Small Business Gets Big Wi-Fi, Finally!
In a wireless world that’s so dependent on reliable connectivity, there’s something small business owners will tell you: Wi-Fi for small businesses really stinks. The small business sector is one of today’s most underserved and overlooked markets, and the opportunity...GNS3 1.1
I was never a big fan of GUI tools, so I used dynagen and dynamips for my network designs. But since 15.2 was the last version released for 7200, dynamips is no longer useful (especially for IKEv2 and OSPFv3 stuff)
I was hoping that Cisco would release VIRL, and they promised to do so for the past year and a half, but it looks like it will never come. Shelling out 10K$ for CML (the payed version of VIRL) is a bit too much for most of us. But there is a good alternative:
Not long time ago GNS3 version 1.0 was released and soon after version 1.1. was released too. And after long time of being a backer for their funding campaign I have decided to try GNS3 with IOU.
After installing GNS3 on both linux and windows (vmware required), I found that GNS3 is really easy to use, and that IOU is AMAZING. IOU is sooooo fast, and everything just works(tm). I wish I had it years ago!
Goodbye dynamips and dynagen, and thank you so much.
Hello IOU and GNS3. I know it will be a start of a wonderful friendship :)
JNCIE study lab setup.
Boom – you’ve got to love Junosphere. I just created the Proteus JNCIE study lab in 35 minutes flat. I made the topology of 13 routers, gave everything a hostname, loopback and interface descriptions and then just fired it up. When I did my CCIE I was there for >weeks< trying to get the right kit plugged together!
Have a look below:
Free Seminar – Advancing Security with the Software-Defined Data Center
We’re excited to take to the road for another edition of our VMware Software-Defined Data Center Seminar Series. Only this time, we’ll be joined by some great company.
VMware & Palo Alto Networks invite you along for a complementary, half-day educational event for IT professionals interested in learning about how Palo Alto Networks and VMware are transforming data center security.
Thousands of IT professionals attended our first SDDC seminar series earlier this year in more than 20 cities around the globe. Visit #VirtualizeYourNetwork.com to browse the presentations, videos, and other content we gathered.
This free seminar will highlight:
- The Software-Defined Data Center approach
- Lessons learned from real production customers
- Using VMware NSX to deliver never before possible data center security and micro-segmentation
Who should attend?
People who will benefit from attending this session include:
- IT, Infrastructure and Data Center Managers
- Network professionals, including CCIEs
- Security & Compliance professionals
- IT Architects
- Networking Managers and Administrators
- Security Managers and Administrators
Agenda
- 8:30 a.m. Registration & Breakfast
- 9:00 a.m. VMware: Better Security with Micro-segmentation
- 10:00 a.m. Palo Alto Networks: Next Generation Security Services for the SDDC
- 11:00 a.m. NSX & Palo Alto Networks Integrated Solution Demo
- 11:45 a. Continue reading
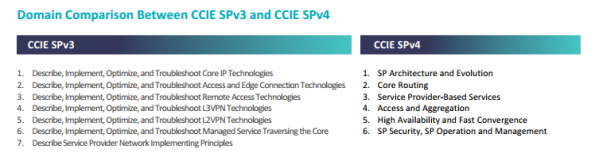
New CCIE Service Provider Version 4.0 Blueprint Announced
Cisco has announced their plans to transition the CCIE Service Provider certification blueprint from Version 3.0 to Version 4.0 starting May 22nd, 2015. The official announcement for the Written and Lab Exam Content Updates can be found here.
There are four key points to this announcement, which are:
- Lab Exam format changes
- Hardware & software version changes
- New technical topics added
- Old technical topics removed
CCIE SPv4 Lab Exam Format Changes
The Lab Exam format of SPv4 has been updated to follow the same format as the new CCIE Routing & Switching Version 5.0. This means the exam now consists of three sections: Troubleshooting, Diagnostic, and Configuration.
CCIE SPv4 Hardware & Software Version Changes
Following along with the current CCIE RSv5, CCIE SPv4 now uses all virtual hardware as well. Specifically the new hardware and software variants are as follows:
- ASR 9000 running Cisco IOS XR 5.2
- ASR 1000 running Cisco IOS XE 3.13S.15.4(3)S
- Cisco 7600 running Cisco IOS 15.5(3)S
- Cisco ME 3600 running Cisco IOS 15.5(3)S
Both the IOS XR and IOS XE variants are already available as virtual machines that you can download from cisco.com Continue reading
Juniper’s Day One: Junos Cup 2014 Book
Some fun today. Juniper recently ran a competition they called the Junos Cup 2014. It was modeled after a world cup of sorts, with each challenge involving a country in the name, four Tournament and then – because in the … Continue reading
If you liked this post, please do click through to the source at Juniper’s Day One: Junos Cup 2014 Book and give me a share/like. Thank you!
Basic OOP Python
I’ve just started with object oriented programming in Python so I thought I’d cover some of the basics here. Please don’t assume this is a thourough tutoriol on OOP! The beauty of OOP is that it allows me to create a template with which I can create objects. The building blocks of the object sit […]PS Show 35 – OEM SFP and QSFP Modules – Do They Work ?
Do you really need genuine SFP and QSFP modules in your network equipment ? We talk technical with a supplier of OEM modules for your network equipment about the technology, functions and operation of non-vendor SFP optics and modules.
Author information
The post PS Show 35 – OEM SFP and QSFP Modules – Do They Work ? appeared first on Packet Pushers Podcast and was written by Greg Ferro.
CCIE SP version 4 has been announced
Cisco has been updating their certifications lately. The CCIE RS got bumped to version 5 and went all virtual. The CCNP RS was then also updated and now it’s time for the CCIE SP.
It seems that Cisco has done a better job lately of tying all the certifications together and providing a more unified exam format. At least this is the indications I’m getting for the CCIE track.
CCIE SP v4 will use the same exam format as the CCIE RS v5. This means that there will be a diagnostic (DIAG) and troubleshooting (TS) module at the CCIE SP lab. First let’s go over the exam domain.
My impression from this is that the v4 blueprint is a bit more generic. This makes it easier to develop the exam content and I also get the feeling that it’s getting more important to have a high level understanding of the different technologies and architecture.
The exam is designed to be dual stack, so you can’t afford to be weak on v6, you must master the v6 topics at the same level as v4. If you get certified you may use the IPv6 Forum Gold logo.
The following topics have been Continue reading
Conformity as an inhibitor to strategy
Early in life, we are all made acutely aware of the power of peer pressure. Most of us probably attribute it to a deep need for belonging. But what if that deep sense of belonging is less about social acceptance and more about how we are psychologically wired? In fact, the pursuit of conformity goes beyond mere social dynamics; it is rooted in how our cognitive selves.
While this plays out in very obvious ways for individuals, the dynamics actually hold true for organizations. And for companies, the stakes might be even higher.
A guy named Solomon
In the 1950s, an American psychologist named Solomon Asch ran through a series of experiments to test the effects of conformity on individuals. His studies have been published several times, but one test in particular gives a fascinating look into how we operate.
Asch took a number of participants and asked them very simple cognitive questions. To conduct the study, Asch brought participants into a room that had seven other people. However, these seven people were actually part of the study. The eight individuals were shown a card with a line on it, followed by a card with three lines on it. The Continue reading
New Webinar: Scaling Overlay Virtual Networks
You can get an overlay virtual networking solution from almost every major hypervisor- and data center networking vendor. Do you ever wonder which one to choose for your large-scale environment? I’m positive you’d get all of them up and running in a one-rack environment, but what if you happen to be larger than that?
We’ll try to address scalability hiccups and roadblocks you might encounter on your growth path in Scaling Overlay Virtual Networks webinar (get your free ticket here).
Read more ...Is November 12 D-Day for 512k prefixes?
Is November 12 D-Day for 512k prefixes?
by Brian Boyko, Technology Contributor - October 28, 2014
During his presentation on October 7th at NANOG on the trends for prefixes over the past half-decade, Jim Cowie, chief scientist at Dyn Research, found something interesting: We may be reaching “512K day” as soon as next month.
Back in 2009, a typical IPv4 routing table contained only 269k entries. Today, in 2014, it is around 471k, and it is projected to be 519k in 2015… if not sooner. See the chart below from Cowie’s presentation.

Many older but still-in-use Cisco routers can only handle 512k border gateway protocol (BGP) routing entries in their TCAM memory. Indeed, a major outage occurred on August 12th of this year, when an accidental de-aggregation of 20k prefixes pushed the consensus routing table size over that 512k limit.
Was this an aberration, or an industry wake-up call to the fact that we are rapidly approaching a persistent 512k number of BGP entries? The chart above certainly suggests that latter. Cowie predicts that as the consensus BGP routing table hits 512k organically, we'll have a much larger and longer outage as everyone works to upgrade or replace Continue reading
Junos – Wildcard Ranges, Interface Ranges and Configuration Groups
Until recently I have worked almost exclusively on Cisco ASA and IOS platforms. Within the last six months I’ve added Juniper’s Junos platform into my repertoire. The story for how this came to be is one for another post I hope to write soon. For those who aren’t familiar, Junos is a whole different ball […]
Author information
The post Junos – Wildcard Ranges, Interface Ranges and Configuration Groups appeared first on Packet Pushers Podcast and was written by Christian Talsness.
Checking community interest for a new kind of networking site
A couple of days ago I got an idea for a new kind of networking site. The idea is to do something similar to dpreview.com but for network products.
I work a lot on network designs these days and part of the design is always what device to choose. Maybe I need a product that does NAT, IPSEC, 200 Mbit/s of throughput and has at least 4 ports. This is the kind of knowledge that you get from working on design and staying up to date with products from different vendors. There is not a community for people where they can find a broad range of products and get help choosing the right one based on different search criteria such as number of ports, features and the throughput.
What I would like to do as well is to have people write about the products. The product page said 200 Mbit/s but I got 500 Mbit/s with IMIX traffic. After enabling IPSEC I only got 80 Mbit/s. These kind of figures are very difficult to find. There could then be some kind of rating or voting system to rate if the post is helpful to sort out if people are Continue reading
Fire your mobile app programmer and build it yourself
This vendor-written tech primer has been edited by Network World to eliminate product promotion, but readers should note it will likely favor the submitter’s approach.
Everyone used to hire mobile app developers to build custom programs, but that often resulted in shoddy, insecure programs that sometimes didn’t even work. And even when the software suited the need, chances are it was a colossal waste of money.
Today you can program without programming. Even business people can define and build apps that suit their needs – in just hours or days, depending on the complexity. Or have them built for you for as a low as $500 from a provider harnessing the same automated software creation tools.
To read this article in full or to leave a comment, please click here
Using Scapple To Help Manage Complex Network Changes
I’ve blogged about Scapple in the past, describing how I’ve been using Scapple to do basic network diagrams. If you are willing to give up some of the fancy features you get with an advanced diagramming tool like Visio or Omnigraffle, Scapple can take you reasonably far. In preparation for a recent change […]Hotspots Get Hotter with Release 2 of Hotspot 2.0
Hotspot 2.0 Release 2 is here – expanding and improving on the considerable innovations introduced with HS2.0 Release 1. At Ruckus, we’ve always been huge fans of Hotspot 2.0 and have taken an active part in its testing and development....ISC DHCP WLTM NTP. Really.
I’ve mentioned before I think that on my home network, DHCP service is provided by a pair of ubuntu servers running ISC DHCP servers in a redundant configuration. Part of the reason for this is pure nerdiness, and the rest … Continue reading
If you liked this post, please do click through to the source at ISC DHCP WLTM NTP. Really. and give me a share/like. Thank you!
Learning NSX, Part 17: Adding External L2 Connectivity
This is part 17 of the Learning NSX blog series. In this post, I’ll show you how to add layer 2 (L2) connectivity to your NSX environment, and how to leverage that L2 connectivity in an NSX-powered OpenStack implementation. This will allow you, as an operator of an NSX-powered OpenStack cloud, to offer L2/bridged connectivity to your tenants as an additional option.
As you might expect, this post does build on content from previous posts in the series. Links to all the posts in the series are available on the Learning NVP/NSX page; in particular, this post will leverage content from part 6. Additionally, I’ll be discussing using NSX in the context of OpenStack, so reviewing part 11 and part 12 might also be helpful.
There are 4 basic steps to adding L2 connectivity to your NSX-powered OpenStack environment:
- Add at least one NSX gateway appliance to your NSX implementation. (Ideally, you would add two NSX gateway appliances for redundancy.)
- Create an NSX L2 gateway service.
- Configure OpenStack for L2 connectivity by configuring Neutron to use the L2 gateway service you just created.
- Add L2 connectivity to a Neutron logical network by attaching to the L2 gateway service.
5 Dev Tools for Network Engineers
I’d like to write about five things that you as a hardcore, operations-focused network engineer can do to evolve your skillsets, and take advantage of some of the methodologies that have for so long given huge benefits to the software development community. I won’t be showing you how to write code – this is less about programming, and more about the tools that software developers use every day to work more efficiently. I believe in this, there is a lot of potential benefit to network engineering and operations.
I’m of the opinion that “once you know what you don’t know, you’re halfway there”. After all, if you don’t know what you don’t know, then you can’t very well learn what you don’t know, can you? In that spirit, this article will introduce a few concepts briefly, and every single one will require a lot of hands-on practice and research to really understand thoroughly. However, it’s a good starting point, and I think if you can add even a few of these skills, your marketability as a network engineer will increase dramatically.
Proper Version Control
As a developer, version Continue reading