Can I Be Brutally Honest?
There are several reasons I love being on the road. One of them is the sense of accomplishment I get from doing a particular job in a set amount of time. There is a defined period in which I will be on site with a client to do a job, or a set number of days I will be sitting in training. The light is always at the end of the tunnel. I find that when I am involved in projects around where I live, that they tend to drag on. Time is always important, but not as important as when I am on the road.
Another reason I love being on the road is the fact that I get to interact with a number of my fellow IT professionals on their home turf. I love talking to them about their networks and seeing how they solve the particular issues of their business with technology. I also love to help them improve their networks when needed. Depending on the engagement length, a good working relationship may develop to the point where you seek each other out for conversation or shared meals when you are in the same general vicinity. In Continue reading
Bufferbloat Killed my HTTP Session… or not?
Every now and then I get an email from a subscriber having video download problems. Most of the time the problem auto-magically disappears (and there’s no indication of packet loss or ridiculous latency in traceroute printout), but a few days ago Henry Moats managed to consistently reproduce the problem and sent me exactly what I needed: a pcap file.
TL&DR summary: you have to know a lot about application-level protocols, application servers and operating systems to troubleshoot networking problems.
Read more ...Universal SSL: How It Scales
On Monday, we announced Universal SSL, enabling HTTPS for all websites using CloudFlare’s Free plan. Universal SSL represents a massive increase in the number of sites we serve over HTTPS—from tens of thousands, to millions. People have asked us, both in comments and in person, how our servers handle this extra load. The answer, in a nutshell, is this: we found that with the right hardware, software, and configuration, the cost of SSL on web servers can be reduced to almost nothing.
Modern Hardware
CloudFlare’s entire infrastructure is built on modern commodity hardware. Specifically, our web servers are running on CPUs manufactured by Intel that were designed with cryptography in mind.
All Intel CPUs based on the Westmere CPU microarchitecture (introduced in 2010) and later have specialized cryptographic instructions. Important for CloudFlare’s Universal SSL rollout are the AES-NI instructions which speed up the Advanced Encryption Standard (AES) algorithm. There’s also a set of instructions called Carry-less Multiplication (CLMUL) that computes mathematical operations binary finite fields. CLMUL can be used to speed up AES in Galois Counter-mode (GCM): our preferred mode of encryption due to its resistance against recent attacks like BEAST.
As we described in our primer on TLS Continue reading
Traveling Light – 15 Things in an Engineer’s Bag (including the bag)
My day job involves traveling around northern Europe and occasionally further afield. I often get little notice of where I’m going, or how long I’m going for. This makes for a lot of trudging along train platforms and across departure lounges. Hauling too much stuff around is guaranteed to ruin my day. Traveling light becomes a necessity, […]
Author information
The post Traveling Light – 15 Things in an Engineer’s Bag (including the bag) appeared first on Packet Pushers Podcast and was written by Glen Kemp.
Interop Debate – What-to-Study 2-minute Drill
We’re holding the Interop debate today about traditional certifications versus studying SDN. During the debate, we expect to discus the specific topics we should be studying to learn SDN. And we each get roughly two minutes each, so the answer doesn’t easily fit. This post is here so I can point people at the show here, since they might not be able to furiously write it all down.
I will circle back to this topic following the show.
Prerequisites
- CCNA + CCNP R/S
- CCNA + CCNP DC
- VCP-DCV and VCAP-DCV
- Some OpenStack Neutron
And on the first three, you can back off one cert level on one, or possibly two, depending on your goals.
Foundational SDN
- Mininet w/ options
- POX w/ options
- Wireshark of it all
- OpenFlow protocol (for learning’s sake)
Basically try as many command-line options as you can with Mininet and POX. Try the options to make POX act like a hub, switch, and router. Understand the resulting OpenFlow flows.
Pick a few more SDN controllers, install, and repeat similar exercises using Mininet.
Mininet lets you easily point to any controller by IP address and port. Try Open Daylight and a vendor’s controller.
Make a choice of Continue reading
Tech Talks: MPLS Traffic Engineering Basics
After covering the basics of MPLS, the discussion I had with Seamus Gilchrist turned to the basics of MPLS Traffic Engineering.
The video of that discussion is available online on the ipSpace.net Tech Talks web page.
Datacenter resource fragmentation
The concept of resource fragmentation is common in the IT world. In the simplest of contexts, resource fragmentation occurs when blocks of capacity (compute, storage, whatever) are allocated, freed, and ultimately re-allocated to create noncontiguous blocks. While the most familiar setting for fragmentation is memory allocation, the phenomenon plays itself out within the datacenter as well.
But what does resource fragmentation look like in the datacenter? And more importantly, what is the remediation?
The impacts of virtualization
Server virtualization does for applications and compute what fragmentation and noncontiguous memory blocks did for storage. By creating virtual machines on servers, each with a customizable resource footprint, the once large contiguous blocks of compute capacity (each server) can be divided into much smaller subdivisions. And as applications take advantage of this architectural compute model, they become more distributed.
The result of this is an application environment where individual components are distributed across multiple devices, effectively occupying a noncontiguous set of compute resources that must be unified via the network. It is not a stretch to say that for server virtualization to deliver against its promise of higher utilization, the network must act as the Great Uniter.
Not just a virtual phenomenon
While Continue reading
Cumulus Linux: First Impressions
Typically, when you buy a network router or switch, it comes bundled with some version of the manufacturer's operating system. Cisco routers come with IOS (or some derivative), Juniper routers come with Junos, and so on. But with the recent proliferation of merchant silicon, there seem to be fewer and fewer differences between competing devices under the hood. For instance, the Juniper QFX3500, the Cisco Nexus 3064, and the Arista 7050S are all powered by an off-the-shelf Broadcom chipset rather than custom ASICs developed in-house. Among such similar hardware platforms, the remaining differentiator is the software.
One company looking to benefit from this trend is Cumulus Networks. Cumulus does not produce or sell hardware, only a network operating system: Cumulus Linux. The Debian-based OS is built to run on whitebox hardware you can purchase from a number of partner Original Device Manufacturers (ODMs). (Their hardware compatability list includes a number of 10GE and 40GE switch models from different vendors.)
Cumulus Linux is, as the name implies, Linux. There is no "front end" CLI as on, for example, Arista platforms. Upon login you are presented with a Bash terminal and all the standard Linux utilities (plus a number of Continue reading
Rome Wasn’t Software Defined In A Day
Everywhere you turn, people are talking about software defined networking. The influence can be felt in every facet of the industry. Major players are trying to come to grips with the shift in power. Small vendors are ramping up around ideas and looking to the future. Professionals are simultaneously excited for change and fearful of upsetting the status quo. But will all of these things happen overnight?
Not Built In A Day, But Laying Bricks Every Hour
The truth of SDN is that it’s going to take some time for all the pieces to fall into place. Take a look at the recent Apple Pay launch. Inside of a week, it has risen to become a very significant part of the mobile payment industry, even if the installed base of users is exclusive to iPhone [6,6+] owners. But did this revolution happen in the span of a couple of days?
Apple Pay works because Apple spent months, if not years, designing the best way to provide transactions from a phone. It leverages TouchID for security, a concept introduced last year. It uses Near Field Communication (NFC) readers, which have been in place for a couple of Continue reading
Inside Shellshock: How hackers are using it to exploit systems
On Wednesday of last week details, of the Shellshock bash bug emerged. This bug started a scramble to patch computers, servers, routers, firewalls, and other computing appliances using vulnerable versions of bash.

CloudFlare immediately rolled out protection for Pro, Business, and Enterprise customers through our Web Application Firewall. On Sunday, after studying the extent of the problem, and looking at logs of attacks stopped by our WAF, we decided to roll out protection for our Free plan customers as well.
Since then we've been monitoring attacks we've stopped in order to understand what they look like, and where they come from. Based on our observations, it's clear that hackers are exploiting Shellshock worldwide.
 (CC BY 2.0 aussiegall)
(CC BY 2.0 aussiegall)
Eject
The Shellshock problem is an example of an arbitrary code execution (ACE) vulnerability. Typically, ACE vulnerability attacks are executed on programs that are running, and require a highly sophisticated understanding the internals of code execution, memory layout, and assembly language—in short, this type of attack requires an expert.
Attacker will also use an ACE vulnerability to upload or run a program that gives them a simple way of controlling the targeted machine. This is often achieved by running a "shell". Continue reading
What The Heck Is SPDY?
A10‘s presentation at NFD8 seemed to generate a bit of interest (dare I say excitement) and many a question around the SPDY (pronounced ‘speedy’) protocol. I promised Lindsey Hill (@northlandboy) on Twitter that I’d write a blog post about it and here it is. It took me rather longer to write than I thought and […]
Author information
The post What The Heck Is SPDY? appeared first on Packet Pushers Podcast and was written by Steven Iveson.
The Atomic Weight of Policy

The OpenDaylight project put out a new element this week with their Helium release. The second release is usually the most important, as it shows that you have a real project on your hands and not just a bunch of people coding in the back room to no avail. Not that something like that was going to happen to ODL. The group of people involved in the project have the force of will to change the networking world.
Helium is already having an effect on the market. Brocade announced their Vyatta Controller last week, which is based on Helium code. Here’s a handy video as well. The other thing that Helium has brought forth is the ongoing debate about network policy. And I think that little gem is going to have more weight in the long run than anything else.
The Best Policy
Helium contains group-based policies for making groups of network objects talk to each other. It’s a crucial step to bring ODL from an engineering hobby project to a full-fledged product that can be installed by someone that isn’t a code wizard. That’s because most of the rest of the world, including IT people, don’t speak in specific Continue reading
What’s so special about 512?
The 12th August 2014 was widely reported as a day when the Internet collapsed. Despite the sensational media reports the following day, the condition was not fatal, and perhaps it could be more reasonably reported that some parts of the Internet were having a bad hair day. What was happening was that the Internet’s growth had just exceeded the default configuration limits of certain models of network switching equipment. In this article I'll look at how the growth of the routing table and the scaling in the size of transmission circuits impacts on the internal components of network routing equipment.Replacing a Central Firewall
During one of my ExpertExpress engagements I got an interesting question: “could we replace a pair of central firewalls with iptables on the Linux server?”
Short answer: Maybe (depending on your security policy), but I’d still love to see some baseline scrubbing before the traffic hits the server – after all, if someone pwns your server, he’ll quickly turn off iptables.
Read more ...Using frameworks for effective sales presos
Anyone who has ever delivered a presentation or even listened to one knows that the key to an effective presentation is telling a story. If you peruse even a few pages of any of the books about how to deliver a solid presentation, you will find references to storytelling and its role in passing along information throughout history. Yes, we must tell stories. But not all stories work.
So how do you pick a story or a framework for a presentation that will be effective?
Stories vs frameworks
Let me start off by saying that you need both stories and frameworks. When you think about the structure of the points you want to convey, think about frameworks. When you want to make a point real, use a story. When you are delivering a technical presentation especially, you are very unlikely to find a single story that can weave in all the points you want to make. You are, after all, a presenter not a comedian. Don’t try to force all of your points into a long story.
So that leaves you searching for a framework. A framework is simply a way of organizing your points. It is ultimately the framework Continue reading
Network Automation & Controller Questionnaire
With all of the current trends coming in to the industry around policy based network configuration, network automation and controller value add, do you understand why and where the trends are coming from? With organisations, consultancy outfits and independents struggling to see where things are going in the industry, it’s imperative that as an industry we steer eduation and awareness. Sure, the big players are steering things, but you, the fraternity drive the demand. Have your say and the results will be published at the end of the year once there are enough submissions to represent a varying set of opinions.
Do you actually have a customer dying to move to a policy based operations model? Do you know what policy based configuration is and where the industry is going with it?
Does your organisation have a rigid change management stucture? How would your company handle automatic network configuration generation? Would you still need to manually execute the deployment and email with a “green tick” to the change board?
Do you automate your build configuration already? How do you do that? Are you comfortable with it?
Do you have ideas on what value a controller could bring to your organisation? Continue reading
Software Defined Networking – SDN
Software defined networking (SDN) is an approach to computer networking that allows network administrators to manage network services through abstraction of lower level functionality. This is done by decoupling the system that makes decisions about where traffic is sent (the control plane) from the underlying systems that forward traffic to the selected destination (the data […]
The post Software Defined Networking – SDN appeared first on Roger Perkin - Networking Articles.
CCIE RFC List for Routing & Switching Lab Exam
In computer network engineering, a Request for Comments (RFC) is a memorandum published by the Internet Engineering Task Force (IETF) describing methods, behaviors, research, or innovations applicable to the working of the Internet and Internet-connected systems. The list below details all RFC’s relevant to the CCIE Routing and Switching track. CCIE RFC List OSPF RFC […]
The post CCIE RFC List for Routing & Switching Lab Exam appeared first on Roger Perkin - Networking Articles.
Universal SSL: Be just a bit more patient

It turns out it takes a while to deploy SSL certificates for 2 million websites. :-) Even longer when you get a flood of new sign ups. While we'd hoped to have the deployment complete within 24 hours of the announcement, it now looks like it's going to take a bit longer. We now expect that the full deployment will be complete about 48 hours from now (0700 UTC). Beyond that, nothing about the plan for Universal SSL has changed and hundreds of thousands of sites are already active.
Errors you may see
In order to get through the highest priority sites first, we've prioritized provisioning the sites with the most traffic.
While you wait for your site to get provisioned, you may see a certificate mismatch error if you try and visit it over HTTPS. (Rest assured, there are no errors if you visit over HTTP.) The errors over HTTPS are expected and normal during the provisioning process. Examples of what these error looks like in various browsers )Chrome, Safari, Firefox, and Internet Explorer) are below:

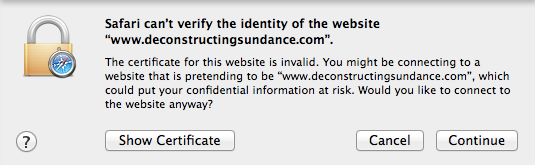
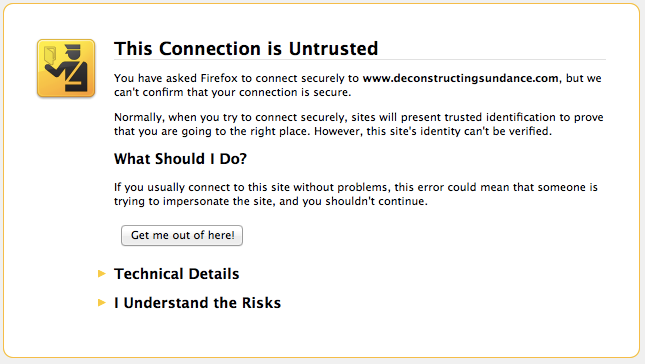
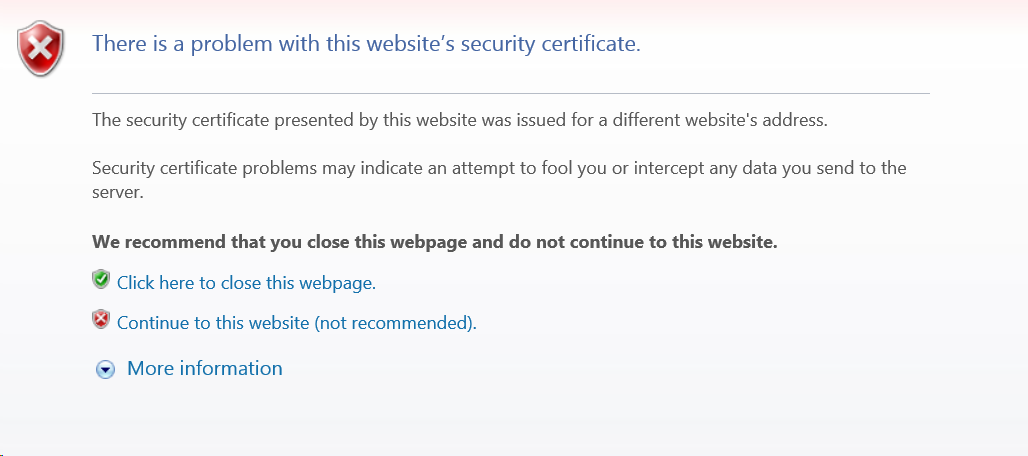
Tracking our progress
To give you a sense of our progress provisioning Universal SSL for your sites, we've updated the alert that Continue reading