IOS server load balancing with mininet server farm
The idea is to play with IOS load balancing mechanism using large number of “real” servers (50 servers), and observe the difference in behavior between different load balancing algorithms. Due to resource scarcity in the lab environment, I use mininet to emulate “real” servers. I will stick to the general definition for load balancing: A load balancer is a device […]Create a free virtual private server on Amazon Web Services
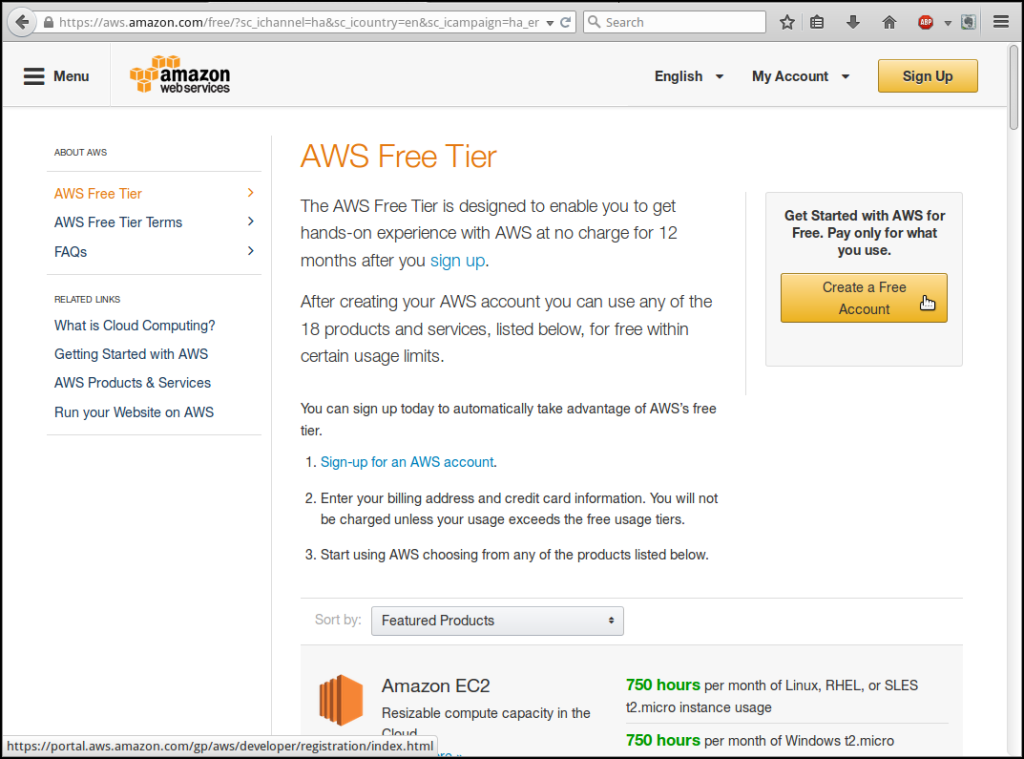
As an incentive to use their service, Amazon Web Services offers new users a “free tier” of service that provides a VPS “micro-instance” at no cost for one year.
The free tier of service is fairly flexible. Amazon AWS provides enough free hours to run the micro-instance twenty-four hours a day for a year. But if a user needs more services, he or she may create multiple micro instances and run them concurrently, which multiplies the rate the user consumes hours.
In this post, we’ll show how to set up the free server, and how to connect to it using SSH.
Create an AWS account
The first step is to create a user account on AWS. Go to the AWS Free Tier web page and click on “Sign up for AWS Account”
Then, click on “Create a free Account”.
Click on the “Free Account” button
Follow the directions provided on the AWS web site to set up a user account. You need to have a mobile phone for identity verification.
If you already have an account on amazon.com, you can use your already existing account to log into AWS services.
Create a free instance
Amazon AWS provides excellent Continue reading
Zero Touch Provisioning can help the network world catch up to server advances
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
While the term Zero Touch Provisioning (ZTP) might be increasingly more common to networking, the concept of automation has existed for years in IT. At its core, ZTP is an automation solution that’s designed to reduce errors and save time when IT needs to bring new infrastructure online.
This is particularly useful for data center servers, where scale and configuration similarities across systems make automation a necessity. In the server world, for example, Linux has revolutionized on boarding and provisioning. Rather than using command-line interfaces (CLI) to configure systems one at a time, administrators can use automation tools to roll out the operating system software, patches and packages on new servers with a single command, or the click of a mouse.
To read this article in full or to leave a comment, please click here
SDN’s First Use Case Is the WAN, But Wither Management?
SDN's First Use Case Is the WAN, But Wither Management?
by Steve Harriman, VP of Marketing - January 28, 2015
Considering how long Packet Design has been talking about the promise of SDN in the WAN, it was encouraging to see a Q&A in Network World last week on the subject. Editor John Dix interviewed Michael Elmore, IT Senior Director of the Enterprise Network Engineering Infrastructure Group at Cigna. Michael is also on the board of Open Network Users Group (ONUG).
Dix began the interview by asking why ONUG’s membership has voted the WAN as the top use case for SDN twice in a row now. In the context of the enterprise, Elmore replied that software defined WANs (SD-WANs) can reduce both capital and operational costs. He also said that they are easier to deploy than in the data center.
Elmore went on to discuss the limitations of today’s WANs (mainly the MPLS-based layer 3 VPN service offerings used by the Fortune 500) in terms of cost, scale, service quality, security, visibility, and agility/flexibility. He then outlined the benefits of SD-WANs in all those areas, saying that enterprises will be able to “take back control from service Continue reading
Open Networking is the New Normal
The data center is in a constant state of transition. What was once home for rows upon rows of propriety and often siloed equipment based on closed-architecture designs, the modern day data center is now filled with white box solutions serving various functions but working in a harmonious or converged manner.
Several key factors are driving the change to white box or open hardware – ROI, flexibility and customizability of design, ease of implementation, and the avoidance of vendor lock-in along with the high price-tag it can bring. The rise of white box hardware started with servers and storage, and now a movement towards the adoption of open networking has gained quite a bit of traction. The
Open Compute Project (OCP) movement is driving creation of bare metal switches, such as Open Switches, that are designed to be open and disaggregated. This white box model for switching enables users to deploy, monitor, and manage networking alongside servers and storage at a much lower price-point than a traditional network switch.
Scaled Networking Simplified
With a white box switch, the OS layer is decoupled from the hardware itself which allows users to independently select the best-of-breed components and networking software stack Continue reading
Big Switch Is Getting Bigger. Much Bigger.

Cool news today from BigSwitch who have taken some big steps forward with their rather awesome Big Cloud Fabric (BCF) solution.
Building on the existing features of BCF 2.0 that was announced last July (see my post on the BCF launch for more details), version 2.5 adds some pretty good new features and a surprise partner.
BCF 2.5 New Features
VMWare vCenter Support
BCF now supports VMWare vCenter. BigSwitch sees an Ethernet fabric as a complementary technology to VMWare’s NSX, not a competitor; very wisely they would like to be the underlay while NSX provides the overlay. The BCF controller integrates right into vCenter so that network configuration can be automated with the virtual environment, and the controller provides a single interface to the entire fabric.
CloudStack / OpenStack
The original BCF supported OpenStack. BCF 2.5 now has more elements of OpenStack (Juno) support and adds CloudStack support. With this and the vCenter integration, BCF has positioned itself quite nicely for full server and switch automation.
Brite Box Switching?
My first question when I heard about this was “What on earth is Brite Box switching?” It turns out that somebody somewhere coined the phrase Continue reading
Cisco Live 2015 – Time to get ready!
It is just about time to get ready for Cisco Live US this year and, harking back to 2012, we are again in San Diego, CA for the June 7-11th event. I just wanted to take a few moments and share some information that I have put together. Oh, if you have not registered yet – […]
The post Cisco Live 2015 – Time to get ready! appeared first on Fryguy's Blog.
News Analysis: Big Cloud Fabric 2.5 Released
Big Switch Networks has released version 2.5 of their Big Cloud Fabric SDN offering. Read the full press release here. What’s Big Cloud Fabric? BCF is an SDN-based IP fabric where you manage all of the individual switches as one “big switch.” In other words, you manage the fabric as a whole, and not individual switches. Big […]MPLS TE Design -Part 3
This is a continuation from Part 2 Fast Reroute Why Fast Reroute? Many NSP’s like ACME have traffic with tight SLAs. For instance below is an ITU delay recommendation for Voice. One Way Delay Characterization of Quality 0-150ms Acceptable for most applications 150-400ms May impact some applications Above 400ms Unacceptable ITU G.114 delay recommendations Having […]
Author information
The post MPLS TE Design -Part 3 appeared first on Packet Pushers Podcast and was written by Diptanshu Singh.
MPLS TE Design -Part 2
This is a continuation from Part 1 Case for LDPoRSVP As we mentioned at the very beginning that ACME provides L3VPN and L2VPN services, which requires end to end LSP between the PEs. But due to scaling reasons, ACME decided not to extend RSVP to the edge routers. This creates a problem as there is […]
Author information
The post MPLS TE Design -Part 2 appeared first on Packet Pushers Podcast and was written by Diptanshu Singh.
MPLS TE Design -Part 1
In this post we will be exploring different aspects of Traffic Engineering (RSVP-TE) from a design perspective using fictional ISP as a reference. The intent of the post is to not necessarily recommend a particular solution, but to bring up different aspects involved in the design. I am assuming that the reader already has somewhat […]
Author information
The post MPLS TE Design -Part 1 appeared first on Packet Pushers Podcast and was written by Diptanshu Singh.
Is Controller-Based Networking More Reliable than Traditional Networking?
Listening to some SDN pundits one gets an impression that SDN brings peace to Earth, solves all networking problems and makes networking engineers obsolete.
Cynical jokes aside, and ignoring inevitable bugs, is controller-based networking really more reliable than what we do today?
Read more ...GNS3 1.2.X in the “Cloud” using CentOS 7.X
Hi Everyone, I thought I would go ahead and share some of my knowledge here with everyone. I'm not sure if anyone else has triedHow to stay ahead of threats to DNS servers
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
Gartner predicts more than 30 billion devices will be connected by the Internet of Things (IoT) by 2020, and Domain Name System (DNS) servers are critical to keeping it all running. However, the number, frequency and variety of attacks on DNS servers is rising, putting businesses and initiatives like IoT at enormous risk. The good news is, there are steps you can take to mitigate these attacks.
The DNS system translates easily memorized domain names into the numerical IP addresses needed for locating computer services and devices worldwide. According to the Internet Corporation for Assigned Names and Numbers (ICANN), there are 30 to 50 million DNS servers on the planet. These servers are being hit by four main types of attacks: zero-day, cache poisoning, denial of service (DoS) and distributed denial of service (DDoS).
To read this article in full or to leave a comment, please click here
Where to Start with SDN
For the 3rd and final installment on my SDN series, this post builds on A Business Case for SDN, and the SDN Ecosystem, theNoction Intelligent Routing Platform (IRP) – What is it?
I was contacted by some people at Noction and asked if I was interested in writing about their platform, the Intelligent Routing Platform (IRP). Since it’s a product that uses Border Gateway Protocol (BGP), it peaked my interest. First let’s make the following things clear:
- I am not being paid to write this blog post
- My opinions can’t be bought
- I will only write about a product if it’s something that interests me
BGP is the glue of the Internet (with DNS) and what keeps everything running. BGP is a well designed and scalable protocol which has been around for a long time. It has grown from carrying a few hundred routes to half a million routes. However, there will always be use cases where BGP might not fit your business model.
In Noction’s white paper they define the following as the network’s major challenges:
- Meeting the customer’s demand for 100% uptime
- Facing the low latency requirement
- Achieving reliable data transmission
- Avoiding network congestion and blackouts
- Achieving consistency of throughput
- Keeping bandwidth usage below predefined commit levels
- Reducing the cost and time of network troubleshooting
The product is designed for multihomed networks running BGP. You can’t optimize network flows if Continue reading
How to transition from customer understanding to customer action
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
Many companies focus on using cheaper, faster data warehouses to organize their accumulated customer data for business intelligence. But in order to remain competitive, businesses need to be using customer data to build applications that make real-time, data-driven decisions.
If you can interpret each attribute, event and transaction as a hint to help make the best predictions and decisions for your customers, you can transition from just customer understanding to customer action. But acting upon data to optimize customer experiences requires an architecture different from traditional data warehousing and business intelligence applications.
To read this article in full or to leave a comment, please click here
Its a new year!
My apology. I have been very absent here as of late.
I have been doing some different stuff, which is irrelevant here, but rest assured, i got some posts lined up. The next one on Unified MPLS. I think you will like it, so stay tuned! ![]()
Happy New Year! ![]()