Transform ISP Choice from Anecdote to Evidence
Have you ever had to defend your choice of internet service provider? All you can say is: “Everyone says they’re reliable”, “My buddy recommended them.”, “They are the incumbent player”. But when pressed about frequent connectivity issues, then what? Sound familiar? This plays out in businesses across the world every day. We make one of […]
The post Transform ISP Choice from Anecdote to Evidence first appeared on Rick Mur.Blog Reboot
When I first launched this site, many years ago, it served as a humble lab notebook and sharing short personal stories from my working life. I shared diagrams, Junos configs , and field notes written after late night maintenance windows or proof of concepts. Those stories took on a life of their own. They brought […]
The post Blog Reboot first appeared on Rick Mur.JNCIE-DC Lab Experience
After plenty of hours of studying and labbing the wide ranging topics on the JNCIE-DC blueprint, I took the JNCIE-DC lab exam and passed! I can proudly say I’m JNCIE-DC #389. In this conclusion of the previous JNCIE-DC blogs about my lab setup and about the remote lab environment, I will talk about my experience […]
The post JNCIE-DC Lab Experience first appeared on Rick Mur.JNCIE-DC remote lab exam resources
Due to the COVID-19 pandemic the exam centers of Juniper are at time of this writing closed for external visitors. Fortunately the Juniper Education team did a great job and made JNCIE lab exams available from your own home! Now this does impact how you make the test and also what resources you have available […]
The post JNCIE-DC remote lab exam resources first appeared on Rick Mur.JNCIE-DC lab in EVE-NG tips and tricks
After having some feedback regarding my previous post on running the JNCIE-DC self-study workbook in EVE-NG. I wanted to share some of the most common questions I personally experienced while using the lab and general things to be aware of and some tips! I also ran into some aspects of going through the workbook that […]
The post JNCIE-DC lab in EVE-NG tips and tricks first appeared on Rick Mur.JNCIE-DC lab in EVE-NG
As explained in my previous post on my home servers, I have a bare metal system deployed with EVE-NG Pro installed. As I’m (slowly) preparing for the JNCIE-DC certification I wanted to share the topology that I’m using. As the hardware required to study for the JNCIE-DC is quite significant, it makes a lot of […]
The post JNCIE-DC lab in EVE-NG first appeared on Rick Mur.Home Network 2020
Recently I moved to a new house and as a lot of reconstruction was done to bring the house up to date. I took the opportunity to have something I’ve always wanted in my home: a server rack! In my previous lab set-ups they were either located in my employers lab location or placed in […]
The post Home Network 2020 first appeared on Rick Mur.Next Generation Global Connectivity
Technologies like SDWAN have fundamentally changed the way we think about WAN infrastructures for enterprise IT environments over the past few years. Global WAN offerings are no longer a necessity as pretty much ‘any’ connectivity will do. You are no longer bound to private (MPLS-based) connections/networks. Software and smarter routing mechanisms will fix all your […]Why leave a vendor job….twice?
Over the past few months I’ve been working hard on my new start-up company PeakFactory, it’s going really well, but for this post I want to focus on the reason why I chose to leave the companies I used to work for. I thought this was relevant, as many people have asked me why, but also in general there is a lot of discussion how to advance your career in different directions.
Why leave a comfortable and good job at all?
Back in 2013 I was working in a very good position, where I had a lot of freedom in choosing the customers I’d like to work on and was involved in all technical aspects of a project (pre-sales, proof of concepts, implementation and support). Still I had this feeling that I wanted to explore more an different areas for a wider audience. Which is why I decided to start working for a networking vendor. My main reason for choosing a vendor is that I could leverage my experience in the technology and apply it for a wider audience (maybe even worldwide)
Why work for Cisco and Juniper?
In early 2014 I got in touch with Cisco and I left Continue reading
What is P4?
Recently I attended a workshop organised by the Open NFP organisation about Data Plane acceleration. The primary goal of the workshop was to get students and researchers (why was I there you may think) familiar with the P4 programming language.
P4 is a programming language created to simplify writing data planes for networking use cases. Recently the P4-16 spec was released and could be considered a mature version of the language.
Now I’m not a hardcore developer. I know my way around in Python, GoLang and C#, but I never wrote anything more low level like C. P4 is created a little bit like GoLang, where I do not mean it as comparison, but as an architecture. P4 is designed so you only need to focus on the actual networking features that you want to make available on the hardware you are programming it for. Then when you compile it, it will generate runtime code for your hardware. Or as the creators explain it:
At one level, P4 is just a simple language for declaring how packets are to be processed. At another level, P4 turns network system design on its head.
There is no need to worry on low Continue reading
VMware NSX 101 – Components
Today I want to explain the basic components and the set-up of VMware NSX. In this case I’m referring to NSX for vSphere or NSX-V for short. I want to explain what components are involved, how you set them up for an initial deployment and what the requirements are.
Versioning
At time of this writing the latest release is NSX 6.1.4. This version added support for vSphere 6, although you cannot use any vSphere 6 feature in this release, there is support for the platform itself only.
vSphere
The first step is of course deploy your ESXi vSphere cluster with ESXi 5.5 or 6.0 with vCenter 5.5 or 6.0. I recommend using the vCenter Server Appliance (VCSA) instead of the Windows version. You will also need a Windows VM where the vSphere Update Manager is installed, this is not available as virtual appliance, only as Windows application. I also highly recommend installing an Active Directory server to manage all of your passwords. You will be installing a large amount of machines with all different usernames and possibly passwords. I recommend picking a very long and difficult one, as all VMware appliances seem to require Continue reading
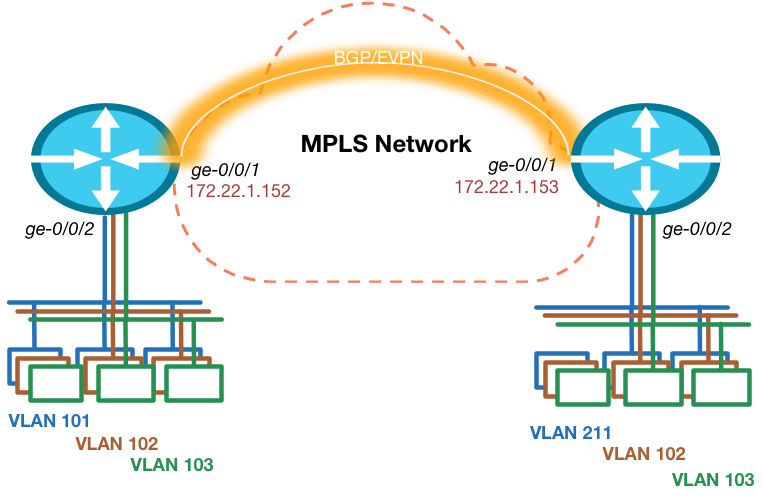
EVPN Configuration
In my last blog I explained the features and use cases of the EVPN technology. In this blog I want to show how easy it is to configure, enable and expand EVPN. The configuration is focused on the Juniper MX platform, but as Junos is the single operating system across the entire Juniper portfolio, configuration on other platforms (like EX9200) is equal.
Design
The topology is really simple. I’m using 2 routers in this example, so multi-homing is not in scope. Each router has an Ethernet segment connected that consists of multiple VLANs on each side. There is 1 VLAN ID that is not equal on both sides, so this has to be taken care of.
Prepare for EVPN
To make sure we can start creating our VPN, we have to ensure the foundation is in place. This means we need IP reachability to the other Data Center routers loopback address and we need BGP with the EVPN address family enabled. The Junos release I’m testing with needs a special knob to be enabled to ensure packet lookups are done in the right way. Other versions will see this knob disappear as it is default moving forward.
routing-options {
autonomous-system 64999;
forwarding-table {
Continue reading
EVPN (RFC 7432) Explained
EVPN or Ethernet VPN is a new standard that has finally been given an RFC number. Many vendors are already working on implementing this standard since the early draft versions and even before that Juniper already used the same technology in it’s Qfabric product. RFC 7432 was previously known as: draft-ietf-l2vpn-evpn.
The day I started at Juniper I saw the power of the EVPN technology which was already released in the MX and EX9200 product lines. I enabled the first customers in my region (Netherlands) to use it in their production environment.
EVPN is initially targeted as Data Center Interconnect technology, but is now deployed within Data Center Fabric networks as well to use within a DC. In this blog I will explain why to use it, how the features work and finally which Juniper products support it.
Why?
Data Center interconnects have historically been difficult to create, because of the nature of Layer 2 traffic and the limited capabilities to control and steer the traffic. When I have to interconnect a Data Center today I have a few options that often don’t scale well or are proprietary. Some examples:
- Dark Fiber
- xWDM circuit
- L2 service from a Service Provider
- VPLS
- Continue reading
Nested Virtualization
A typical Network Virtualization demo is difficult as you need quite some hypervisor hosts to run some VMs on and interconnect them using Overlays. I solve this using nested virtualization. This means that I run a hypervisor running on another. This gives me the flexibility that my physical nodes, or “hypervisor underlay” if you will, can scale easily and I’m independent of them.
My physical cluster consists of 2 nodes running ESXi with vCenter. On top of that I’m running 4 other ESXi hosts divided in 2 “virtual” clusters and 4 KVM hosts as Contrail Compute Nodes.
How does this work?
This technology works using Intel’s VT-x (which is hardware assisted virtualization) and EPT (to virtualise memory allocations). This combination works since the “Nehalem” arch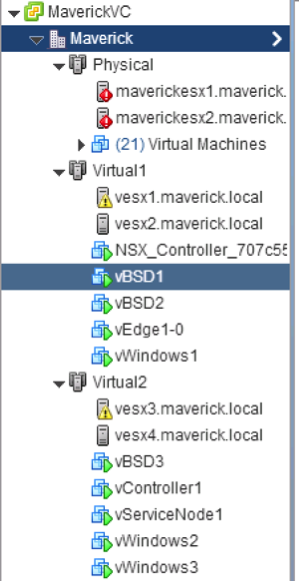 itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).
itecture (released 2008). The technology is ported to the more “Desktop” oriented CPU’s as well, so there is a good chance your notebook supports it as well. Since the Haswell architecture the nested virtualization works even better as Intel now supports VMCS Shadowing for nested VMs, which creates a data structure in memory per VM (and now supports nested VMs as well, which used to be a software effort).
Memory is the biggest burden in these Continue reading
Using the Junos Space REST API
Automation is going to be fundamental in all networking products. I’ve been working a lot on integrating Juniper products in existing and standard software. There are many different ways to automate something on a network running Junos. Using REST (or RESTful) APIs is one way of doing this. The reason I’m using REST is that it’s fairly easy to understand, but the best thing is that a large amount of existing products supports REST to integrate with it.
The goal of this blog is to explain how Junos products support REST, compatibility with older versions and how it scales.
What is REST?
REST (REpresentational State Transfer) is a simple stateless architecture that generally runs over HTTP. There are 4 commonly supported commands. When you issue a command your input data consists of a URL, HTTP headers and a body holding the data.
HTTP Headers are used for things like Authentication and a Content Type to let the application know what data format the body will contain.
The URL specifies which data you want to receive from the application or you want to change.
The body is empty in a request for data, when you want to change some data this Continue reading
Home Lab Server
Currently I’m doing a lot of testing at home on Network Virtualization solutions, like VMware NSX, Juniper Contrail, etc. Therefore I was stressing my current single home server quite a lot. Which is a custom build Xeon E3-1230 quad core with 32GB of RAM and 128GB SSD. I built this server according to the specifications found at: http://packetpushers.net/vmware-vcdx-lab-the-hardware/ . This has been a great investment as I’m running nested virtualization for both KVM and ESXi hypervisors and run the testing in there. Due to the fact that for a decent Network Virtualization (NV) set-up you need quite some memory, especially if you look at the memory utilisation of the NV Controller VMs, I had to expand my lab. I chose to extend it with an additional server so I would be physically redundant as well, making it easier to run upgrades on the physical machines.
Requirements
My requirements aren’t difficult as I mainly perform feature testing in my lab I don’t need a lot of CPU performance. There are no “Production” VMs running, everything is there to play around, so downtime is not a problem if necessary.
Other requirements:
- Average CPU performance
- Nested virtualization support
- At least 32GB of Continue reading
Passed CCIE Data Center!
After a number of months studying and final 2 weeks full 100% dedicated preparation I passed the CCIE Data Center Lab exam last week on April 25th in Brussels at first attempt!!!
This is my fourth CCIE title and I can honestly say that this is the title means a lot to me! Currently there are so few individuals who passed the CCIE Data Center lab and many have failed it already.
Preparation
What did I use for preparation?
IPexpert CCIE Data Center Workbook
Of course I used the CCIE Data Center Workbook from IPexpert for my preparation, because I wrote the book. After writing the labs for the past couple months I really had to re-do them all to get a feeling about the entire picture again. This has been an invaluable resource with labs that are a lot harder than the actual lab tasks!
Real life experience
In my work for a Cisco Gold Partner (Telindus) I did a lot of projects with Nexus 7000, Nexus 5000, Nexus 2000, MDS switches and a ton of UCS systems. This is where I found that I learned most of the knowledge that was required for the test.
Focus Focus Focus!
What about 2013?
Happy new year to you all! I truly hope that all your dreams for 2013 may come true and maybe even more.
For the first time I didn’t really made a to-do list for 2013, but in my head I’m still working on things I want to have accomplished by the end of the year. I wanted to discuss in short a few of those topics.
House
Just at the end of December I bought a house in Utrecht, Netherlands. This is going to fill up a lot of time for me in 2013, where I literally need to buy everything and arrange a lot of things.
Of course the fun part of designing my home network, automating my house as much as possible and designing my little office if already in progress :)
CCIE Data Center
The CCIE Data Center is also taking up a lot of time in 2013. Besides that I’m studying to pursue the title myself. I’m also writing the CCIE Data Center Lab Workbook for IPexpert. This is an amazing opportunity and I really love to work on it. I really hope you like using it when you purchase. Otherwise I’m more than happy to Continue reading
Cisco Live 2012 San Diego
That was it! My work life has an absolute peak every year and that’s when I’m again fortunate enough to visit Cisco Live in the US. This year it was held in San Diego, California.
I flew in on Saturday with 2 colleagues on LA and drove to San Diego after a quick tour around Sunset Boulevard ;)
We stayed at the Manchester Grand Hyatt, which is a hotel I can truly recommend when visiting San Diego. Services were good and staff was helpful!
My focus this year was to combine both Datacenter and Service Provider sessions as those are the fields I’m active in. I found that the SP related sessions had a quite smaller crowd attending them. I guess this is related as the SP customers are considered important customers and get a lot more attention from Cisco people, so they already know what to expect in terms of roadmap and technologies. Still I had quite some very good sessions where I learnt about the features (and limitations) about some cool new things :-)
Sunday
On Sunday it’s a special day as you need to purchase additional sessions called Techtorials. This was the first year I took a Continue reading
CCIE Datacenter techtorial notes
The CCIE Datacenter techtorial was a very good session giving a good overview about the contents of the exam. I will not focus on the technologies in this article, but only on the specifics that I wrote down during the session. This means you will only find details about the exam and not about the technologies.
There are enough resources to find details about the technologies, but you are reading this article if you want to know what to find when you step into the testing center or the lab.
The session was presented by 3 guys, I would specifically mention Walid Issa who is the product manager for this particular CCIE track. Walid is a very nice guy and if you want to know something about the lab, ask him!
Written
Over 200 took the written beta already. it’s expected that a lot more people will take the DC written beta during Cisco live San Diego.
The Written is an overview of technologies with a medium to hard level. As all other written exams for CCIE the focus is on theory and not on configuration. When you know the technologies you should be able to pass.
Lab
Sample topology Continue reading