Case study: Calico helps Upwork migrate legacy system to Kubernetes on AWS and enforce zero-trust security
Upwork is a freelancing platform that connects a global base of clients to freelancers via job postings. Since going public on the New York Stock Exchange in 2019, the company has become one of the leading freelance platforms worldwide and was named on Time’s list of the 100 Most Influential Companies of 2022.
Upwork’s platform team was running containerized workloads on Consul and Spring Cloud, which required service owners to manually switch to a new code library each time Upwork’s platform team had a new release, and vice versa. This manual switching happened as often as every two months, which was inefficient for a company with over 800 microservices. Also, service owners were not adopting new libraries immediately and could not add upstream and downstream dependencies as needed without going through a review process. Combined, these problems meant that service owners and the cloud engineering and InfoSec teams lacked visibility, were highly susceptible to zero-day attacks and had a slow incident mitigation response.
To solve these problems, Upwork needed to adopt a distributed architecture from the application layer to the network layer. To do this, they required Kubernetes. The switch to Kubernetes meant Upwork’s containers needed to adhere to cloud-native Continue reading
How to secure Kubernetes workloads using Calico DNS Security Policy
In my previous blog on Kubernetes security foundations, we discussed the growing adoption of cloud-native applications and the security challenges they present. We highlighted the limitations of traditional network firewalls in securing these applications and emphasized the importance of implementing cloud-native security policies to protect network traffic effectively.
In this blog, we will focus on one specific aspect of network security: securing egress traffic from microservices based on fully qualified domain names (FQDNs). Protecting egress traffic is crucial for ensuring the integrity and privacy of data leaving the microservices.
We will explore the challenges associated with safeguarding microservices egress traffic to destinations outside the cluster and discuss how Calico DNS logging and DNS policy can address these challenges. DNS logging allows for the collection and analysis of DNS queries made by microservices, providing valuable insights into their communication patterns and potential security risks. DNS policy enables the enforcement of granular access controls on domain names located outside the cluster, allowing only authorized requests and preventing malicious activities.
By implementing Calico DNS logging and DNS policy, organizations can gain better visibility into their microservices’ egress traffic, detect anomalies or security breaches, and establish stricter controls to protect their valuable data. This Continue reading
Case study: Calico enables HanseMerkur to reduce infrastructure overhead and achieve ISO 27001 compliance
Established in 1875, HanseMerkur is one of the oldest private health insurance companies in Germany, with customers across Europe. The company ran multi-tenant clusters on premises with Kubespray, with around 150 internal software developers as users. As the company must handle personal information and confidential data, it adheres to ISO 27001, the German equivalent of SOC 2, as per industry standards.
The company’s legacy platform was based on Kubernetes 1.11 (released in 2018), and no updates could be made without completely rebuilding the platform. In fact, the company needed to build new clusters for each new product and also rebuild the existing clusters in order to update Kubernetes versions.
HanseMerkur’s clusters were virtualized on top of a legacy hypervisor, and resources had to be sized for traditional deployment on a per tenant basis. There were a number of issues with this set up, including high overhead, low flexibility, and over-consumption of hardware. As a result, the company’s platform team wanted to go bare metal and consolidate the company’s entire infrastructure into one place.
In an exclusive interview, HanseMerkur details how Calico helped solve the challenges of their consolidation project and helped the company enforce the security and observability capabilities Continue reading
Secure egress access with DNS Policy and NetworkSets
One of the common concerns about migrating applications to Kubernetes is the control over the network traffic egressing your environment. Due to its highly dynamic architecture, Kubernetes will not tie a specific IP address to an application by default. Instead, it will lease a different IP address from an IP pool whenever the application restarts.
Suppose you use traditional network security appliances like firewalls to provide network perimeter protection. In this case, enforcing the least privilege principle by allowing only a specific application to egress traffic outside your network is impossible. In a firewall configuration, you must specify the application IP address when creating the egress rule. As it is impossible to determine the application IP address, you must allow access to the nodes’ IP addresses if you are using overlay, or to the entire IP range you use in the IP pool. By doing this, you will also allow access to any application running on that Kubernetes cluster.
Learn more: Kubernetes Network Policy: Code Example and Best Practices
A better option would be to use Kubernetes network policies, which enable you to create rules to allow ingress and egress traffic to a workload based on the labels applied to Continue reading
Technical Blog: What you can’t do with Kubernetes network policies (unless you use Calico): TLS Encryption
Kubernetes documentation clearly defines what use cases you can achieve using Kubernetes network policies and what you can’t. You are probably familiar with the scope of network policies and how to use them to secure your workload from undesirable connections. Although it is possible to cover the basics with Kubernetes native network policies, there is a list of use cases that you cannot implement by just using these policies. You can refer to the Kubernetes documentation to review the list of “What you can’t do with network policies (at least, not yet)”.
Here are some of the use cases that you cannot implement using only the native Kubernetes network policy API (transcribed from the Kubernetes documentation):
- Forcing internal cluster traffic to go through a common gateway.
- Anything TLS related.
- Node specific policies.
- Creation or management of “Policy requests” that are fulfilled by a third party.
- Default policies which are applied to all namespaces or pods.
- Advanced policy querying and reachability tooling.
- The ability to log network security events.
- The ability to explicitly deny policies.
- The ability to prevent loopback or incoming host traffic (Pods cannot currently block localhost access, nor do they have the ability to block access Continue reading
How to secure the cluster in an air gap environment with Calico Cloud
The concern about securing the clusters has grown exponentially and one of the ways to secure it is by isolating the cluster from the Internet to lower the risk of eventual attack. Enterprises that deal with confidential customer data and work with regulatory agencies, such as financial and insurance institutions, require air gap environments for their clusters to create highly secure environments.
What’s an air gap?
The air gap is a security configuration in which the cluster, network, or workload will not have access to the Internet, unless it is explicitly authorized to do so. It is a highly controlled environment and prevents the cluster from establishing external connections without prior authorizations.
The diagram below shows an air gap network:
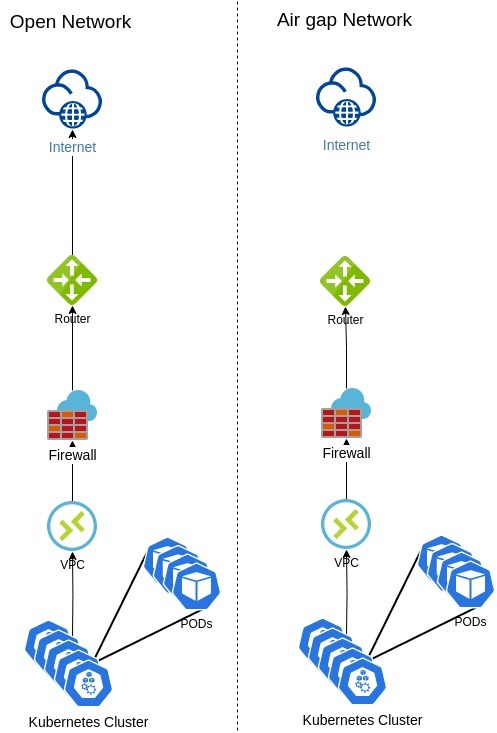
In a containerized environment, the cluster needs to pull the images for spinning up containers and it is usually done by pulling the images from a repository located on the cloud or Internet. However, as the air gap network doesn’t have access to the Internet, pulling images from the Internet is not possible. To address this situation, it is necessary to create a private registry/repository in the air gap network and pull all required images for the cluster into Continue reading
Case study: Calico enables zero-trust security and policy automation at scale in a multi-cluster environment for Box
Box is a content cloud that helps organizations securely manage their entire content lifecycle from anywhere in the world, powering over 67% of Fortune 500 businesses. As a cloud-first SaaS, the company provides customers with an all-in-one content solution within a highly secure infrastructure, where organizations can work on any content, from projects and contracts to Federal Risk and Authorization Management Program (FedRAMP)-related content.
Box has two types of operations: cloud-managed Kubernetes clusters in hybrid, multi-cloud, and public cloud environments, and self-managed Kubernetes clusters in co-located data centers. The company runs multiple clusters with sizes of 1,000 nodes and larger. As one of the early adopters of Kubernetes, Box began using Kubernetes much before Google Kubernetes Engine (GKE) or Amazon’s Elastic Kubernetes Services (EKS) was born, and has been on the leading edge of innovation for Kubernetes in areas such as security, observability, and automation.
In collaboration with Tigera, Box shares how Calico helped the company achieve zero-trust security and policy automation at scale in a multi-cluster environment.
ICYMI: Watch this recording from the 2022 CalicoCon Cloud Native Security Summit, where Tapas Kumar Mohapatra of Box shares how Box moved into automated dependency mapping and policy generation with API Continue reading
DNS observability and troubleshooting for Kubernetes and containers with Calico
In Kubernetes, the Domain Name System (DNS) plays a crucial role in enabling service discovery for pods to locate and communicate with other services within the cluster. This function is essential for managing the dynamic nature of Kubernetes environments and ensuring that applications can operate seamlessly. For organizations migrating their workloads to Kubernetes, it’s also important to establish connectivity with services outside the cluster. To accomplish this, DNS is also used to resolve external service names to their corresponding IP addresses. The DNS functionality in Kubernetes is typically implemented using a set of core-dns pods that are exposed as a service called kube-dns. The DNS resolvers for workload pods are automatically configured to forward queries to the kube-dns service.
The output below shows the implementation of the kube-dns services in a Kubernetes cluster.
kubectl get service kube-dns -n kube-system NAME TYPE CLUSTER-IP EXTERNAL-IP PORT(S) kube-dns ClusterIP 10.0.0.10 <none> 53/UDP,53/TCP
The core-dns pods have to rely on external DNS servers to perform domain name resolution for services outside the cluster. By default, the pods are configured to forward DNS queries to the DNS server configured in the underlying host in the /etc/resolv.conf file. The output below displays Continue reading
Visualizing service connectivity, dependencies, and traffic flows in Kubernetes clusters
Today, the cloud platform engineers are facing new challenges when running cloud native applications. Those applications are designed, deployed, maintained and monitored unlike traditional monolithic applications they are used to working with.
Cloud native applications are designed and built to exploit the scale, elasticity, resiliency, and flexibility the cloud provides. They are a group of micro-services that are run in containers within a Kubernetes cluster and they all talk to each other. It can quickly become overwhelming for any cloud engineer to understand and visualize their environment.
Visualizing Kubernetes network traffic and service dependencies presents significant challenges due to the dynamic and distributed nature of Kubernetes environments. The dynamic nature of Kubernetes clusters, with frequent scaling of pods, creation and deletion of services, and changes in network connections, makes it difficult to capture an accurate and up-to-date representation of network traffic and service dependencies.
Additionally, the complexity of Kubernetes networking, involving multiple components such as pods, services, and network policies, further complicates the visualization of network traffic flow and understanding of service dependencies. The use of microservices architecture in Kubernetes, where applications consist of interconnected services, adds to the complexity, particularly as the number of services grows.
Moreover, the scalability Continue reading
What’s new in Calico v3.26
We are excited to announce the release of Calico v3.26! This latest milestone brings a range of enhancements and new features to the Calico ecosystem, delivering an optimized and secure networking solution. This release has a strong emphasis on product performance, with strengthened security measures, expanded compatibility with Windows Server 2022 and OpenStack Yoga, and notable improvements to the Calico eBPF dataplane.
As always, let’s begin by thanking our awesome community members who helped us in this release.
Community shoutout
Big thanks to our GitHub users afshin-deriv, blue-troy, and winstonu for their valuable contributions in enhancing the Kind installation and VXLAN documentation, as well as improving the code comments.
Additionally, we would like to extend our appreciation to laibe and yankay for their efforts in updating the flannel version and improving the IPtables detection mechanism. Their contributions have been instrumental in improving the overall functionality and reliability of our project.
Finally, a huge thank-you to dilyevsky, detailyang, mayurjadhavibm, and olljanat for going above and beyond in pushing Calico beyond its original scope and for generously sharing their solutions with the rest of the community.
Community-driven enhancement request: Fine-grained BGP route control
The primary responsibility Continue reading
Encryption in container environments
Kubernetes has become the de facto standard for container orchestration, providing a powerful platform for deploying and managing containerized applications at scale. As more organizations adopt Kubernetes for their production workloads, ensuring the security and privacy of data in transit has become increasingly critical. Encrypting traffic within a Kubernetes cluster is one of the most effective components in a multi-layered defence when protecting sensitive data from interception and unauthorized access. Here, we will explore why encrypting traffic in Kubernetes is important and how it addresses compliance needs.
Why Encryption is Necessary
Two encryption methods are commonly adopted for protecting the data integrity and confidentiality; encryption at rest and encryption in transit. Encryption at rest refers to encrypting stored data, e.g. in your cloud provider’s managed disk solution, whereby if the data was simply copied and extracted the raw information obtained would be unintelligible without cryptographic keys to decrypt the data.
Encrypting data in transit is an effective security mechanism and a critical requirement for organization compliance and regulatory frameworks, as it helps protect sensitive information from unauthorized access and interception while it is being transmitted over the network. We will dive deeper into this requirement.
Encrypting data in transit Continue reading
Calico monthly roundup: May 2023
Welcome to the Calico monthly roundup: May edition! From open source news to live events, we have exciting updates to share—let’s get into it!

Customer case study: Rafay Rafay achieved turnkey Kubernetes security using Calico on AWS. Read our new case study to find out how. |

New guide: CISO’s security guide to containers and Kubernetes This guide provides CISOs and other security decision-makers with an overview of container security, insights into securing Kubernetes landscapes and container-based applications, and why securing these technologies requires a unique approach. |

Tigera Named Winner of the Esteemed Global InfoSec Awards during RSA Conference 2023 We’re excited to announce that we won the ‘Hot Company: Container Security’ category of the Global InfoSec Awards from Cyber Defense Magazine! Check out the full press release for more details. Read the press release. |
Open source news
- Calico Wall of Fame – As a valued member of our Calico users community, we would like to feature you on our NEW Project Calico Wall of Fame. To participate, fill out the form here.
- Flagsmith & Project Calico Interview – In this podcast, Ben Rometsch from Flasgsmith interviews Tigera’s Shaun Crampton about his experiences as Continue reading
How doNotTrack policies work in the Calico eBPF dataplane
Almost all modern network systems, including stateful firewalls, make use of connection tracking (“conntrack”) because it consumes less processing power per packet and simplifies operations. However, there are use cases where connection tracking has a negative impact, as we described in Linux Conntrack: Why it breaks down and avoiding the problem. Distributed Denial of Service (DDoS) mitigation systems, defending against volumetric network attacks, is a well known example of such a use case, as it needs to drop malicious packets as fast as possible. In addition to these attacks, connection tracking becomes a potential attack vector as it is a limited resource. There are also applications generating huge amounts of short lived connections per second, to the point that tracking connections leads to more processing and defeating its intended purposes. These use cases demonstrate that there is a need to not track connections in a firewall, also known as stateless firewalling.
In this blog post, we will explain how Project Calico uses eXpress Data Path (XDP) in its eBPF dataplane (also in its iptables dataplane but not the focus of this post) to improve the performance of its stateless firewall. XDP is an eBPF hook that allows a program to Continue reading
Case study: Calico on AWS enables turnkey networking and security for Rafay’s enterprise-grade Kubernetes Operations Platform
Organizations are adopting Kubernetes on Amazon Web Services (AWS) to modernize their applications. But Kubernetes clusters and application lifecycles demand a considerable investment of cost and resources, especially for edge applications.
Rafay’s SaaS-based Kubernetes operations platform (KOP) helps platform teams deploy, scale, and manage their fleet without requiring anyone on the platform team to be a Kubernetes expert. Hosted on AWS Elastic Kubernetes Services (EKS), Rafay’s unified, enterprise-grade KOP supports Kubernetes and application lifecycle management through automation and self-service with the right standardization, control, and governance level. Rafay empowers organizations to accelerate their digital transformation while limiting operating costs.
In partnership with AWS and Tigera, Rafay shares the story of how it leveraged Calico on AWS to secure its turnkey offering in an exclusive case study. Here are the highlights.
Challenges
To secure its KOP and enable customers with little to no Kubernetes experience, Rafay required a scalable, Kubernetes-native security solution that could:
- Provide and enforce networking and security policy for multi-tenant environments through workload isolation with identify-aware microsegmentation
- Eliminate IP address exhaustion issues and deliver automated flexible IP address management (IPAM) to allow for agile scaling without increasing operational overhead
- Seamlessly integrate with Amazon EKS, where Rafay’s KOP is Continue reading
Achieving High Availability (HA) Redis Kubernetes clusters with Calico Clustermesh in Microsoft AKS
According to the recent Datadog report on real world container usage, Redis is among the top 5 technologies used in containerized workloads running on Kubernetes.
Redis database is deployed across multi-region clusters to be Highly Available(HA) to a microservices application. However, while Kubernetes mandates how the networking and security policy is deployed and configured in a single cluster it is challenging to enforce inter-cluster communication at pod-level, enforce security policies and connect to services running in pods across multiple clusters.
Calico Clustermesh provides an elegant solution to highly available multiple Redis clusters without any overheads. By default, deployed Kubernetes pods can only see pods within their cluster.
Using Calico Clustermesh, you can grant access to other clusters and the applications they are running. Calico Clustermesh comes with Federated Endpoint Identity and Federated Services.
Federated endpoint identity
Calico federated endpoint identity and federated services are implemented in Kubernetes at the network layer. To apply fine-grained network policy between multiple clusters, the pod source and destination IPs must be preserved. So the prerequisite for enabling federated endpoints requires clusters to be designed with common networking across clusters (routable pod IPs) with no encapsulation.
Federated services
Federated services works with federated endpoint identity, Continue reading
Make your FortiGate firewalls work with Kubernetes: How Calico enables Fortinet firewalls to secure Kubernetes workloads
FortiGate firewalls are highly popular and extensively utilized for perimeter-based security in a wide range of applications, including monolithic applications developed and deployed using the traditional waterfall model. These firewalls establish a secure perimeter around applications, effectively managing inbound and outbound traffic for the organization. FortiGate relies on IP addresses for implementing “allow/deny” policies.
The use of IP addresses is effective for non-cloud native applications, where static IP addresses serve as definitive network identifiers. However, in a Kubernetes environment, workloads have dynamic IP addresses that change whenever they are restarted or scaled out to different nodes. This dynamic nature poses challenges when utilizing FortiGate with Kubernetes workloads, requiring continuous updates to firewall rules and the opening of large CIDR ranges for node-based access. This introduces security and compliance risks, as workloads running on these CIDR ranges gain unrestricted access to external or public services.
To facilitate the usage of FortiGate firewalls with Kubernetes workloads, it becomes crucial to identify workloads that necessitate access to external resources and assign them fixed IP addresses for utilization in FortiGate firewall rules. The integration of Calico with FortiGate firewalls and FortiManager offers an elegant solution, enabling the use of FortiGate firewalls while retaining existing Continue reading
Case study: Calico Enterprise empowers Aldagi to achieve EU GDPR compliance
Founded in 1990, Aldagi is Georgia’s first and biggest private insurance firm. With a 32% market share in Georgia’s insurance sector, Aldagi provides a broad range of services to corporate and retail clients.
With the onset of the pandemic in 2019, Aldagi wanted to make its services available to customers online. To this end, the company adopted an Agile methodology for software development and re-architected its traditional VM-based applications into cloud-native applications. Aldagi then began using containers and Kubernetes as a part of this process. Using self-managed clusters on Rancher Kubernetes Engine (RKE), Aldagi created distributed, multi-tenant applications to serve its broad EU customer base.
In collaboration with Tigera, Aldagi details its journey using Calico to achieve EU GDPR compliance, in order to share its experience with the rest of the Kubernetes community.

Case study highlights
Because Aldagi’s applications are distributed and multi-tenanted, the company faced three major challenges when it came to achieving EU GDPR compliance:
- Granular access control
- Visibility and security controls for workloads with sensitive data
- Continuous compliance reporting and auditing
By deploying Calico, Aldagi solved these challenges and achieved EU GDPR compliance, Continue reading
Kubernetes network security foundations: Get started on building your Kubernetes network security policies with Calico!
The adoption of cloud native applications has become a necessity for organizations to run their businesses efficiently. As per Gartner, more than 85% of organizations will embrace a cloud-first principle by 2025, which will rely on adopting cloud native applications for complete execution. The massive increase in adoption of cloud native applications has given rise to more security challenges such as container image vulnerabilities, configuration errors and a larger runtime attack surface. Kubernetes has become the de facto standard platform to host and run cloud native applications. However, as Kubernetes adoption gains momentum, so does the security risk associated with business-critical applications that communicate with multiple external and internal systems. Kubernetes network security is a critical aspect of securing cloud native applications and the Kubernetes platform itself. This multi-part blog series aims to explore the network security challenges of the Kubernetes environment and provide insights into mitigating them using Calico security controls. The series will cover various aspects of network security, including security policies, application layer security, host network security, Pod traffic encryption, and the importance of a defense-in-depth security approach. Let’s dive into the world of Kubernetes network security and learn how to protect your organization’s valuable assets.
Detect malicious activity and protect your containerized workloads in Amazon EKS or AWS
As containerized applications become increasingly complex, it can be challenging to design and execute an effective container security strategy. With the growing trend towards cloud-based applications and services, cyber criminals are also evolving their attack techniques, making container security solutions more critical than ever. Calico provides robust detection capabilities to detect known and zero-day container and network-based attacks. In this blog, we will look at Calico’s capabilities to detect network-based attacks.
Calico offers comprehensive protection against both known and zero-day network-based attacks. Using a combination of workload-based IDS/IPS, Calio can detect and block connections to known malicious IPs identified with AlienVault and custom threat intelligence feeds. Calico also uses heuristics-based learning to identify anomalous network activity and prevent zero-day attacks. To further protect against OWASP Top 10 attacks, Calico provides a web application firewall (WAF) that can intercept attacks and prevent them from reaching your applications. Additionally, Calico can also block requests from malicious IPs to prevent DDoS attacks from overwhelming your system.
Malicious attack on cloud-native application and how to prevent it
In this blog, we will go through a scenario where an attacker compromises a public-facing application and gains a foothold in the AWS EC2 or EKS network Continue reading
How to integrate Calico Image Scanner with Argo CI/CD
In today’s fast-paced software development environment, developers often use common public libraries and modules to quickly build applications. However, this presents a significant challenge for DevOps teams who must ensure that these applications are safe to use. As organizations move towards dynamic models of software development that rely on Continuous Integration and Continuous Deployment, the responsibility for deploying secure applications has shifted from traditional security teams to development teams.
To address this challenge, I will provide general guidelines on how to integrate the Calico Image Scanning feature into a CI/CD pipeline, using Argo. This will help ensure that images are built safely and free from Common Vulnerabilities and Exposures (CVEs). In this blog post, we will use a Kubernetes validating webhook configuration to attach a Calico Cloud admission controller that can accept or reject certain actions on resources, such as the creation of pods. This will prevent the deployment of images that contain known CVEs, thus strengthening the overall security of your software development process.
Overall Architecture
The building blocks to use Argo as an example of this integration are below:
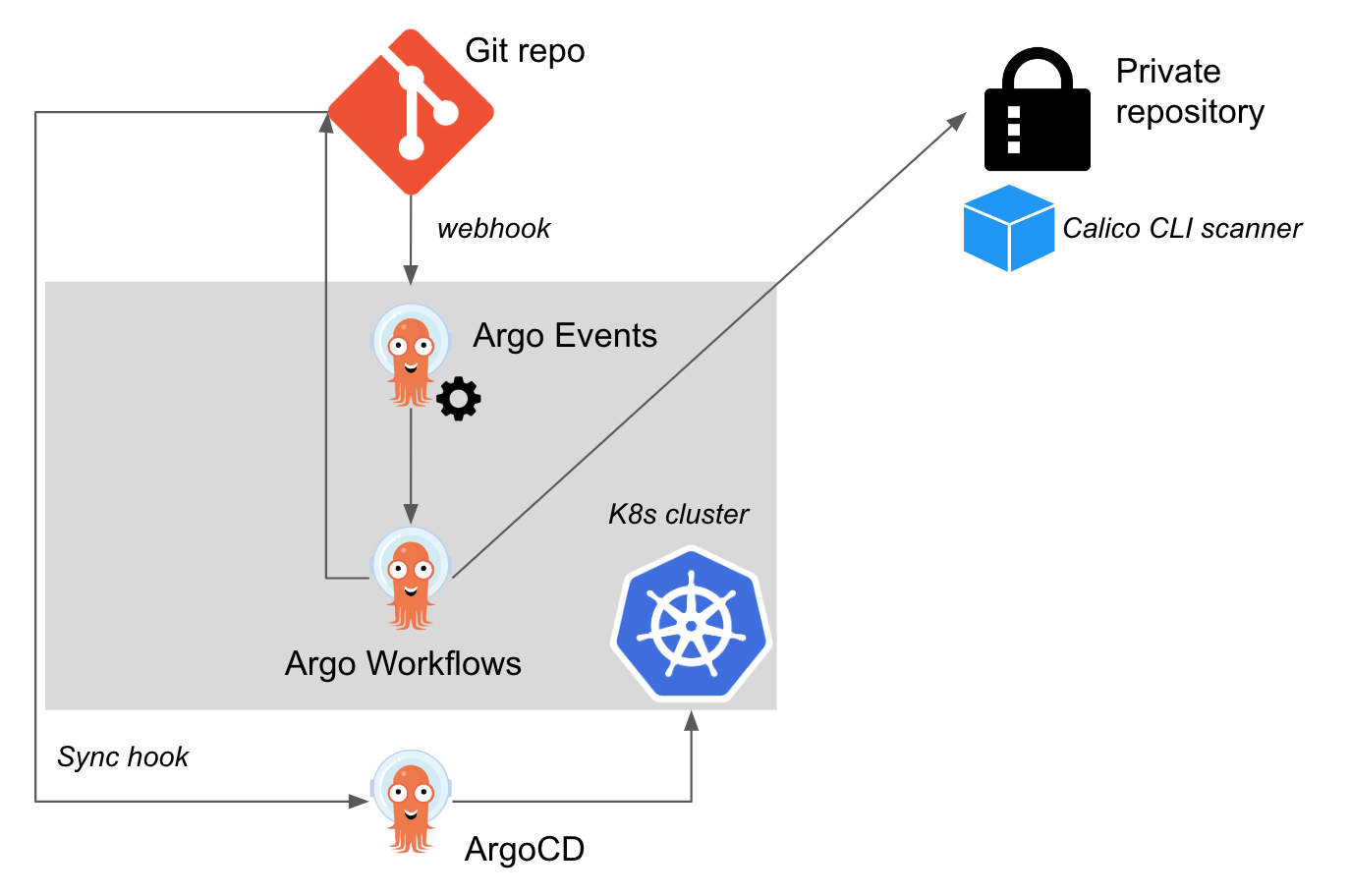
Relevant Calico configuration
Before even committing changes to our application, we must setup the Calico Admission Controller within our Continue reading