Rolling back to Maven 3.0.X on OSX (Homebrew)
The current version of Maven in Homebrew at the time of writing is 3.2.2
This is great... unless one of the plugins in your project doesn't support it and then you have to downgrade :(
Fortunately it's not too painful
brew uninstall maven
brew tap homebrew/versions
brew install …Five Sinkholes of newGOZ
By Dennis Schwarz and Dave Loftus
It has been a few weeks since news broke of the Zeus Gameover variant known as newGOZ. As has been reported, the major change in this version is the removal of the P2P command and control (C2) component in favor of a new domain generation algorithm (DGA).
The DGA uses the current date and a randomly selected starting seed to create a domain name. If the domain doesn’t pan out, the seed is incremented and the process is repeated. We’re aware of two configurations of this DGA which differ in two ways: the number of maximum domains to try (1000 and 10,000) and a hardcoded value used (0×35190501 and 0x52e645).
Date based domain generation algorithms make for excellent sinkholing targets due to their predictability, and provides security researchers the ability to estimate the size of botnets that use them. With this in mind, we have gathered five days worth of newGOZ sinkhole data. Our domains are based on the first configuration, since this configuration seems to be used the most in the wild.
As with all sinkhole data, many variables can affect the accuracy of victims such as network topology (NAT and DHCP), timing, Continue reading
Introducing the Multicast “Dating Service” (aka the “RP”)
In February of 2001 I attended a 5 day multicast class within Cisco taught by none other than Beau Williamson! In both his book and during the class, he kept referring to the multicast rendezvous point (RP) as: “a meeting place for multicast receivers and senders (almost like a multicast dating service for multicast routers)” -Developing IP Multicast Networks, […]
Author information
The post Introducing the Multicast “Dating Service” (aka the “RP”) appeared first on Packet Pushers Podcast and was written by Denise "Fish" Fishburne.
Internet Touches Half Million Routes: Outages Possible Next Week
There was minor consternation in Internet engineering circles today, as the number of IPv4 networks worldwide briefly touched another magic “power of 2″ size limit. As it turns out, 512K (524,288 to be exact, or 2-to-the-19th power) is the maximum number of routes supported by the default TCAM configuration on certain aging hardware platforms.
The problem is real, and we still haven’t seen the full effects, because most of the Internet hasn’t yet experienced the conditions that could cause problems for underprovisioned equipment. Everyone on the Internet has a slightly different idea of how big the global routing table is, thanks to slightly different local business rules about peering and aggregation (the merging of very similar routes to close-by parts of the Internet address space). Everyone has a slightly different perspective, but the consensus estimate is indeed just under 512K, and marching higher with time.
The real test, when large providers commonly believe that the Internet contains 512K routes, and pass that along to all their customers as a consensus representation of Internet structure, will start later this week, and will be felt nearly everywhere by the end of next week.
Enterprises that rely on the Internet for delivery of Continue reading
Huawei Learning Website
Huawei is showing some signs of maturity in the Enterprise market with this Learning website offering free e-learning courses. Unfortunately, it’s seriously restricted to partners or some other weird criteria for membership. Entitlement E-Learning courses currently face to the following types of users: Huawei channel partners; Huawei Authorized Learning Partner(HALP) and the one who passed […]
The post Huawei Learning Website appeared first on EtherealMind.
A Training Class Where I Actually Learned Something
 TL/DR – Canned labs never work for me.
TL/DR – Canned labs never work for me.
Training for me has always been hit or miss. I have had better luck with in person classes than online training. I realize that everyone learns differently, so I suppose you pick the model that works best for you and hope you get your money’s worth out of it.
Back in June, I had the pleasure of attending the ClearPass Advanced Labs course at the Aruba headquarters out in Sunnyvale, CA. This was not a typical “class”. In fact, every time I referred to it as a “class”, I was reminded by the instructor that it was more of a workshop. The instructor was not there to teach you everything about ClearPass. Their job is to simply function as a proctor and help out when you got stuck on a particular issue. Yes, there was a slide deck, but it was VERY brief and just covered the goals of the day’s activities.
What Made It Different?
In short, the lack of step by step instructions. Many of the training classes I have attended consist of the following:
1. Death by Powerpoint
2. Canned labs
There’s no need to elaborate on the first Continue reading
What caused today’s Internet hiccup
Like others, you may have noticed some instability and general sluggishness on the Internet today. In this post we’ll take a closer look at what happened, including some of the BGP details!
At around 8am UTC Internet users on different mailing lists, forums and twitter, reported slow connectivity and intermediate outages. Examples can be found on the Outages mailing list company support site such as liquidweb and of course on Nanog.
How stable is the Internet
So how do we know if the Internet was really unstable today? One way to look at this is by looking at the outages visible in BGP over the last 12 months. On average we see outages for about 6,033 unique prefixes per day, affecting on average 1470 unique Autonomous Systems. These numbers are global averages and it’s worth noting that certain networks or geographical areas are more stable than others.
If we look at the number of detected outages by BGPmon today we see outage for 12,563 unique prefixes affecting 2,587unique Autonomous Systems. This is well above the daily average and indeed both the unique prefixes and the unique Autonomous Systems count are Continue reading
Rolling back to Maven 3.0.X on OSX (Homebrew)
The current version of Maven in Homebrew at the time of writing is 3.2.2
This is great... unless one of the plugins in your project doesn't support it and then you have to downgrade :(
Fortunately it's not too painful
:::bash brew uninstall maven brew tap homebrew/versions brew install maven30
@dave-tucker
Cisco 881 or Cisco 881?
There are two versions of the Cisco 881 branch router:- Part numbers beginning with CISCO881, which have been end of lifed.
- Part numbers beginning with C881, which are newly available.
| New C881 on top, old CISCO881 (not wireless - don't believe the stickers) on bottom. |
| New C881 on top |
| Twin screw holes on the new C881... |
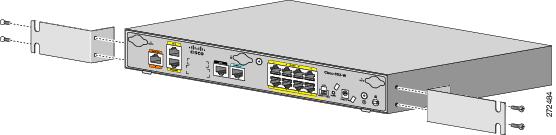 |
| ...make the ACS-890-RM-19= work on the C881. |
- The USB port has been moved from one side to the other.
- The "fake" screw hole on the side is now a threaded hole, which means that the C881 will accept the 891's rack mount hardware.
- The Fa4 port has moved a bit.
- The C881 is lead free, which seems to be what prompted all of these gyrations.
- We have a power switch!
- There's no longer a dedicated PoE brick.
- There's still a required internal PoE module, and it's got a different part number.
After CCIE SP >>>>Python
After certifying CCIE SP #44298 , I am using my time now to explore Python and seriously enjoying it…
Tipping Point 2.0
Nine months ago, I wrote about how advances in silicon designs and technologies were going to create a product set that will democratize the networking components in modern data centers. Specifically, that the Trident II family of products will perform the role that Xeon did on the compute side and provide the fulcrum on which open networking OSes would flip the industry.
Today, I am happy to add to that story and talk a little about the secondary effects that that tipping point has set in motion. We had set about to make the networking space an open, agile and innovation-laden environment akin to the compute space, but we are finding a tremendous appetite for the story to be moved further forward and have networking and compute be treated as complete equals. The drive to manage compute and networking in a harmonious way, in the way that a bus and CPUs operate inside a single box, will have a familiar lynchpin – x86 processors.
Let’s look at a little historical context around the progression of CPUs that sit inside data center switching systems. Traditionally, the CPU that sat inside a networking box operated its control plane. The calculus used to Continue reading
Maybe MU-MIMO Matters

As 802.11ac becomes more widely deployed in environments I find myself looking to the next wave and the promise it brings. 802.11ac Wave 1 for me really isn’t that groundbreaking. It’s an incremental improvement on 802.11n. Wave 1 really only serves to wake up the manufacturers to the fact that 5 GHz radios are needed on devices now. The real interesting stuff comes in Wave 2. Wider channels, more spatial streams, and a host of other improvements are on the way. But the most important one for me is MU-MIMO.
Me Mi Mo Mum
Multi-user Multiple-Input Multiple-Output (MU-MIMO) is a huge upgrade over the MIMO specification in 802.11n. MIMO allowed access points to multiplex signals on different channels into one data stream. It accomplished this via Spatial Division Multiplexing (SDM). This means that more antennas on an access point are a very good thing. It increases the throughput above and beyond what could be accomplished with just a single antenna. But it does have a drawback.
Single-user MIMO can only talk to one client at a time. All the work necessary to multiplex those data streams require the full attention of a single access point for Continue reading
Thwarting BGP Route Hijacking with SDN as a Catalyst
Thwarting BGP Route Hijacking with SDN as a Catalyst
by Cengiz Alaettinoglu, CTO - August 12, 2014
Following up on my last post about the security vulnerabilities in BGP, the IETF has taken two efforts to fix them. Back in 1995, the Routing Policy System Working Group was formed (I have chaired this working group, and many in the community, including folks from service providers and address registry operators, contributed). We have standardized a language called Routing Policy Specification Language (RPSL[ref]), and a security model (RP-SEC [ref]).
Network operators, both service providers and enterprises, would register their authorized routes (by chain of trust starting from the Internet Assigned Numbers Authority), and the neighbor ASs they pass these routes to. Given the state of the art in 1994, the security credentials (authentication as well as authorization) would be checked at the time of registration. We then wrote a tool that read these validated policy specifications and generated router configurations that would be immune to these kinds of attacks. Unfortunately, RPSL adoption has been low (more on this later).
IETF recently took another effort in its Secure Inter-Domain Routing Working Group (SIDR). The technology developed there can check the security credentials in-band Continue reading
The Accumulated IGP Metric Attribute for BGP
This is an interesting draft which can ensure better paths are chosen in certain corner cases. Before this draft, BGP was able to redistribute the IGP metric as a MED value into BGP. The issue with MED is that it’s very low on the BGP best path algorithm. Note that Cisco/Brocade consider weight as primary, […]VMworld 2014 Networking and Security Session Guide
At last year’s show, we introduced you to VMware NSX, and presented a vision for how network virtualization will fundamentally change data center networking. We focused a lot on what NSX is, what it does, and why you should start planning to virtualize your network.
This year, we’re still focused on the basics. We have a lot of content that will help those of you who are new to network virtualization and NSX start to establish a base. But of course, we have a whole year of selling NSX under our belt. And we want to share that experience with you in a VMworld program that will take you, and NSX, to the next level.
Security and network micro-segmentation? We’ve got it covered. Customer deployment stories? You bet. Partners with real GA solutions, solving real-world problems? They are on the agenda.
Take a pass through the list below, and then check out the schedule builder on VMworld.com to organize your week.
We think the #NSXninjas will be out in full force at VMworld. Are you one? We hope so!
Monday August 25, 2014
Networking Sessions
|
NET1846 |
Introduction to NSX |
11:00 – 12:00 PM |
|
NET1214 |
NSX Continue reading |
Balanced Buffer Design for Mission-Critical Cloud Networks
Leading customers and researchers in cloud and data center networking have been promoting the importance of understanding the impact of TCP/IP flow and congestion control, speed mismatch and adequate buffering for many decades. The problem space has not changed during this time, but the increase in the rates of speed by 100X and in storage capacity by 1000X have aggravated the problem of reliable performance under load for data intensive content and for storage applications, in particular. One Arista fan summed it up best by saying:
“Basically the numbers have changed by order of magnitude, but the problem is the same!”
Poor performance and inadequate buffering in a demanding network is a painful reminder that buffering, flow control, and congestion management must be properly designed. TCP/IP was not inherently built for rate-fairness, and packets are intentionally dropped (yes, only window fairness is possible). Yet the effect of these drops can be multiplicative given major speed mismatches of 10-100X inside the data center. In the past, QoS and rate metering were adequate. However, at multi-gigabit and terabit speeds and particularly as more storage moves from Fiber Channel (with buffer credits) to Ethernet, packet loss gets more acute.
Benefits of Balanced Continue reading
The Canadian Bitcoin Hijack
A few days ago researchers at Dell SecureWorks published the details of an attacker repeatedly hijacking BGP prefixes for numerous large providers such as Amazon, OVH, Digital Ocean, LeaseWeb, Alibaba and more. The goal of the operation was to intercept data between Bitcoin miners and Bitcoin mining pools. They estimated that $83,000 was made with this attack in just four months. The original post has many of details which we won’t repeat here, instead will take a closer look at the BGP details of this specific attack.
Attack details
Our friends at Dell SecureWorks decided not to name the network from which the hijacks originated. As a result we won’t name the exact Autonomous System either, instead we will suffice by saying that the originator of this hijack is a network operating in Eastern Canada.
Initial experiment
BGPmon detected the first hijack by this Canadian Autonomous System on October 8th 2013. For about 14 minutes a more specific /24 prefix for a Palestinian network was hijacked. Looking at geographical scope of the announcements and the probes that saw this route, we believe that in this case the route was only announced over the Toronto Internet Exchange.
Bitcoin hijack
On Feb Continue reading
Let’s Connect at VMworld 2014
I’ll be at VMworld in a couple of weeks. If you’re a vendor that would like to chat, please schedule me. I’d be happy to meet. If you’re a fellow IT engineer, I’d be happy to meet up as well. I’ll be hanging with folks from Tech Field Day, as well as Chris […]Downloads
Here is a repository of Wi-Fi related documents and resources that WLAN administrators will find useful.
If you have a Wi-Fi related document, tool, or resource that you would like included on this list, please contact me for inclusion! My contact info is listed on the right column of this website.
Revolution Wi-Fi Downloads:

35 presentation slides, PDF format.
This presentation covers an approach and methodology to integrating WLAN capacity planning into the WLAN design process to allow network engineers to effectively meet growing capacity demands by clients on wireless networks. It defines what capacity means for a WLAN, what factors determine capacity, provides an approach to designing for capacity, and where capacity planning should be integrated into the overall WLAN design process.
Effective capacity planning is required for all WLANs, not just high-density environments.
This information was presented at the WLAN Professionals Conference (2014).
You can also
and download the
to help calculate capacity needs, which helps simplify the process and step the user through each step.

Wi-Fi SSID Overhead Calculator
Excel Spreadsheet format.
This tool allows WLAN administrators to assess the network performance impact that multiple SSIDs Continue reading
SSID Overhead Calculator
One of the most commonly cited best practices among Wi-Fi professionals is to the limit the number of SSIDs you have configured on your WLAN in order to reduce the amount of overhead on the network and to maintain high performance. But there is not a lot of public data out there to really drive home this point when explaining it to another engineer, management, or a customer. Simply telling someone that they shouldn't create more than 'X' number of SSIDs isn't very convincing.Therefore, I've created a visual tool to help you explain WHY too many SSIDs is a bad thing:
The Wi-Fi SSID Overhead Calculator
(Click Image to Download)
| Wi-Fi SSID Overhead Calculator |
This tool calculates the percentage of airtime used by 802.11 beacon frames based on the following variables:
- Beacon Data Rate - beacon frames are sent at the lowest Basic / Mandatory data rate configured on the WLAN. Beacons must be sent at a "legacy" data rate, meaning only 802.11a/b/g rates. Select the beacon data rate from the drop-down menu within the tool.
- Beacon Frame Size - beacon frames can vary in size based on the version of the 802.11 standard implemented (802. Continue reading
