuration files will be built for you.
Enter Cloudflare Terraforming
Terraform is a tremendous time-saver once you have your configuration files Continue reading
SDxCentral Weekly Wrap: Google Pledges $13B for US Data Centers and Offices
 SDxCentral Weekly Wrap for Feb. 15, 2019: Google's plan will include geographic and workforce...
SDxCentral Weekly Wrap for Feb. 15, 2019: Google's plan will include geographic and workforce...
DriveNets Pockets $110M to Pave Software Disaggregation Path
 The company's software is designed to support SDN in core, aggregation, and provider edge networks,...
The company's software is designed to support SDN in core, aggregation, and provider edge networks,...
Weekend Reads 021519
The consolidation trend also has the potential to affect who participates in the IETF and how those in the industry view the value of standardization. Larger, more prosperous companies tend to have a greater ability to support standardization work, which is often paid for out of R&D or innovation budgets. Continue reading
DigitalOcean Kicks Off Managed Database Service With PostgreSQL Support
 The Managed Database service offers one-button launch and handles maintenance and updates.
The Managed Database service offers one-button launch and handles maintenance and updates.
SDxCentral’s Weekly Roundup — February 15, 2019
 Verizon adds a secure connection to Alibaba Cloud, Microsoft Azure debuts new data services; 6Wind...
Verizon adds a secure connection to Alibaba Cloud, Microsoft Azure debuts new data services; 6Wind...
Related Stories
Kaloom’s Cloud Edge Fabric Supports Network Slicing, 5G Apps
 The fabric is in trials with “two major wireless operators,” said Thomas Eklund Kaloom’s VP...
The fabric is in trials with “two major wireless operators,” said Thomas Eklund Kaloom’s VP...
SEO Best Practices with Cloudflare Workers, Part 2: Implementing Subdomains
Recap
In Part 1, the merits and tradeoffs of subdirectories and subdomains were discussed. The subdirectory strategy is typically superior to subdomains because subdomains suffer from keyword and backlink dilution. The subdirectory strategy more effectively boosts a site's search rankings by ensuring that every keyword is attributed to the root domain instead of diluting across subdomains.
Subdirectory Strategy without the NGINX
In the first part, our friend Bob set up a hosted Ghost blog at bobtopia.coolghosthost.com that he connected to blog.bobtopia.com using a CNAME DNS record. But what if he wanted his blog to live at bobtopia.com/blog to gain the SEO advantages of subdirectories?
A reverse proxy like NGINX is normally needed to route traffic from subdirectories to remotely hosted services. We'll demonstrate how to implement the subdirectory strategy with Cloudflare Workers and eliminate our dependency on NGINX. (Cloudflare Workers are serverless functions that run on the Cloudflare global network.)
Back to Bobtopia
Let's write a Worker that proxies traffic from a subdirectory – bobtopia.com/blog – to a remotely hosted platform – bobtopia.coolghosthost.com. This means that if I go to bobtopia.com/blog, I should see the content of Continue reading
SEO Best Practices with Cloudflare Workers, Part 1: Subdomain vs. Subdirectory
Subdomain vs. Subdirectory: 2 Different SEO Strategies

Alice and Bob are budding blogger buddies who met up at a meetup and purchased some root domains to start writing. Alice bought aliceblogs.com and Bob scooped up bobtopia.com.
Alice and Bob decided against WordPress because its what their parents use and purchased subscriptions to a popular cloud-based Ghost blogging platform instead.
Bob decides his blog should live at at blog.bobtopia.com – a subdomain of bobtopia.com. Alice keeps it old school and builds hers at aliceblogs.com/blog – a subdirectory of aliceblogs.com.

Subdomains and subdirectories are different strategies for instrumenting root domains with new features (think a blog or a storefront). Alice and Bob chose their strategies on a whim, but which strategy is technically better? The short answer is, it depends. But the long answer can actually improve your SEO. In this article, we'll review the merits and tradeoffs of each. In Part 2, we'll show you how to convert subdomains to subdirectories using Cloudflare Workers.
Setting Up Subdomains and Subdirectories
Setting up subdirectories is trivial on basic websites. A web server treats its subdirectories (aka subfolders) the same as regular old folders in a Continue reading
SSH to all of the serial ports
This is just a quick-and-dirty script for logging into every serial port on an Opengear box, one in each tab of a MacOS terminal.Used it just recently because I couldn't remember where a device console was connected.
Don't change mouse focus while it's running: It'll wind up dumping keystrokes into the wrong window.
Heavy Networking 430: The Future Of Networking With Guido Appenzeller
Today in our Future of Networking series I speak with Guido Appenzeller. He's been deeply involved in SDN and held key roles at Big Switch Networks and VMware, and now a new job at Yubico. We talk about the role of public cloud in IT, where the industry is with the adoption of "software-defined," the rise of whitebox, the P4 programming language, and more.
The post Heavy Networking 430: The Future Of Networking With Guido Appenzeller appeared first on Packet Pushers.
Loop Avoidance in VXLAN Networks
Antonio Boj sent me this interesting challenge:
Is there any way to avoid, prevent or at least mitigate bridging loops when using VXLAN with EVPN? Spanning-tree is not supported when using VXLAN encapsulation so I was hoping to use EVPN duplicate MAC detection.
MAC move dampening (or anything similar) doesn’t help if you have a forwarding loop. You might be able to use it to identify there’s a loop, but that’s it… and while you’re doing that your network is melting down.
Read more ...Cisco CEO Spies Networking Opportunity in AWS Outposts
 Chuck Robbins said he didn’t want to imply that a deal with AWS was in the works. But he added...
Chuck Robbins said he didn’t want to imply that a deal with AWS was in the works. But he added...
Kernel of Truth season 2 episode 1: EVPN on the host
Subscribe to Kernel of Truth on iTunes, Google Play, Spotify, Cast Box and Sticher!
Click here for our previous episode.
Guess who’s back? Back again? The real Kernel of Truth podcast is back with season 2 and we’re starting off this season with all things EVPN! This topic is near and dear to Attilla de Groots’ heart having talked about it in his recent blog here. He now joins Atul Patel and our host Brian O’Sullivan to talk more about EVPN on host for multi-tenancy.
Join as we as discuss the problem that we’re solving for, how to deploy EVPN on the host, what the caveats are when deploying and more.
Guest Bios
Brian O’Sullivan: Brian currently heads Product Management for Cumulus Linux. For 15 or so years he’s held software Product Management positions at Juniper Networks as well as other smaller companies. Once he saw the change that was happening in the networking space, he decided to join Cumulus Networks to be a part of the open networking innovation. When not working, Brian is a voracious reader and has held a variety of jobs, including bartending in three countries and working as an extra in a German Continue reading
Solving Problems with Serverless – The Cloudflare LED Data Center Board, Part I
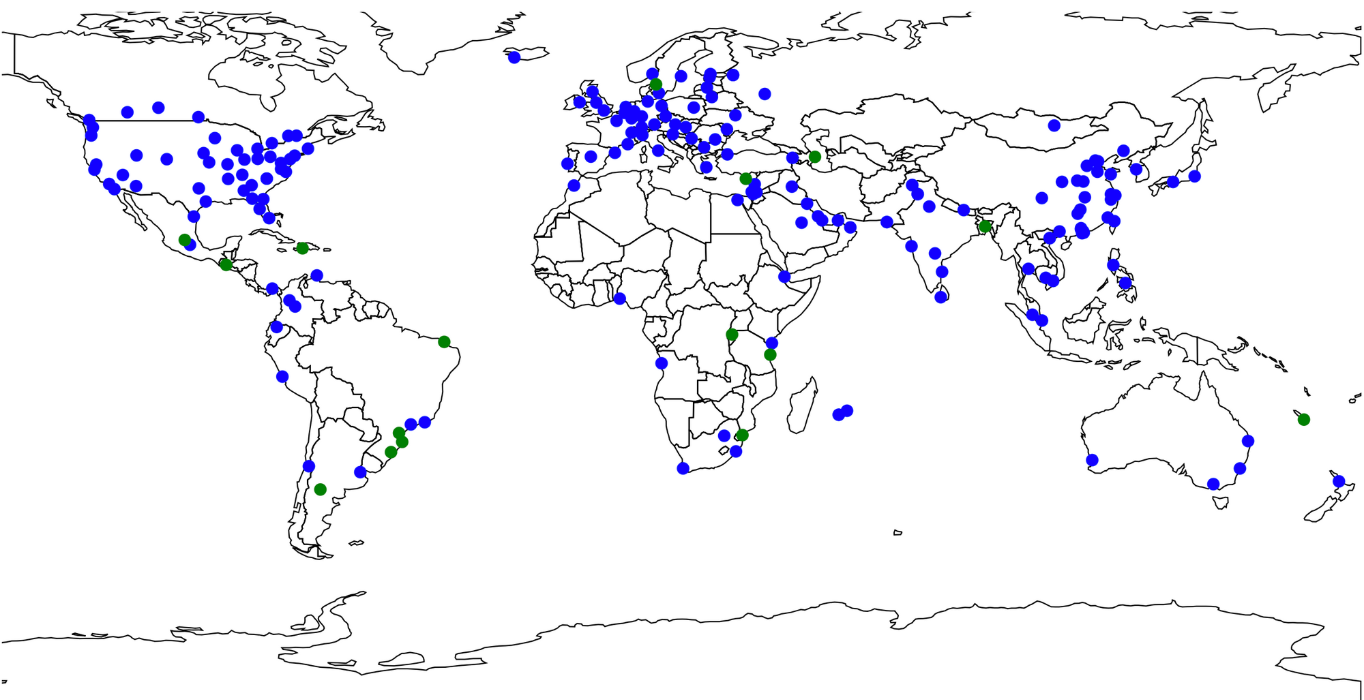
You know you have a cool job when your first project lets you bring your hobby into the office.
That’s what happened to me just a few short weeks ago when I joined Cloudflare. The task: to create a light-up version of our Data Center map – we’re talking more than a hundred LEDs tied to the deployment state of each and every Cloudflare data center. This map will be a part of our booths, so it has to be able to travel; meaning we have to consider physical shipping and the ability to update the data when the map is away from the office. And the fun part – we are debuting it at SF Developer Week in late February (I even get to give a talk about it!) That gave me one week of software time in our San Francisco office, and a little over two and a half in the Austin office with the physical materials.
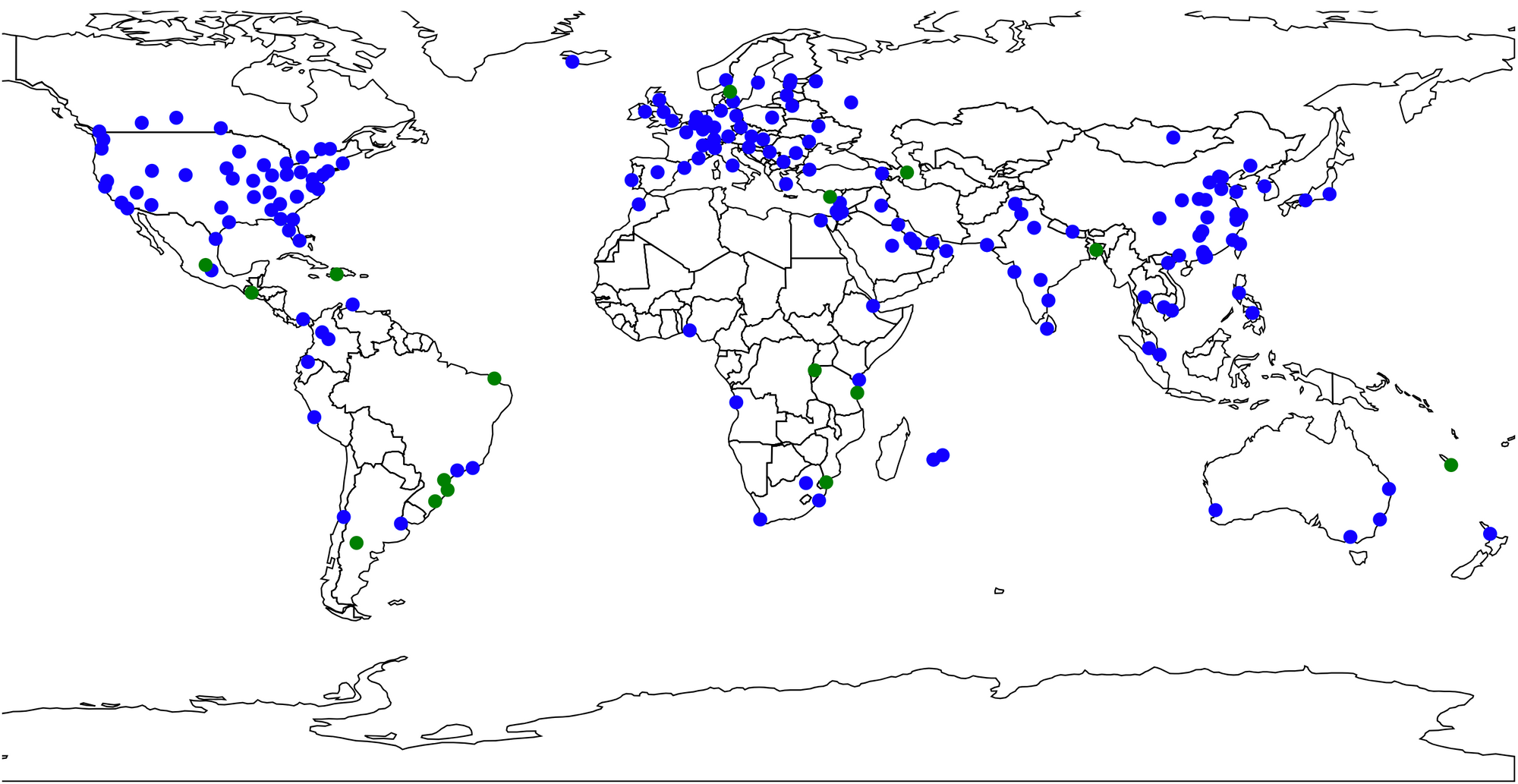
So what does this have to do with Serverless? Well, let’s think about where and how this map will need to operate: This will be going to Continue reading