Webinars in First Half of 2017
The first half of 2017 is almost gone, so it’s time to check how far I got with the plans I made in January.
Delivered:
- Total refresh of Networking in Private and Public Clouds;
- Right-sizing the network;
- Open Networking (and single-SKU data center networks);
- Two additional network automation use cases;
- Ansible deep dive material (delivered)
Worth Reading: ISO 27018 for the cloud
The post Worth Reading: ISO 27018 for the cloud appeared first on rule 11 reader.
Cord-cutting explodes – Axios
Cord cutting is an existential threat to MPLS
The post Cord-cutting explodes – Axios appeared first on EtherealMind.
Worth Watching: The Impact of Encryption
The post Worth Watching: The Impact of Encryption appeared first on rule 11 reader.
Is Anyone Using Open Daylight?
A while ago I sent out an email to my SDN and network automation mailing list (join here) asking whether anyone uses Open Daylight in anything close to a production environment (because I haven’t ever seen one).
Among many responses saying “not here” I got a polite email from VP of Marketing working for a company that sells OpenDaylight-related services listing tons of customer deployments (no surprise there).
Read more ...10 IoT Platforms Changing How Companies do Business
 When it comes to picking an IoT platform, it’s like the Wild West.
When it comes to picking an IoT platform, it’s like the Wild West.
DNS OARC 26
OARC 26 was held in May in Madrid. Here are my impressions of the meeting, drawn from some presentations that I found to be of personal interest.SREcon, DevOpsDays and Seattle vs Sillicon Valley
I am the Product Manager for StackStorm. This gives me the opportunity to attend several industry events. This year I attended SREcon in San Francisco, and devopsdays Seattle. I found both events interesting, but also found them more different than I expected.
SREcon Americas
This year SREcon Americas was held in San Francisco, a nice walk along the Embarcadero from where I live. This is bliss compared to my regular daily tour of the Californian outdoor antique railway museum, aka Caltrain.
According to the organizers, SREcon is:
…a gathering of engineers who care deeply about site reliability, systems engineering, and working with complex distributed systems at scale
That was pretty much true to form. Two things stood out to me:
- The number of smart people, working on interesting problems
- The number of companies aggressively hiring in this space.
I had many interesting conversations at SREcon. We had a booth, so would briefly start describing what StackStorm is, but would very quickly move past that. Conversations often went “Oh yeah, we’ve built something along those lines in-house, because there was nothing on the market back when we needed it. But I wouldn’t do it again. How did you solve <insert knotty Continue reading
SREcon, DevOpsDays and Seattle vs Sillicon Valley
I am the Product Manager for StackStorm. This gives me the opportunity to attend several industry events. This year I attended SREcon in San Francisco, and devopsdays Seattle. I found both events interesting, but also found them more different than I expected.
SREcon Americas
This year SREcon Americas was held in San Francisco, a nice walk along the Embarcadero from where I live. This is bliss compared to my regular daily tour of the Californian outdoor antique railway museum, aka Caltrain.
According to the organizers, SREcon is:
…a gathering of engineers who care deeply about site reliability, systems engineering, and working with complex distributed systems at scale
That was pretty much true to form. Two things stood out to me:
- The number of smart people, working on interesting problems
- The number of companies aggressively hiring in this space.
I had many interesting conversations at SREcon. We had a booth, so would briefly start describing what StackStorm is, but would very quickly move past that. Conversations often went “Oh yeah, we’ve built something along those lines in-house, because there was nothing on the market back when we needed it. But I wouldn’t do it again. How did you solve <insert knotty Continue reading
Learning Python: Week3 (Conditionals and For Loops) -Part 4
As discussed in post ( https://crazyrouters.wordpress.com/2017/02/25/learning-python-kirk-byers-python-course/ ) , i will be sharing the my learning on weekly basis as course continues. This will not only motivate me but also help others who are in phase of learning python 3. This post will focus on Week 3 (Conditionals and For Loops) .This post will focus on […]WISP Design – Using eBGP and OSPF transit fabric for traffic engineering
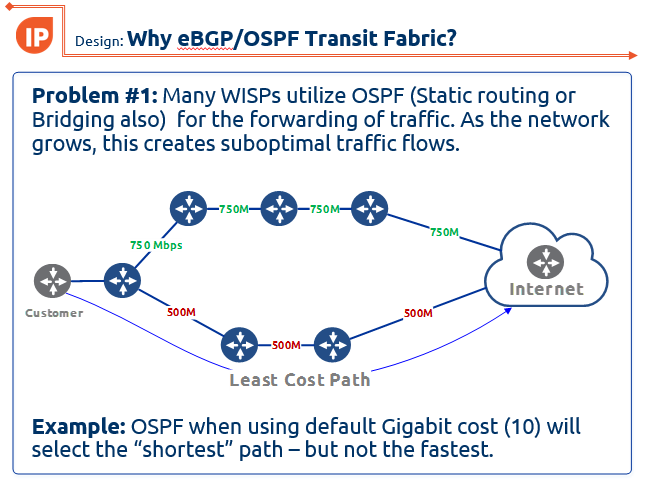
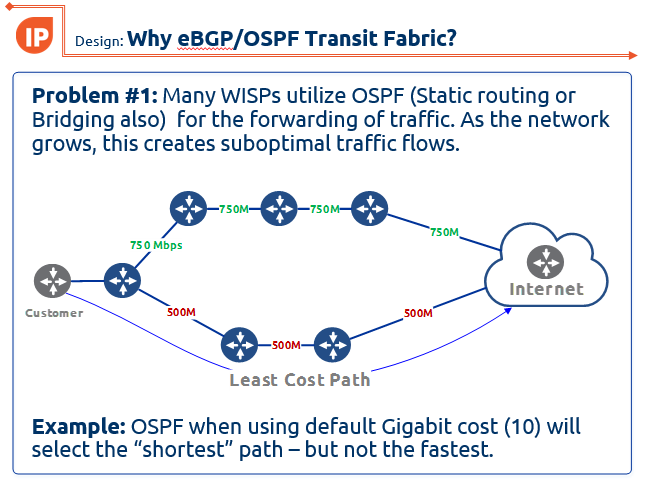
One of the latest designs we have been working on at IP ArchiTechs is using eBGP and an OSPF transit fabric to provide traffic engineering and load balancing. If you missed this presentation at the 2017 MikroTik User Meeting in Denver, CO, here are the slides:
WISP-Design-Using-eBGP-and-OSPF-TF-traffic-engineering-MUM-2017_KevinMyers-4-by-3
WISP Design – Using eBGP and OSPF transit fabric for traffic engineering
One of the latest designs we have been working on at IP ArchiTechs is using eBGP and an OSPF transit fabric to provide traffic engineering and load balancing. If you missed this presentation at the 2017 MikroTik User Meeting in Denver, CO, here are the slides:
WISP-Design-Using-eBGP-and-OSPF-TF-traffic-engineering-MUM-2017_KevinMyers-4-by-3
CCNA Wireless – CCNA Wireless Notes Chapter 3
Interference
Interference will exist if there are other transmitters on the same channel or adjacent channels. This will lead to loss of frames and the frames will then have to be retransmitted, using up air time. Interference can be caused by micro waves, DECT phones and other devices depending on the band used.
Co-Channel Interference
Co-Channel Interference occurs when two or more transmitters use the same channel. The signals completely overlap and the whole 20 or 22 MHz channel bandwidth is affected. This is only a problem if they transmit simultaneously though. However they will contend for the same airtime and a channel can become very congested. When two signals interfere, it causes data corruption, rentransmitting of frames and that in turn uses up even more airtime.
It is common practice to only place a transmitter on a specific channel where received signals are much weaker. A margin of 19 dB is recommended. The margin depends on the coding and modulation scheme. BPSK may need less than 10 db but 64-QAM will require 19 dB. More advanced modulation such as 256-QAM may require between 31 to 50 dB.
Neighboring Channel Interference
In the 2.4 GHz band neighboring Continue reading
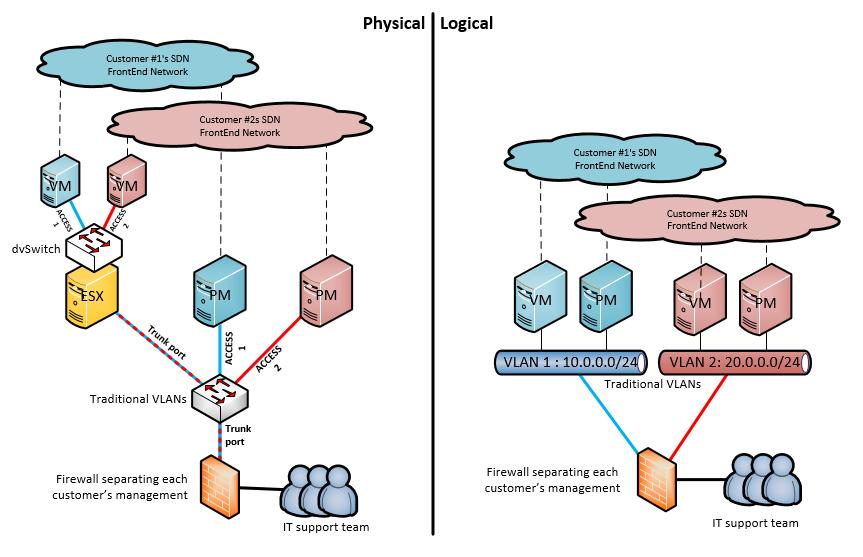
Example of private VLAN isolation across Virtual and Physical servers using ESX/dvSwitch and HP Networking Comware switches
The target was simple, we have an internal cloud datacenter at work that provides users and customers both virtual machines and physical machines. Each machine has to network interface cards (NICs), one is in control of the user/customer using SDN layer, the secondary NIC is for our support to monitor and help troubleshoot these machines when needed. This second NIC will be our target today. In the past we used per-user or per-customer firewall separations that was configuration intensive nightmare, but was reliable. However since we learned private VLANs are now supported by vmWares Distributed vSwitch (dvSwitch), we immediately tried to make it cooperate with private VLANs on physical switches. And since it worked like a charm, let me share with you a quick lab example. But theory first!
Theory of separating management rail between different customers with and without private VLANs
Fortunately Private VLANs arrived for most major vendors and promissed the ability to have one giant subnet and separate every host from each other on L2 using some basic principle of declaring ports as either promiscuous (can talk to any other port type), community (can talk to ports Continue reading
Worth Reading: A few secrets of successful learning
The post Worth Reading: A few secrets of successful learning appeared first on rule 11 reader.
Show 341: The Packet Pushers’ 7th Anniversary
The Packet Pushers 7th anniversary Weekly Show delves into the market impacts of SD-WAN, whats up with white box & thoughts on net neutrality. The post Show 341: The Packet Pushers’ 7th Anniversary appeared first on Packet Pushers.
It’s Not The Size of Your Conference Community

Where do you get the most enjoyment from your conference attendance? Do you like going to sessions and learning about new things? Do you enjoy more of the social aspect of meeting friends and networking with your peers? Maybe it’s something else entirely?
It’s The Big Show
When you look at shows like Cisco Live, VMworld, or Interop ITX, there’s a lot going on. There are diverse education tracks attended by thousands of people. You could go to Interop and bounce from a big data session into a security session, followed by a cloud panel. You could attend Cisco Live and never talk about networking. You could go to VMworld and only talk about networking. There are lots of opportunities to talk about a variety of things.
But these conferences are huge. Cisco and VMware both take up the entire Mandalay Bay Convention Center in Las Vegas. When in San Francisco, both of these events dwarf the Moscone Center and have to spread out into the surrounding hotels. That means it’s easy to get lost or be overlooked. I’ve been to Cisco Live before and never bumped into people I know from my area that said they Continue reading