Network Modeling: Segmented Lab access with Containerlab and ZeroTier
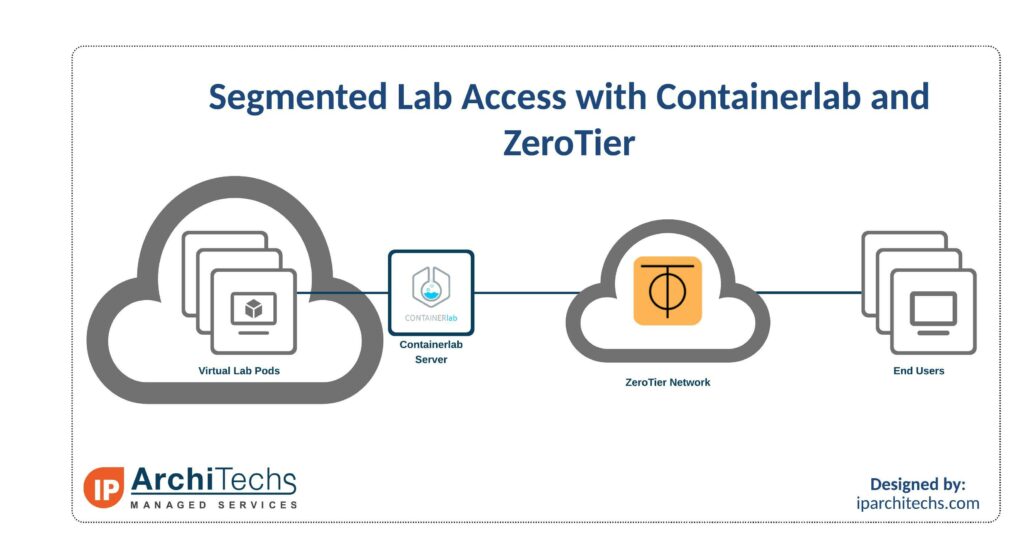
Introduction
When building out network labs, often multiple people will need access to the lab. The main way right now is to use something like EVE-NG or GNS3 to provide access.
There are 2 downsides to this method. The first is that your server is exposed to the internet and if your usernames/passwords aren’t strong enough, your server can become compromised. The second is that sometimes you may not want everyone to be able to add or edit to the lab topology.
The solution to this is using Containerlab and ZeroTier. This setup is great for things like testing new hires, training classes, or for providing lab access to others on a limited basis.
What is Containerlab?
Containerlab is a container orchestrating tool for managing container-based networking labs. It doesn’t just support Container based Network Operating Systems though. Through vrnetlab, there is support for a wide variety of commonly used NOSes: Mikrotik RouterOS, Nokia SROS, Juniper vMX and vQFX, and many more.
Configs are text based making it easy to add/update links between nodes. The lab does need to be destroyed and redeployed when adding/removing links. With some tools to generate configs, it’s easy to spin up a 500+ node Continue reading
Migrating from fabricpath to EVPN/VxLAN
Introduction
Do you have a 3 tier, switched, or vendor proprietary data center design?
Does it rely on spanning tree or proprietary solutions to eliminate spanning tree?
Not sure how to migrate to a new architecture without serious downtime?
If you answered yes to any of these questions then this post is for you. We’ll be looking at deploying an EVPN/VxLAN Data Center fabric and migrating a from a cisco fabricpath environment to the new design.
Although we will be focusing on a fabricpath migration many, if not all, of the principles apply to migrating a 3 tier architecture.
1. Building the new Data Center Fabric
2. Connecting the current fabricpath and new fabric
3. Migrating switched virtual interfaces
4. Migrating various types of physical devices
Building the new Data Center Fabric
The easiest part of designing and building the new fabric is the physical topology. This should be a symmetric topology to easily take advantage of equal cost multipath and add additional switches with ease. This is also known as a spine/leaf or clos topology. The basic idea is leafs connect to spines and spines connect to super spines. A leaf/spine should not connect to another switch of the Continue reading
ISP Design Guide: Separation of network functions – introduction and overview

PDF link is here
A reference guide for new & existing ISPs that need to understand network functions and separation.
“How do I add redundancy?”
“How do I scale?”
“How do I reduce downtime and operational costs?”
These are questions that I get asked practically every day as a consulting network architect that designs and builds ISPs.
In most cases the answer is the same whether the ISP uses fixed wireless broadband, copper or fiber to deliver the last mile – separation of network functions.
This illustrated guide is intended to define the topic and create visual context for each function using a network drawing. It’s the first in a new series on this subject.
A new series of content
This topic is deep and there is a lot to unpack so this will be the first segment in a series of blog posts and videos covering function separation.
Large ISPs typically already embrace the philosophy of separating network functions, so the focus of this series will be to help new or growing regional ISPs understand the design intent and the challenges/costs of running networks that don’t separate network functions.

http://iparchitechs.com/contact
Utilizing BGP Communities for traffic steering – part 1: Firewalls
Overview:
I typically spend more time in the enterprise data center than most of our team members and this comes with its own unique set of problems. One discussion that seems to never fail to come up is “where do I put the Firewalls (FWs)?”. That is typically followed by I have a disaster recovery or backup site with FWs there as well. This inevitably leads to a state management problem. Let’s look at how we can utilize BGP to address this problem:
- what is a BGP standard community
- BGP best path selection process
- how to utilize them to steer traffic
This is something most service providers deal with on a daily basis but can be new to an enterprise.
BGP Standard communities
A BGP community is a route attribute that, essentially provides extra information for someone to take action or glean information from the route such as where it came from (location, type, organizational role).
By definition, a community is a 32 bit number that can be included with a route and when utilizing the new community format is displayed as (0-65535):(0-65535). It is recommend to utilize the new community format versus the old community format which is Continue reading
MikroTik – RouterOSv7 first look – feedback on routing filters
Overview
Routing filters have been a hot topic lately in the world of RouterOSv7. The first implementation of routing filters in ROSv7 was difficult to work with and documented in the two articles below:
MikroTik – RouterOSv7 first look – Dynamic routing with IPv6 and OSPFv3/BGP
MikroTik RouterOS – v7.0.3 stable (chateau) and status of general release
MikroTik then made some changes and opened up discussion to get feedback. I did a lot of work and testing using ROS 7.1beta7 which never made it to public release and was close to publishing the results when 7.1rc1 came out so this post will use that version.
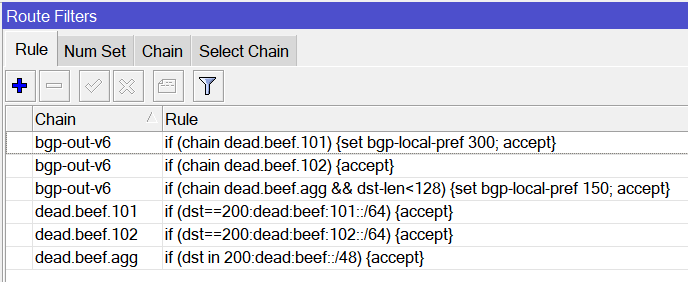
RouterOSv7.1rc1 syntax example
Here is an example of the latest syntax in ROSv7.1rc1
CLI
### MikroTik RouterOS 7.1rc1 ###
/routing filter rule
add chain=dead.beef.101 rule="if (dst==200:dead:beef:101::/64) {accept}"
add chain=dead.beef.102 rule="if (dst==200:dead:beef:102::/64) {accept}"
add chain=dead.beef.agg rule="if (dst in 200:dead:beef::/48) {accept}"
add chain=bgp-out-v6 rule="if (chain dead.beef.101) {set bgp-local-pref 300; accept}"
add chain=bgp-out-v6 rule="if (chain dead.beef.102) {accept}"
add chain=bgp-out-v6 rule="if (chain dead.beef.agg && dst-len<128) {set bgp-local-pref 150; accept}"Winbox
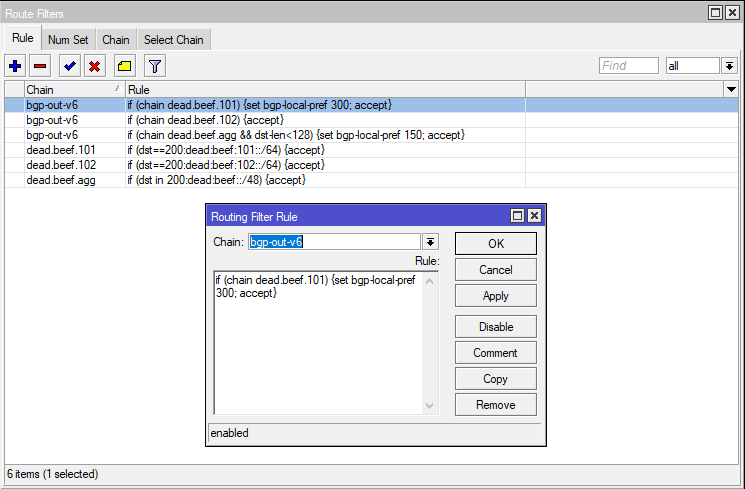
And the corresponding routes received Continue reading
WISP cheat sheet for MPLS/VPLS MTU
A guide for working with MTU and MPLS in a Wireless ISP
MPLS/VPLS MTU math can be complicated and is always a struggle to unravel.
To make it a little easier and put it into a WISP context, I designed this cheat sheet on 8.5 x 11 (to print for those that actually trust printers) and used common WISP equipment like MikroTik routers, Ubnt and Cambium radios with real world MTU values.
The MTU values are displayed in layers to make it easier to see where each value fits.
PDF is here

A starting point
These values are meant to be a starting point by representing the minimum values required for MPLS/VPLS with a single 802.1q VLAN tag.
In general, after going through hundreds of WISP migrations, I’ve found it to be easier to implement the minimum values required when working on a production WISP to identify the effective lowest MTU in the network.
Once the network equipment has been modified and has been running in a stable way on the minimum values, then higher values can be considered and implemented (now that the effective lowest MTU on the network is documented)

Let’s talk MPLS-VPLS, part 1 – use cases
Hey guys, today we’ll be taking a look at what are the main reasons that MPLS – and in particular VPLS – is a useful technology tool to get traffic from point A to point Z. There’s really 2 major use cases that I deal with regularly: IPv4 conservation and L2VPN.
Why am I talking about VPLS specifically? Well, mostly because many times I end up working with Mikrotik routers, which only support VPLS. What is VPLS? It stands for Virtual Private Line Service, and it’s a way to deliver layer 2 services over a layer 3 network. Said another way, it connects a single broadcast domain to multiple endpoints across a routed network. I’ll discuss why MPLS is better for you and your network than switching/bridging in part 2 of this series – for now just know that MPLS/VPLS will allow you to offer enhanced services without the risks of extending layer 2 (I’ll talk more about that below, and why that’s bad in part 2, also).
Use case 1: IPv4 Conservation
OK, so let’s visualize the problem with IP conservation on a small /24 allocation.

If you’re like most other service providers, you have a Continue reading
MikroTik RouterOS – v7.0.3 stable (chateau) and status of general release
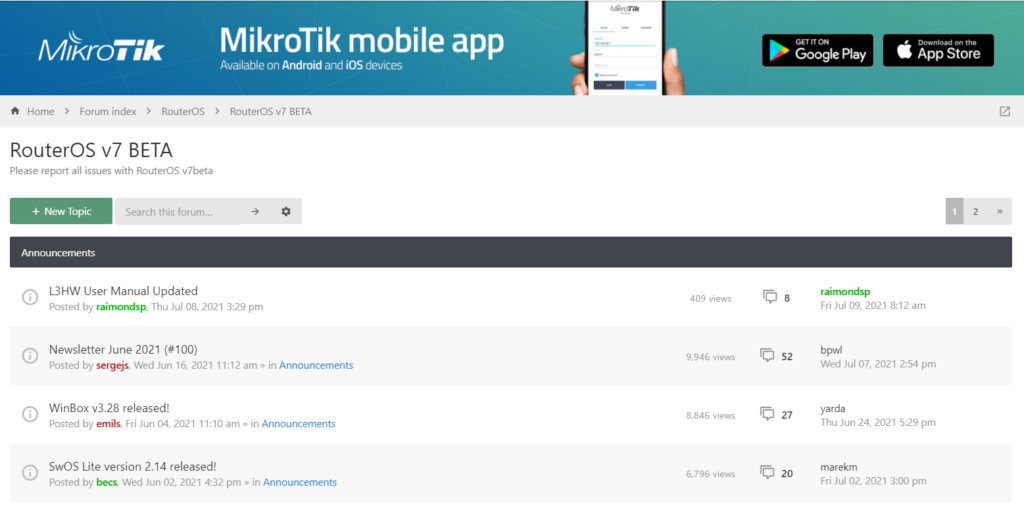
If you don’t already use it, the MIkroTik v7 BETA forum (forum.mikrotik.com) is a fantastic source of information
When will stable be released?
This is the million dollar question. Technically, it already has been for one hardware platform…
!! Spoiler Alert – There is *already* a stable release of ROSv7 – v7.0.3!!
The Chateau 5G router originally shipped with a beta version of ROSv7 but was quietly moved to a stable version that’s developed specifically for that platform.

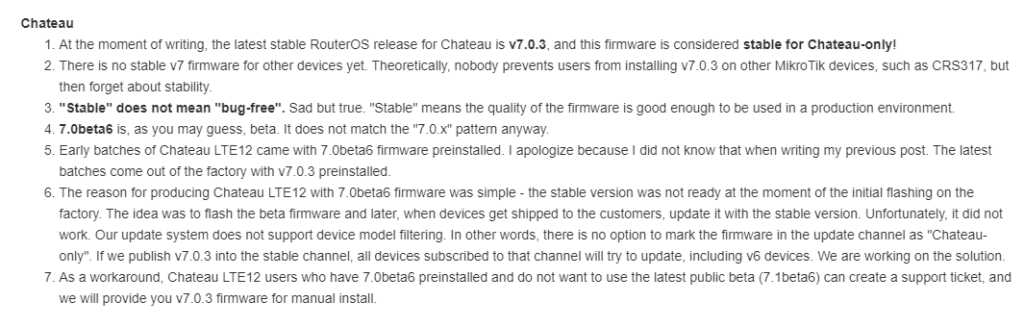
Because of the way MikroTik’s code repo works, this version can’t easily be added to the main download page and support provides the software:
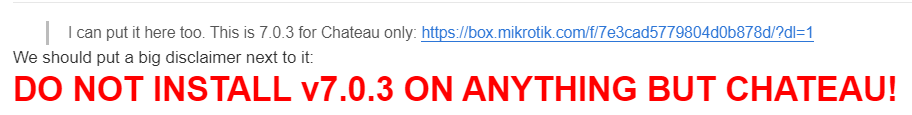
ROSv7.0.3 Stable Download (!!! Chateau Only – will brick other hardware !!!)
https://box.mikrotik.com/f/7e3cad5779804d0b878d/?dl=1
It’s worth repeating MikroTik’s warning about using this on any platform other than the Chateau

What’s holding up v7 from being released?
If you’ve been around MikroTik for a while, then you know that version 7 has been in the works for a long time to add new functionality and address limitations of the older Linux kernel in ROSv6.
MikroTik recently Continue reading
MikroTik – RouterOSv7 first look – MLAG on CRS 3xx switches
What is MLAG?
Multi-Chassis Link Aggregation Group or MLAG is an idea that’s been around for a while.
It allows for the ability to form LACP channels across multiple physical switches.
Wikipedia shows a few different topology examples here
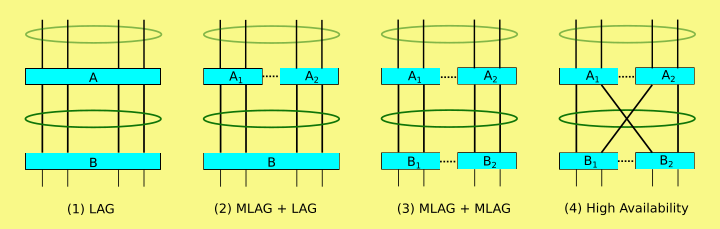
Vendor implementations are proprietary but the idea of MLAG was first mentioned in 802.1AX-2008 in 2008.
It first started to become popular in data center networking in the late 2000s
What makes the addition of MLAG to MikroTik’s RouterOS feature set notable is that it lowers the barrier to entry for this particular feature.
CRS 3xx switches are very inexpensive (starting at $149 USD) and may very well be the lowest cost MLAG capable hardware available on the market.

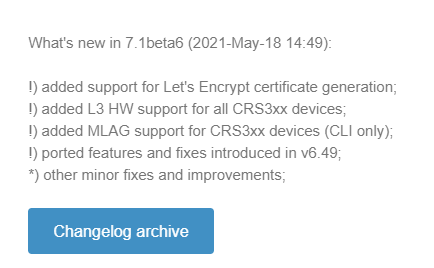
Introduced in 7.1beta6
MLAG has been asked for by the MikroTik community a number of times and the most active feature request thread started here in 2020:
new feature request MLAG!!! – MikroTik
MikroTik added several version 7 beta releases in 2021 and included MLAG for all CRS 3xx series switches in 7.1beta6 on May 18th, 2021.
Overview of protocol requirements
MLAG is fairly consistent across vendors with the need Continue reading
MikroTik CRS404-96s-8q-rm
Moving into Chassis form factors
We are starting to see some larger footprints, speeds and power consumption from MikroTik and have a copy of the latest data sheet for the recently announced CRS404-96s-8q-rm switch
Data Sheet:
https://iparchitechs-my.sharepoint.com/:b:/p/kevin_myers/ERl4kYo6cOZPnFXKB9SRLgoBY0WGxbrH91OrWBNe9fIDFw?e=EnFYTZ

#AprilFools2021 
Juniper to Mikrotik – MPLS Commands
About the Juniper to MikroTik series
In the world of network engineering, learning a new syntax for a NOS can be daunting if you need a specific config quickly. Juniper is a popular option for service providers/data centers and is widely deployed across the world.
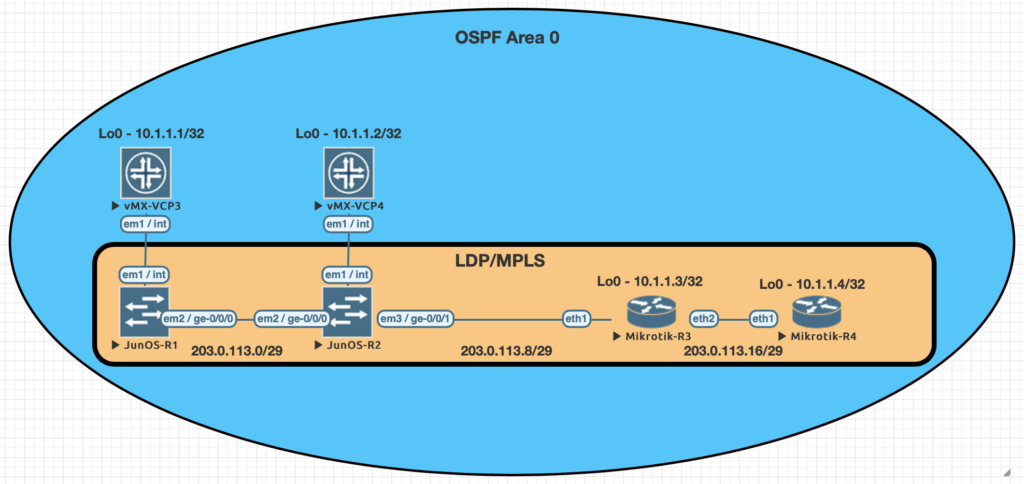
This is a continuation of the Rosetta stone for network operating systems series. In this article we will be covering multi-protocol label switching (MPLS) using label distribution protocol (LDP). We are sticking with LDP as MikroTik does not have wide support for RSVP-TE.
You can find the first two articles of the series here:
Juniper to MikroTik – BGP commands
Juniper to MikroTik – OSPF commands
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Using EVE-NG for testing
We conducted utilized EVE-NG for all of the testing with the topology seen below.
| Juniper Command | MikroTik Command |
|---|---|
| show ldp neighbor | mpls ldp neighbor print |
| show ldp interface | mpls ldp interface print |
| show route forwarding-table family mpls | mpls forwarding-table print |
| show ldp database | mpls Continue reading |
Juniper To MikroTik – OSPF Commands
About the Juniper to MikroTik Series
In the world of network engineering, learning a new syntax for a NOS can be daunting if you need a specific config quickly. Juniper is a popular option for service providers/data centers and is widely deployed across the world.
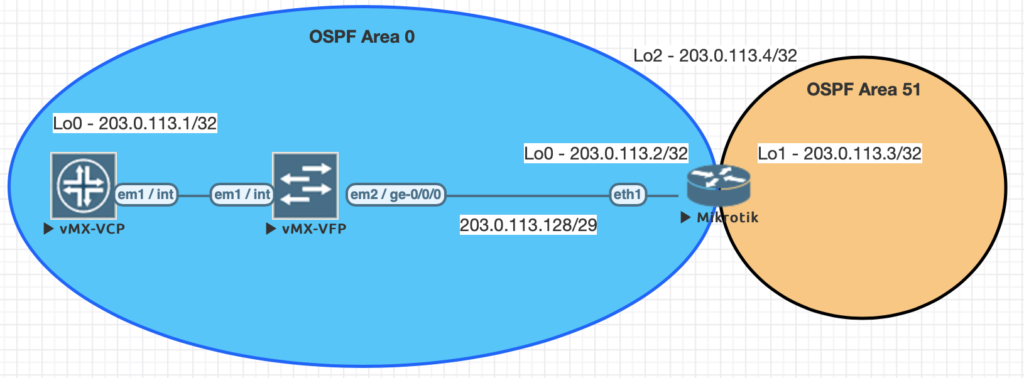
This is a continuation of the Rosetta stone for network operating systems series. In this portion of the series we will be covering Open Shortest Path First, OSPF, version 2 which is a popular interior gateway protocol (IGP).
You can find the first article of the series Juniper to Mikrotik – BGP Commands here.
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Using EVE-NG for testing
We conducted all testing on EVE-NG utilizing the topology seen below.
| JunOS Command | MikroTik Command |
|---|---|
| show ospf neighbor | routing ospf neighbor print |
| show ospf interface | routing ospf interface print |
| show ospf overview brief | routing ospf instance print detail |
| show ospf database | routing ospf lsa print |
| show route protocol ospf | ip route print where ospf=yes |
| show Continue reading |
Juniper to MikroTik – BGP commands
About the Juniper to MikroTik series
In the world of network engineering, learning a new syntax for a NOS can be daunting if you need a specific config quickly. Juniper is a popular option for service providers/data centers and is widely deployed across the world.
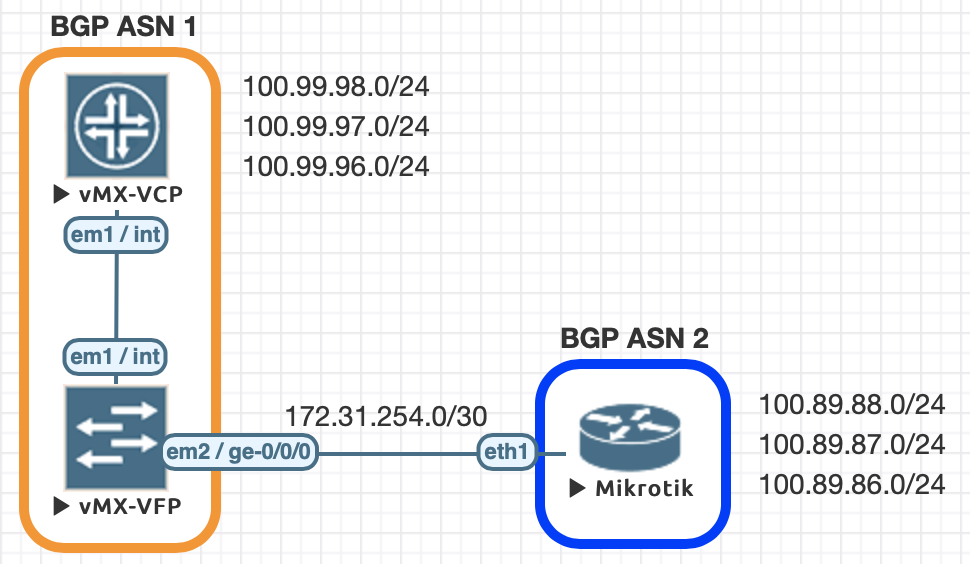
This is a continuation of the Rosetta stone for network operating systems series. We’ll be working through several protocols over series of posts to help you quickly move between different environments.
While many commands have almost the exact same information, others are as close as possible. Since there isn’t always an exact match, sometimes you may have to run two or three commands to get the information needed.
Using EVE-NG for testing
We conducted all of this testing utilizing EVE-NG and the topology seen below.
| Juniper Command | MikroTik Command |
|---|---|
| show bgp summary | routing bgp peer print brief |
| show bgp neighbor | routing bgp peer print status |
| show route advertising-protocol bgp 172.31.254.2 | routing bgp advertisements print peer=peer_name |
| show route receive-protocol bgp 172.31.254.2 | ip route print where received-from=peer_name |
| show route protocol bgp | ip route print where bgp=yes |
| clear bgp neighbor 172.31.254.2 soft-inbound | Continue reading |
MikroTik – RouterOSv7 first look – Dynamic routing with IPv6 and OSPFv3/BGP
If you missed it, take a look at MikroTik’s video on RouterOS v7 routing performance and changes.
Overview
One of the long awaited benefits of RouterOS version 7 is a new routing protocol stack that enables new capabilities and fixes limitations in RouterOSv6 caused by the use of a very old Linux kernel.
The new routing stack in v7 has created quite a buzz in the MikroTik community as lab tests have shown that it’s significantly more efficient in processing large numbers of BGP routes.
The ability to use MikroTik’s new generation of CCR routers with ARM64 to quickly process BGP routes is a blog post all to itself and we’ll tackle that in the future – however, the information below provides a quick look into the performance comparison between ROS v6 and v7.
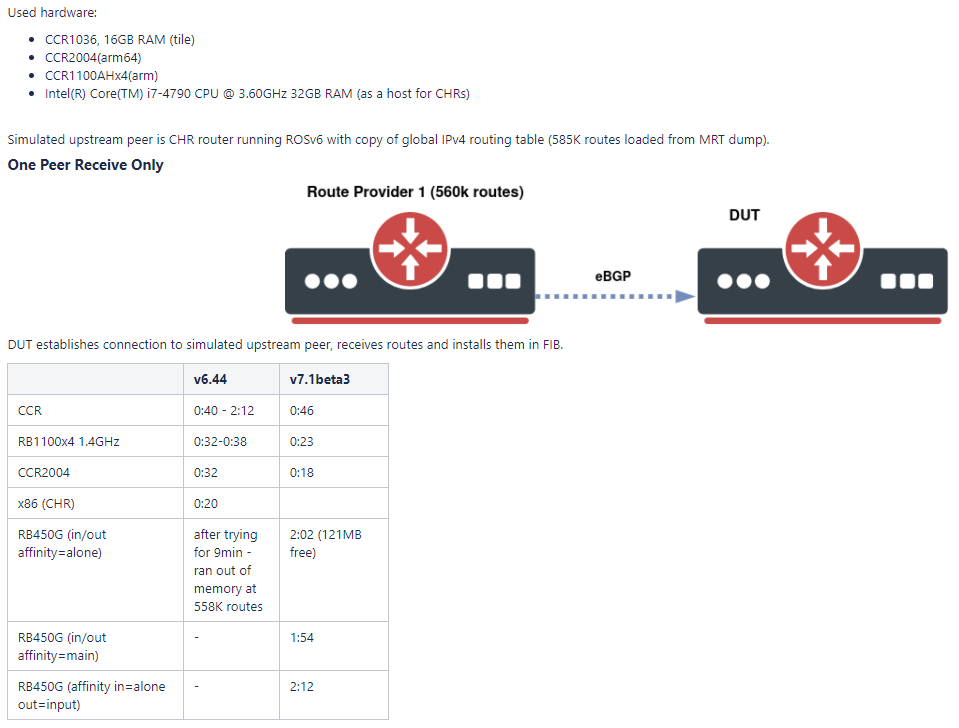
The new routing stack also paves the way to add a number of features that have been needed for a long time like RPKI and large community support.
Using a lab based on EVE-NG, we’ll take a look at configuration changes and iBGP using the IPv6 AFI with OSPFv3 as the IGP for loopback/next hop reachability. Prior to 7.1beta2, this has been nonfunctional for years Continue reading
MikroTik – RouterOSv7 first look – L3 ASIC performance testing

When MikroTik announced the CRS3xx series switches a few years ago, one of the most exciting aspects of that news release was the prospect of L3 forwarding in hardware on very inexpensive devices.
A quick review of the Marvell Prestera ASIC family showed a number of advanced routing, switching, MPLS and VxLAN capabilites.
Fast forward to 2020, where MikroTik has started to enable some of those features in RouterOS v7 beta.
Now we can finally take some of the CRS3xx switches and test their capabilities with L3 forwarding performance in hardware
CRS 3xx series capabilities overview
Before getting into the testing, it’s probably helpful to review some of the basic specs and capabilities of the CRS3xx switch line.
Here is a chart from MikroTik that outlines ACL rule count, Unicast FDB entries and MTU size.
CRS 3xx model comparison

MIkroTik has been working on the development of the features listed below to offload into hardware.
For the tests in this article, we’ll be using IPv4 Unicast and Inter-VLAN routing.
Supported feature list

Currently, the following switches are supported.
For the testing in this article, we are using the CRS317-1G-16S+
Switches supported by 7.1beta2


Performance testing – overview
The physical Continue reading
Conference Preview: WISP Virtual Summit 2020

It seems like ages ago that we blocked out time in our schedules to fly to technical conferences and immerse ourselves with great people and content for an entire week.
In reality, it’s only been a few months but 2020 has made it seem like a lifetime.
However, those of us in tech are quick to adapt and virtual conferences are now a thing.
For the fixed wireless industry, in-person conferences are critical because most of the attendees are entrepreneurs.
For a small business owner in tech, going to a show is one of the best ways to evaluate content and business opportunities needed to stay competitive in a short amount of time.
The first virtual conference for Wireless ISPs

Thankfully, due to some amazing effort and collaboration in the WISP industry led by Preseem and supported by WISPA, we are about to kick off the first virtual conference for the fixed wireless industry on July 28th, 2020.
An enormous amount of work has gone into planning and preparation to replicate the experience of an in-person technical conference as much as possible.
First thing’s first….get registered
Kick off the registration process by visiting: https://wispvirtualsummit2020. Continue reading
Remote workers – rapid and cost-effective VPN scale with ZeroTier, OPNSense and FRRouting.
Overview
This would probably be a relevant topic on any given day in the world of IT, but given the current global pandemic due to COVID-19 (aka coronavirus), it’s become especially important.
IT departments are scrambling to figure out how to react with capacity to connect entire companies remotely for extended periods of time.
With a traditional vendor solution that centers around a router or firewall that’s racked in a data center somewhere, this can be difficult to solve for a few reasons.
Challenges:
- Hardware capacity – most firewalls or routers have a fixed capacity for VPN sessions that must be deployed into a cluster to scale.
- Software licensing – taking a company of thousands and suddenly extending licensing to account for the entire company is a financial hurdle for most companies.
- Time to deploy – assuming both hardware and software licensing challenges can be dealt with in a timely manner, it may take weeks or months to deploy the additional capacity.
Luckily, IT is much more focused on software and cloud solutions these days then putting out boxes for everything.
Open source and cloud solutions when used together can provide an incredible amount of scale and performance without a Continue reading
Starting a WISP: guide to selecting a routing architecture

Understanding the choices – why is routing design so important?
Routing is the foundation of every IP network. Even a router as small as the one in your home has a routing table and makes routing decisions.
Selecting a routing architecture is a critical but often overlooked step to ensure that a startup WISP can provide the necessary performance, scalability and resiliency to its subscribers.
This post will go through each the major design types and highlight pros/cons and when it is appropriate to use a particular routing architecture.
A note on IPv6
Dual stack is assumed in all of the designs presented. The cost of IPv4 public will continue to climb.
It’s no longer a scalable option in 2020 to build an ISP network without at least a plan for IPv6 and ideally a production implementation.
1. Flat network (aka bridged network)
“Behind the L3 boundary, there be L2 dragons”
-ancient network proverb
Unfortunately, this is often the worst choice for all but the smallest WISPs that don’t have any plans to scale beyond 1 to 100 subscribers.
Bridged networks with one or more subnets in the same L2 broadcast domain are the most commonly deployed routing design that Continue reading
MikroTik – RouterOSv7 first look – VxLAN
VxLAN support added in 7.0beta5
MikroTik announced VxLAN support on Valentine’s Day (Feb 14th) of 2020.
This is a significant feature addition for RouterOSv7 as it will pave the way for a number of other additions like EVPN in BGP.
It will also give MikroTik the ability to appeal to enterprises and data centers that might need cost-effective VxLAN capable devices.
Service Providers are also moving towards VxLAN as a future replacement for VPLS so this is helpful for that market as well.
Download the OVA here:
https://download.mikrotik.com/routeros/7.0beta5/chr-7.0beta5.ova
Implementation
The initial release of VxLAN is based on unicast and multicast to deliver Layer 2 frames.
As there is no EVPN support, the VTEPs must be manually configured for each endpoint in a full mesh configuration.
The VxLAN interface can then be bridged to a physical ethernet port or VLAN interface to deliver the traffic to the end host.
Lab Example
Here is an overview lab in EVE-NG with a basic setup using 3 linux servers on the same 10.1.1.0/24 subnet which is carried as an overlay by VxLAN.
VxLAN reachability for VTEPs is acheived with OSPFv2 and loopback addresses.
VNI: 100
Continue reading
Juniper to MikroTik – MPLS and VPNv4 interop

Juniper to MikroTik – a new series
Previously, I’ve written a number of articles that compared syntax between Cisco and MikroTik and have received some great feedback on them.
As such, I decided to begin a series on Juniper to MikroTik starting with MPLS and L3VPN interop as it related to a project I was working on last year.
In the world of network engineering, learning a new syntax for a NOS can be overwhelming if you need a specific set of config in a short timeframe. The command structure for RouterOS can be a bit challenging if you are used to Juniper CLI commands.
If you’ve worked with Juniper gear and are comfortable with how to deploy that vendor, it is helpful to draw comparisons between the commands, especially if you are trying to build a network with a MikroTik and Juniper router.
Lab Overview
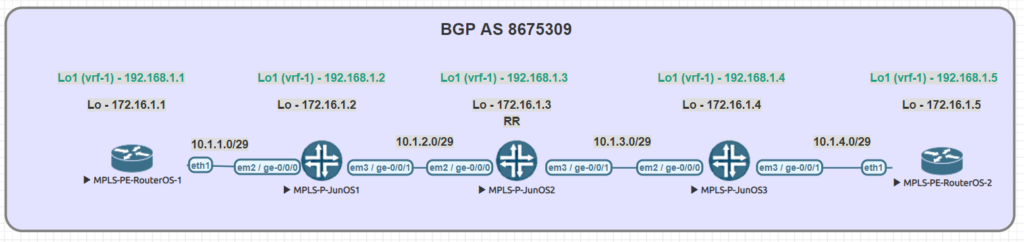
The lab consists of (3) Juniper P routers and (2) MikroTik PE routers. Although we did not get into L3VPN in this particular lab, the layout is the same.
A note on route-targets
It seems that the format of the route-target has some bearing on this being successful. Normally i’ll use a format like Continue reading

